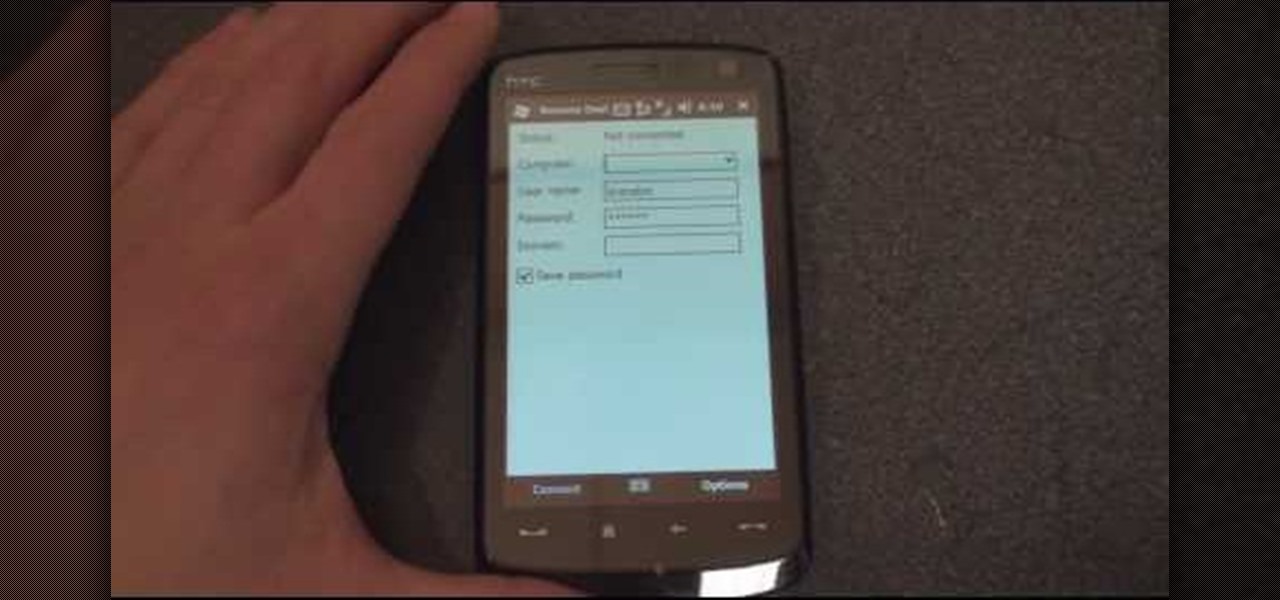
In this tutorial Brandon from Pocketnow.com will show you how to set up and use your remote desktop on a Windows mobile smart phone. Windows mobile remote desktop allows you to remotely access and control your Windows computer from your cellphone device, it is just like controlling your computer but in the palm of your hands. This guide will also show you how to get the Remote desktop software on your cell phone device if you don't already have it. The remote desktop requires for you to have ...
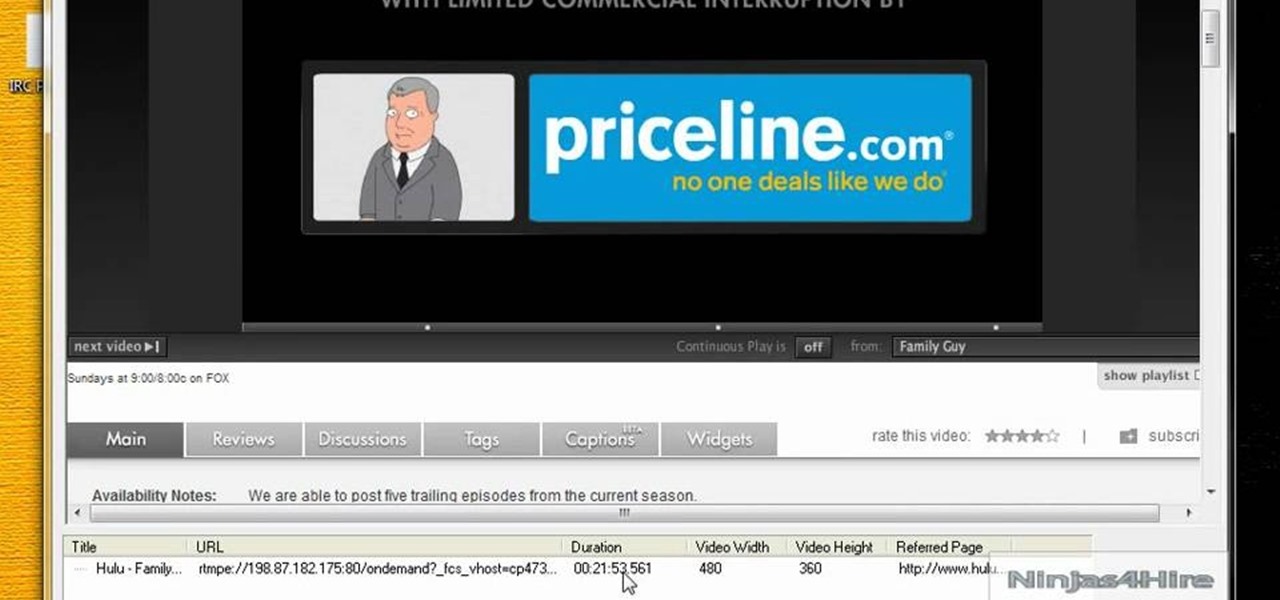
Hulu is a great video site, but unfortunately the TV shows and clips they show have a time limit and won't always be there for you to watch.
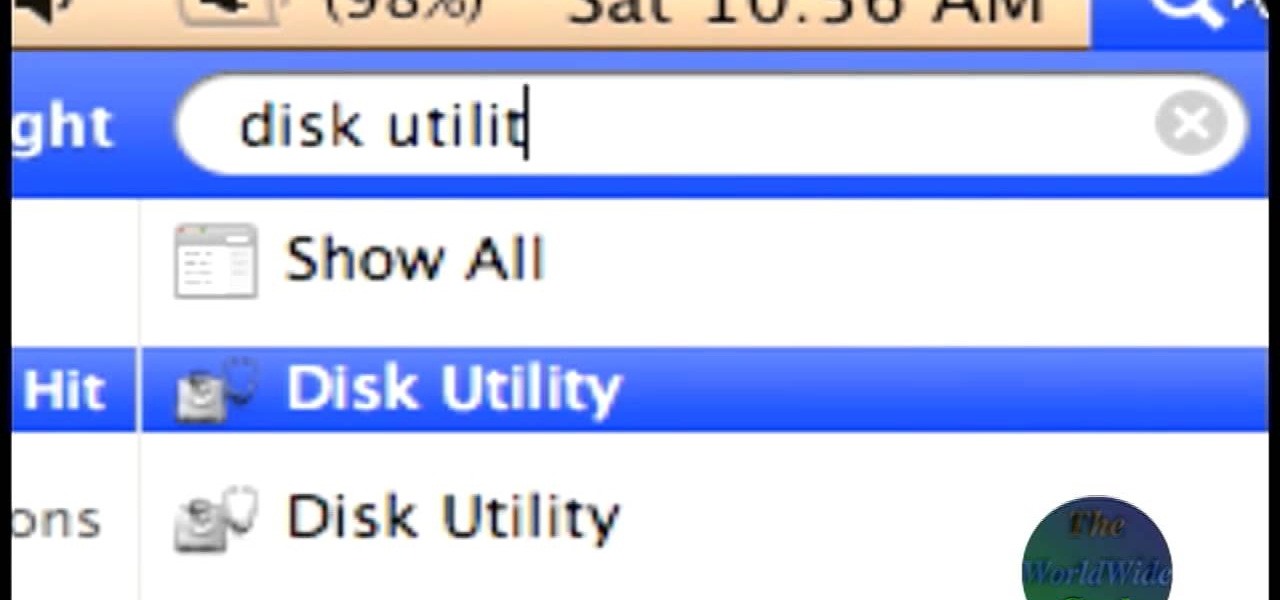
The World Wide Geek demonstrates how to format an external hard drive for Mac OS X. External hard drives are usually formatted for windows. To change the format, you will need to use the disk utility option. Access the disk utility by going to finder and clicking on applications. Next, click on the utilities folder. Then, click on the disk utility option to open it. You can also search for disk utility in spotlight. Select your external hard drive in the options to the left of the disk utilit...
In this video tutorial, viewers learn how to transfer iPhone videos and pictures to a computer. Begin by connecting the iPhone to your computer. Then click on the Start menu and select Computer. Now select your iPhone device drive and click on the eternal storage. Then continue clicking on the folders. Users will then be able to access the videos and pictures from their iPhones. To transfer the files, simply drag it onto your desktop. This video will benefit those viewers who have an iPhone a...

Have you locked yourself out of your car? Well, as long as you have a shoelace, you may be able to get back in.

In this video tutorial, viewers learn how to repair a broken Les Paul Guitar Hero guitar controller for the Xbox 360. Begin by unscrewing the screws in the neck of the guitar. It is recommended to detach the neck from the guitar for easier access. Now open the top part of the neck and carefully remove the green chip from the tab. Then put the green chip in front of the original tab. Now screw the neck back together and attach it to the guitar. This video will benefit those viewers who enjoy a...

Consider a normal and ideal height for a girl in 5feet 8inches in height. The book of Andrew Loomis is a good guide for drawing realistic human figures. It explains the body proportions, techniques, drawing the parts, human movements, and poses of the body.

A new introduction into the iPhone community is WordPress which easily allows you to easily control things like your WordPress blog on the move. Start off by tapping in your blog details, start writing a new post with a single tap, setting your tabs or publishing data right from the main editor through this. This also allows you to add photos directly taken from your iPhone's camera, you can change your publish date and set a password on your posts to decide who has access to them. Finally yo...

Prius models that are equipped with tilt-slide moon roof have a remote control button on their smart keys for the remote air-conditioning system. Before leaving the vehicle, make sure the headlights are switched off or set to auto. All windows are closed and check the temperature setting of the AC system. As you return to the Prius, press the remote AC button on the smart key remote to activate the air conditioning system. The cabin will cool to the pre-set temperature without turning on the ...

When conducting mobile convert surveillance, you will be following someone and it is important to dress appropriately for the environment and carry your surveillance equipment in a bag that will fit into the scene.

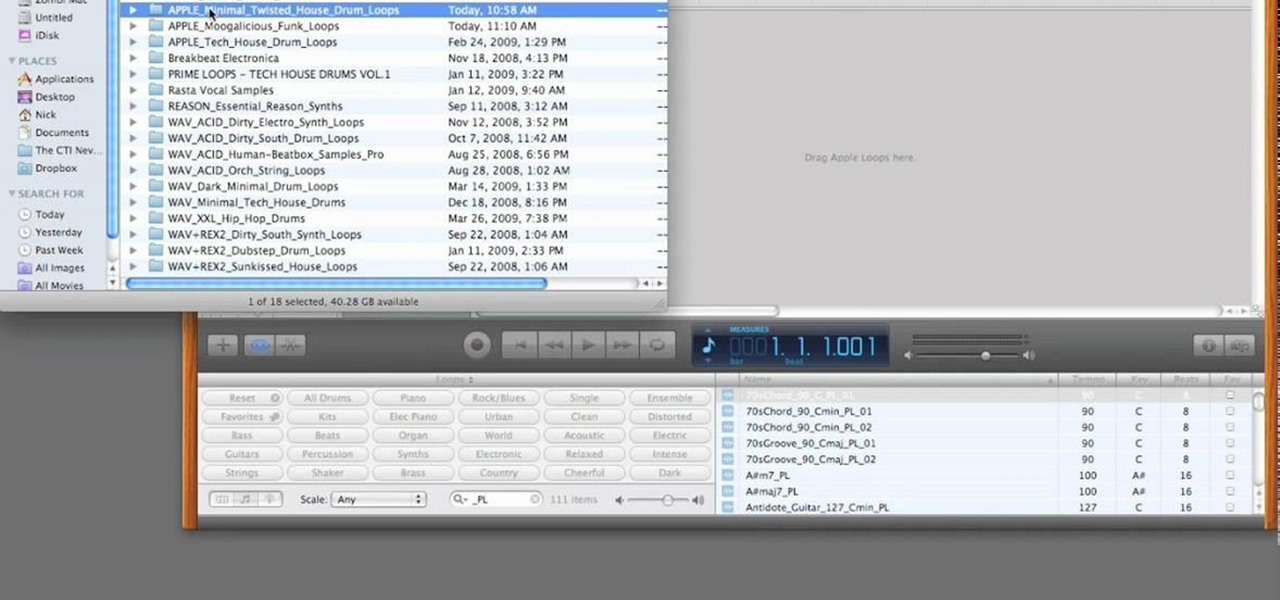
PrimeLoops teaches you how to use loops on Garageband. There are 2 different types of loops - regular and Apple. The last come in .aiff proprietary file format and the information contained has more information than a regular .wav file. To access them click on the small eye symbol in the lower part of the program window. You can switch to music, podcast and all loops. You also have a Favorites tab and you will see the loops that you mark as a favorite. You can also search for all loops in the...

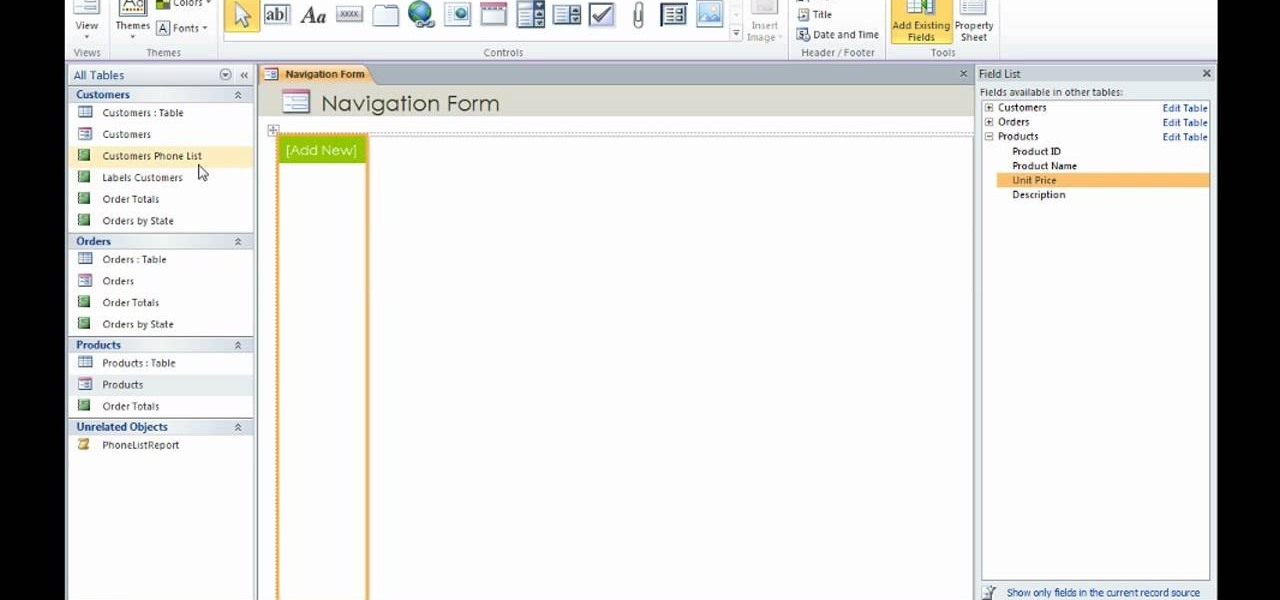
David Rivers shows us how to create navigation forms in Microsoft Office 2010 without writing codes or using logic. A navigation form is kind of like a homepage that will give you a list of reports. There are pre-designed layouts you can choose from to make your navigation form. You will just need to customize your form by adding reports to the navigation pane. What this means for business owners is that you can see customer orders and store reports just by looking at one page. Simple to make...

In this video tutorial from Get Connected TV, hosts AJ Vickery and Mike Agerbo, will show you how to extend Widows Media Center to your XBox 360 using Windows 7. This video assumes that your XBox is already connected to your home network, so you may want to be sure to do that first. With this configuration, you will be able to not only watch movies, but view, pause and record TV on your personal computer, as well. You will learn how to access the Media Center section of your XBox, and get the...

How to Watch Hulu on your Xbox 360. The problem is HULU doesn't look good on some old PCs. Fix this by running it on your TV or projector. This uses the program PlayOn to run Hulu through your XBOX 360. This will tie it into your Media Center. This will make YouTube, Hulu and Netflix on your XBOX video game console. Go to Video Library and access you PlayOn server.

Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

A Membership Provider allows a web application to store and retrieve membership data for a user, and the standard ASP.NET Membership Provider uses pre-defined SQL Server tables. In this video tutorial, Chris Pels shows how to create a custom membership provider that uses custom SQL Server tables separate from the pre-defined tables used by the standard provider. The principles covered in the video will apply to creating custom membership providers using other databases such as Access or Oracl...

In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

Google's G Suite collection of premium cloud services and apps have become popular with business customers, with more than six million subscribers now.

On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.

It's not so difficult to stay at home during the coronavirus lockdown when there's so much free entertainment to take advantage of. That seems to be the M.O. for many studios and streaming services, as they've made so many shows and movies available to the public for free. That said, they aren't running charities here. These deals won't last forever, so make sure to jump on board before it's too late.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

Some of the oldest art on Earth was created 36,000 years ago on the walls of the Chauvet Cave in France. However, these days, physical access to the cave is restricted in order to preserve the site.

I'm a new parent and I just moved into a new home. The first thing I wanted to do was ensure my toddler's safety in his new digs. That meant buying a bunch of baby-proofing products from Amazon, realizing most were junk, then buying some more until I found solutions for all my needs.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

The augmented reality cloud will probably be one of the most important pieces of digital real estate in the next few years, and China has no intention of being left out of the virtual land grab.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

The first annual Snap Partner Summit kicked off on Thursday in Los Angeles, and with it came some new products announcements, several of which enhance Snapchat's already robust augmented reality powers.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

The Oscars are fast approaching, which means that all the most talked about films are getting a second dose of heavy promotion in hopes of winning an Academy Award.

CarPlay is no doubt the best way to use your iPhone when behind the wheel since you can safely drive without too many distractions. It gets even better with all the music and podcasting apps available, as well as third-party navigation apps such as Google Maps and Waze. With more apps being added to CarPlay every day, it becomes more necessary to rearrange your home screen.

Millions depend on Google Maps for directions, and it's easy to see why. The app comes with tons of features like offline navigation, location sharing, and more. Google is far from done, however, and continually improves upon its navigation app to make it even more efficient and safer to use.

After weathering an executive departure and reports of a failed sale to Apple, Leap Motion is getting back to the business of pushing the envelope for augmented reality development and interaction.

The addition of a new research mode for Microsoft HoloLens will enable researchers and developers to tap into a wider range of data collected by the device's sensors.