
News: Amazon’s First Smartphone Will Have 6 Cameras, 3D Controls, & Free Prime Data
It's been rumored ever since the 2012 release of the Kindle Fire, and now Amazon's first smartphone is set to debut a little later this year.


It's been rumored ever since the 2012 release of the Kindle Fire, and now Amazon's first smartphone is set to debut a little later this year.

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

The Nexus 7 is a huge jump in screen size when coming from a phone, but obviously this tablet is still smaller than some of the major players such as the Nexus 10, Galaxy Tab, etc. One way to squeeze out a little more space is to eliminate the navigation and status bars.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.
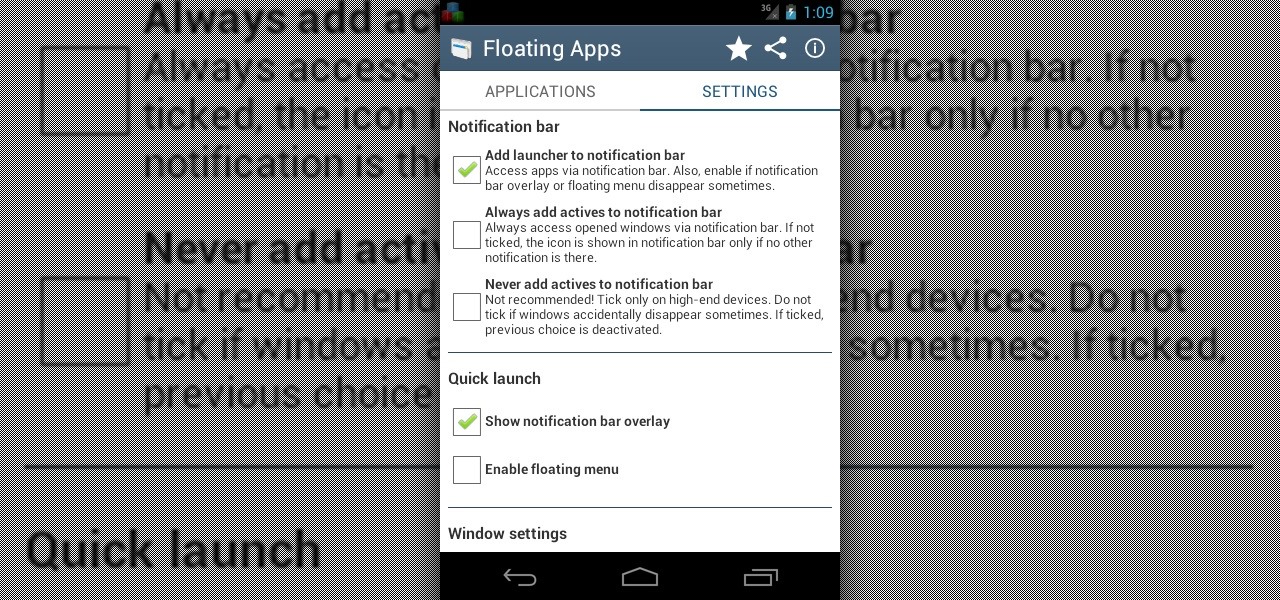
Sometimes, it's very useful to be able to use more than one app on Android phone or tablet. For example, if you want to watch a movie while surfing or if you need calculator, find some contact, write a note, search web or wikipedia for some facts, etc.

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.
According to WitsView, 8-inch displays will rule the tablet scene this year at 11.9% market share, compared to yesteryear's 2.6% market share. By year's end, it'll be almost 18%.

Today's project will show how you can convert your laptop, smartphone, or tablet computer into a makeshift projector—just in time for March Madness! It's super cheap to build, and can add a little bit of creative fun to your next sports party.

The Geminid meteor shower happens every December and has been observed for over 500 years. It's is also known as Winter's Fireworks because when viewed from the right location, there are enough meteors to light up the whole night sky, and some of them can even be different colors. The shower appears to come from the Gemini constellation, but is actually caused by Earth passing through the tail of dust and debris left behind by the comet 3200 Phaethon.

In this project, you'll learn step by step how to modify a microwave oven transformer into a high-current device that can pump out 800 amps of electrical current, which is enough amperage to melt metal. If you liked the Metal Melter you saw in my previous project, here's how you can make your own!

The director of 100 Musicians and Nurse/Fighter/Boy talked with us about old school filmmaking Charles Officer has directed shorts, music videos for K’naan, and the features Nurse/Fighter/Boy and Mighty Jerome, a documentary about Canadian track star Harry Jerome. His new short 100 Musicians, which screens Monday as part of Short Cuts Canada, is a small ode to civic optimism, concerning itself with a lovers’ argument over who exactly misheard a radio DJ reporting the plans of Toronto’s much m...

While I am a writer with a degree in Creative Writing, I haven't published any Steampunk fiction. However, as a panelist and track director, I've been on panels with many well-known Steampunk writers and have gleaned insight from the things they've said. I've compiled some of those things into this post, which will hopefully be helpful to all of the writers out there!

Psy's K-Pop hit, Gangnam Style has taken YouTube, and now the world by storm. Love or hate the song, there is just no way you'll watch the music video only once.

Always downing a glass of red wine in the evening? Don't be ashamed. Red wine has some great health benefits when consumed in moderation, including improved memory, lower risk of heart disease, and even bone strengthening. Photo by Joe Shlabotnik

With the upcycling revolution, folks are turning their otherwise useless junk into something functional for the home. Practically anything that you would normally toss or recycle can be reused for a bigger and better purpose. Your milk jugs, chopsticks, toilet paper cardboard, glass jars, and even your old junk computer keyboards can be upcycled into something totally useful around (or away from) the home.

Hello and welcome to my post. I would like to share a few things I have picked up along the way - while feeding my two dwarf rabbits. In this tutorial I would like to answer the question - How to choose the best food for your rabbit?

Let's face it—if you care about anyone around you, then you brush your teeth. Brushing is an excellent way to not only prevent tooth decay, but to keep people from running away from you with their noses pinched.

Summer is here, and temperatures are rising. Instead of shelling out for an expensive new air conditioning unit, why not build one yourself with a few bucks worth of old computer parts?

So, this idea was born from a necessity to save. My household uses tissues a lot. I have two small kids, so they are extremely useful. The problem with tissues is that they seem to disappear in no time. So, whenever we ran out in-between shopping visits, my family would just use toilet paper.

Hello! This tutorial is made for all who like to sunbath, but also do not want to get those tiny first wrinkles too soon. Or even skin cancer.

Brushing your teeth is a necessity. You don't want to walk around with yellow teeth and stinky breath, and it's common courtesy to those around you to care about your personal hygiene at least that much.

Mentoring is a way to help others and improve your community. There are established mentoring organizations to join or you can go seek out those already in your life who you can help with your time end knowledge.

Play the greatest tower, turret defense game ever... Warzone Tower Defense. And learn how to hack Warzone Tower Defense with tricks and cheats. Watch this video tutorial to learn how to cheat Warzone Tower Defense without a hack (09/30/09).

If you want to improve your violin technique then this how to video is the place to start. You will learn how to play an exercise that improve your tuning. This exercise, based on the Sevcik System, is designed to help intonation training. You should start at the speed of 40 then gradually move it up to the goal of 16th notes at the speed of 192. This exercise will improve the overall shape of the left hand; train the hand to be more articulate and accurate (no muscles just a twitch); builds ...

Self disclosure forms friendships with active listening and sharing, telling others about yourself, your thoughts, fears, and goals. Learn how to improve self disclosure and trust in this free communication video series.

While there's an art to surviving the all-nighter, there's also an art to staying awake throughout the day when you're operating on little to no sleep. In 1964, the record for sleep deprivation was set by 17-year-old Randy Gardner, who stayed awake for an incredible 264 hours and 12 minutes. Now while we're not out to challenge Randy for his title, we can certainly look to him for inspiration in beating back our own fatigue.

This is a lengthy, detailed series on iPhone development, for which you'll need an Intel-based Mac computer, running Mac OS X 10.5 (Leopard) or higher. Then, before you actually get started developing for the iPhone, you'll need to register as a developer with Apple. Then, you'll need to download Xcode and the iPhone SDK. Once you have all this, you can start developing iPhone applications!

Have you ever admired those individuals that get so much accomplished in a day and wonder how the heck they do it? Now's your chance to learn their secrets. The Productivity & Motivation Master Class Bundle brings you everything you need to life-hack your way into leading a more productive lifestyle at home and work.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

If you're interested in becoming an in-demand project manager or leader in today's data-driven world, you need to know more than just a few generic management strategies to lead teams and companies successfully.

While there are many advantages to working from home, properly managing your time can be a real issue. Working remotely requires a particular skill set, including an ability to focus, self-motivate, and communicate from a distance. Thankfully, all of these skills are teachable.

We all know Android updates have been iffy in the past. But Google has implemented several measures recently that have sped up the process substantially, and OnePlus is taking advantage of these. Still, a staged rollout update might keep you waiting for a few days or longer. So if you'd rather skip the wait, there's a better way to manually check for system updates.

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.
Android 11 won't be available as a beta update for Pixel devices until May 2020. Until then, the only way to try the latest Android version is by manually installing it. Usually, this means carrier models are left out since their bootloaders are locked, but there's still a way to get it done.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

New year, new me. You finally committed to working on the best physical you by going to the gym multiple days a week. Except about an hour in, you start getting really tired of it all. Before you run to the exit, pick up your phone.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

While its competitors are concentrating on building out AR cloud platforms to give advanced AR capabilities to mobile apps, Ubiquity6 is taking a step in a different direction.

The wearables space experienced its "big bang" moment back in 2015 when Apple released its first wearable device, the Apple Watch. Although the device was initially dismissed by some as an unnecessary charm bracelet packed with frivolous tech, in very short order, the public learned just how useful the Apple Watch can be.