The year was 1947. Scientists had isolated a virus from a pyrexial rhesus monkey in Uganda and named it after the forest where the monkey lived — Zika.

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

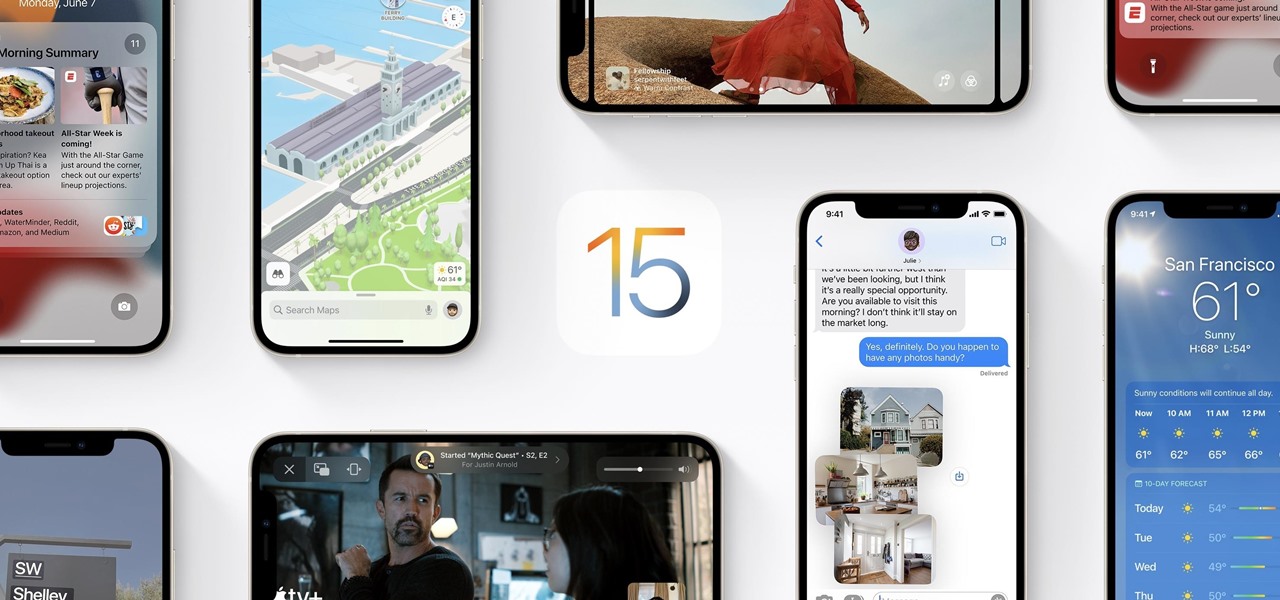
Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.
The body's usual response to a bacterial infection in the blood — called sepsis — takes time. It requires a carefully orchestrated sequence of events that gets the body's immune system ramped up to deal with the invading bacteria.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

You only need eggs and bananas to make these tasty pancakes that fit almost every hyphenated category: dairy-free, Paleo-friendly, grain-free, gluten-free, low-carb, and high-protein. It sounds too good be true, but these pancakes are easier to make than traditional pancakes and don't have any of that troublesome white flour. I've also included a three-ingredient recipe below for a slightly thicker pancake recipe.

Of all the places you'd think to check for bed bugs, I doubt that library books would be at the top of your list. As odd as it sounds, though, libraries and library books are some of the most common places for bed bug infestations. Libraries all over the country have reported bed bug problems this summer, and some have even had to temporarily close to take care of the problem. But before you vow to never set foot inside a library again, here's a little primer on how to check your books for be...

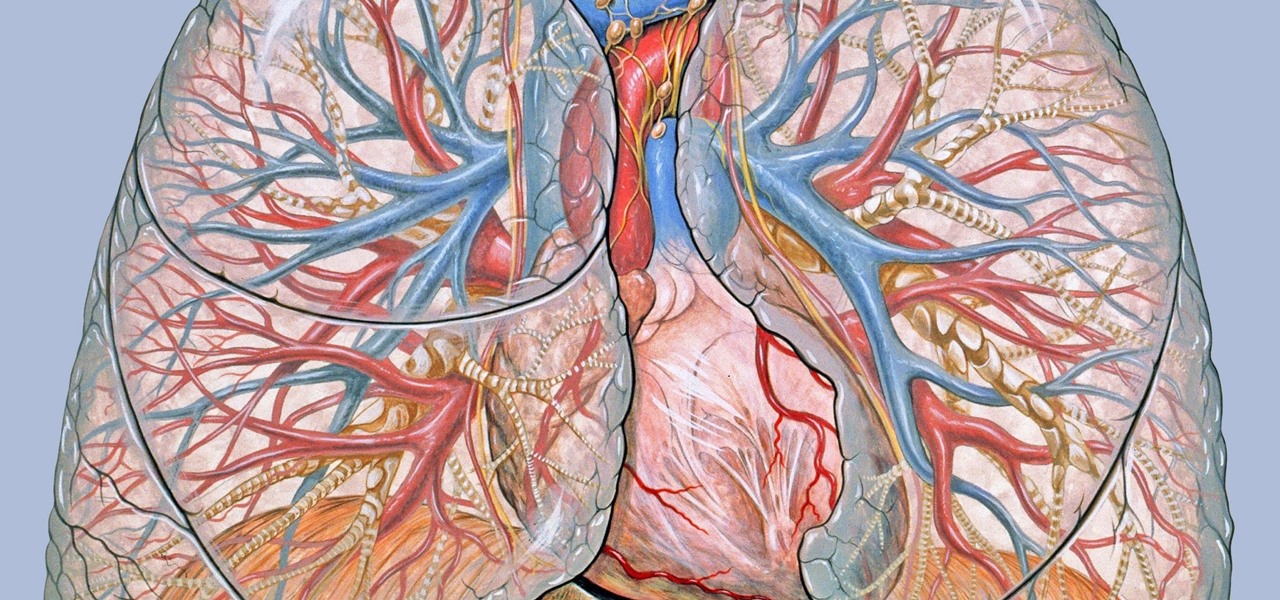
Once we recover from the respiratory infection pneumonia, our lungs are better equipped to deal with the next infection — thanks to some special cells that take up residence there.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

Call them what you will—moss piglets, water bears, or by their real name, tardigrade—but these intriguing tiny creatures can come back from the brink of death. They can survive boiling, deep freezing, UV radiation, completely drying out, and even a trip to space—without the benefit of being in a spacecraft.

Despite the availability of a vaccine against it, almost 50% of men aged 18-59 in the US are infected with the human papillomavirus (HPV). Why?

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Look, I'm no food snob. I once dedicated an entire day to eating only deep-fried things (butter, Twinkies, Oreos, pickles) at the Minnesota State Fair. But even I draw the line at instant mashed potatoes. I mean, why bother? It's not that hard to make perfectly delicious and fluffy mashers yourself.

Mouth burning with pain from eating too much hot sauce or some seriously "spicy" food? Well, ignore your first instinct and steer clear of that cup of cold water — it won't help. Instead, reach for a glass of milk, a lemon slice, a spoonful of sugar, or some starchy bread to dilute the painful heat on your tongue.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities. But don't wait—start submitting your own projects to the most appropriate World now!

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Just days before the release of the first image of the Magic Leap device, the company's CEO, Rony Abovitz, knew that the biggest moment of his life was about to unfold the following week. But instead of hunkering down in the Florida-based confines of the company's skunkworks, he instead decided to deliver a speech to the public about, what else, the future.

There are literally hundreds of granola recipes floating around the internet—but I can tell you right now that they're all completely unnecessary. You don't need a recipe to make granola; I've been making granola for years and have never once used one!

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

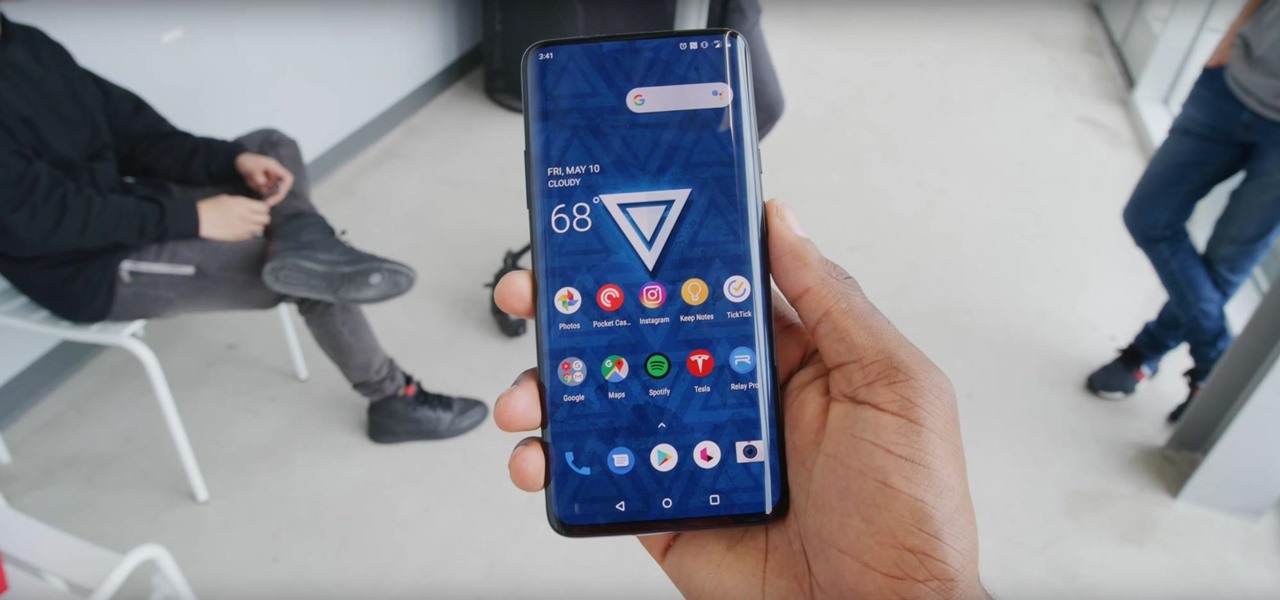
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.

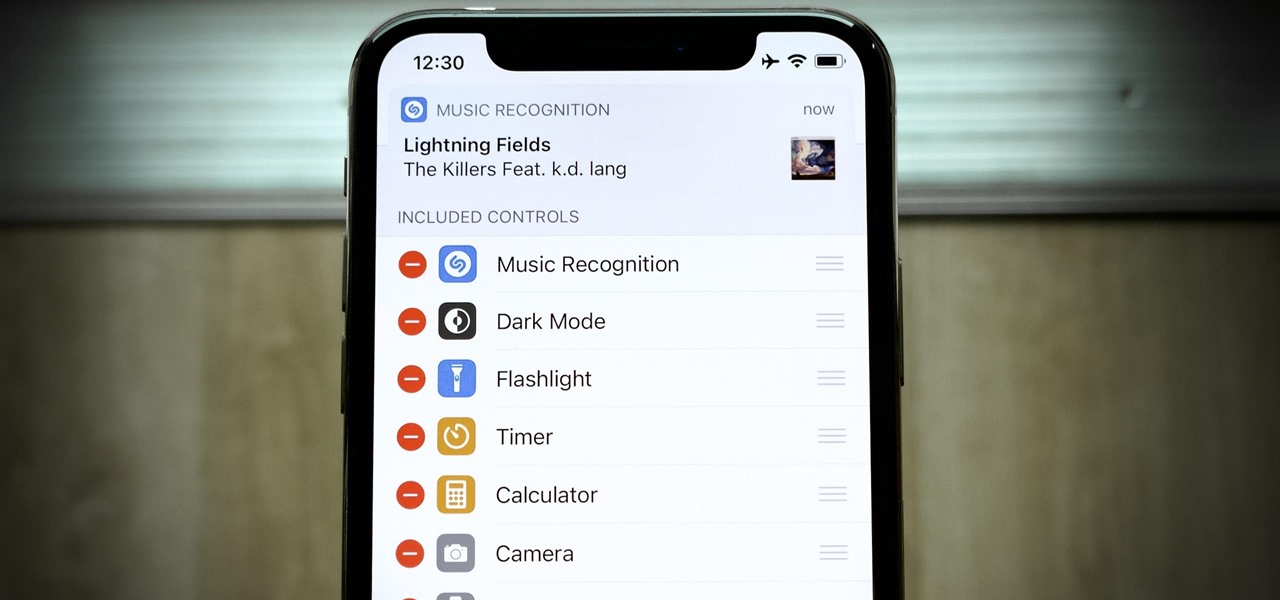
Apple just released the first beta for iOS 14.2 to iPhone software testers today, Monday, Sept. 21. This update brings a new Control Center tile for Shazam music recognition, a redesigned Now Playing Control Center tile, and a new "People Detection" feature in Magnifier.

Apple just released the fifth public beta for iOS 14 today, Wednesday, Aug. 19. This update comes one day after Apple released iOS 14 developer beta 5. It follows iOS 14 developer beta 4 by 15 days, and iOS 14 public beta 4 by 13 days.

Apple just released the fifth developer beta for iOS 14 today, Tuesday, Aug. 18. This update comes two weeks after Apple released iOS 14 developer beta 4, and 12 days after the release of iOS 14 public beta 4.

Watch this instructional quilting video to sew quarter inch piecing on your quilt. Use "Martelli's Stitch in the Ditch Binding Foot" as a 1/4 inch piecing foot. This allows you to sew straight lines on several layers of quilted fabric.

Use the Martelli Stitch in the Ditch Binding Foot for top stitching and with a double needle to get a professional finish to your quilting and sewing projects. Watch this video sewing tutorial and learn how to top stitch with a double need on a sewing machine.

Solving a Dilemma This is a simple how-to for a cost effective drip irrigation system for your garden. My motivation to set up my garden for drip irrigation was pretty simple. In the summer, it gets to 90+ degrees outside, and my 50’ garden hose didn’t reach the far extents where I have the majority of my large trees. I noticed a large amount of the water I applied to the trees just ran off and did absolutely nothing. This was a huge waste of resources.

In this tutorial, we learn how to crochet a puffy Valentine heart. First, you will make 8 foundation half double crochet. After this, you will work 4 half double crochets in the same stitch, then work 1 half double crochet in the next 6 stitches. Continue to do this until you have four more after this. For the second round, pull up and then half double crochet in the first stitch you made. Then, half double crochet for 6 stitches and then increase your stitches until you have 28 half double c...

Interested in getting started binding your own mini books? In this video from TV Weekly, Tricia stitches together mini file folders for the pages and covers the book boards with lovely paper to create a professional looking bound book. Fill this journal with photos and memories and keep it close as a perfect keepsake. Make a small stitchbound book.

This video crocheting tutorial follows a pattern to make a small ball. It not only illustrates how to follow pattern directions, but it also shows how to use stitch markers, right vs. wrong side, stuffing, and binding off. Learn how to crochet in the Japanese amigurumi style by watching this instructional video. Crochet a Japanese amigurumi ball.

Watch this video from This Old House to learn how fix a unbalanced door. Steps:

The Yarn Over (YO) edge is a nice way to increase. Here's how to do it for a Triangle Scarf. WATCH THIS VIDEO TO SEE HOW TO DO THE YO BIND OFF.