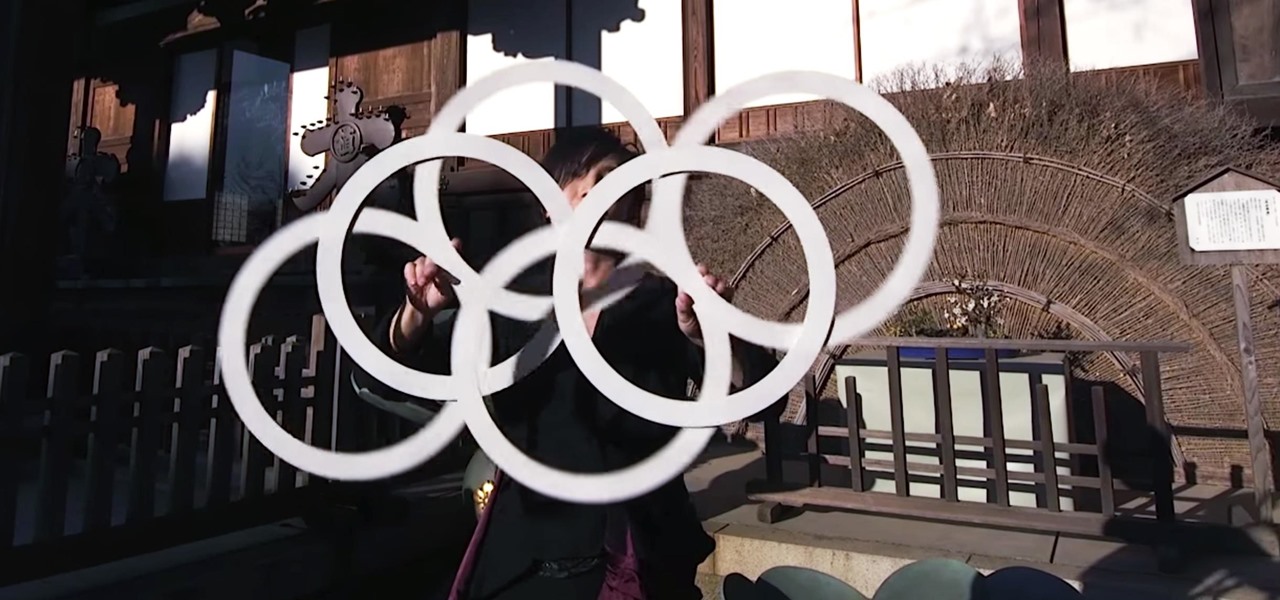
News: Ouka's Hypnotic Performance with Optical Illusion Rings Is Mesmerizing
Heads up: the following videos and GIFs will definitely cause you to zone out and lose focus on whatever it is you're doing.

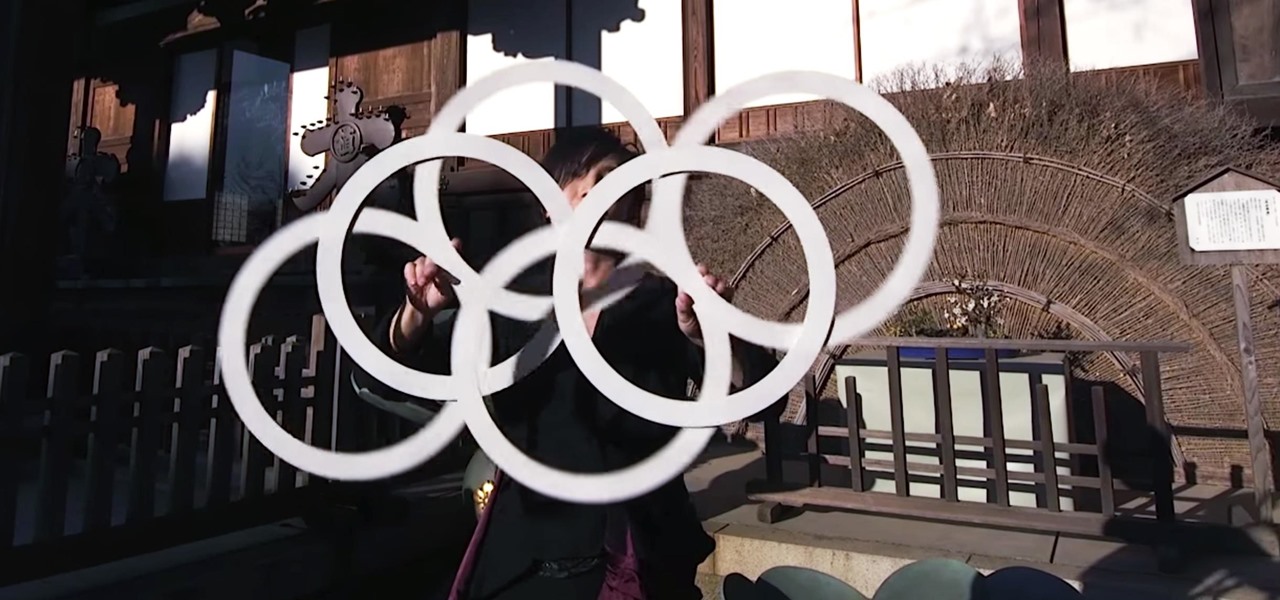
Heads up: the following videos and GIFs will definitely cause you to zone out and lose focus on whatever it is you're doing.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can use to make some educated guesses regarding Apple's upcoming flagship.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

No doubt you internet-savvy folks have seen the incredibly beautiful rainbow bagel going viral all over the country—and if not, let me educate you on its multicolored brilliance. Crafted by the brilliant bakers at The Bagel Store in Brooklyn, this cheery creation has actually been around for 20 years now. Watch the video below to see how the colorful roll is created.

Whether you're ready to admit it or not, we've all got our alter egos—especially when it comes to the internet. Perhaps you have one Facebook account that you use publicly, while maintaining a second account for more private interactions.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.
Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

I'm not a big fan of single-use tools, especially ones that don't get used particularly often. And I'm especially not a big fan of seldom used single-use tools that take up a large amount of space.
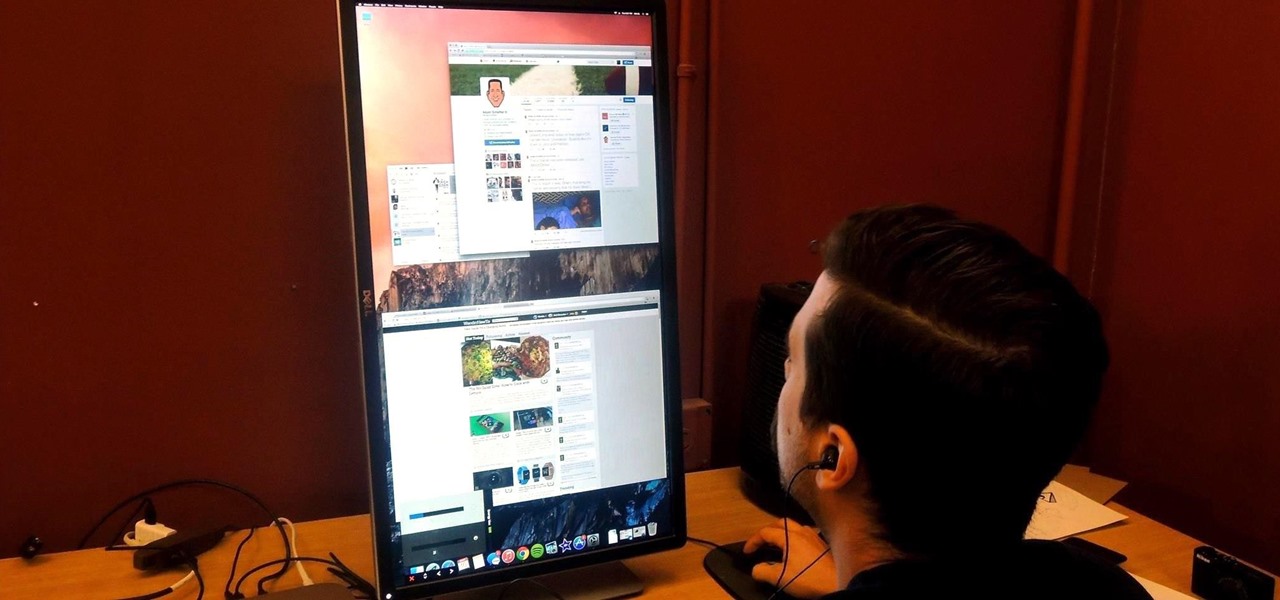
If you've got a desktop computer, I can almost guarantee that you've got a widescreen monitor set up in landscape mode. It's how just about everyone uses their monitor these days, including myself. Except that it's not always the best way of working.

When installing flashable ZIPs and custom ROMs, we always hear the same old adage: "Make a full NANDroid backup first." Trouble with this is that you don't always need an entire system backup, since many mods only apply to specific folders on your device. And while custom recovery software like TWRP will let you select from a few individual partitions to back up, every system mounting point is not always included among the options.

When Android 5.0 rolls out to the Nexus 5, several changes and new features will come along with it. The over-the-air update is already rolling out, and if you don't want to wait, you can get it right now.
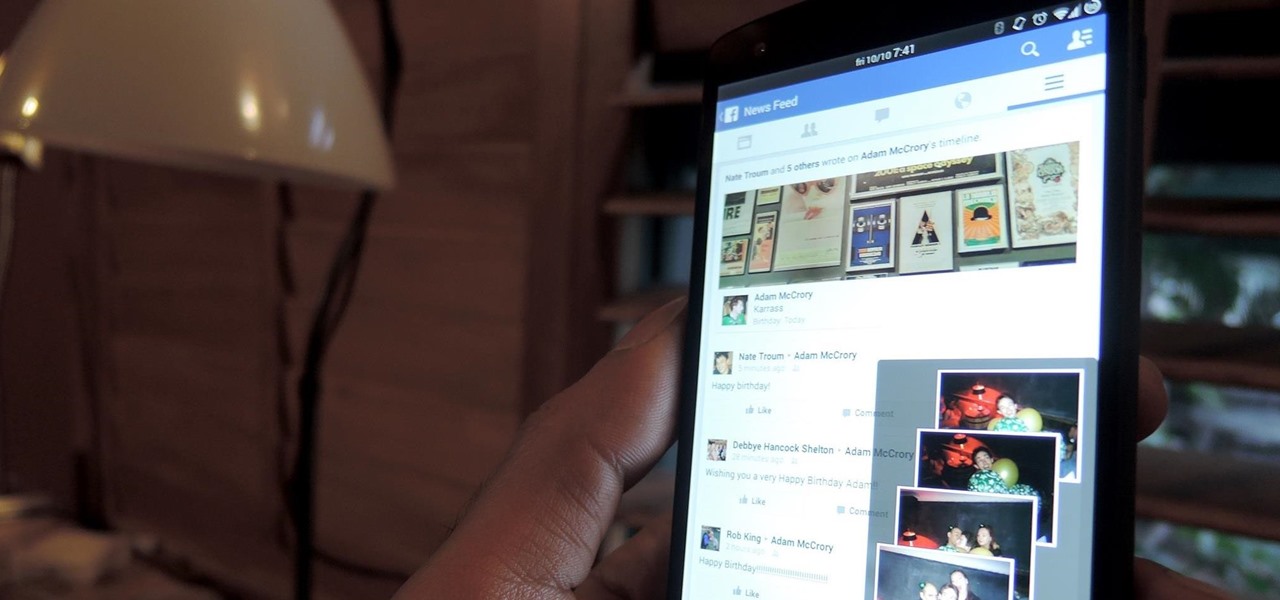
Multitasking is useful in pretty much all walks of life. Being able to do two things at once is better than just doing one thing... who would've thought. When it come to multitasking on my phone, I am constantly jumping between apps—whether it's browsing Facebook while looking at pictures to post or reading my Twitter timeline while keeping up on sports scores.

When Google released Android 4.2, a new feature was introduced for tablets that allowed for multiple accounts to be used on a single device. In order to create a unique experience for each user, apps and personal data were kept separate, and switching between users became as simple as tapping your profile photo from the lock screen.

Samsung catches a lot of flak for all of the "bloatware" it preinstalls on its Galaxy line of devices. Many users complain that "TouchWiz," Samsung's custom Android skin, causes lag with its overabundance of features. But some of these features can actually be pretty handy, like Multi-Window Mode or Milk Music.

After lots of anticipation and leaks, the LG G3 has been unveiled. Sporting a gorgeous 5.5" Quad HD display, the first of its class for smartphones, this flagship device is ready to put some scare into Samsung and HTC. It's currently available for purchase from AT&T and Sprint, and for preorder at T-Mobile and Verizon Wireless.
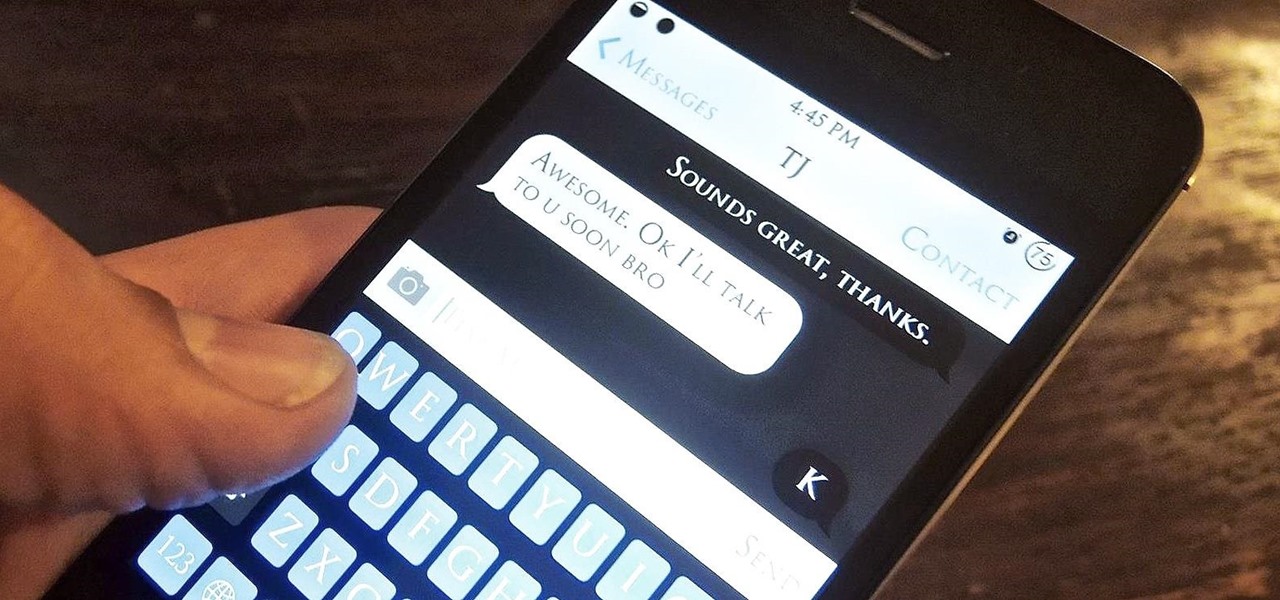
WhatsApp may be one of the most popular mobile messaging services around since it's multi-platform, but if most of your family and friends use iPads and iPhones, there's no need to go beyond the stock Messages app.
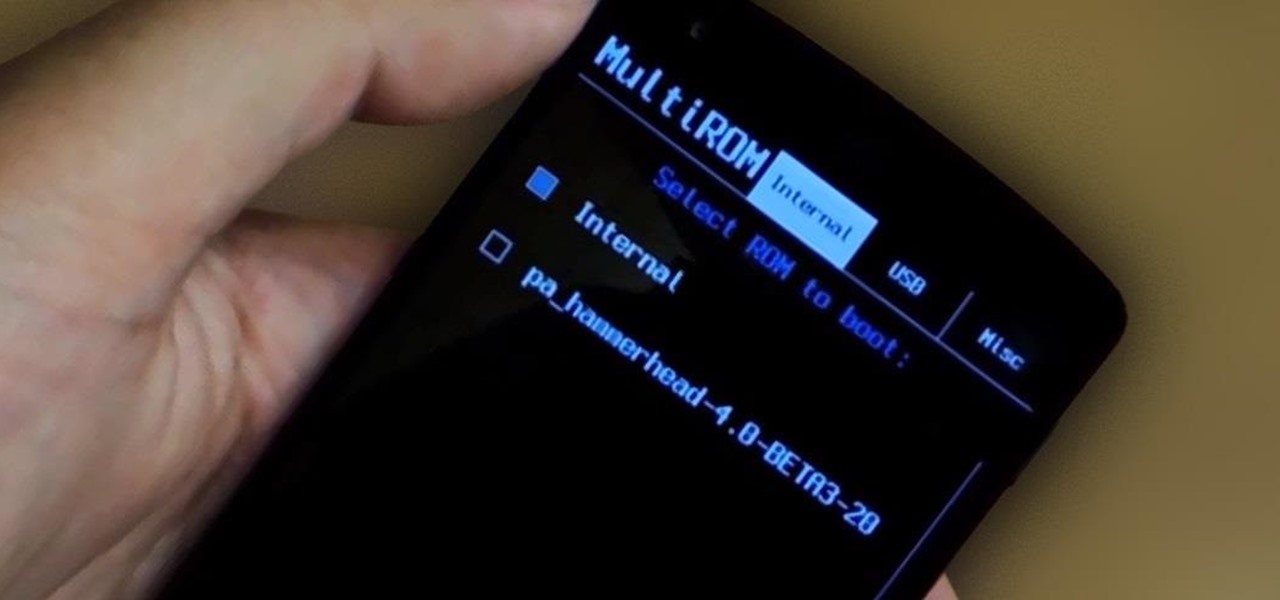
When you enter the softModder realm by rooting your Nexus 5, you open up an exciting world of possibilities and deep customizations for your device. Among other things, it gives you the ability to flash custom ROMs which, individually, act as entirely different operating systems that can vastly alter your user experience.
As things begin to clutter on your device, navigating through it can become much more difficult than when you first got it. The sheer number of added apps and mods that build up after time take its toll not only on the quickness and memory of your device, but also on your efficiency to access everything easily.

This easily installed fender-mount towing mirror is perfect for a multi-vehicle owner with its easily adjustable arms and no tool installation.
While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

in brief:
There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

In the last couple of days there's been a lot of speculation about the powers of Microsoft's HoloLens 2, but few have had a chance to get their hands on one to see if the company's claims live up to what HoloLens inventor Alex Kipman showed off on stage.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

Red Dead Redemption is hard to pin down in game play and story. The game offers this massive multi-layered world in which the player can roam freely, offering plenty of challenges, beautiful graphics and atmosphere for the player to experience. Yet after some point the whole world feels barren and unchangeable, and your achievements are nothing more than a trophy that does not matter in the sandbox world the player resides in. The story, told in three arcs, offers an inconsistent narrative of...

Game categories v3 plug-in is a must have plug-in for PSP users and this video shows how to install it. Using this plug-in, you will be able to put your home files, games, applications and all other stuff organized in sub-folders under "Game folder". The plug-in has two modes. The first mode is Muti-MS mode and the second one is Pre-Game-Menu mode. The Multi-MS mode makes a separate memory stick icon pop up for each category you have and choosing one can enter the appropriate category. There ...

Self-recording and mixing music today is easier than ever with programs such as Apple's Logic Pro 8. Mix any piece of multi-track music easily and quickly with tips from an experienced studio engineer in these free recording videos.

Learn how to play the Melodica in this free music lesson video from a professional multi-instrument musician.

There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer security, networking, software development, testing, and so on...It's probably a bit premature to decide what you want your speciality to be, but keeping the question in the back of your mind will help give you direction in ...

Zynga just added another game to their Zynga with Friends series called Scramble with Friends. If you've ever played Boggle, it's basically the same thing, but is dedicated to playing your buddies just like Words with Friends or Hanging with Friends.

Google+ is taking over more and more of Google's core properties. This week, we've seen several announcements from Google blogs about new products, new features, new looks, new integrations. If you're like me, you actually want to know where to go for all the latest information on Google products.

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?