
News: Legionnaires' Risk Growing in NYC as Weather Warms
The number of Legionnaires' cases in New York over the last couple weeks has led to concern and recommendations of caution for those at risk.


The number of Legionnaires' cases in New York over the last couple weeks has led to concern and recommendations of caution for those at risk.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.
Mixed reality can give you the feeling that you've uncovered a hidden world layered into the physical one you already know. This can happen in so many ways, from a trading card that births a hologram or a first-person shooter with robots blasting through your walls. Xperiel—a California-based augmented and mixed reality company—wants to create a platform to make that a whole lot easier for developers.

It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

Gender standards are entirely pervasive. We raise our sons to be masculine and our daughters to be feminine, which perpetuates the gender role formula when they grow up to be parents and raise their own children. Part of this whole equation is that boys are supposed to remain stoic and project an air of strength, and girls are expected to be amiable while being held to unrealistic standards of outward beauty.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Back in March, Samsung partnered with Slacker Radio to create a streaming service called Milk Music. For those of us who don't own a Galaxy device, this news was a non-starter, as it was exclusive to Samsung's flagship line of phones and tablets.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

You may remember string art from your elementary school days. If so, it probably makes you think of the 2D geometrical designs that took every ounce of patience you had as a kid. Or those laborious curve stitch drawings, which string art was actually birthed from. But thanks to some innovative modern artists, string art has gotten a lot more interesting. Here are some of the most creative applications so far.

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

Giving birth is a joyful but difficult time for many pregnant women. Learn about the stages of labor with tips from a certified doula in this free pregnancy video.

This fast tutorial will show viewers the basics of how to use Facebook for those who are new to using the website. After creating an account and logging into Facebook, you will see your homepage, which has most of the new information regarding your friends and their recent activity. Clicking on the links at the top of the page will allow you to access pages such as your own profile, where you can display information about yourself, such as where you work or your date of birth. After watching ...

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.
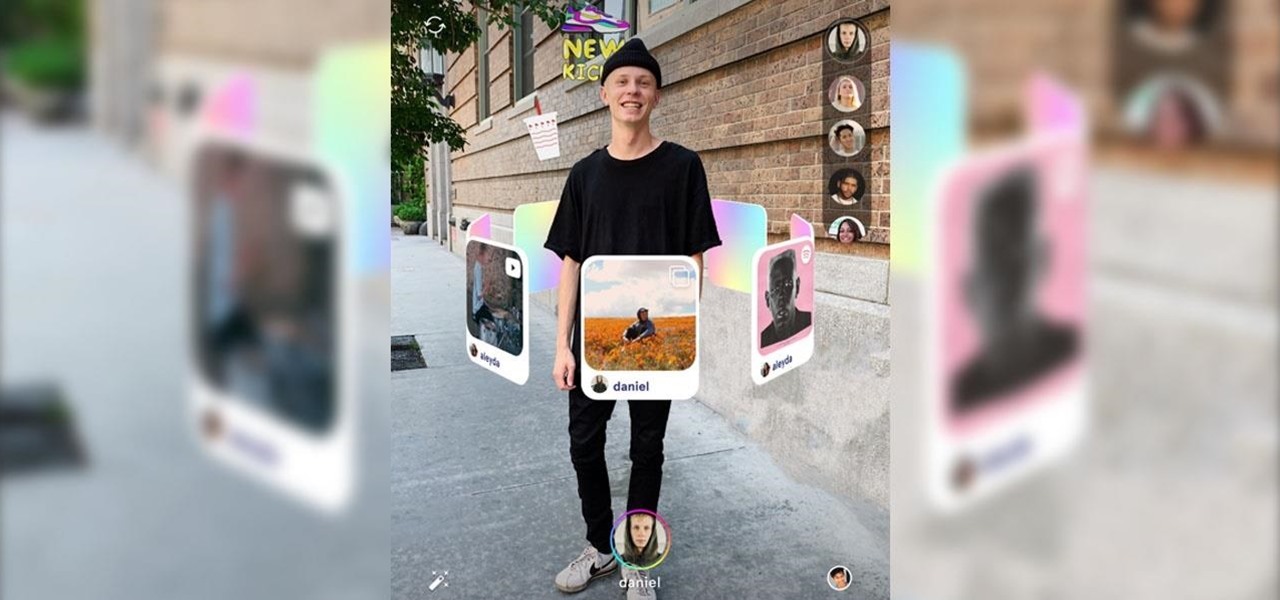
In a world full of augmented reality camera effects apps, one app is going in a more social direction.

We regret to inform you the former king of third-party keyboards, Swype, has officially retired on both Android and iOS. A few weeks ago, we noticed Swype's mysterious disappearance from the iOS App Store but had hoped it was just pulled temporarily, not gone forever. Unfortunately, Swype is no more, but there's something that's ready to take its place for you on your phone.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

US blood banks have assured the American public that they have the tools to prevent a Zika contamination, despite the rapid spread of the disease.

How can bacteria that lives in the throat of 10%–35% of people—without causing an infection—cause life-threatening meningitis and sepsis in others?

There has been an outbreak of syphilis in Oklahoma County with 75 confirmed cases connected by a social network driven by drug use and sex.

Pokémon GO, the biggest augmented reality sensation ever, broke app store records this opening weekend. But it also did something even more important: it gamified physical activity.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Not to be outdone by the announcements of Mac OS X El Capitan and iOS 9, the Apple Watch is also getting a much needed software update. Some of the notable new features we can look forward to on watchOS 2 are Nightstand mode, additional screens for friends, email replies, and other improvements we probably should have already had.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

Starting April 10th, you'll will be able to book 15-minute appointments online to try on an Apple Watch in person at Apple Stores across the world. With the April 24th release date just around the corner, making an appointment is a great idea for those who are unsure about which color and size to purchase—or if they'll even want one.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

Text adventure games, such as the well-known Zork series, were some of the first computer games ever made, second only to the likes of Spacewar! and the better-known Pong. So let's travel back in time for a moment, to a time that never was.

This most recent school shooting, one of the worst in history, has devastated our country. That such an act can be performed not by a begrudged child, but by one or more adults, is nearly unthinkable.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

Hello and welcome to my post. I would like to share a few things I have picked up along the way - while feeding my two dwarf rabbits. In this tutorial I would like to answer the question - How to choose the best food for your rabbit?
Hello! I invite all the readers, interested in space, to discover the origin of the names of the planets in our galaxy. Just simply follow my words,... Step 1: Planets and Stars