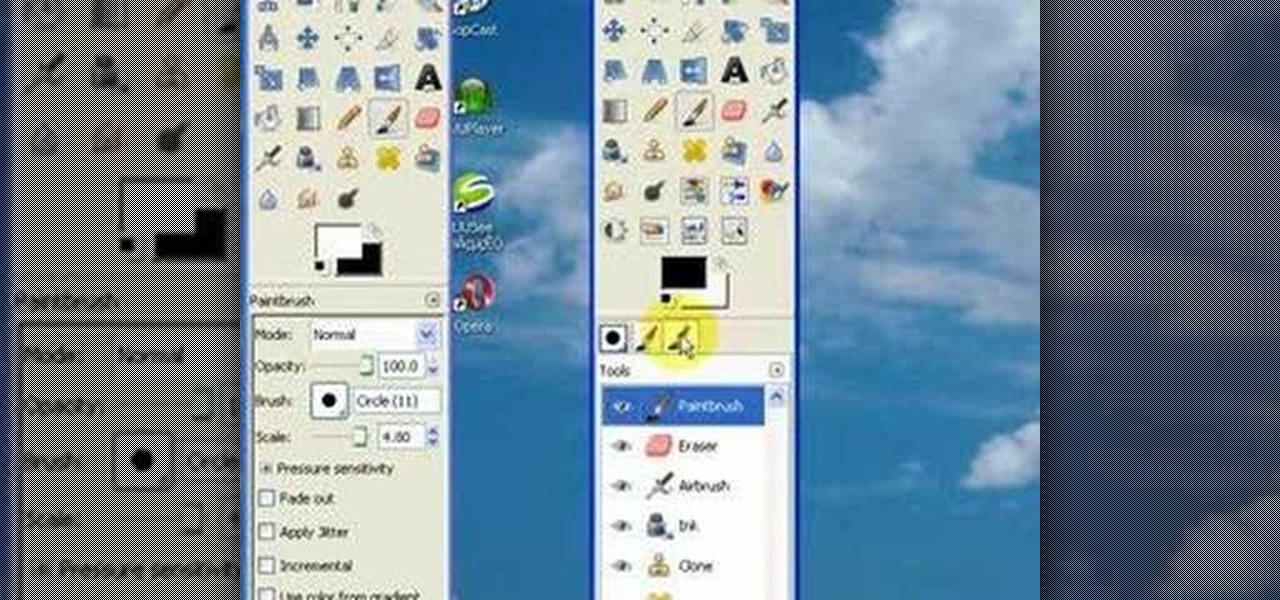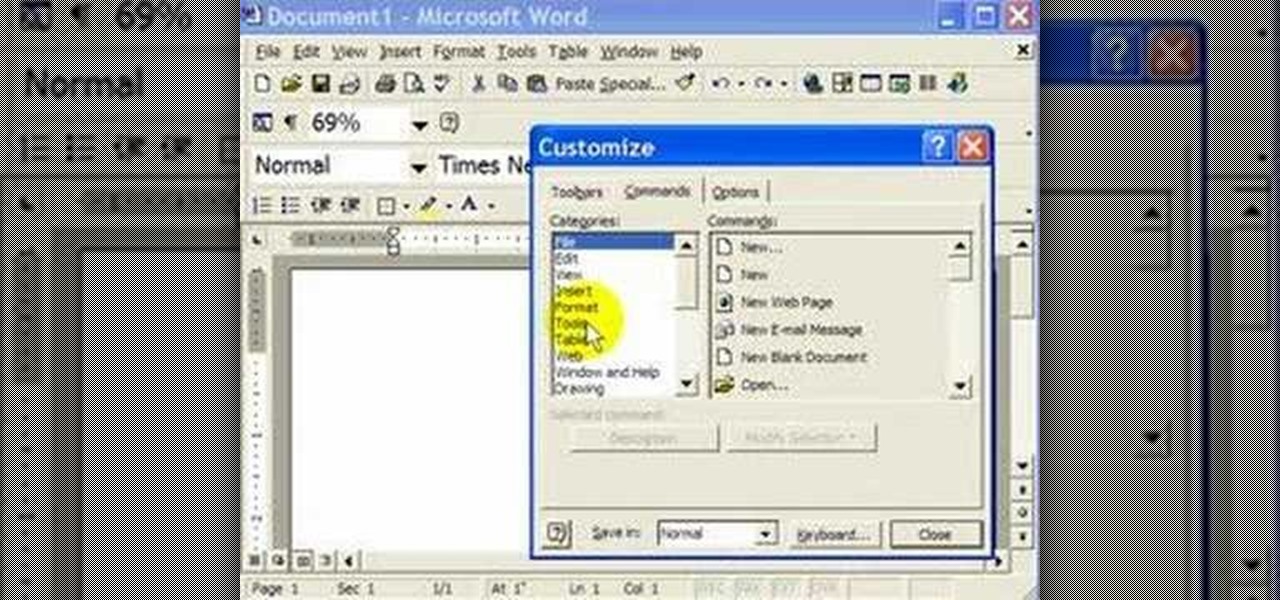
Interested in creating a quick print envelope button in your word processor? With this video tip, you'll learn how to create a quick print button for access to envelope printing in Microsoft Word 2007, previous versions of Microsoft Word and OpenOffice Writer. For more, and to learn how to set up your own quick print button, take a look!
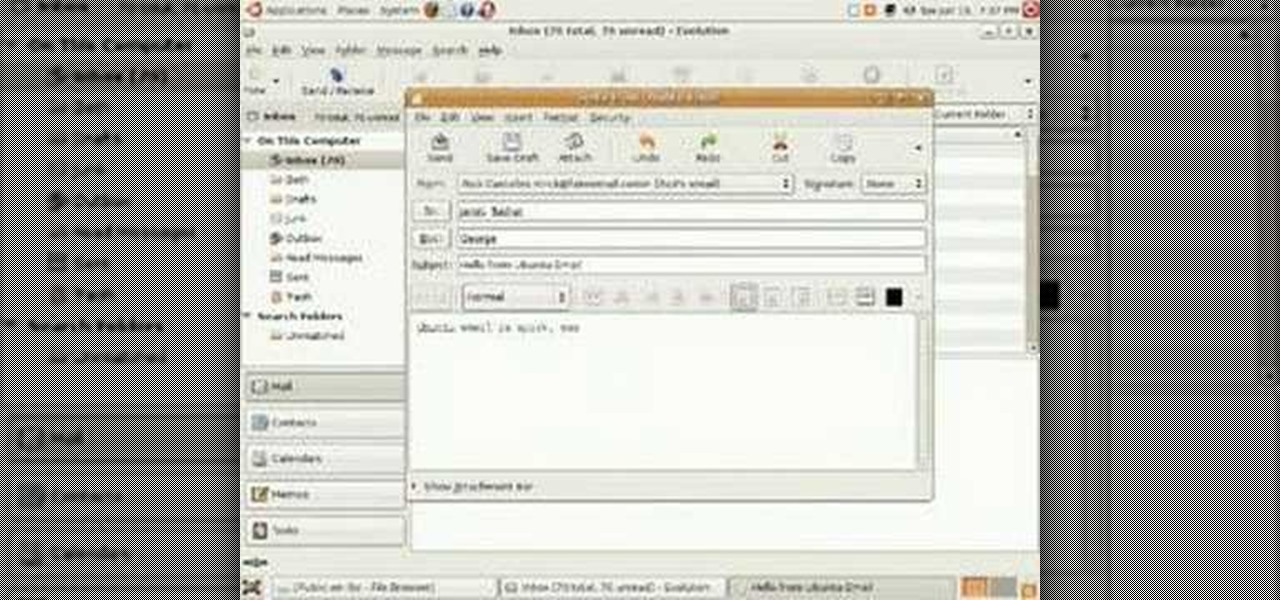
Sending email with the Evolution client in Ubuntu Linux is much the same as with any other email program. In addition to offering step-by-step instructions for the setup and use of Evolution, this Ubuntu tutorial also will teach you how to access your address book when writing an email. For a detailed look at the Evolution email client, take a look!
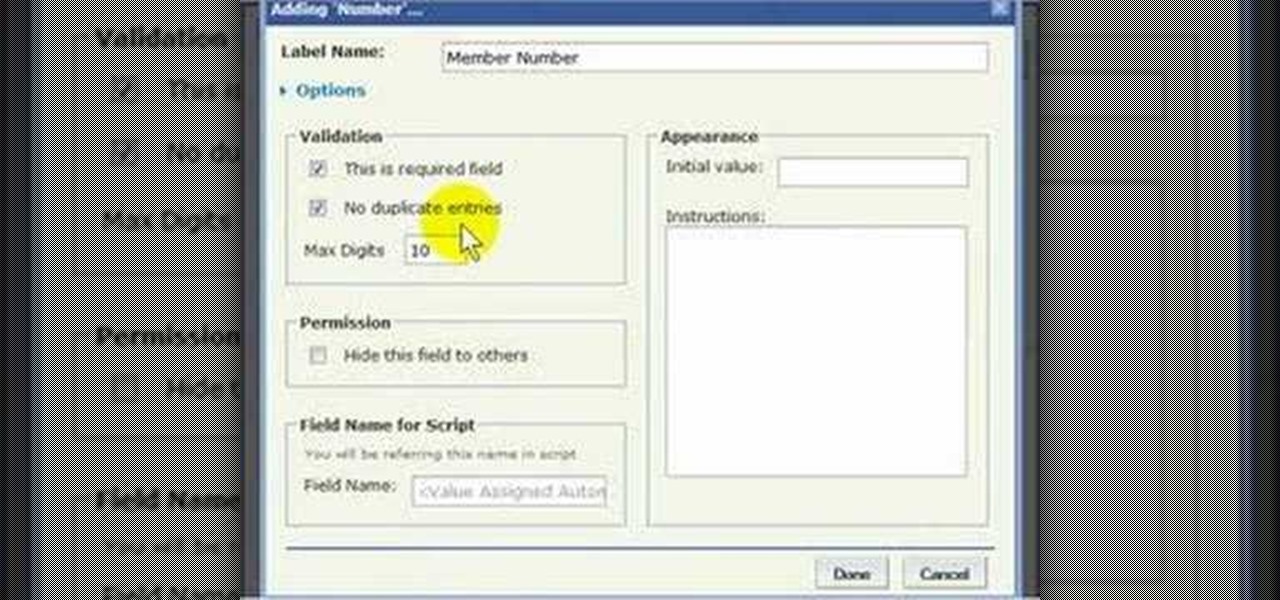
While all Web 2.0 applications are by no means equal, certain among them can save you time, money, and frustration–one such web app is the Zoho Creator database utility, which is comparable to Access from the Microsoft Office suite. For more information, or to get started using the Zoho Creator online database application for yourself, take a look!

Still got stock? Many factory installed exhaust systems not only sound anemic, they actually are because they scrub power. The designers who are given the task of producing these pipes are often handcuffed by several different requirements that add up to one big compromise. Exhaust engineers are required to build systems that are quiet and that meet certain types of emission standards, but not all of the design concerns are driven by government regulations. Some are based on a perception of w...

Do you access either Flickr or Facebook from a home computer running Mac OS X? In this video tutorial, Gary Rosenzweig of MacMost.com looks at two useful extensions for iPhoto that will allow you to upload your photos directly from iPhoto to Flickr and FaceBook.

A hockey stick is used for scoring goals, passing and blocking passes in ice hockey. Learn how to use a hockey stick like an all-star from an experienced hockey coach in this free sports video series.

Take a look at this instructional video and learn how to install the recovery LE to your Playstation portable. With the recovery LE, you can access your firmware's recovery menu options from the PSP's main menu (XMB).

Are there certain tools in GIMP that you use all the time and want easier access to? Or just want to change the default layout? Check out this tutorial and learn how to customize the main toolbar in GIMP to work best for you.

Watch this electronics tutorial video to learn how to enter a secret code and see a lot of interesting info on how your iPhone connects to the network. Field testing your iPhone is easy with the tips in this how-to video.

Watch this helpful electronics tutorial video to learn how to quickly access the Safari address bar on an iPhone. This how-to video, geared primarily toward new iPhone users, will make using quick URLs to browse the internet on an iPhone very easy.

This helpful software tutorial video offers tips on how to keep Firefox bookmarks synced across browsers. The add-on explained in this how-to video will give you access to your Firefox bookmarks no matter what computer you're using.

Blocking in gymnastics is about turning horizontal momentum into vertical momentum for better and higher flips. Watch this video tutorial to learn how to apply gymnastics blocking principles to defy gravity and improve your flips.

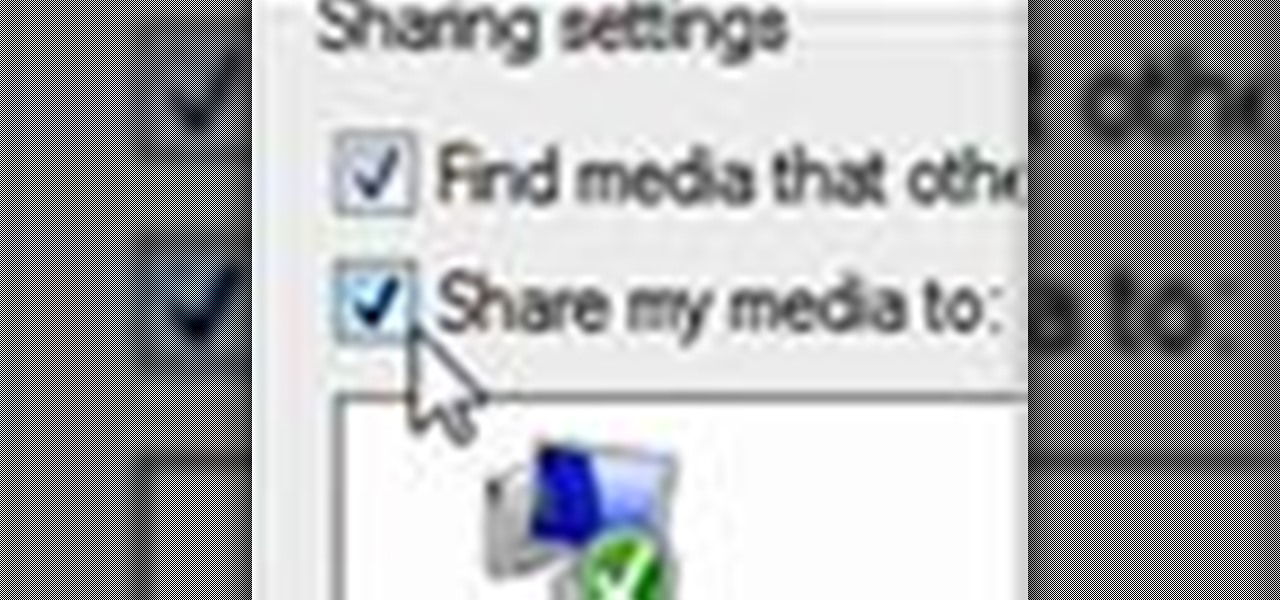
Using Windows Media Player, you can share files among a group of computers and easily access files regardless of where the media is stored. See how to share files in Media Player.

An in depth tutorial on the Sony DSR 250 provided by SPNN Access Staff.

A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

Watch this video to learn how to use Google docs. You can view and edit your documents offline, without an active internet connection.

This episode of Take Zer0 discusses the differences between the multi-camera format used in television, and the single-camera setup most often used in film production. Since it's likely that indie filmmakers have access to only one camera, we will explain and offer examples of how to efficiently shoot multiple takes with one camera to convey a single action.

Learn how to con a vending Pepsi machine and access a secret (but benign) debug menu with this hack how-to video. While this hack won't get you any free soda, you might, at the very least, impress your friends with it. For complete instructions for this simple, pushbutton hack, take a look at this instructional video!

Learn how to install a trailer wiring harness in a Hyundai Sonata. This install will also cover Draw-Tite part # 24757. The first step involved is gaining access to your vehicle, the second step is we can hang the hitch on the tie down loop in the center of the vehicle.

If you are going to use your Subaru Forester to tow, carry a cargo carrier that has lights, or if you have accessories that need power, you are going to need to install a T-One vehicle wiring harness. This video will demonstrate the simple installation of the harness on a 2007 Subaru Forester and includes tips showing which panels need to be removed, where to access the needed plugs, and good locations for the wires and module box.

Pages '08 allows you to access the information in your address book and add it to your documents. This is helpful if you are printing envelopes or writing letters.

Don Schechter demonstrates how to capture your footage from your camera to your computer and log it for easy access later on for Final Cut Pro. Logging clips allows you to organize your footage without having to waste hard drive space.

Learn how to fix a squeaky floor in this brief yet informative tutorial. Note: you will need to have access to the floor and floor joists from underneath.

You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

When an iPhone is lost or stolen, it's imperative to start tracking it via Find My as soon as possible, whether that's from a computer, tablet, or someone else's phone. However, if it's stolen, there's a good chance the thief or robber turns on Airplane Mode, blocking all communication with the iPhone. If this is a scary thought, you can prevent thieves from accessing Airplane Mode altogether.

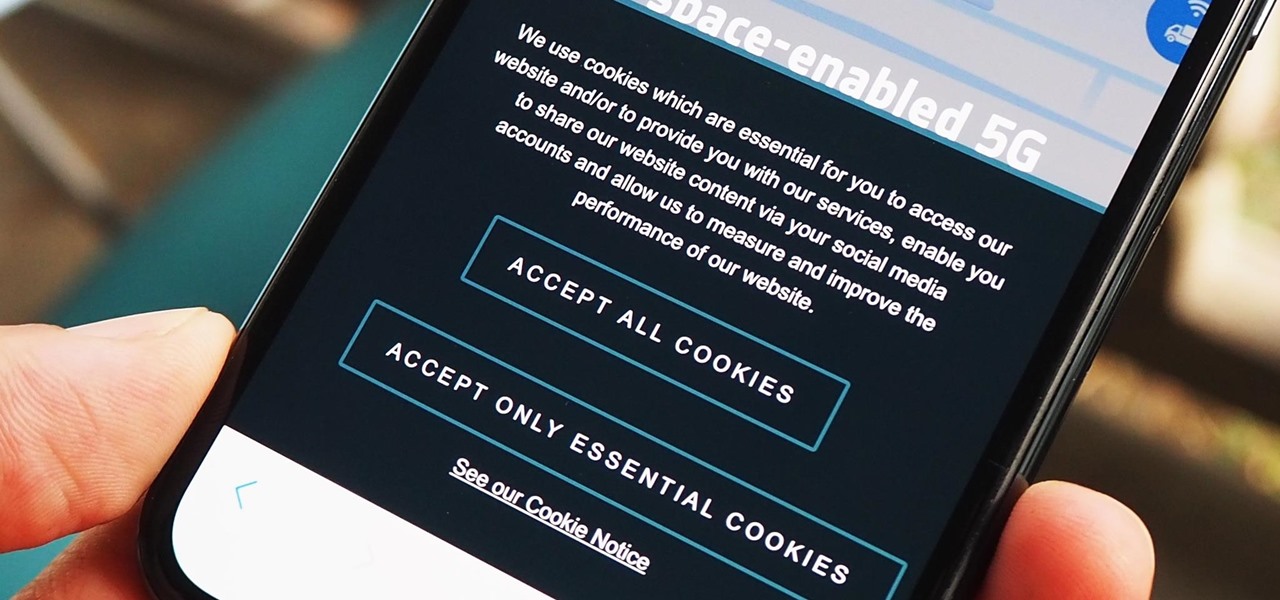
As a means to combat annoying and intrusive advertisements in Safari, Apple added native support for content blockers on the iPhone. Instead of being bombarded by notifications, banners, and pop-ups, content blockers prevent them from opening, which can also be said about those annoying cookie consent notices that many websites now have.

For Android 11, Google is doubling down on the handy App Suggestions feature that debuted in Android 10's app drawer by expanding it to the home screen dock.

With Avatar, Facebook's personalized stickers for use on its social and messaging platforms, those who aren't on Facebook or have otherwise dumped the social network may feel left out.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

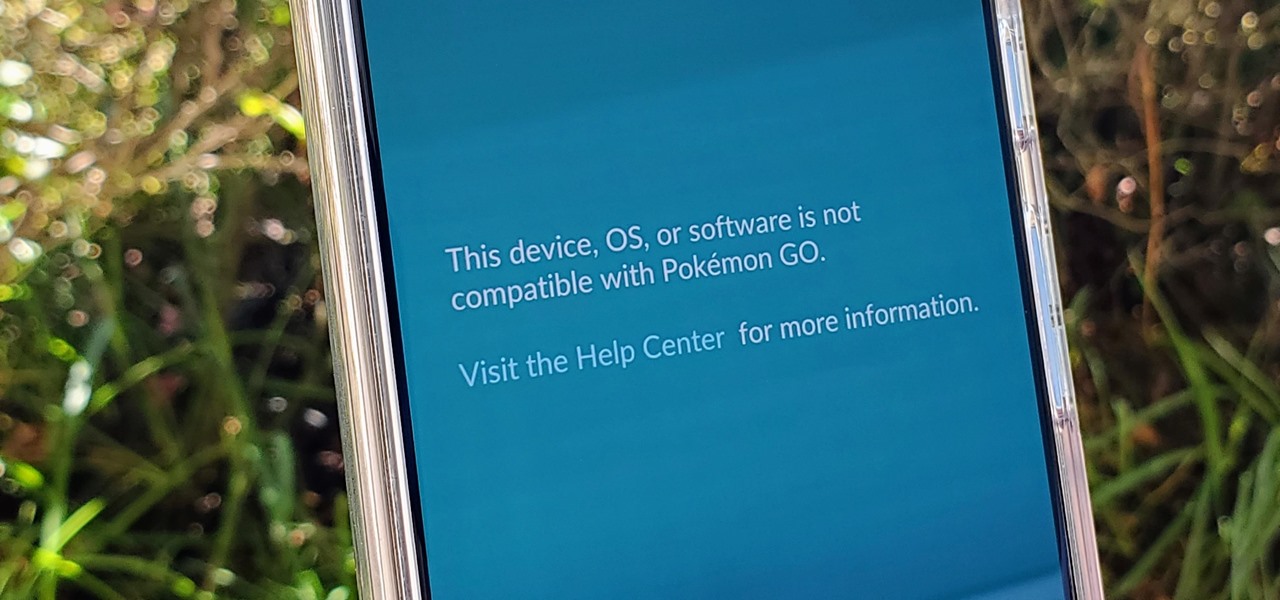
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

Many of us install TikTok just to see what it's like, but most of us stay for good. Inevitably, that involves creating an account. The problem is, TikTok assigns you a username, usually based on your email address — an odd choice for a platform made for self-promotion. If you're not happy with your random TikTok handle, you can change it.

Mobile gaming has exploded, with roughly $70 billion in revenue in 2019. This gave rise to the so-called gaming phone, headlined by names like Razer and ASUS. While the Galaxy S20, S20+, and S20 Ultra are being marketed as everyman devices, make no mistake — these are unstoppable mobile gaming machines.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

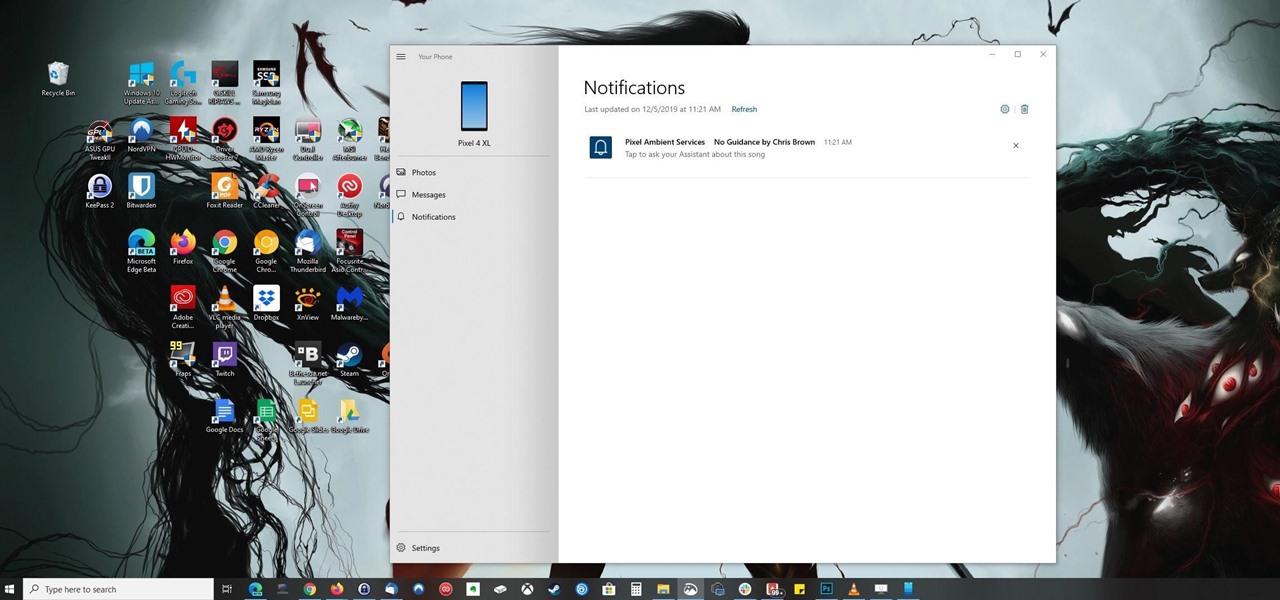
One of the biggest reasons to go with an iPhone over an Android device is Apple's interconnectivity. iPhones, iPads, and macOS devices are all connected in a way that allows seamless transition between devices. Android lacks such a feature by default, but that isn't the end of the story.

It's easy to take your iPhone's Notification Center for granted. As useful as it is for viewing important alerts, reminders, and more, the feature is pretty drab when compared to the customizable Control Center, Accessibility Shortcuts, and others.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Burst mode on iPhone is a great way to ensure you capture the photo you truly want, especially when your subject is moving too fast. You'd be forgiven for thinking that Apple ditched the feature entirely on iPhone 11, 11 Pro, and 11 Pro Max, since a long-press of the shutter button now records video instead. However, burst mode is alive and well on your new iPhone — it's just hidden.

Apple's sixth iOS 13 developer beta was a welcome update for us beta testers. New options for toggling Dark Mode, a way to hide website previews when peeking links, plus UI changes made for a significant iOS 13 upgrade. We're hoping Apple continues this trend of fun and excitement with the release of iOS 13 dev beta 7.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.