Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.
There is no built-in way, or any options in the iOS App Store, to customize the vacant top half of the screen that appears when the newer Reachability feature is triggered in iOS 8. However, there are many Reachability tweaks for jailbroken iPhones, one of which lets you use the feature on devices other than an iPhone 6 or 6 Plus.

An Amazon Prime subscription offers free two-day shipping and discounted rates on many Amazon products, while at the same time granting users access to Amazon's Instant Video library. While this service normally runs $100 per year, Amazon CEO Jeff Bezos announced today that the company will be offering a $28 discount on this price for one day only.
Being fixated on all of the great additions to Android 5.0 Lollipop, it can be a little difficult to take notice in the features that went missing. For instance, lock screen widgets. It's speculated that the lack of practical use for lock screen widgets and the implementation of the revamped Lollipop lock screen may have lead to their departure, but some of us want them back!

Android 5.0 "Lollipop" has only existed for a few months, but a leaked version of Samsung's take on the firmware has already been spotted in the wild. This update came straight from Samsung, and brings with it a plethora of new features, including greatly improved performance and a revamped TouchWiz UI.

If you like free stuff and own a Samsung Galaxy device, then you're entitled to two free popular movies in the Google Play Store—but you better hurry fast, because there's only a certain number of free downloads available.

So you just bought a fancy new Nexus 6 complete with its gorgeous and gigantic display—now what? Unlike Samsung's TouchWiz, stock Android doesn't sport any cool split-screen features, so how do you really take advantage of all that screen real estate?

If you're someone who likes to customize their user experience, stock Android is a lot like a blank canvas. The firmware that comes preinstalled on Nexus devices is just Android—no manufacturer skins or carrier bloat involved. This simplicity opens up the door for many root mods and flashable ZIPs that can be installed in a custom recovery.

On earlier Android versions, you were able to hold down on an app's icon in the recent apps menu (aka app switcher) and jump straight to the app's info page. From there, you could easily uninstall the app, force-stop its activity, or clear its cache and data.

When it comes to subscription-based music streaming services, the conversation doesn't go much further than Spotify and Google Play Music (previously called "All Access"). Both services are essentially the same aside from slightly different catalogues and social options, and they both run ten bucks a month for unlimited music streaming and offline track saving (although Spotify does have a free, ad-supported service).

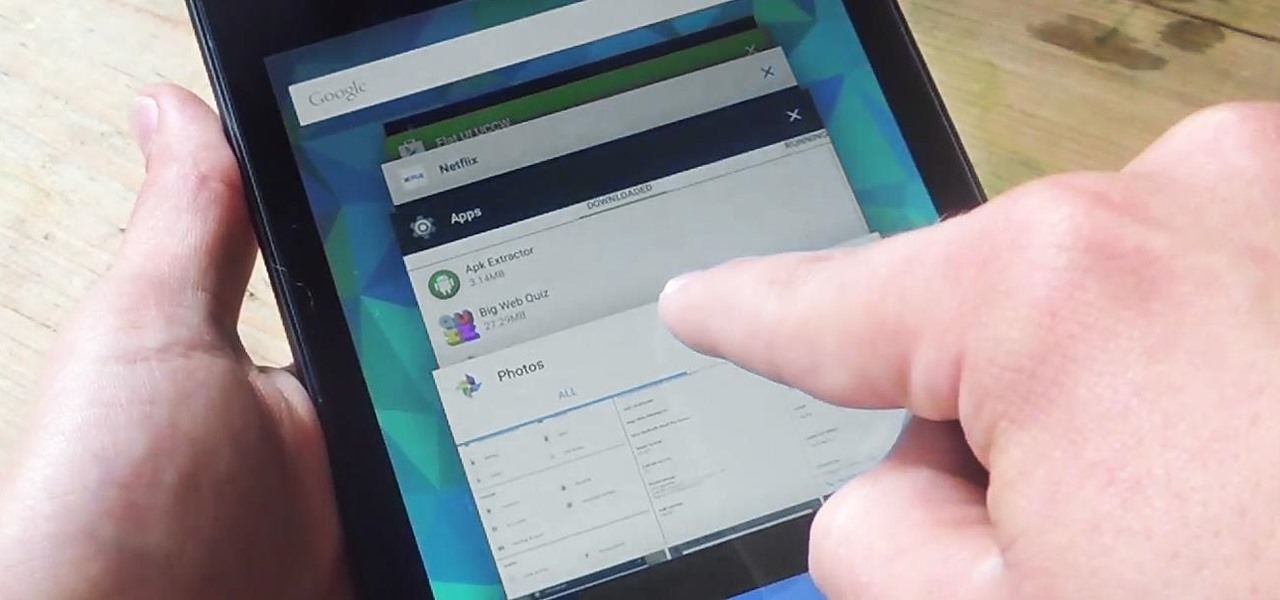
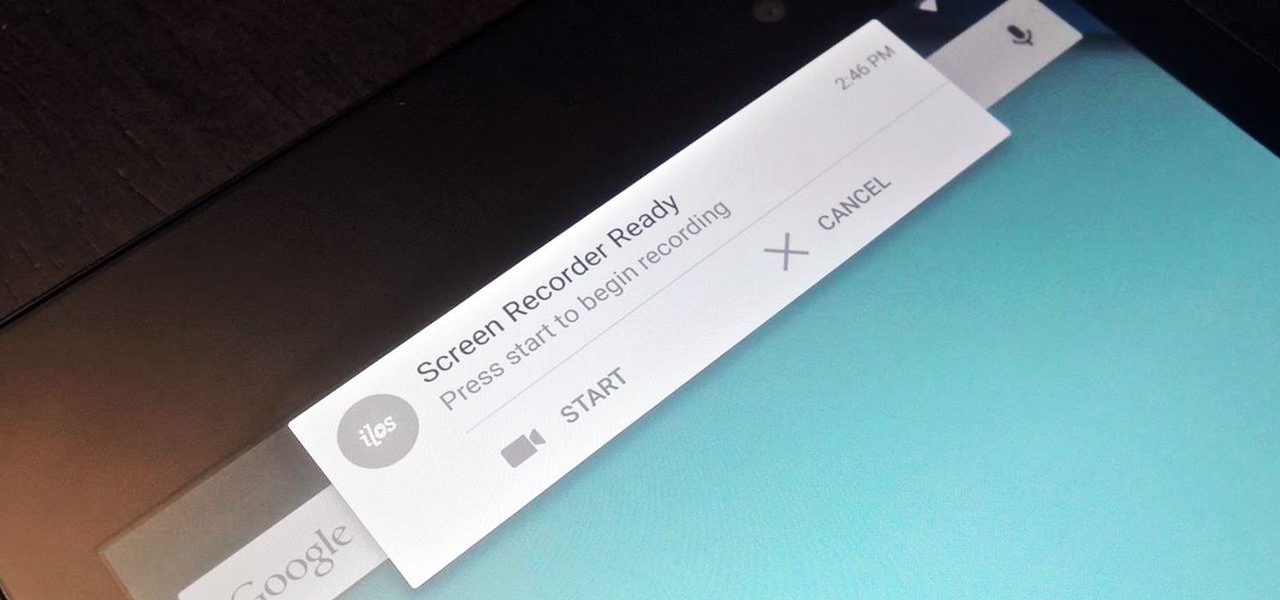
Native screen recording was initially introduced on Android 4.4 KitKat and, although useful, was primarily utilized by developers to showcase their apps. It required either a rooted device and an app or a non-rooted device with some ADB commands, which, while totally doable, wasn't necessarily ideal.

There are those who hold their phone or set it down when they're not using it, and others, like myself, who pocket it. If you're like me and are rocking the pants pocket fade, then you'll love the new Android app I found.

By now, Samsung's Multi-Window Mode is a pretty well-known feature. With other manufacturers now recreating this functionality in their own flagships, like LG, it's safe to say the feature has been a hit with consumers.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

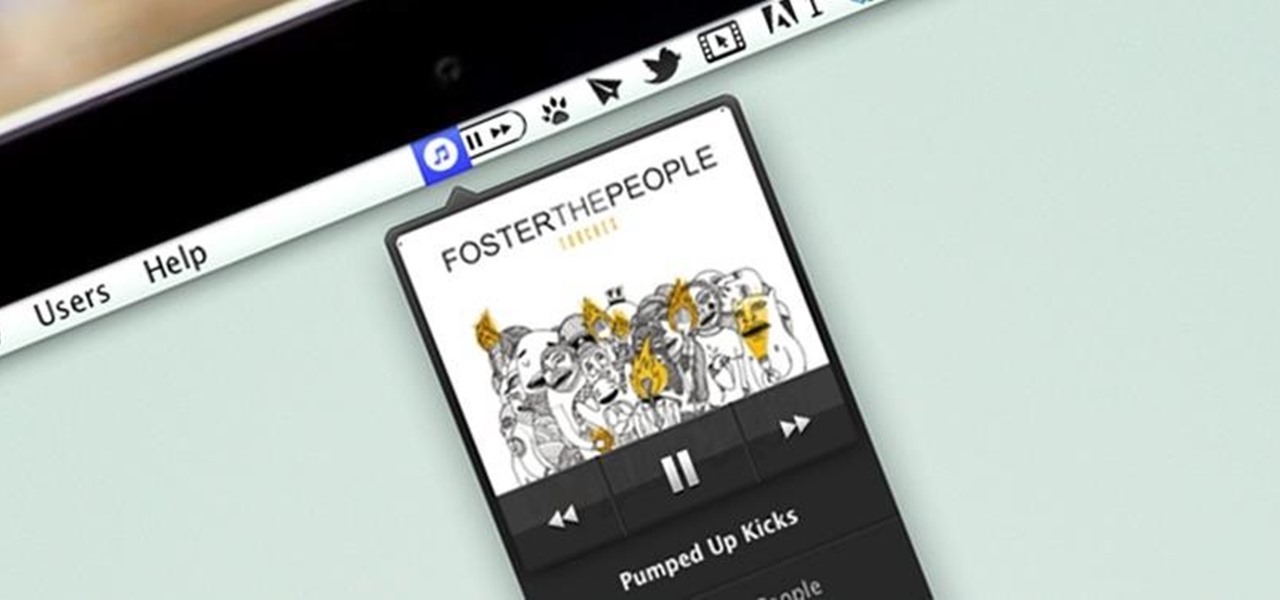
I consider myself a lover of music from all genres, but sometimes a song comes on and I just have to press next. That could be a tedious task, since I often in another app that I'm highly engaged in. Other times, my MacBook is across the room from me without easy access to keyboard shortcuts.

While texting and driving may get you a ticket, there are still a ton of uses for your phone in your car, music and navigation just to name a couple. Every Android device comes with access to GPS and traffic updates, but none of those apps really have your back in real-time.

Last week, I showed off a deeply buried accessibility feature built into iOS 7 and 8 that lets you disable screen touches in certain apps. While useful for many reasons, I found it most helpful for preventing nosy family and friends from swiping through the Camera Roll when showing them a photo.

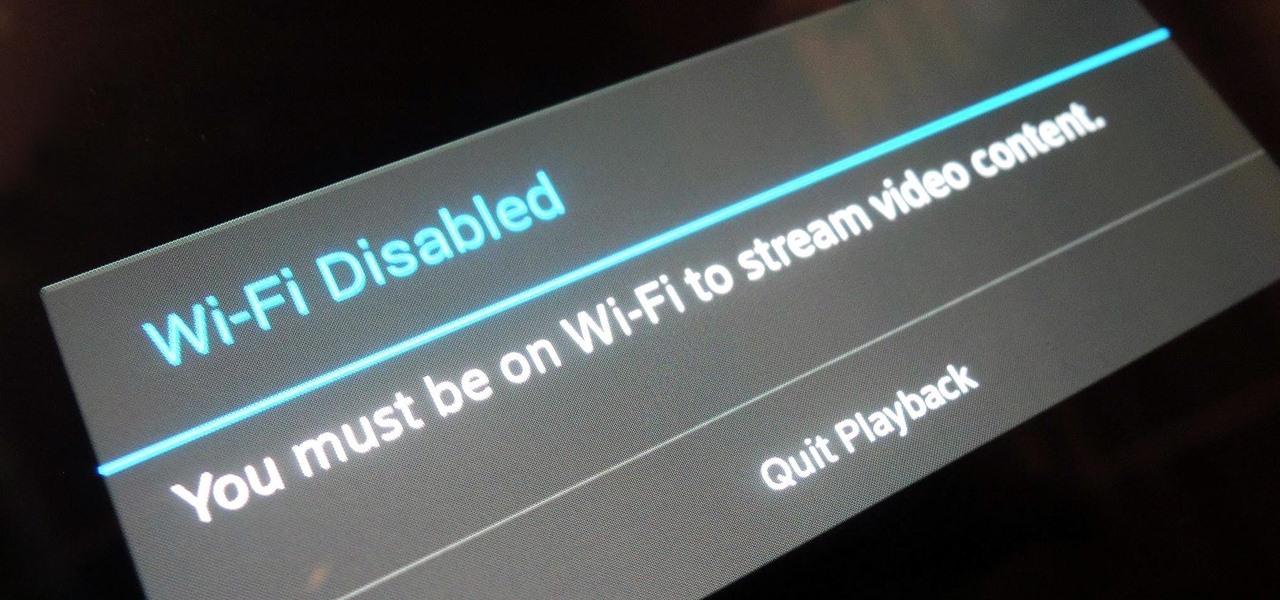
For any multitude of reasons, some apps require you to be connected to Wi-Fi in order to function properly. This could be because they would rather you have a stable connection to enjoy their content, or that they don't want users complaining about the amount of data being guzzled from carrier data plans.

Screen timeouts serve mostly as security measures and energy savers, but they can also interrupt you when you're reading a book or editing a document. There is no built-in way to manage screen timeouts on a per-app basis, but if you've got root access, you can do just that using Never Sleep from Android dev Hamzah Malik.

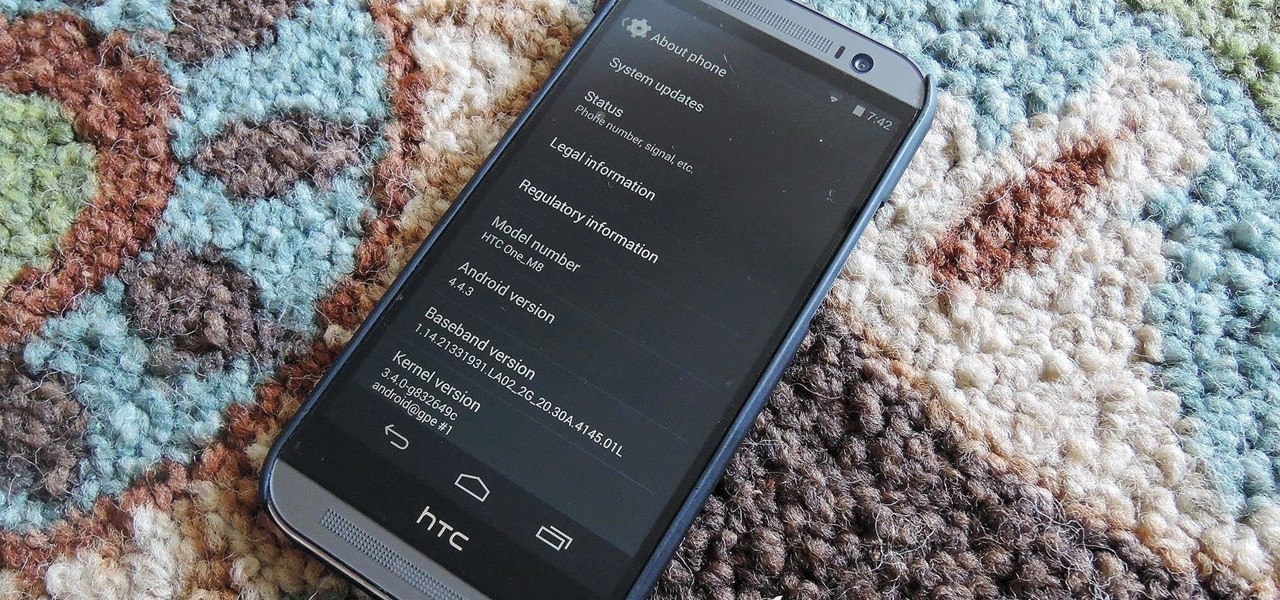
The beauty of having a Google Play Edition HTC One is the ability to get as close to stock Android as possible while still getting some extra non-Google, proprietary HTC features. The newest version of Android, 4.4.3, has just hit the Nexus and Google Play Edition line of phones, but if you are rooted with a custom recovery, you will not be able to apply the OTA.

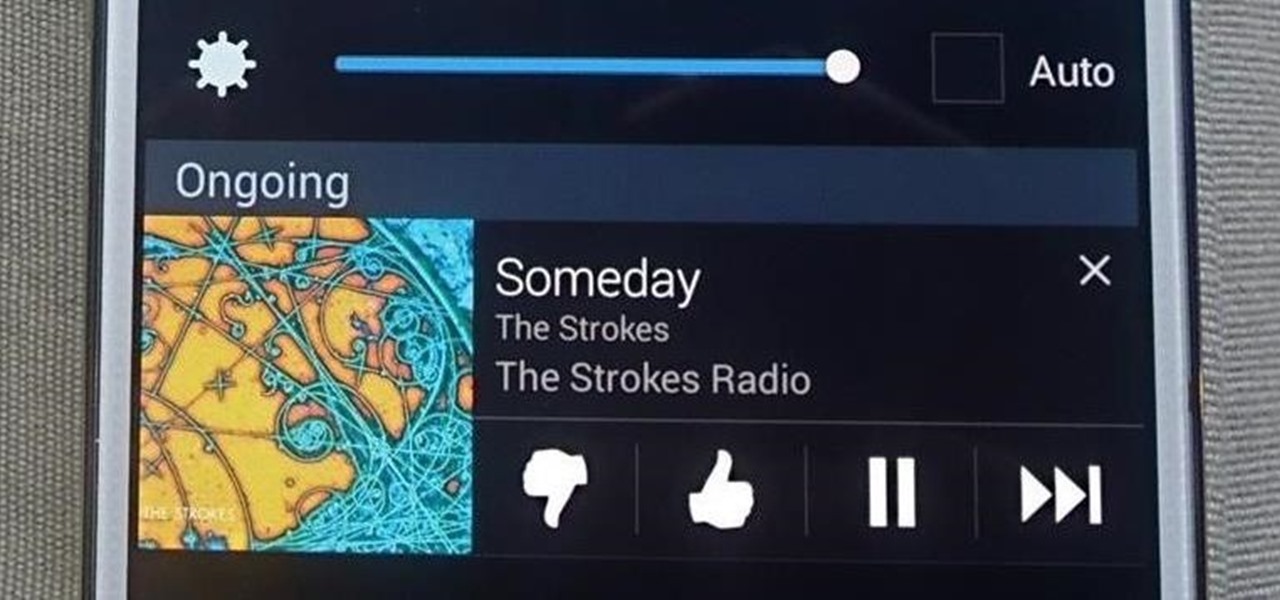
According to a recent survey conducted by Edison Research and Statista, Pandora still has a firm grasp as the most popular music streaming service in the United States. With iHeartRadio, iTunes Radio, and even Spotify trailing behind by a large margin, it doesn't look like Pandora will lose their footing in the near future.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

HTC's Sense 6 has been out for over a month now with the One M8, and most of you have probably played around with its better known features, like the new Camera app and Harman Kardon audio.

Look away from this screen and try to remember the sound of your childhood hero's voice. Did you do it? Do it again, and this time pay attention to your eyes.

One subtle change that Samsung made with the Galaxy S5 is their replacement of the Menu softkey with one for recent applications. Instead of holding down on the Home button, we now have the Recents button, which is used for easy access to multitasking.

In today's dog-eat-dog world, every minute matters. Whether you're in school or working for the Man, a huge amount of your day is consumed by tasks, assignments, and other kinds of work. Then there's the time you spend playing video games, watching TV, or screwing around on your Samsung Galaxy S3.

The iOS 7 lock screen was made to be just that, a lock screen, so it's pretty limited in terms of functionality. We're able to add wallpapers and easily access the Control Center or Notification Center (unless we disable that access through our settings), but other than that, it's pretty bland.

Recently, Mike over on Samsung Galaxy S4 softModder showed how to scroll from the bottom to the top of a page with a single tap, a feature that Apple is well known for, and something I missed very much on my Galaxy Note 3. However, there's always room for improvement.

Starbucks' app is the most used mobile payment app in the U.S. because it's well-designed and convenient. But if you use the iOS version on your iPhone, your username, email address, password and location data could be compromised because the app stores them in plain text.

Lenovo brought out the big guns for CES 2014, with the Vibe Z showcased as the Chinese company's' first foray into the LTE smartphone space. Slated for a February release, the ultra-thin and extremely light smartphone will certainly be in the running for top smartphones of this very new year. Photo via CNET

Like what iMessage is to iOS, Google Hangouts is to Android—allowing users to share messages instantly, as if quickly wasn't good enough. With Google Hangouts, you can share locations and send maps, receive and send SMS, share animated GIFs, make video calls, and chat not only with your phone's contacts, but also your Google+ and Gmail buddies.

It seems like most of the really cool and interesting modifications you can make to your Android device always require special root access, so when a fun mod comes along that doesn't require root—I feel it's my duty to alert you.

Smartphone users these days can get bombarded with texts and emails every hour. Online retailers sending you coupons to get you to buy stuff. Girlfriends asking where you are. Service providers reminding you to pay your bills on time.

When you're on the go, it's important to keep your belongings organized and at an arm's distance so you're not fumbling in public for your keys, cards, or phone.

For new Android users, rooting an Android phone can often be an intimidating process, especially since there are so many different ways to gain root access, depending on your model and firmware version.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.

Are you a messy burger eater? Ants and fruit flies invading your home? Hate drinking warm drinks? Find out the quick and easy DIY solutions to these problems with these 10 amazing tips and tricks for the summer.

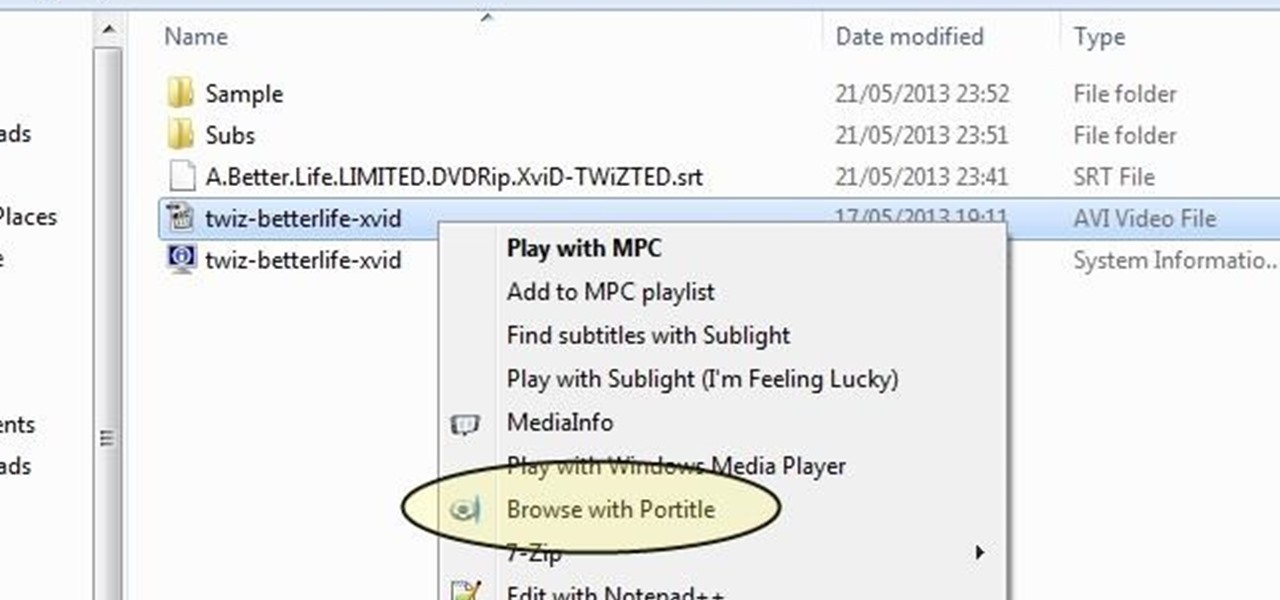
Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

There's something missing on your brand new Samsung Galaxy S4, and if you're a softModder like me, you know exactly what it is already. If you don't know, keep reading, because you should—anyone who wants a better Android experience should.