Ever since 2009, you could send a photo or video that you've already taken right from the Messages app on your iPhone. You would just tap on the camera icon next to the new message box, then choose either to take a new one or select one from your library. If you're running iOS 12, that's no longer the case, but that doesn't mean the capability is gone entirely.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Another AR cloud savior has emerged this week in Fantasmo, a startup that wants to turn anyone with a smartphone into a cartographer for spatial maps.

Snapchat is making it easier for developers and creators to build augmented reality effects in Lens Studio with a slew of new features, including seven face templates.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

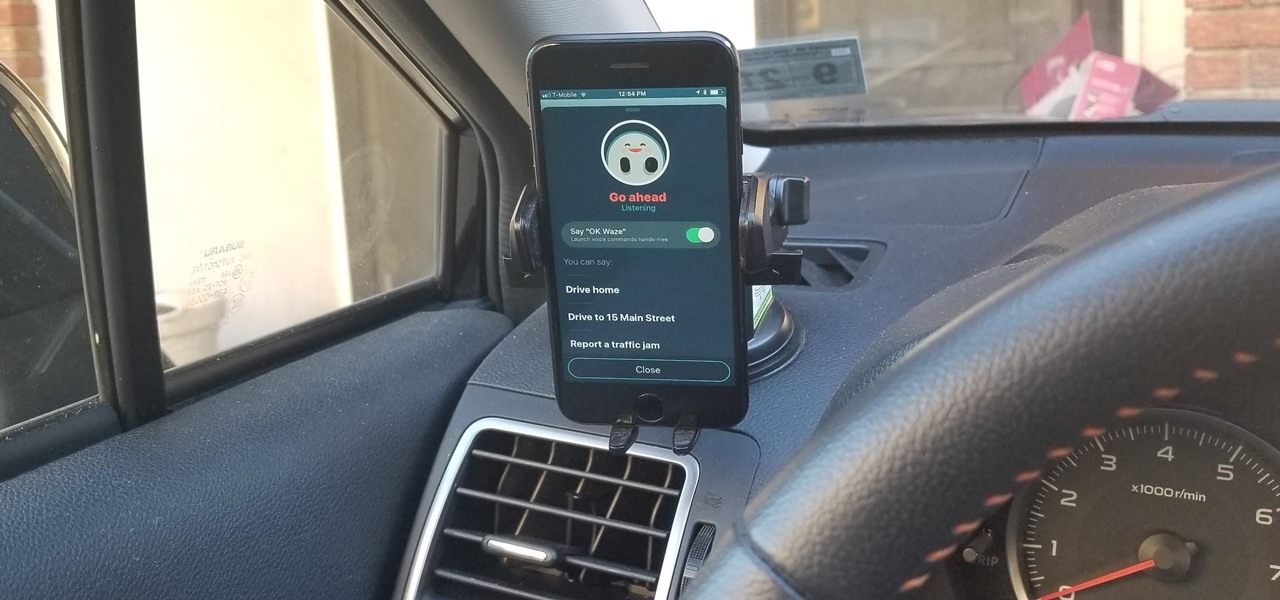
Drivers the world over are painfully aware of the inherent danger of taking their eyes off the road even for a second. In fact, according to the National Safety Council, 27% of all car crashes result from distracted driving due to attempted cell phone use. Fortunately, Waze comes with a feature that can help keep you from being a part of this grim statistic.

The Pixel 2 has a number of new unique features. One of the most interesting is the Now Playing option to identify songs you hear on a daily basis. Now Playing displays the artist and title of songs playing in the background of your day and shows this information on the lock screen. While this functionality is incredibly useful, the song history is not saved anywhere on your phone.

Using the Mail app to log in and sync to email services such as Gmail and Outlook is incredibly easy to accomplish on the iPhone thanks to the intuitive nature of its operating system. This is still evident with iOS 11, and though the process differs slightly from its predecessors, it can still be accomplished with relative ease.

More often than not, road trips will include unforeseen pit stops that have to be made, no matter how well prepared you are. In the past, making an unscheduled stop may have led to headaches and delays when your navigation app got off track, but thanks to a feature in Google Maps, this is no longer an issue.

How can something get more free than free? Well, in the case of Twitter, Virgin Mobile found a way with its newest promotion. If you have a 4G plan with Virgin Mobile, you can now access Twitter from your smartphone without it counting towards your monthly data allowance.

At the eMerge Americas investors conference in Miami, Florida, Magic Leap founder and CEO Rony Abovitz previewed details of the launch of their highly-anticipated device.

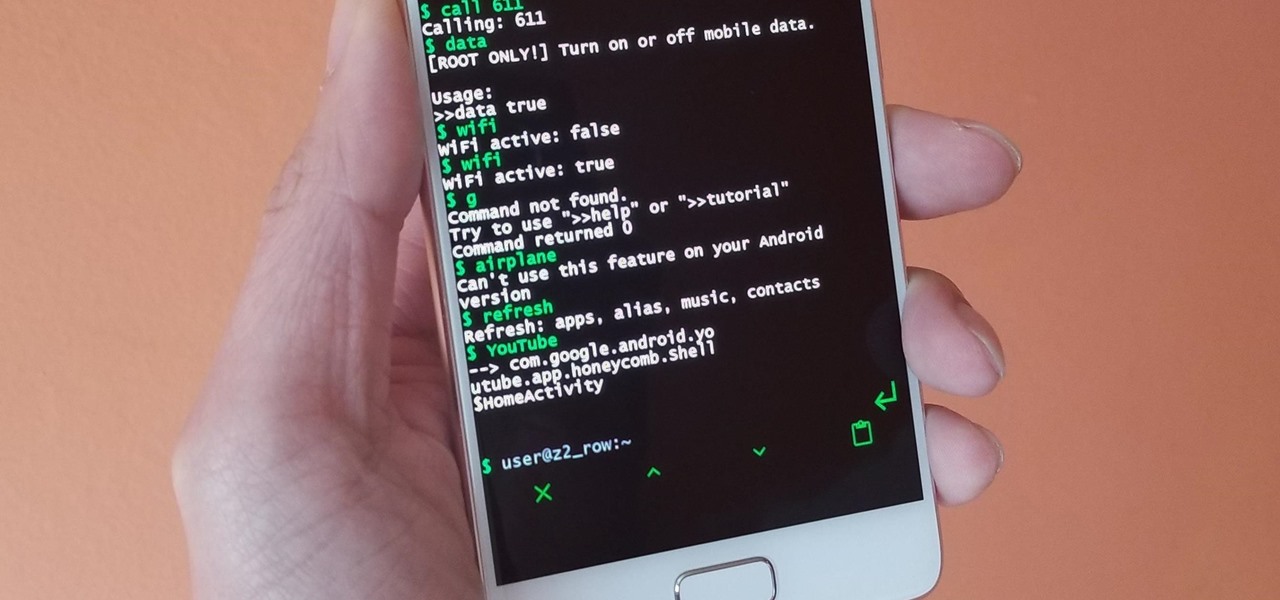
Running commands on Linux seems so complicated for the layman that it may as well be a foreign language. But for the die-hard terminal users, or for those who are just curious about the Linux experience, there's a new Android launcher that gives your home screen a command line makeover.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

Uber and Waymo's lawsuit is starting to pan out. Following a ruling on Monday, May 15, Judge Alsup, who called Waymo's patent infringement claims "meritless," ordered Uber to perform a series of actions and duties for Waymo. Without further ado, here's what Uber must do to begin to put this lawsuit behind them (well, maybe):

Magic Leap has always been intensely secretive about its work on its augmented reality headset, so it's interesting that they're now publicly recruiting developers to build software for the device before its launch.

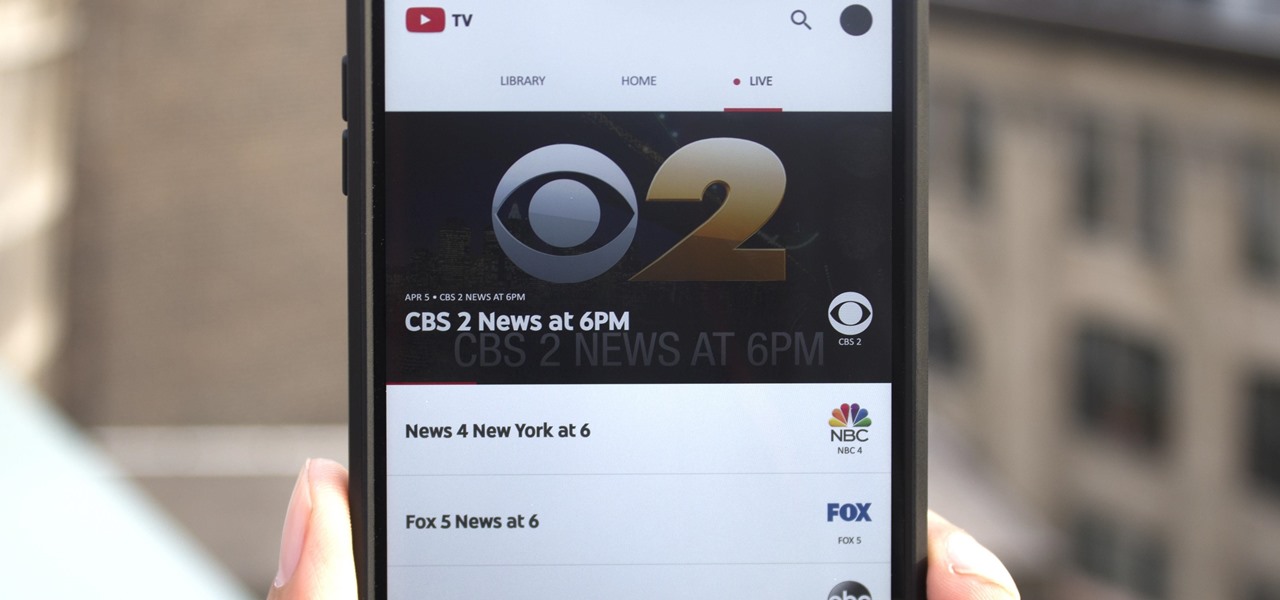
As you may have heard by now, YouTube has launched its own live streaming TV bundle available for users in the select markets of New York, Los Angeles, the Bay Area, Chicago, and Philadelphia. A subscription to the new streaming YouTube TV bundle costs $35 a month, but the service is drawing in users by offering a free 30-day trial.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen burn-in.

The widget system on iOS leaves a lot to be desired when compared to Android's offering, but that's not really Apple's fault. The system is there, we just need some good widgets to really get the most out of it, so it's up to developers to create some awesome apps that work with the home screen and lock screen widget panels on iPhone, iPad, and iPod touch.

The iPhone has a handy feature called AssistiveTouch that lets you quickly adjust volume, lock your screen, rotate your display, and even navigate through the phone's interface using a virtual home button. In a way, it's a lot like the on-screen navigation bar that you'll find on some Android devices, but with a lot more functionality, and bundled together in a floating bubble interface.

Android's notification system is quite robust, especially now that Google added bundled notifications and quick reply features to Android 7.0 Nougat. However, things can still get quite cluttered when you have several unread messages, which fills your status bar with icons and makes your notification tray take up half of the screen by itself.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

With every flagship device they release, Samsung makes sure to add in at least a few little software goodies. Last year's Galaxy Note5 was no exception, because among other things, Samsung included a revamped version of their useful utility called Air Command that gave users quick access to tools and common functions with a small floating bubble.

One of the biggest causes of smartphone battery drain is the mobile data connection—particularly if you live in an area with poor reception. But, chances are, you don't actually need this connection most of the time, because you're probably connected to Wi-Fi for a good chunk of the day, which uses far less battery life.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

You can now access Google's slick Weather app without having to first open the Google or News & Weather apps. However, you will have to use Google to access the weather the old-fashioned way one more time, but you'll have the option to place a shortcut on your home screen to access the weather directly going forth.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

The notification light on phones and tablets is slowly disappearing. The once staple feature is now only found on a few devices, and a bevy of other notification systems have sought to fill the gap. The most popular of these systems is Ambient Display, which has grown in popularity with OEMs over the last couple of years; even Google's own Nexus line of phones have made the plunge.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

As familiar as it may look at first glance, there are still tons of subtle changes in Windows 10. Many options that existed in past versions have been moved, and virtually every system menu received at least a small visual makeover.

In the U.S., smartphone users spend more time on Facebook and Instagram than on any other app. If this sounds surprising for any reason, it shouldn't. Anyone that's browsed Instagram in a moment of boredom knows that a few minutes can quickly turn into an hour down a rabbit hole filled with Likes, Follows, and straight-up lurking.

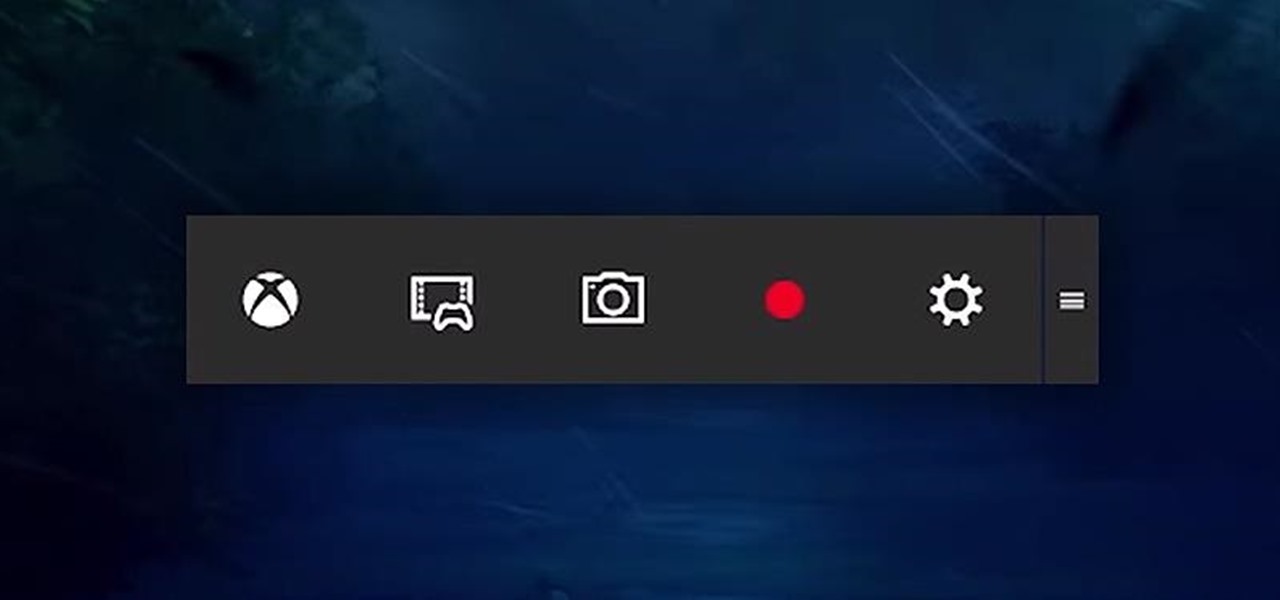
Up until now, if you wanted to record videos of the apps on your screen, you had to rely on a third-party option. However, Windows 10 changes this thanks in part to the new Xbox app. One of the new features of the Xbox app is the Game bar, which allows you to record footage of your gameplay.

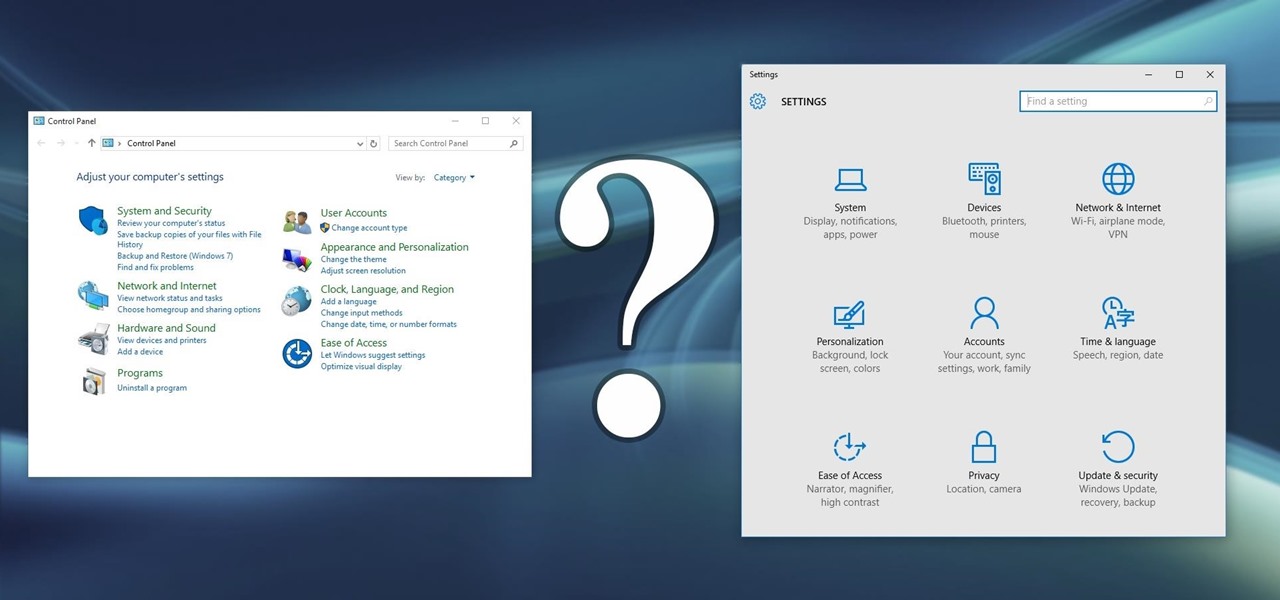
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

Keyboard shortcuts can make using your Mac faster and easier, and leave your mouse feeling archaic. With just a few taps, you can save files, open new tabs, or play a movie—all without using your mouse even once.