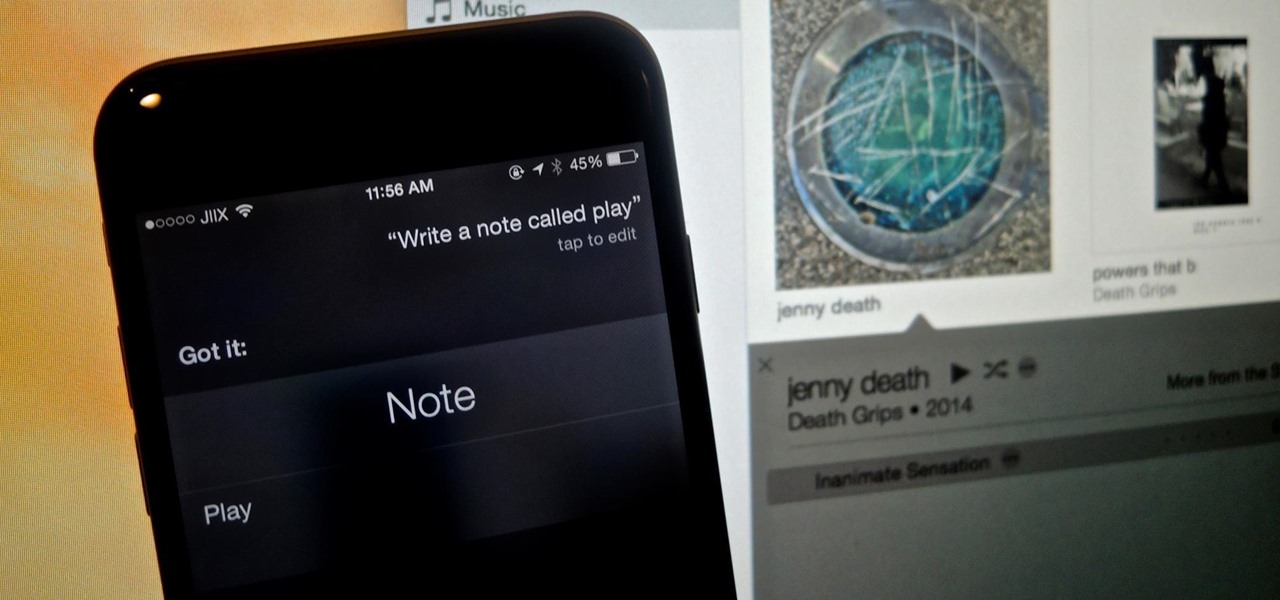
This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

One of the great joys of cooking is taking the most basic of foods and preparing them in new and exciting ways. About two years ago, my wife opened my eyes to a delicious staple of Indian and Moroccan cuisine that is made in a very elementary way, the preserved lemon.

It is a truth universally acknowledged that food molded into fancy shapes somehow seems tastier. That's true even with chocolate, which is inherently delicious. Now, while you can buy chocolate that's been pre-molded into fancy shapes, you can have a lot of fun and save a few bucks by making your own specialty chocolate molds. All you need to get started are items you most likely already own.

If you're a fan of Thai food, I'm sure you're familiar with sticky rice. There is something so special about its chewy texture and sweet flavor. If you have a desire to make it in your own kitchen but don't have the proper tools such as a traditional bamboo basket or stackable steamer, there are several other methods that work just as well. Once you try these alternative methods, I'm sure you'll be "sticking" to them for a while. What Makes Sticky Rice So Sticky?

Lasagna, that layered, creamy baked pasta dish, is a lovely comfort food that's great for a crowd. But if you've ever made it, then you know you're usually left with some leftover lasagna noodles. (Although that's always better than the frustration of running out of the noodles while you're still making a traditional lasagna.) Still, what do you do when you're still left with a bowlful of the wide ribbons?

Christmas trees, once decorated and brightly lit, are the penultimate holiday decoration, but authentic pines lose their brilliance fast without any nourishment. Plus, they are major fire hazards without regular hydration. But watering one requires a lot of sliding around on the floor, and it can be hard to tell how much water is in the bowl beneath the dark, prickly branches. These five hacks can help!

While Apple's Continuity feature has certainly impressed me, I can't help but feel like it could be used to create a better connection between my iPhone and Mac. Sure, Handoff allows me to pick up where I left off in certain applications between the two devices, and it lets me pick up calls and send text messages on my Mac, but I want even more functionality.

It's that time of year again, folks. Each fall, Google debuts a new device alongside the latest iteration of its mobile operating system—but this year marked the release of three new Nexus gadgets.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Food is a necessity, sure, but every now and then it's so satisfying to eat something because it is fun and delicious. While eating a whole tub of homemade ice cream might satisfy your need for gluttony, there's a way to take it even further—make your dinnerware edible.

We've already taught you a few tricks for getting chilled, rock-hard butter to spread easily on toast, and some of you probably bypass that issue entirely by purchasing spreadable butter from the supermarket. But why waste your money when you can make a healthier, tastier version at home for a fraction of the cost?

Let's be honest, most of us buy the bottom-shelf vodka either because we're broke or because we're going to disguise the gag-inducing taste of it with juice or something fizzy. If you're cooking or baking with vodka (ice-cold vodka works wonders in pie crust), what's the point of buying Belvedere?

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Nintendo fans rejoice! Not only can you play classic NES games on your iPad or iPhone without jailbreaking, you can play Game Boy Advance and Game Boy Color games. And that's not it. Now, thanks to @angelXwind, we can add Nintendo DS to our list of non-jailbreak emulators for iOS 7.

If you don't want to wait for Android 4.3 Jelly Bean to hit your HTC One, you don't have to. Android developer LlabTooFeR released his MaximusHD ROM, which includes a leaked copy of HTC's own 4.3 update, complete with Sense 5.

Considering that the average movie ticket these days is $8.38, it's not much of a surprise that Netflix is kicking ass. The same amount will get you a full month of unlimited streaming, and you don't even have to leave your couch. While no one's arguing that it isn't a great deal, the biggest issue most users have with the service is the limited amount of available content. Anything?

One thing that gets overlooked on Facebook is the amount of videos you can watch, and I'm not just talking about videos uploaded directly by Facebook users—I mean everything ever shared—YouTube, Vine, Instagram, Vimeo, etc.

With warm weather comes bugs, and with bugs come bites, and with bites come itches. From ticks and spiders to mosquitoes and bees, insect bites come in sundry shapes and sizes, but they all commonly pull an itchy, red reaction out of our bodies.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

There are hundreds of keyboard shortcuts out there, but these 7 are the ones you'll definitely want to remember. I use them every day, and you should too. Step 1: Tab Domination

In the UK, 20 percent of divorce filings include the word "Facebook." You may think you're being slick by using the site to chat with your ex, but the problem is that Facebook saves everything, and I mean everything. All someone needs is your login information and they have access to everything you've ever said on Facebook, public or private.

We've all been there. Your phone is on your nightstand, but you're on the couch in the living room browsing the web on your Nexus 7. Then you hear it—a faint sound for a new text message notification from the bedroom.

Prepaid phones are becoming more and more popular, and tons of people can see the benefits of switching now that some companies are offering prepaid services that are on par with the big players. For a lot of folks, the only thing keeping them from switching is the huge early termination fees that service providers charge to break a contract early.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Offensive pictures, depressing tweets, political statuses, and just plain old dumb comments are only a few of the reasons why people unfriend or unfollow others on social media sites. Sometimes it's just social spring cleaning, other times there's no reason at all.

For the vast majority of people, coffee is a must-have in the morning. It provides a stimulating effect that not only wakes you up, but sets your mood and attitude for the rest of the day. Personally, I wouldn't get anything done without coffee.

There's nothing like buying an awesome new gadget, but it leaves you with one problem (besides an empty wallet)—what do you do with the ones you already have? There are plenty of ways to put your old gadgets to use, but if you'd rather get rid of them, you may as well get something out of it, right? Here are five places where you can recycle your electronics and replenish your cash stash.

Last week, we rolled out a major site-wide update on WonderHowTo, making it even easier to follow the subjects you're passionate about—and easier to share your creations with people who'll give you the kudos you deserve!

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

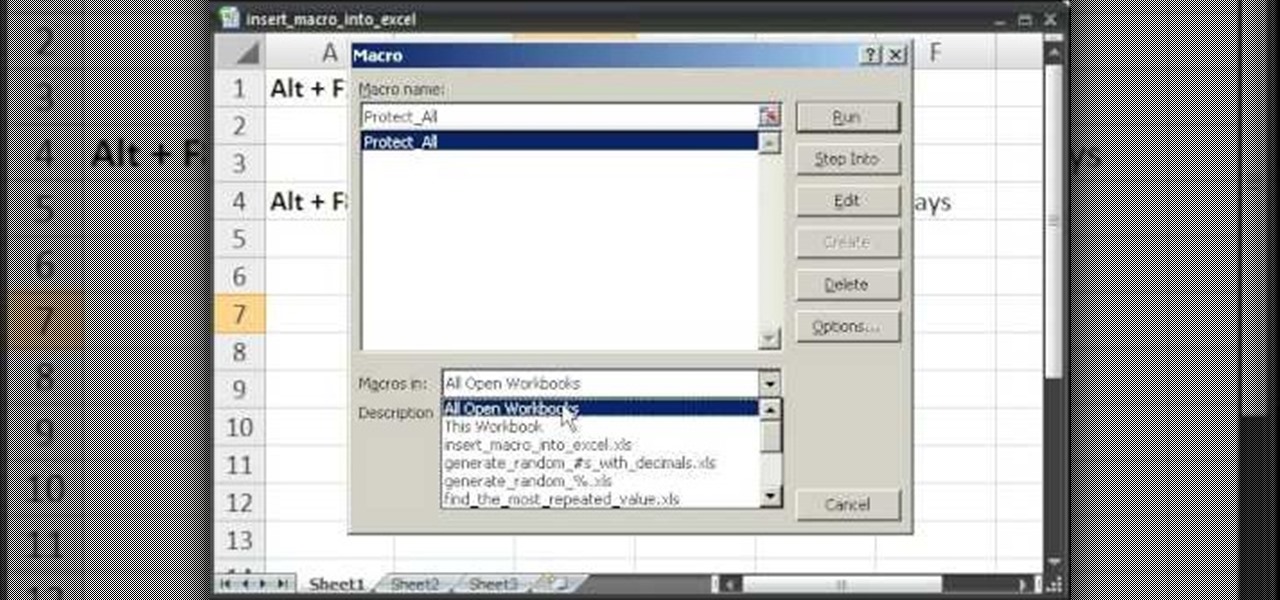
This video takes us through a process of inserting Macros from internet into a excel workbook. Two shortcuts Alt-F11 and Alt-F8 is used. Alt F-11 is used to open the visual basic window and Alt-F8 is used to open macro lists window that opens all macros. These shortcuts work in most versions of Excel.The steps followed:1. Go to internet explorer and the site selected is Teach Excel and in the home page you have to select free macros, you will come to page of macros.2. You can simply select th...

Create lasting memories by organizing a well-planned family reunion. This video will show you how to organize a family reunion.

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

The quickest way to get a gorgeous lawn is to lay sod, uniform patches of grass-covered soil held together by matted roots. It will go more smoothly if you know a few landscaping tricks. Learn how to lay sod for a perfect lawn with this how to video.