If you don't want to dress up as a vampire, witch, werewolf, or zombie again this Halloween, step things up a notch and go viral. There have been a ton of funny memes and absurd news since last October, so the only hard part is settling on the right one for inspiration for your costume.

Microsoft recently released "Seeing AI," an app aimed to help the blind understand their surroundings. As Microsoft puts it, "the app narrates the world around you by turning the visual world into an audible experience."

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Have you ever admired those individuals that get so much accomplished in a day and wonder how the heck they do it? Now's your chance to learn their secrets. The Productivity & Motivation Master Class Bundle brings you everything you need to life-hack your way into leading a more productive lifestyle at home and work.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

Media subscriptions are all the rage these days. Between Netflix, Apple Music, HBO Now, and countless more, your TV, movie, and music options have never been better. Unfortunately, all these choices weigh heavily on your wallet. So, when there's an opportunity to snag not just Spotify but Hulu and Showtime as well, all for just a tad bit over five dollars a month, how could you turn that down?

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

Foodborne infections often occur through the contamination of equipment, food-prep tools, and unsanitary surfaces. A recent report from the Centers for Disease Control and Prevention (CDC) reminds us that breast pump parts are part of the food-delivery chain — and they can become contaminated too.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Breastfeeding is the ultimate in farm-to-table dining. It is sustenance prepared just for the baby and delivered with a very personal touch. Along with bonding, breastfeeding provides powerful protection to infants and young children in the form of beneficial bacteria, hormones, vitamins, protein, sugar, and antibodies manufactured on site to support infant health.

Colorado State University scientists have developed new tech that quickly identifies the presence of Zika virus in mosquito populations — and in human body fluid.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

An advance in the race to stop birth defects caused by Zika-infected mothers has been made by a team of researchers from Rensselaer Polytechnic Institute in Troy, New York. They have identified the process Zika uses to gain entry into the placenta, and published their findings in the journal Biochemistry.

Most females have had at least one urinary tract infection in their lifetimes. Recurrent UTIs are particularly problematic in young, sexually active women, where about 80% of the infections are caused by the bacteria Escherichia coli, better known as E. coli.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

Even if your cat drives you a little nuts, don't worry, because a new study says that cats pose no risk to your mental health.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

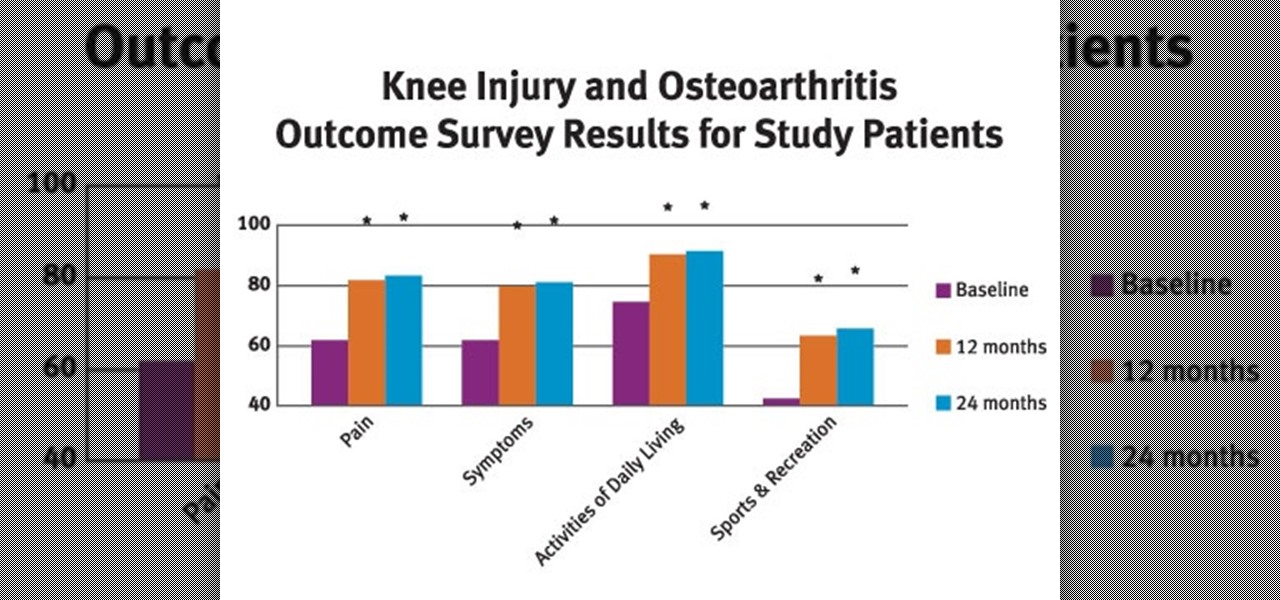
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis.

Broccoli is super. Not only is it jam-packed with nutrients like vitamin C, vitamin A, folic acid, calcium and fibre, but it's one veggie that refuses to be just a side-dish. Nobody puts broccoli in the corner.

Nintendo fans rejoice! Not only can you play classic NES games on your iPad or iPhone without jailbreaking, you can play Game Boy Advance and Game Boy Color games. And that's not it. Now, thanks to @angelXwind, we can add Nintendo DS to our list of non-jailbreak emulators for iOS 7.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

Religion is one of the most-ignored topics when it comes to Steampunk, which is surprising given how important religion was in Victorian England. Even the hot-button issues of race and gender are confronted with a greater awareness than religion.

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

If you're using a VPN-based ad blocker with full HTTPS functionality on a Samsung phone, you'll get a notification informing you there's a third-party security certificate in use. No big deal, except it shows up every time you restart the phone. Samsung isn't alone in this type of annoyance, either.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

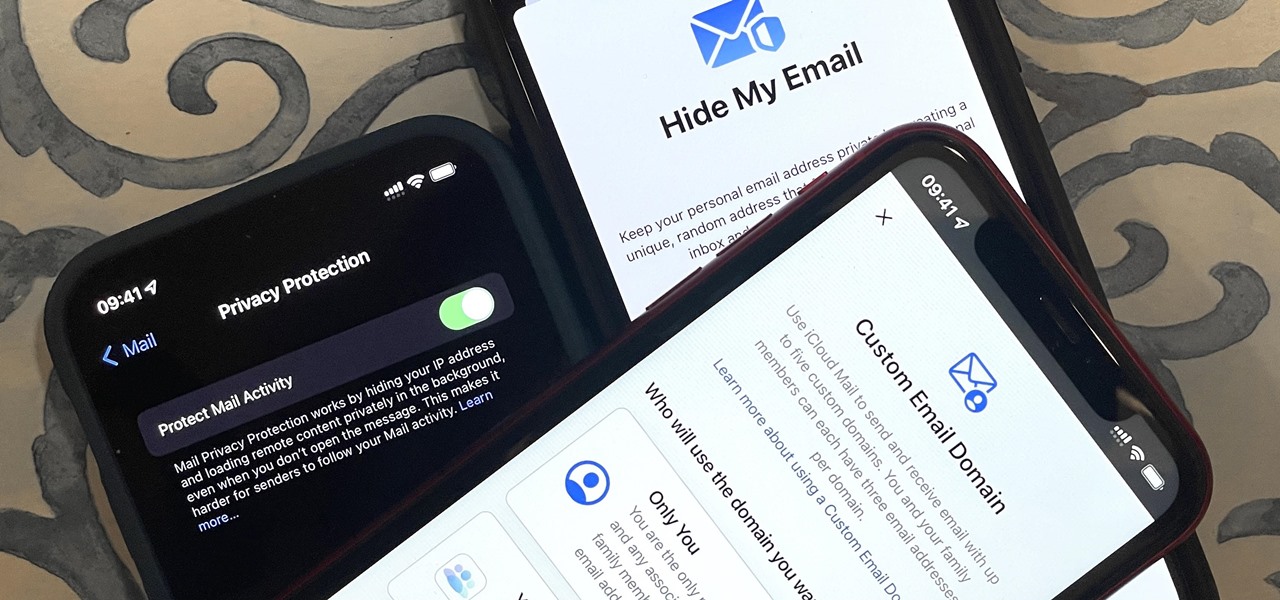
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

We all know IT development is a valuable skill to have. But being a certified professional in the world's most in-demand project management and development tools? That's enough to get the promotion or new developer career you've been dreaming about.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.