Keyless entry remotes are great, but they don't always work how you want them to. One of the most common complaints is that they just don't reach far enough, and there's nothing more annoying when you can't remember where you parked. After all, what's the point of having "remote" entry if you have to be right next to the car for it to work?

It always sounds like a good idea to throw a party... until the party gets there. Next thing you know, you're running around hiding anything breakable, and once everyone leaves, you're stuck cleaning up the mess. But the worst part is footing the bill for everything, and if you don't charge at the door, your chances of getting anyone to chip in are slim to none once the party starts.

You can do a lot with water guns. Have trouble waking up? Make a water gun alarm clock that (almost) no one could sleep through. Prefer real ammo? Turn your water gun into an airsoft BB gun. And if you don't have one, you can even make your own.

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

Whether you want to use it to keep your guests safe or just to see who's the most drunk, it's always fun to have your own breathalyzer at a party. We've seen DIY breathalyzers before, like this one by Craig Smith, but how about an Arduino breathalyzer?

Most of us have given up our big, bulky stereos in favor of smaller, sleeker models, but how many of us actually get rid of the old ones? If you don't like the idea of throwing out or giving away electronics you spent good money on, you can always upgrade them instead!

Got an upset stomach or a little heartburn? America's favorite pink pill will cure it right up. But did you know that there's actually metal hiding in those chewable Pepto-Bismol tablets? Yes, metal. Technically, it's a poor metal, but metal's metal, right? Well, we do tend to eat a lot of iron in our diets, because it carries oxygen throughout our bodies, so consuming metallic minerals isn't anything abnormal. But you'd never think that Pepto-Bismol is actually made up of metal.

If you've ever been on your way to a party and felt that your outfit just wasn't flashy enough, engineering student 'Rambo' has got just the thing for you. His homemade LED suit lights up and dances to the beat of the music, and can even be controlled via Bluetooth.

If you've finished building your Curiosity rover and are wondering, now what? Perhaps it's time to move onto something a bit more... mobile?

For his thesis at Design Academy Eindhoven, artist/designer Tuomas Markunpoika Tolvanen created this incredible chair using tubular steel cut into thin rings. How did he get them to stay that way? He burned them. His project is called Engineering Temporality, and the inspiration came from his grandmother whose Alzheimer's disease is deteriorating her health and memories. Once he cut the rings, he laid them over an existing chair, only partially covering it. The fire acted as a varnish, creati...

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Gerridae—you've probably seen these weird bugs gliding across the surface of the water when you're out swimming or fishing. These insects are commonly referred to as water striders, or more cleverly, Jesus bugs, for their ability to "walk on water". It's a pretty cool trick, but what could it do for science, right? Turns out, quite a bit. Photo by felixtsao

Helping to prove that science is way awesome, an 18-year old electrical engineering student has successfully made a light bulb float. His name is Chris Rieger, and he's been working on his "LevLight" project for about six months now, with pretty amazing results. This feat of ingenuity was accomplished by using magnetic levitation, although that over-simplification masks how considerably difficult this undertaking was.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about capturing digital photos with the Meade Deep Sky Imager. The universe is out there, and you can take a picture of it.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Check out this cool art video tutorial to learn how to create cool infinite designs in AutoCAD. You'll see a quick overview of the AutoCAD interface, like the draw command toolbar. It's pretty cool to design infinite looking objects in AutoCAD, just watch to see how. An artist can create brilliant art even from an engineers software!

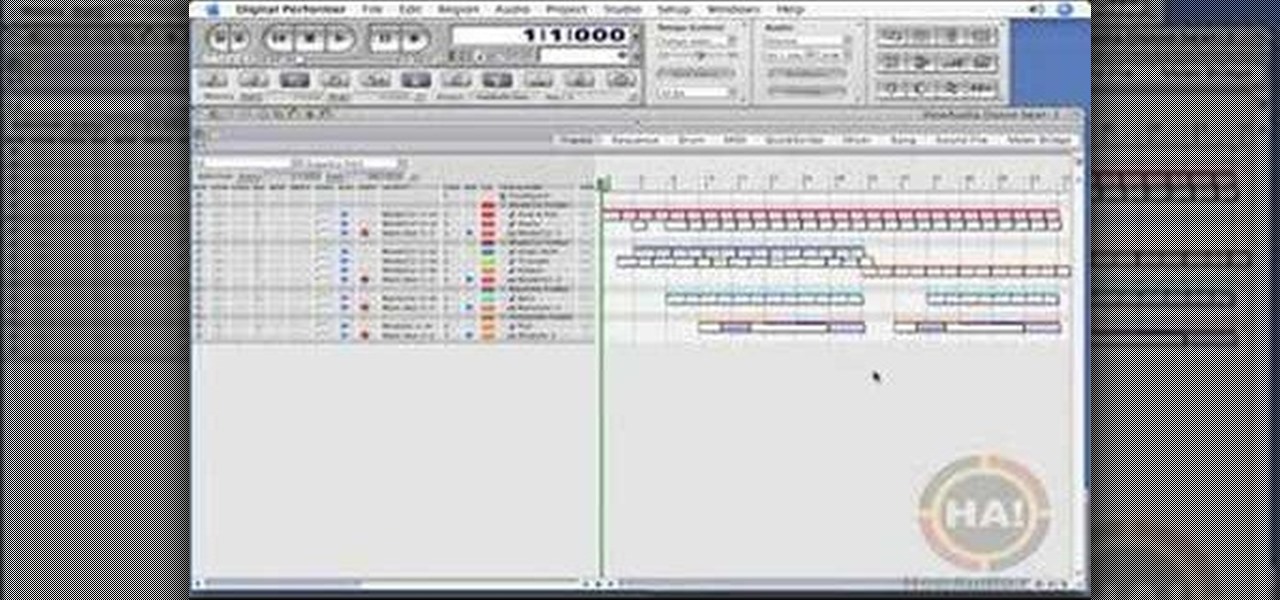
n this episode Academy and Grammy Award winning engineer Les Brockmann will share a little from his upcoming HowAudio.com title on MOTU Digital Performer 5.1. Here Les is talking about the audio set-up.

The Holy Grail of chicken has just been found by an unsuspecting reporter of the Chicago Tribune. Yes, that's right: The secret 11 herbs and spices in Colonel Sanders' Original Recipe chicken has finally been revealed, and it looks legit as hell.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

8-ball, or eight-ball is a challenging game, and it all starts with the rack. If you don't have the perfect eight-ball rack, your billiards game is going down the drain (not the pockets). But you can help yourself by learning how. Watch this video to learn how to rack eight-ball pool with professional pool player Borana Andoni, using the Delta-13 aerospace engineered pool rack.

Let's see a 3-D graphic being created using autocad. So the kids can learn to be engineers one day.

Building a robot in real life is not an easy task, and not usually accomplishable unless you have a degree in electrical engineering. But building one virtually on your computer is something almost anyone can do, if you know what program to use.

Hotels are anonymous and while this is a great thing, you should also be careful about the nameless folks who've used your room before you. Follow this tutorial to make the most of your hotel and ensure a great vacation experience.

If there ever was a day to eat green candy, St. Patrick's Day would be it. But is there something better than the banality of green candy swarming the streets on St. Patty's Day? Yes—glowing green candy, and Instructables user BrittLiv wants us to show you how it's done.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

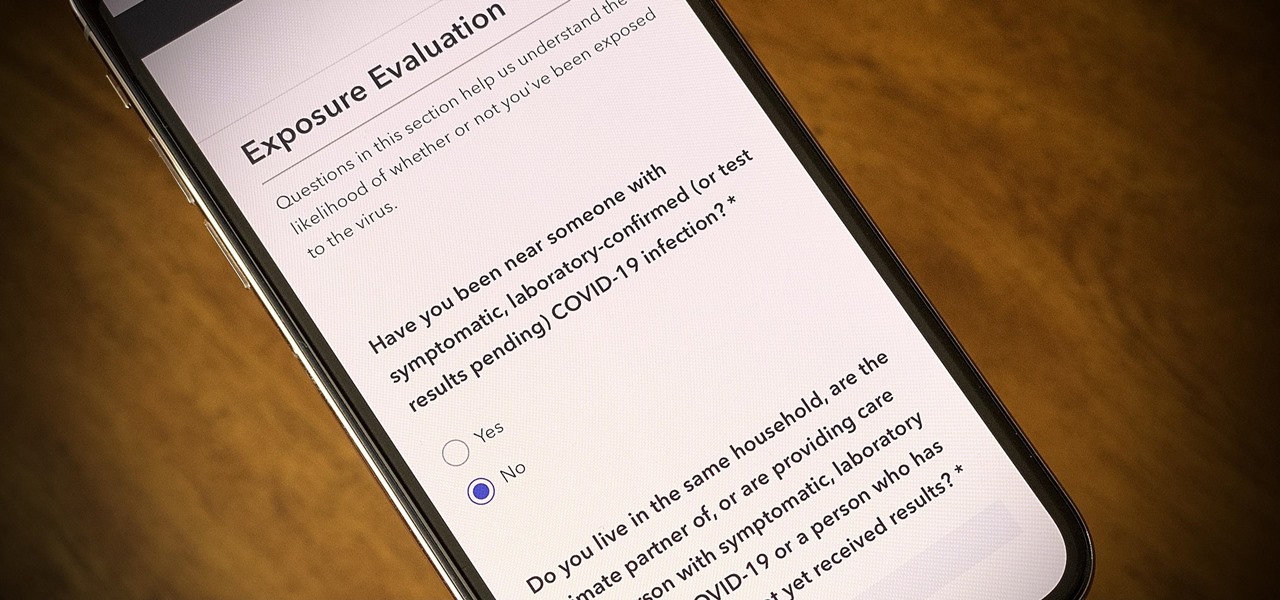
One of the scariest things about the COVID-19 virus is that you can show no symptoms but still be infected (and contagious). Naturally, we all want to know whether we're carrying the new coronavirus, but if you're showing signs of COVID-19, how can you be tested to know for sure? Websites are popping up to help with that, screening for symptoms, and directing you to a testing site if needed.

Smartglasses startup Nreal enjoyed some highs and endured some lows this week, as the company landed a product placement with Kevin Bacon but then faced production issues related to the coronavirus outbreak.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.