
Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

Drive.ai (a startup founded by Stanford University graduates), Waymo, General Motors, and serial entrepreneur and author Vivek Wadhwa are featured in today's top news.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.

Waymo's transfer of its driverless car know-how to commercial trucks will likely pose few challenges for the self-driving unit of Alphabet, which owns Google.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.
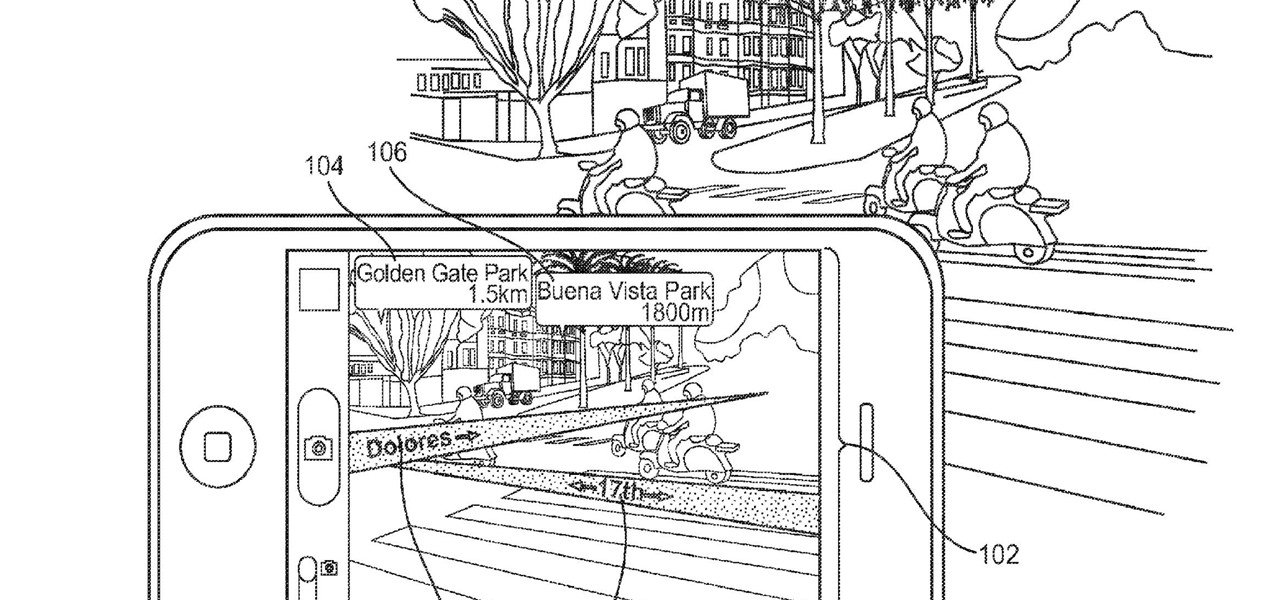
Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

Hello friends. This is actually my first how to.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Creating a class in Black Ops 2 is kind of like an art form. Every player has an insane amount of options for creating a character for all sorts of situations. Combining perks, with secondary weapons, and attachments allows for a wide range of killing options. But in order to unlock a lot of these perks and attachments, you need to gain XP. Gaining XP and collecting tokens is the lifeblood of the online gaming experience.

If you want to know the best way to get an accurate pH measurement, this shows the lab equipment needed and the processes used. When doing chemical reactions, sometimes the acidity or the basicity is important. This is usually defined as pH and measuring it can be very useful for getting the reaction right. There are a few ways to measure pH, and the simplest, cheapest, most reliable method is paper. But that's not all. See a whole lot of ways in this two-part video.

Need to secure your track to the road bed for your model railroad? Well, this video tutorial will show you how to do it, not to mention show you how to weather your flex track.

Every day we pass bridges, whether it's a foot bridge, a highway overpass, a span over water, or a viaduct over a valley. We pass on these structures without even thinking of the engineering genius that went into their design and construction, let alone the science behind their strength.

Redoing your floors can be expensive unless you know how to do it yourself. Learn the basics for installing a new engineered wood floor in this how to video. Watch the short DIY show clip and follow along so that you too can install a new engineered floor in your kitchen.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

MATLAB, an acronym for "matrix laboratory," was created over 40 years ago to service the applied mathematics community. The powerful programming language now has over four million users worldwide and is of particular import to engineers, scientists, and economists.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

The de Blasio Administration of New York City has announced that the NYU Tandon School of Engineering will be hosting the country's first publicly funded VR/AR facility.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

Drug-resistant bacteria have made curing some infections challenging, if not nearly impossible. By 2050, it's estimated that 10 million people will be dying annually from infections with antibiotic-resistant organisms.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

The Dark Knight Rises. The Amazing Spider-Man. The Avengers. Halloween is a few weeks away and all we're going to see are these same ol' superhero costumes. It's like that every year, due to the immense popularity of comic book films by DC and Marvel.

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to make an LED blink with an AVR microcontroller.

Check out this home repair tutorial video that demonstrates how to fix and diagnose your appliance. These videos are for information purposes only. A qualified and proficient engineer should be employed to replace any faulty parts on your domestic appliance.

Electricity can be conducted through a variety of unexpected mediums, including Jell-O, lemons and potatoes. Learn more about electric circuit experiments in this free science experiment video from a professional audio engineer and instrument builder.

Check out this video to see how to collect blood with the BD Vacutainer Eclipse Blood Collection Needle.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

The long guarded veil of mystery surrounding Magic Leap for years was finally lifted last year when the company revealed its Magic Leap One device.









































