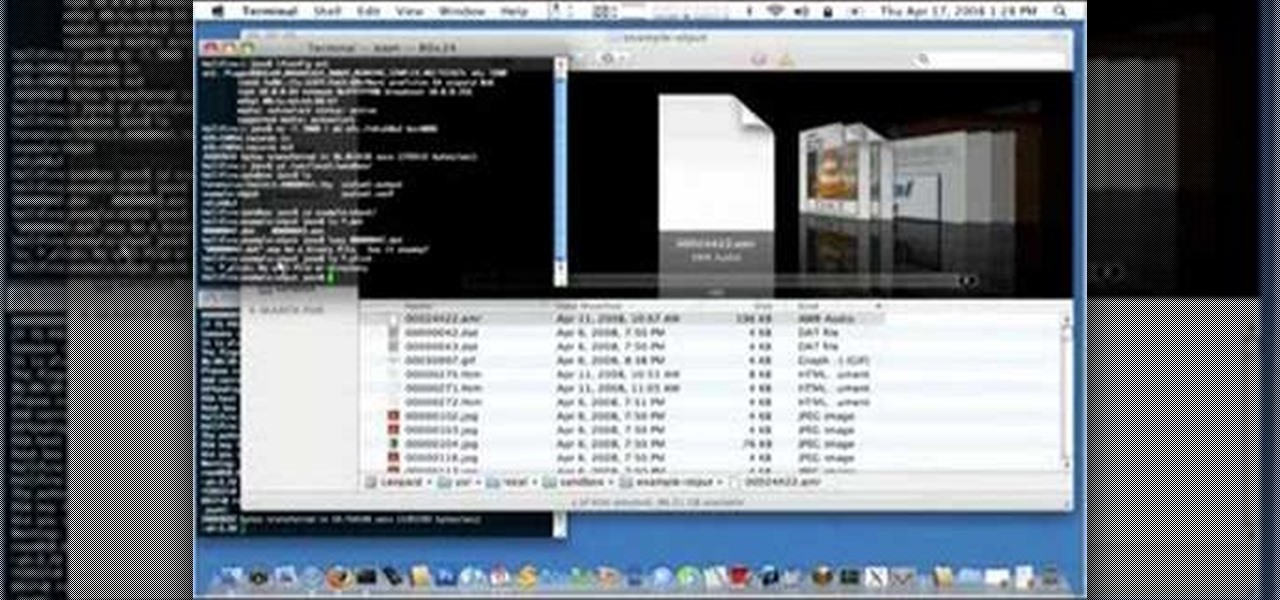
In this video one of the ultimate iPhone hackers, Jonathan A. Zdziarsk, demonstrates how to use a forensics toolkit to recover deleted text messages on an iPhone. But wait - there's more! Not only can you access text messages, but almost any other data on an iPhone as well. We can't be responsible for what you find though!
In this two-part video, learn how to jailbreak an iPhone, iPod, or iTouch 3.1.2 with help from computer whiz, Black Rain. In order to complete this jailbreak, you will need Cydia and web access to visit www.blackra1n.com.
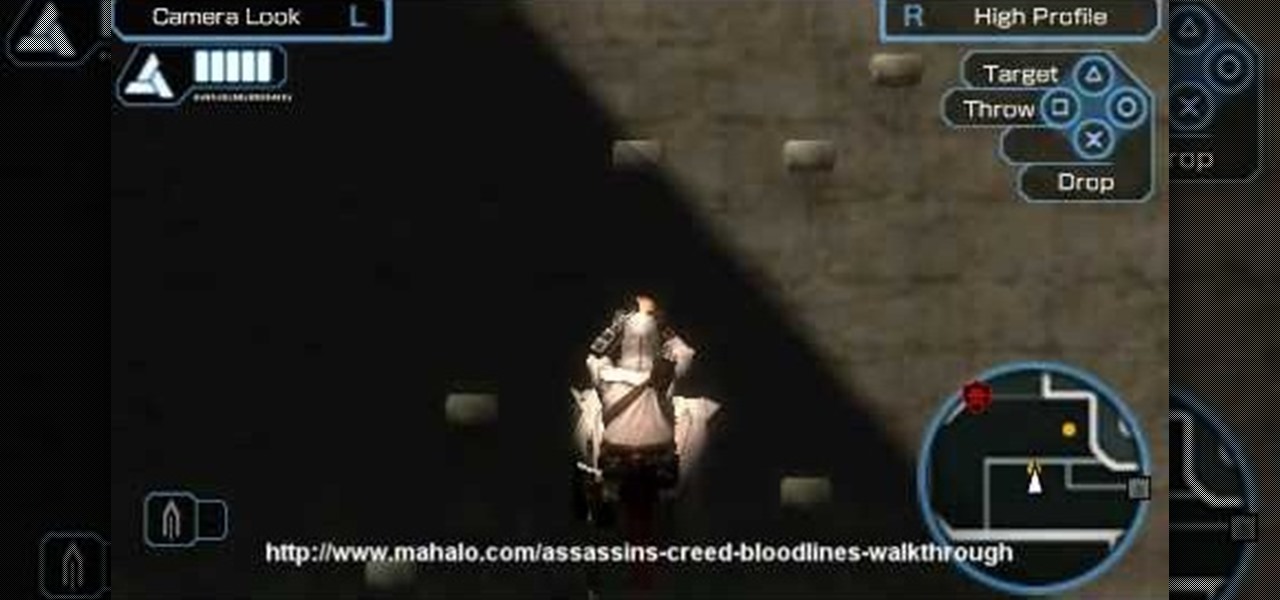
See how to infiltrate the Limassol Castle and kill Frederick "The Red" in Mission 6 on the Sony PSP. Guards patrol almost every corner of the Limassol Castle Courtyard, and soldiers armed with sturdy-looking shields block the normal route into the castle. Looks like you will have to find an alternate way. That path reveals itself quickly enough in the form of protruding pieces of bricks along the wall, allowing Altair to gain suitable height above the ground. Jump on the merchant stand roof f...
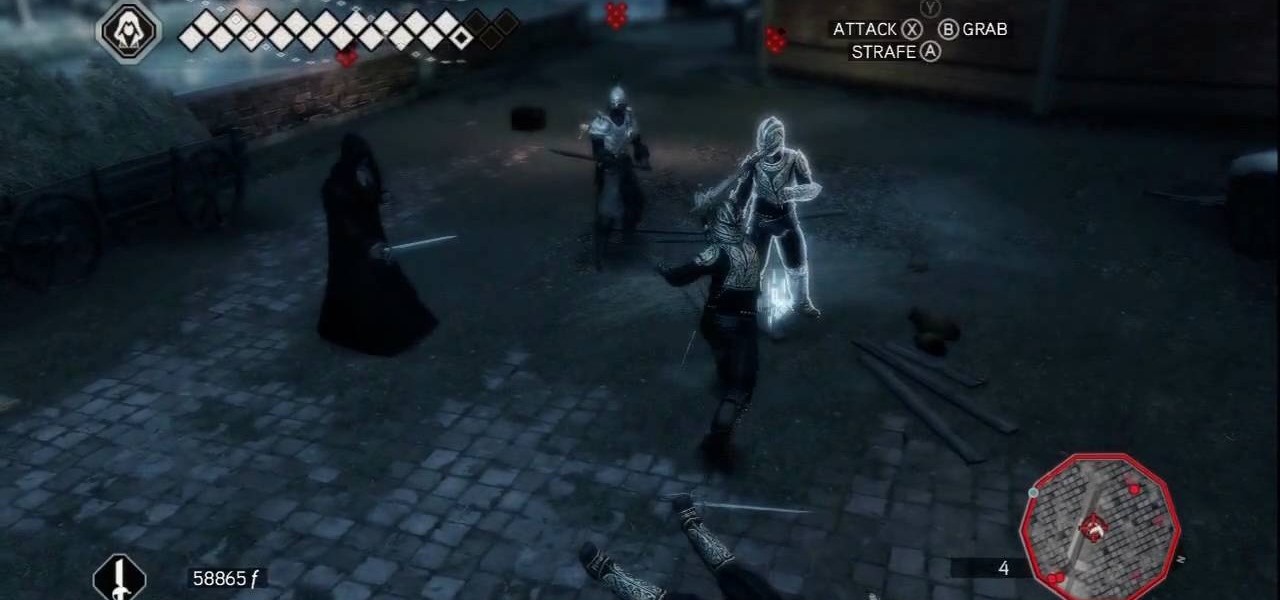
Play Along: At the start of the mission, you simply need to follow the leader through the city. Do your best not to bump into anyone, as Ezio will drop the chest if you do. Eventually, you read the end of the trail and a cut scene takes over.

Cleaning House: This mission just might be the best one of all. Talk to Antonio, the head of the thieves guild and you'll at first get a cut scene and a memory sync, without having to do anything. Talk to him again, however, and you'll get a mission to identify and kill some traitors. The nearest traitor is in an area just north of you, so head toward the green area on your map.

Arivederci: Or is that Arrivederci? This mission won't take long. As long as your notoriety is at zero (and it has to be), this mission is a piece of cake. You have to escort Ezio's mother and sister across town to the city's exit. The city is temporarily packed with guards, but they'll pay you no mind, even if you run. Just avoid bumping into guards and you'll be a-okay.

Family Heirloom: Find the precious family peice passed down generation to generation. Go back to Giovanni's room and use eagle vision to locate the hidden door. Okay, it's not really very hidden. Open the door and step into the secret room. Open up the chest inside to get a snazzy new outfit, plus a useful sword.

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Learn how to teach your dog to high-five. Make your pooch the hippest dog on the block by teaching him how to greet you with a high-five.

Lure luck your way at your workplace by arranging things according to the ancient Chinese design philosophy known as feng shui. De-clutter your desk and workspace, which is the most important thing you can do to balance the _chi_—or energy—in your office. Repair or get rid of anything that’s broken—like a pen that’s out of ink or a flickering desk lamp. They block your chi. The placement of your desk and chair should allow you to see who’s coming into the room. Business and opportunity symbol...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

Whether it's a small business or a work group inside a large corporation, all members need access to the same materials in order to work effectively. Mac OS X server makes it easy for groups to collaborate and communicate through their own Wiki-powered Internet website. To learn how to use Wiki Server with Mac OS X Server, watch this video tutorial.

In this tutorial Lindsay Adler will teach you how to add makeup to your models in Photoshop. Sometimes you do not have access to a makeup artist, or after the shoot decide you want a splash of color. Lindsay will teach you to add makeup in a few quick steps in Photoshop.

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

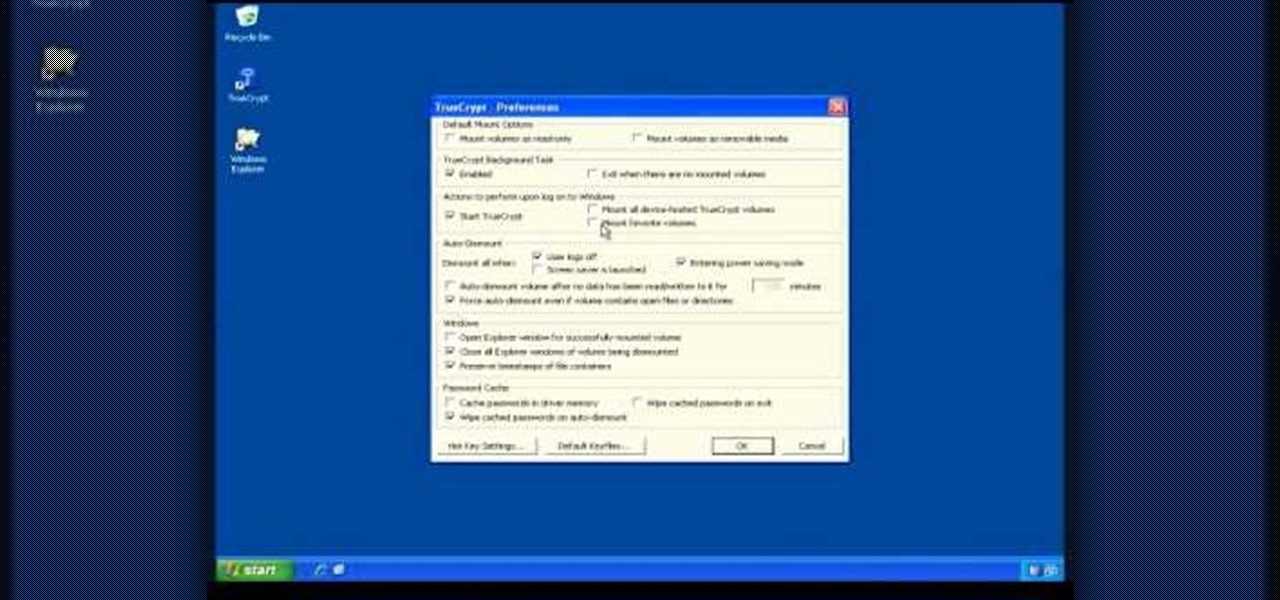
How to use or mount a TrueCrypt volume to access the data that you have encrypted with the program.

Third-party apps on your iPhone must ask for your permission to access your library in the Music app. Some will even want to get access to your Apple Music account. If you no longer use the apps, you shouldn't be letting them have access anymore. It's easy to hunt them down, and doing so might even show some apps you can't even remember giving any permissions to.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

When Apple acquired the popular Workflow app in 2017, many were worried that it would either get replaced with something much worse, or just disappear entirely. Thankfully, Apple put these concerns to rest with the launch of Shortcuts. In iOS 13, Shortcuts is becoming more powerful than ever, providing functionality on the iPhone that the original Workflow team could only dream of.

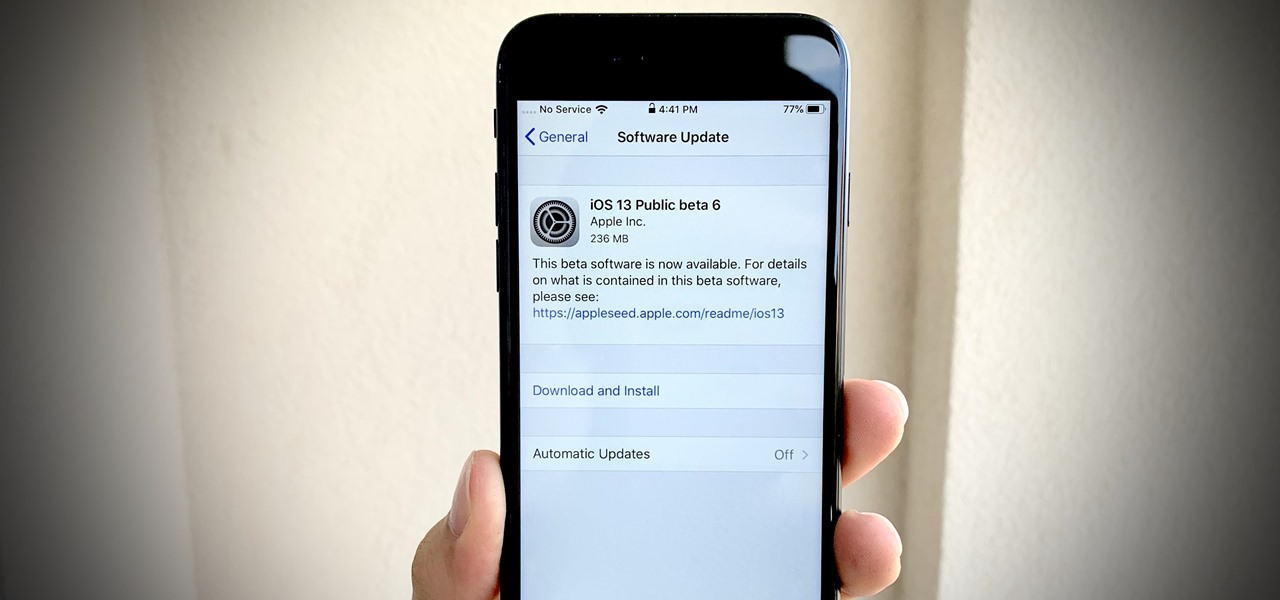
Apple dropped the sixth public beta for iOS 13 today, Aug. 15. This public update comes just hours after the release of developer beta 7, an interesting move for Apple. The company has recently stuck to a schedule of seeding the public beta at least one day after the developer beta, presumably to weed out any debilitating bugs that might have gone unnoticed.

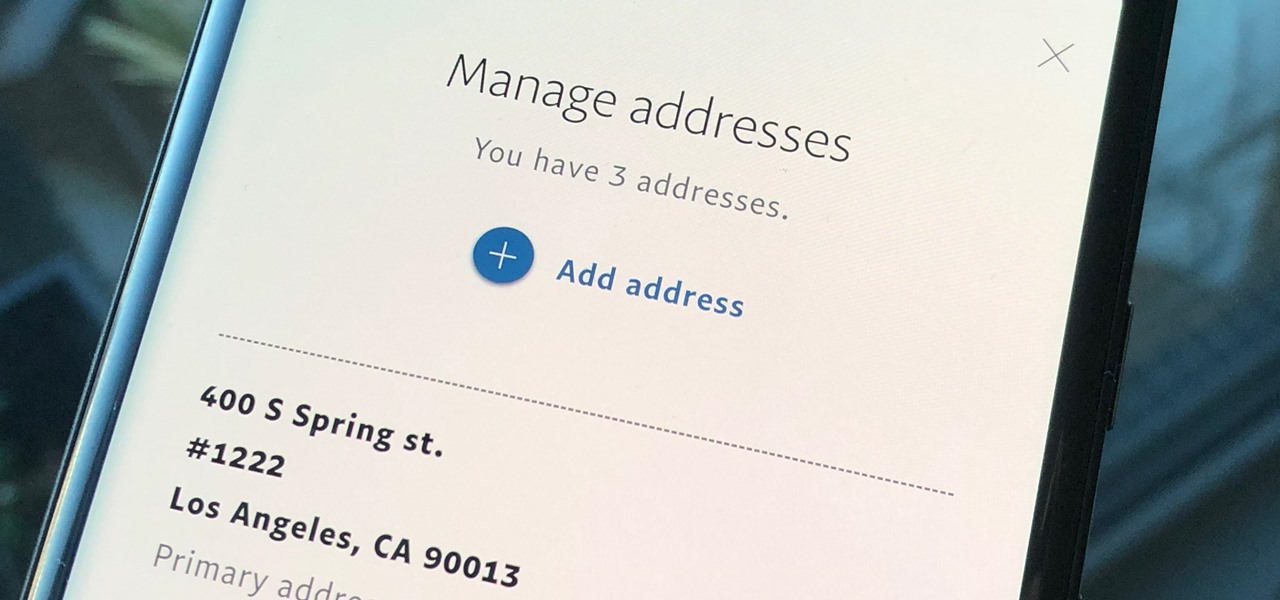
Whenever you move into a new home, whether that's a house or apartment, changing addresses on all your online accounts is one of the most monotonous tasks that needs to be done. It's even more tedious when you have to update both shipping and billing addresses. But it's necessary, and if you regularly use PayPal, it'll be one of the first places you'll want to update.

By now, there's no way you haven't stumbled upon a TikTok video, whether it was on Facebook, Instagram, Twitter, or YouTube. Just watching these addictive short-form videos is enough to make you want to join up and make your own, and when you do, we've got some tips that will help get your TikTok account in order.

On Thursday, Mojo Vision, a startup comprised of former engineers from Apple, Amazon, Google, and other Silicon Valley mainstays, emerged from stealth backed by $50 million in funding for a hands-free augmented reality platform that runs without smartphones, tablets, or other devices.

Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. Fortunately, some of you can fix this.

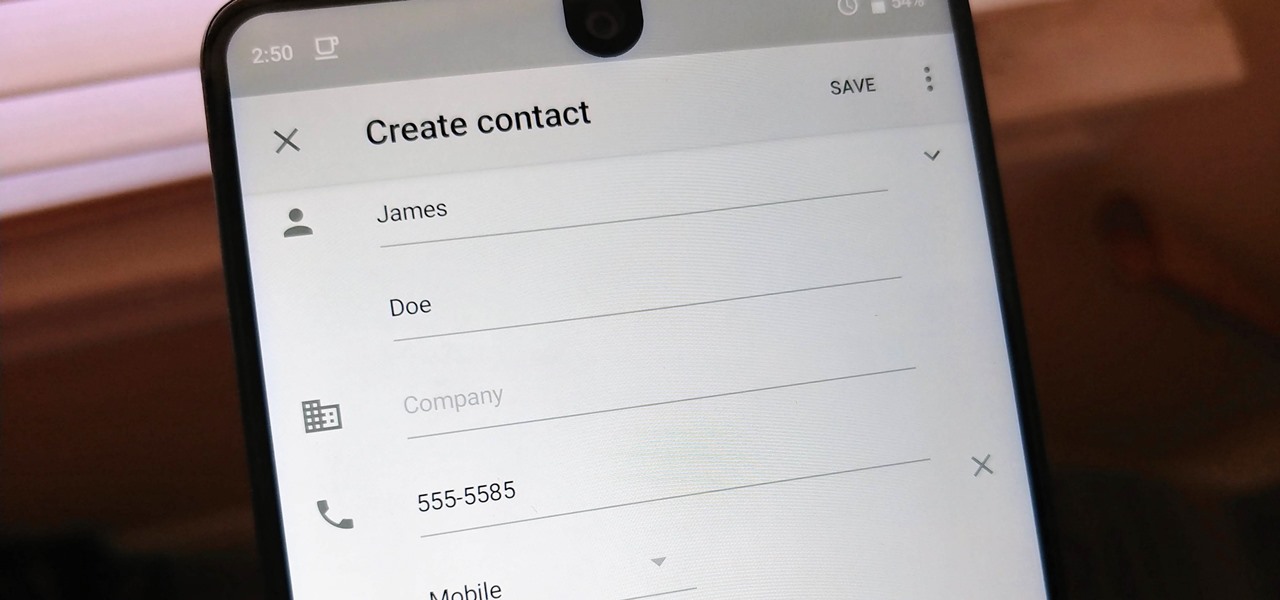
Android lets you sync your contacts across devices. The OS will use not only contacts saved on your phone, but also your Gmail. This choice can lead to a contacts list populated with entries that don't have a phone number, which can quickly add up. To mitigate this problem, there are a few methods.

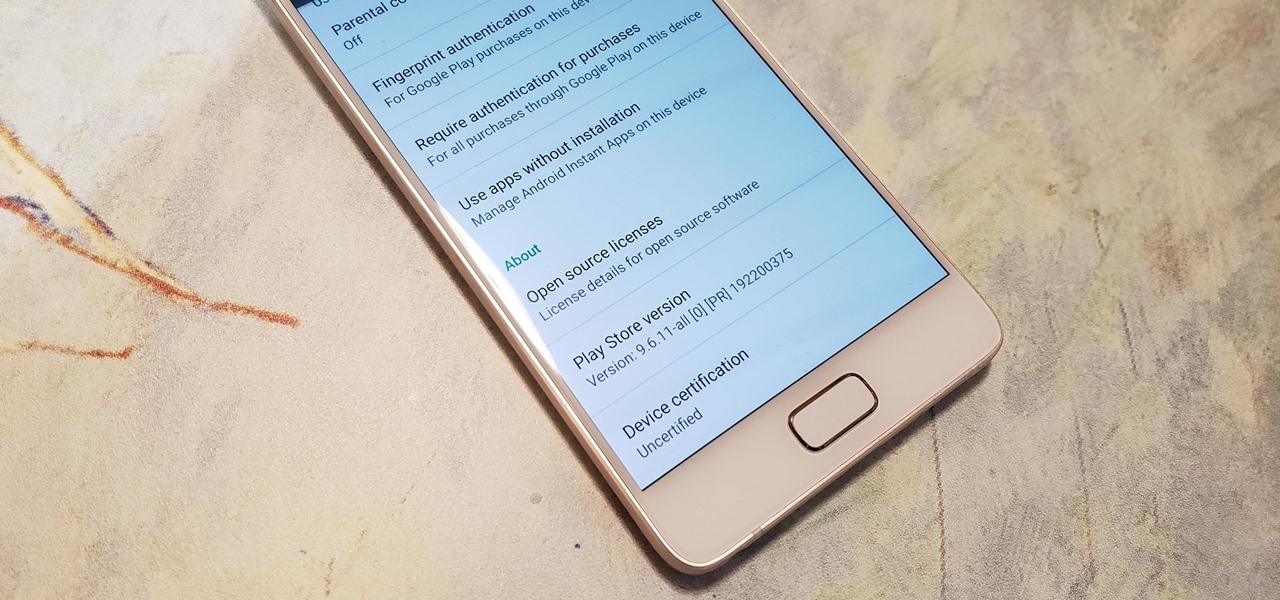
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.

While some of our group chats should probably remain private and closed off, others will only get better with more people. Whether you're organizing an event and need a headcount or you want to share a funny YouTube video with a large crowd, you can add all the friends you wish to on Facebook Messenger by sending them a unique link.

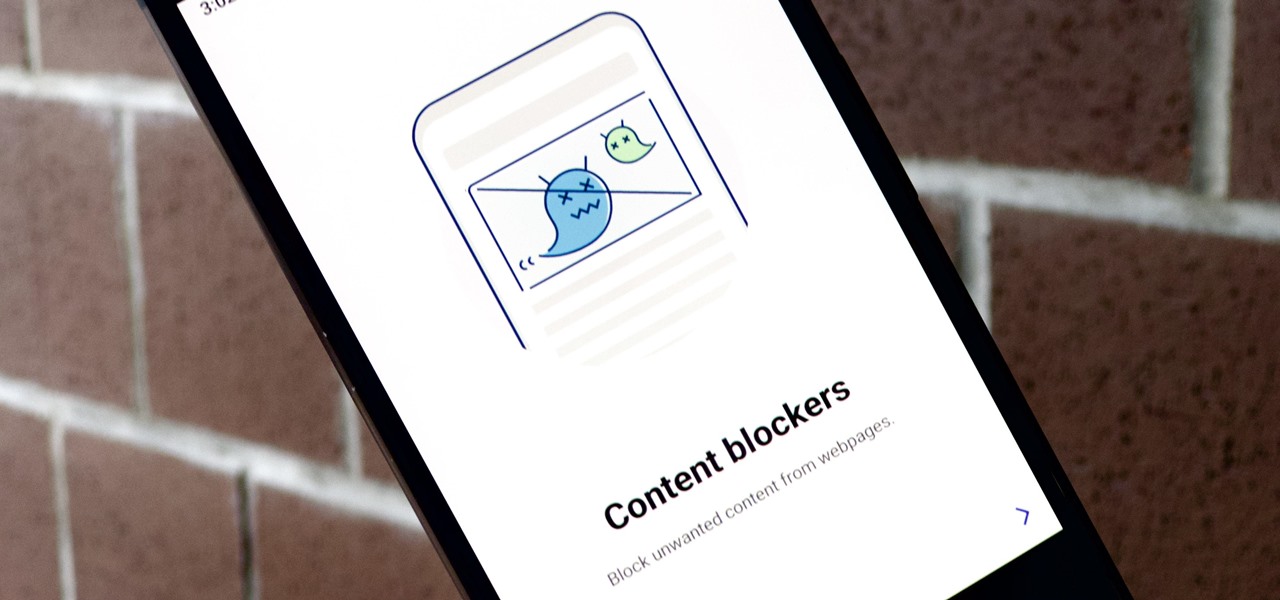
Samsung Internet offers excellent features that enhance the mobile web browsing experience, often through its extensions. A QR code scanner, ad blockers, tracker blockers, and more work directly in the browser, so you can do exactly what you want to do on the web.

With the S9 and S9+ upon us, you maybe wondering if it's time to retire your aging Galaxy and either sell it or do a trade-in to get Samsung's latest flagship. Before you do, however, it's important to make sure that all its components — most notably the sensors — are working fully in order to avoid potential headaches.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.