Now, you can prevent Donald Trump from building that idiotic wall from the comfort of your smartphone. Well, in theory, you can, thanks to a hilarious new gaming app called — wait for it — Trump's Great Wall.

We all know we shouldn't be using our smartphones while driving. But we also know many people do it anyway. Soon, however, the addicts among us may not have a choice but to kick their habit. A new app announced today by Samsung will block all calls and texts while you drive, stopping those who text and drive right in their tracks.

Almost every Android device comes with a Google search bar embedded directly into its stock home screen app. But Google search is available in so many different places on Android that having this bar in your launcher is almost overkill. On top of that, Google recently changed the logo overlay to a more colorful one that may clash with your home screen theme, so there's plenty of reasons to dislike this feature.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Opioids, or narcotic painkillers, serve as our primary method for alleviating physical distress. They also happen to be a leading cause of death due to their addictive nature. AppliedVR hopes to introduce a safer alternative: virtual reality gaming. They utilize the existing Samsung Gear VR for the hardware, but provides specialized software that offers up a distracting experience that fosters greater pain ignorance.

Don't Miss: The Difference Between Virtual, Augmented, & Mixed Reality

Pong, one of the simplest video games ever created, has managed to evolve in some crazy ways over time, from the original basic 2D version and colorful Breakout sequel, to the PlayStation game with power-ups and 3D graphics, and now Cyberpong VR—a virtual reality game on the HTC Vive—where you act as the paddle instead of just moving it into place with a controller.

Microsoft's enjoyed being the only mixed reality headset on the block for a little while, but the Meta 2 intends to join the party very soon. According to UploadVR, in a couple of weeks they'll begin shipping alpha versions of their headset with improved hand tracking.

Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies.

Most sandboxes wait for children on a playground or the occasional zen garden raking. This one combines light, sand, and depth cameras to create a completely malleable topographical map you can alter with a brush of your hand.

The following are 5 pranks you can set up on your friends and family using their shoes. They're quite funny and to prepare these pranks all you really need are a few household items and a couple other things you can get at your local dollar store such as party snaps and party poppers. You'll also need access to your friends' shoes.

The team behind Minecraft, the popular open-world game beloved for its freedom to create and build, has teamed up with Oculus to release an official edition that takes you even further into the block-based world using a Samsung Gear VR headset. While the Oculus Rift version itself is still forthcoming, Gear VR users can play right now.

If you're all out of prank ideas for April Fool's Day, we've got a few that your Apple-loving friends will enjoy (or hate?). You can have a little bit of fun if you don't have access to their iOS device or Mac, but for the best pranks, you will need access to their devices, even if it's just for a few seconds.

Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate.

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

3D Touch on the iPhone 6S and 6S Plus is a pretty cool feature, and will only get better as more developers begin to roll its functionality into their apps.

As we go about our daily grind, our smartphones and tablets take a silent beating. Dirt, dust, oil, and grime that our hands have picked up immediately gets transferred over to our shiny pocket-sized computers every time we check the time or look for new notifications, and over the course of months, this can have a very noticeable adverse effect.

If you have a broken laptop computer, but the hard drive still works, this video will show you how to access and remove your old photos, pictures and files.

When I started to go to this site I found it fascinating and found myself coming here all day I have used a lot of the info I have gotten from here in my professional career and on my own. I currently am the VP of RND for a small IT company. I have been pushing toward Penetration Testing as a service for our clients and future clients. For the past 10 years here it has been a very long uphill battle and have hit a lot of road blocks. So I decided to work on this on my own of course as soon as...

By now, a mobile phone that isn't "smart" is about as hard to come by as a TV that isn't high definition. As a result, members of older generations who were previously reluctant to purchase a newfangled smartphone have no other choice but to cave into the more recent trends when their old device finally breaks down.

A long time ago I was reading an issue of Saveur and saw an article about a trendsetting bar in Portland. The bartender at the joint had started making enormous blocks of smoked ice for his cocktails. When a patron ordered a drink that called for the smoked ice, the bartender would chip off a large chunk and place it in a glass with the booze. Then, as the ice slowly melted, the drink would take on more and more smoky notes, and the flavor profile of the beverage would change with every passi...

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

It would be an understatement to say that Supercell hit it big with Clash of Clans. The game has topped both Google Play and the iOS App Store for years and shows no signs of ever slowing down.

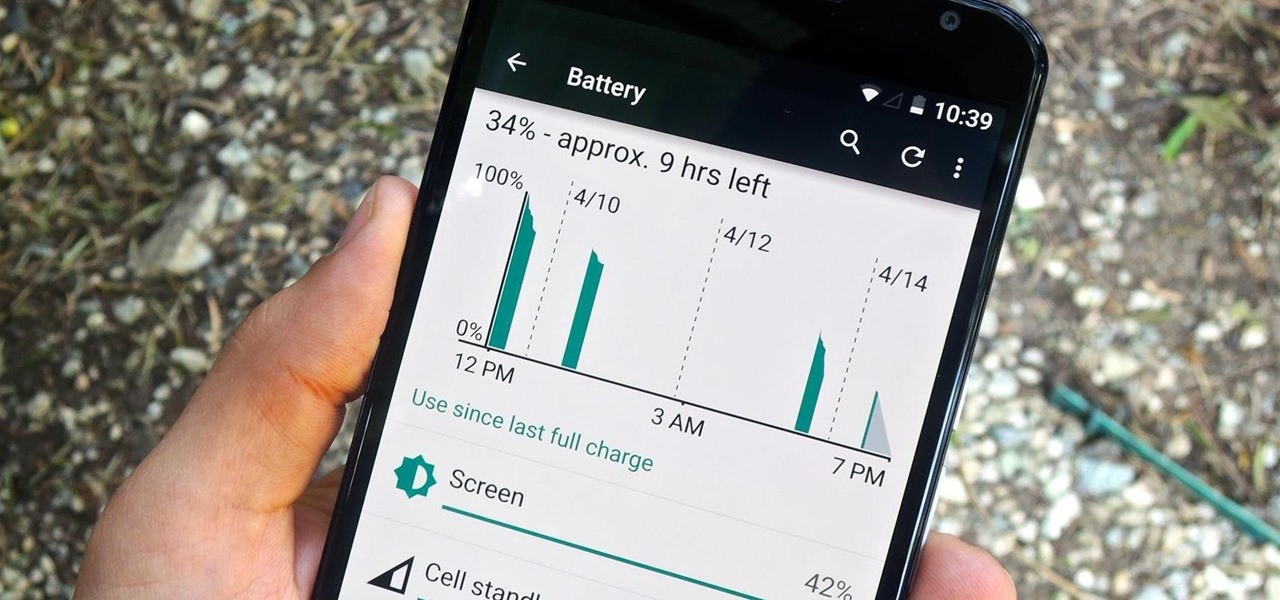
When purchasing a new phone, one of the most vital features to consider is battery life. Everyone wants to know how long they can use their device without needing to hug a wall. Increasingly, more and more manufacturers ship their devices with some variation of a "battery saving" mode, which can help combat dead-phone issues in times of dire need for battery life.

Indoor electric grills are nothing new; George Foreman grills have been around for over 20 years now, providing healthy, smokeless grilling options for indoor use. Yet as nifty and fun as George Foreman grills are, indoor grills have never been considered a hot item for passionate and avid home cooks.

In this simple tutorial, you'll learn how to easily set up a prank on your teacher in class for April Fool's Day. If you're looking for a simple yet effective prank to pull on your teacher on April 1st, why not try this one? All you pretty much need is black shoe polish and access to your teacher's dry board eraser. The rest is easy.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Essentially, the Anti-Griddle does exactly what its name promises: it turns things almost instantaneously cold when you drop them on its "grilling" surface. Unlike home methods of flash freezing, its staggeringly low temperatures (-30°F/-34.4°C) allows ingredients that normally can't be frozen—like oil or alcohol—to turn into solids in the wink of an eye. As you might imagine, this allows chefs to play with textures and tastes in a way that was previously unimaginable.

YouTube and the National Football League have announced a partnership that should greatly improve the online experience for gridiron fans. In a posting on their official blog, YouTube outlines a deal that will bring NFL video clips to their immensely popular site while bumping official NFL pages up to the top of relevant Google search results.

There's no denying it was a hectic 2014 here in the United States. We saw the rise of ISIS, dealt with an Ebola scare, and witnessed the turmoil in Ferguson (and its aftermath). Plus, let's not forget about all of the hype revolving around The Interview, in which Sony was hacked.

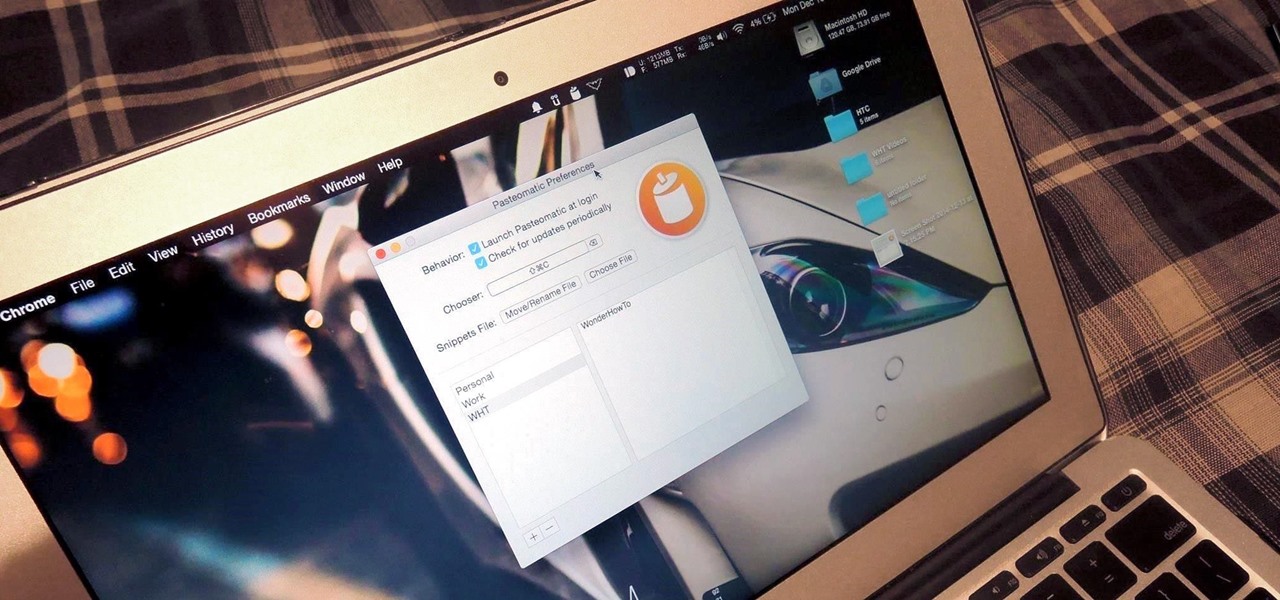
Your Mac's clipboard is great when you are just copying and pasting a phone number or address, but sometimes you end up having to re-copy the same thing over and over every day. To make those phrases a lot more easily accessible, the people over at Tiny Robot Software have released Pasteomatic. With this app, you will be able to use a hotkey to bring up a collection of your most commonly used text snippets and paste them into any text field or document.

Yosemite brought a new, Alfred-like Spotlight search to our Macs, but at times I still find myself wanting more out of it. However, after stumbling upon Flashlight by developer Nate Parrot, I am now able to perform Google searches, look up weather, and even enter Terminal commands straight from Spotlight's search bar.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?

Automator takes the work out of common repetitive tasks. I don't enjoy compressing videos for quick sharing or uploading to the web, so I created an Automator action to handle the process for me.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Oddly enough, stock Android does not come with a "do not disturb" function out of the box. Samsung has their own version built into to TouchWiz called "Blocking Mode," and Apple has had their "Do Not Disturb" feature since iOS 6, so why is stock Android so late to the game?