The Georgetown Army ROTC program first describes the benefits, and then demonstrates a proper army pushup to standard. Pushups are common in the army, they increase the strength and endurance of your chest, shoulders, and triceps muscle. The push up is also a part of the Army Physical Fitness Test (APFT). In order to be contracted and received scholarship benefits male cadets in the age range of 17 - 21 must perform 43 pushups while female cadets in the same age range must perform 19 pushups.

In this how-to video, you will learn how to use a song to read palms. Memorize these lines to music to help you. First, if you have a rich line, you are the rich and you get much money. If you have a sun line, you are popular. Everyone likes you because you are the sunshine. Check your palm. Check your life line. If it is thick, you have a powerful body. If it is thin, you are weak. Check the head line. If you have a short line, you quickly decide and act. If it is long, you need to think fir...

This is a great way to turn your treadmill into a walk station quickly and cost effectively. You only need a few things for this project: a tape measure, four shelf mounting brackets, screws, a drill, and a shelf.

This video demonstrates how to stain a white sheet of paper and make it look antique. You'll need two tea bags (an extra one if the other tears open. Place the paper to be stain on a tissue or newspaper to avoid a mess. Take half a tumbler of hot water and dip a tea bag until the color becomes dark orange. Take out the tea bag and gently wipe all over the sheet of paper and also dab gently on the applied parts for a darker stain in some regions to look natural. Repeat this process by turning ...

Ben for Mechanical Mashup demonstrates how to build a barn door halogen light system for a studio and how to establish right triangles and parallel lined without a square. It is quiet expensive to buy a barn doors according Ben, so it could be built by us. These barn doors can be adjusted anyway we want to. So the barn doors are to be fixed to a halogen light. First thing done is to unscrew the frame of the halogen light. The glass is removed by just bending the frame. Next thing to do is to ...

This video shows you how to create a continuous, daisy-chain necklace. The materials used include: size 11 rock eyes in yellow, red and purple, a toggle clasp , 9mm thread and a size 10 beading needle. Start by sewing on one half of the clasp, tying a knot to hold it in place. Be sure to leave the tail ends long enough to be able to re-thread it later with a needle to sew the tail ends. The video then shows the precise order in which the various beads are threaded through to produce a chain i...

This do it yourself centerpiece is brought to you by A-Bnc parties and more. This starts of by making the bow, shown by painting a dowel and letting it dry. Then glue the 'frogs' at the ends of the dowel and glue fishing line to both frogs and trim to fit. Next take a polystyrene cut out of a violin and seal it. This helps paint stick to the surface of the cut out. The violin is painted brown to replicate an actual violin. Using black paint you detail the 'f' holes and allow to dry before pro...

In this video the instructor shows how to make a simple flash click-through photo gallery with Action Script 3. First the instructor shows a sample gallery that you can make using this tutorial. To do this open a new flash action script 3.0 file. The first thing you have to do now is, in the right hand side change the document size to 750 by 500 pixels and give it a dark back ground color like dark gray. Now open the image that you want to use in this album by dragging them on to your flash w...

In this video from gally042, Aaron Gallagher of Free and Easy Guitar shows us how to play "Need You Now" by Lady Antebellum. He begins by teaching the intro which is an F then A minor for 16 beats. Then into the chorus he tells us the chords go C then A minor, then back to C, and back to A minor. Next is F, F. Then he plays the second verse and also tells us it is all down strums. Then the instrumental comes and here are the chords for that: A minor, G, C, A minor, F, G. Then the bridge is on...

The video is from the DJ tutorial and it shows us the basic principles of scratching for the beginners. And the first lesson you should learn is that there are basically four movements and here you will actually be not going to scratch put will be moving the record forward and backward. These four moves form the basis for starting to learn scratching. First you need are the type of sounds which are either acapella (song with no music) or with sounds (tracks with breaks on it). Before starting...

This tutorial is great if you want to apply porcelain theatre clown makeup. First white out your face and then with colored eye liner, trace out where you want the color to go. Apply a blue colored base on the lid and blend it just above the crease. The video uses a red Mufe flash color and applied it over the blue bringing the color onto the side of the nose. Using Nyx jumbo eye pencil in Black Sheep being filling in the remaining space on the brow. Using shimmery blue, a matte red, and a ma...

This video shows you how to tile and waterproof a shower. Stage 1

If there was a way to make duct tape more desirable and distinct, would you do it? Well, what if there was a way to make duct tape glow? There is a way. Watch this science video tutorial from Nurd Rage on how to make duct tape glow with Dr. Lithium.

If you're interested in upgrading your RAM for the Samsung NC20 netbook, this video shows you how. This simple to follow video gives you a quick and simple way to make changes to your netbook. The only tool that is required is a small screwdriver.

Birds of a Feather: As you move on from mission to mission, things get harder. Trigger this mission in the center of town. A couple of conspirators meet up and begin walking away from you. You need to trail them, but obviously you don't want to rouse their suspicion. Stay close enough that they never leave your line of sight, but try not to run or do anything else high profile. If a nearby guard bumps into you and gives you crap, turn the other cheek. If you get into a fight, you stand a good...

Have you tried working out with a single leg bridge exercise? Single leg bridge exercises are an essential part of lifting weights and strength training. This fitness how-to video tutorial demonstrates how to gain leg strength with single leg bridges. Learn about working out leg muscles with exercises in this workout video.

Bottleneck slide guitar is based on an early one string folk instrument called the Diddley-Bow, and the traditional playing style of Hawaiian Guitar. The early Blues Masters of the 1920s and 30s, would place a bottleneck from a wine bottle, or a short piece of metal pipe on their finger. Using this as a slide, they could move up and down along the strings of a guitar imitating singing or the cries and moans of the human voice. This style uses an early method of tuning the guitar called open t...

Learn how to do reverse flys on a pec deck. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do wide push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do plyometric clap push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

We've all been there. You wake up early, hungry for breakfast, but not just any breakfast will do. You want bacon and eggs. So, you blindly stumble into your kitchen, underwear-clad, and begin fumbling about with pots and pans. After a few minutes, you fill your pan with delicious and smokey rashers and turn the heat on. Everything seems okay... until the bacon actually starts to cook. With a splat, burning hot grease flies out of the pan and bombards your skin, causing intense pain and great...

There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because:

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

The video begins with a piece of card/thick paper in front of the person who is making the box. The maker then shows a small box as an example of what the finished box will look like. The maker then takes the top left corner and folds it over so that it is against the right edge of the paper and so the two edges are straight. Then she takes some scissors and cuts the excess paper (the area which is just a single thickness, not double) to leave a folded triangle. Next she unfolds the paper and...

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

The punch hole design of the Samsung Galaxy Note 10 has challenged users to find a clear way to deal with it. Although it's less intrusive than a notch, if left unaccounted for, it can be just as much of an eyesore. One of the more creative ways we've found is to use as a battery indicator.

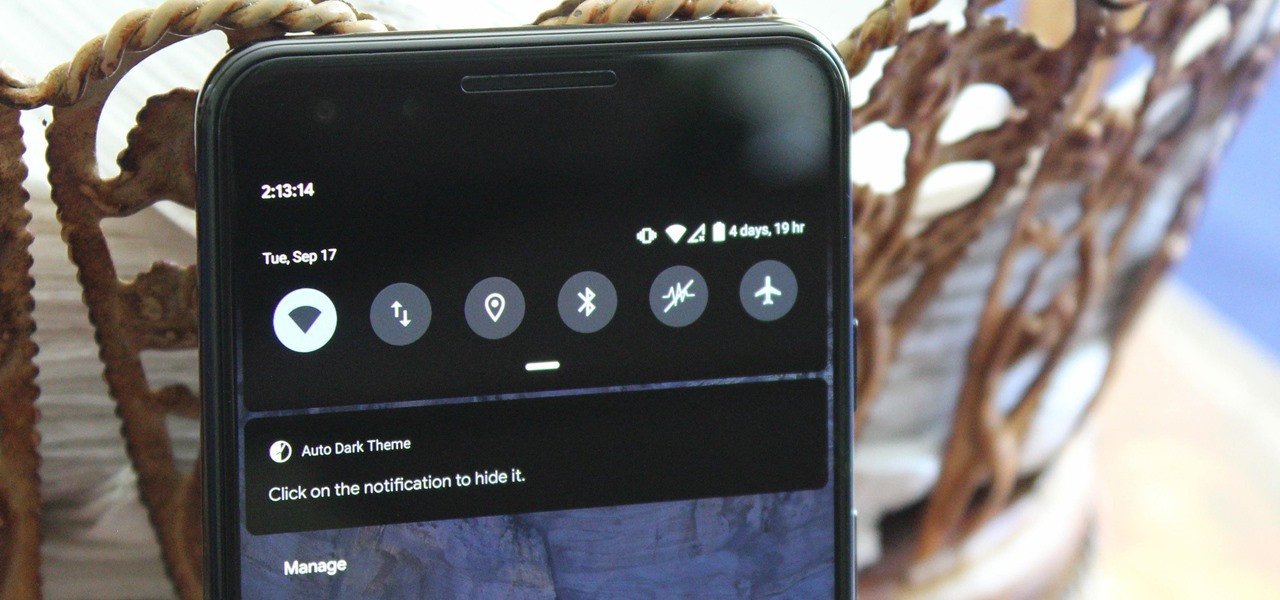
Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple app can turn dark mode into a true night mode.

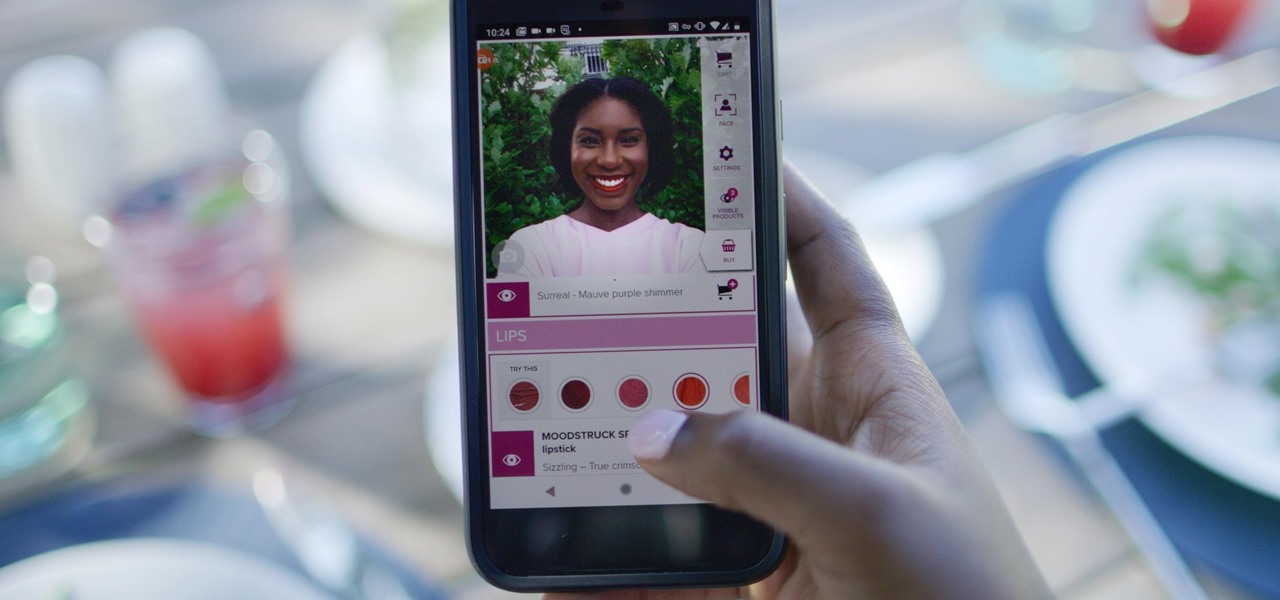
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

The longer it takes Apple, Snapchat, Facebook, and other tech giants to build their own version of augmented reality headsets and smartglasses, the longer runway of practical experience Microsoft gains with the HoloLens and its sequel. The latest example: AR cloning.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

As the opening act to the grand unveiling of the long-awaited HoloLens 2 at Mobile World Congress Barcelona on Sunday, Microsoft showed off the standalone Azure Kinect time of flight sensor, which also happens to supply the improved human and environmental understanding capabilities of the next-generation augmented reality headset.

Now that Lego Movie 2, a film about an imaginary world made of plastic bricks existing parallel to the real world, is in theaters, it's the perfect time to shop for Lego apparel at a store modeled after that world.

Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stable, and undetectable ways to do it. Perhaps we should discuss why OnePlus has been holding out you when it comes to this feature, though.

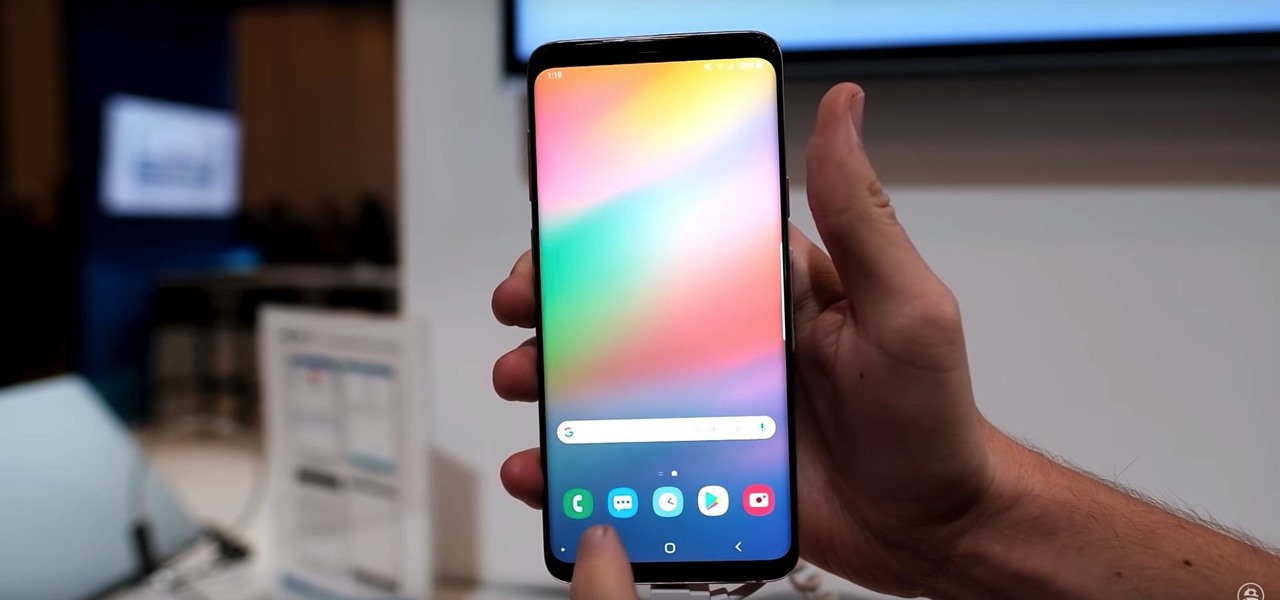
Who doesn't love a refresh? Samsung's upcoming One UI makes it easier to use your device with one hand and adds a fresh coat of paint to the formally "Samsung Experience" skin. While you're probably looking forward to installing One UI on your phone, not all Galaxies are equal — your device could be one of the first to receive the update, or it could never see One UI at all.