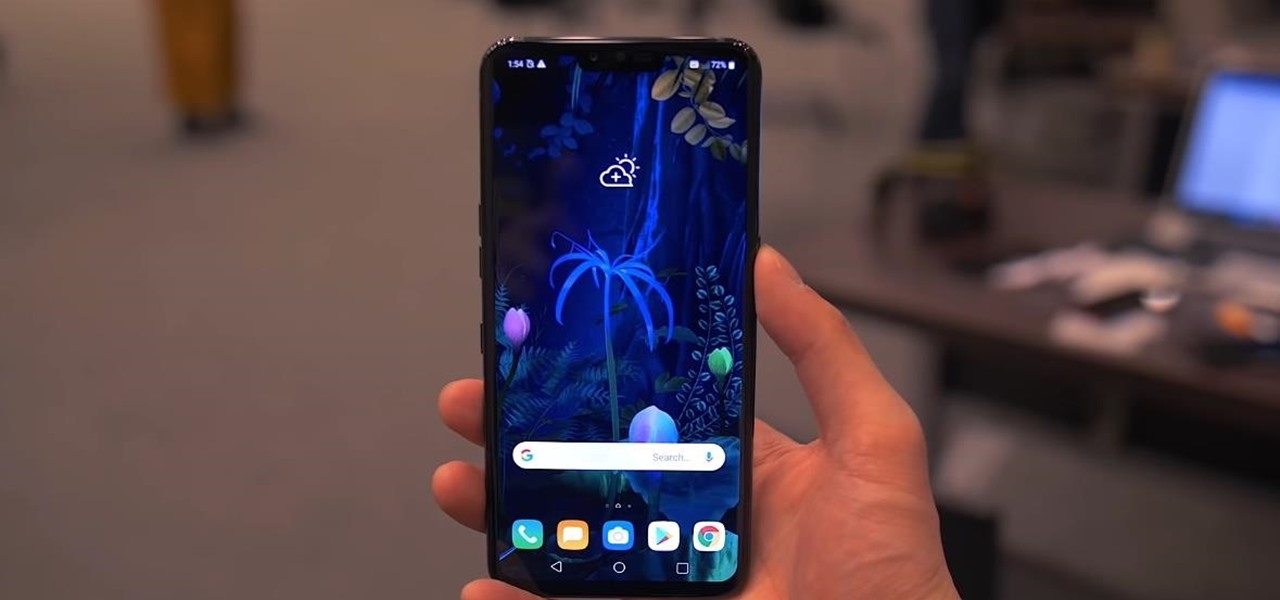
Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.
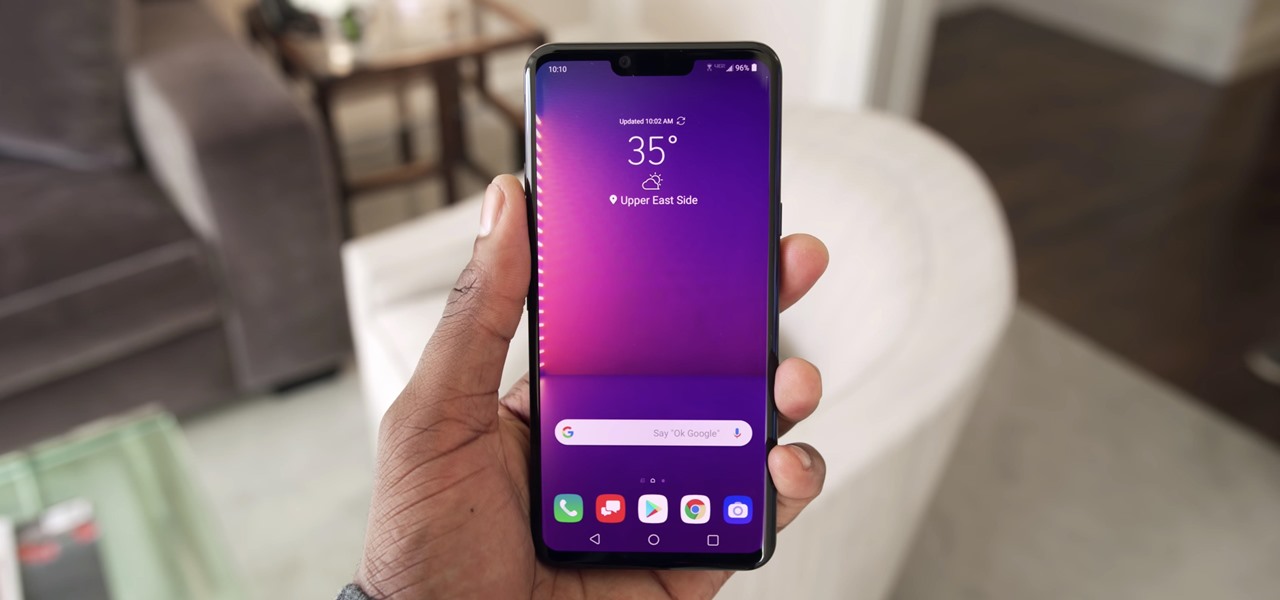
Once again, LG is mixing up its launch. Instead of the announcing the latest entry in G series later in the year, the LG G8 ThinQ was announced at Mobile World Congress 2019, shortly after Samsung's Galaxy S10 event. And instead of trying to match what other OEMs are doing, LG is once again trying to be different.

While Apple has moved on from Touch ID to Face ID in newer iPhone models, there are still plenty of iPhones with fingerprint sensors — in fact, Apple's second-generation iPhone SE is the first new Touch ID iPhone in three years. With Touch ID, you can register up to five fingerprints, but it doesn't stop there. Using a little-known trick, you can sneak another five fingerprints in there for a total of ten.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

To combat their poor coverage in rural areas, T-Mobile spent nearly $8 billion on 600 MHz spectrum in 2017, which was converted to LTE Band 71. With such a low frequency, the signal can travel further, providing LTE speeds to more Americans. But your phone also has to support this frequency, and so far, only a handful do.

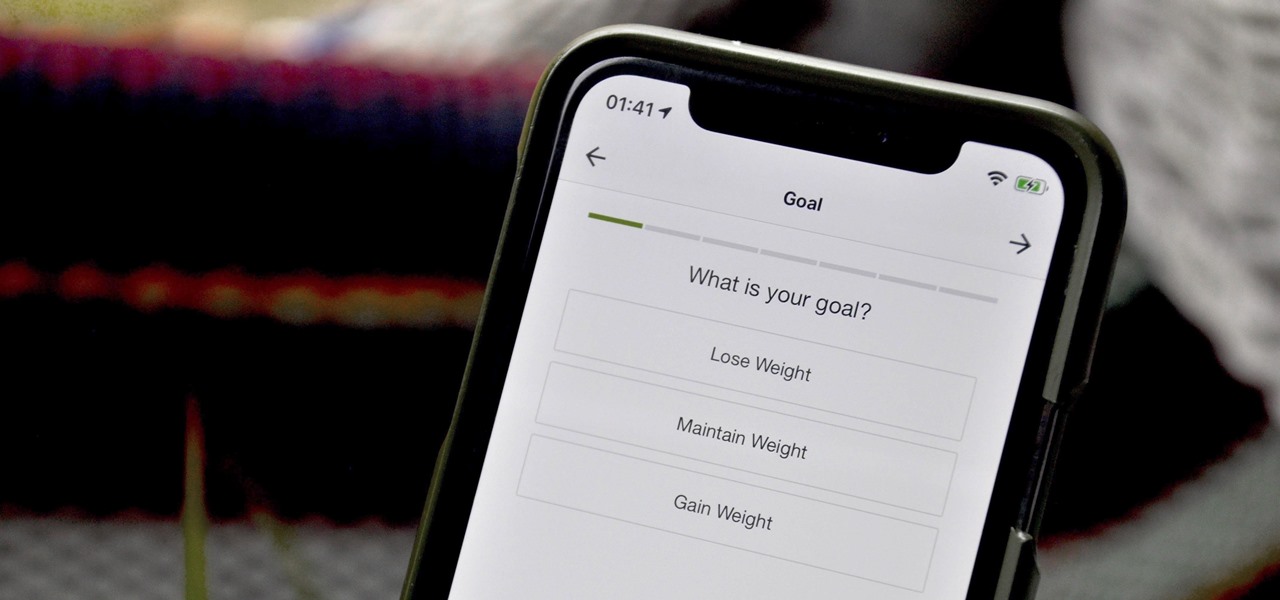
When you set up your MyFitnessPal account for the first time, it asks for a checklist of personal info to create nutrition and fitness goals for you. Whatever you decide then, it's important to know that the goals provided to you are not fixed. If your doctor or nutritionist recommends a new plan, or you simply want to change up your routine, you can customize your weekly and daily goals.

Sony Pictures has tapped the powers of augmented reality as provided by startup 8th Wall & the Amazon Sumerian development platform to help it promote the latest motion picture manifestation of Spider-Man.

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.

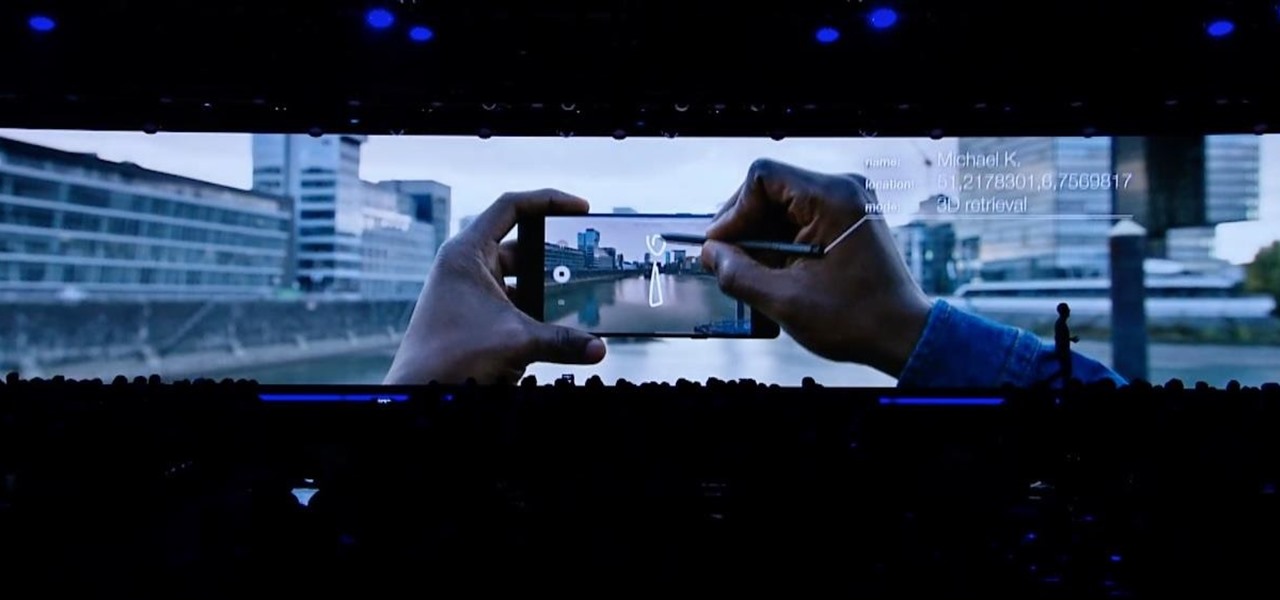
This week, at its developer's conference, Samsung took the wraps off a new tool from Wacom that bestows the S-Pen with AR powers, as well as its own entry to the AR cloud market called Project Whare.

This week, inside sources divulged details of how Apple nearly acquired Leap Motion, twice. Otherwise, companies offering or working on augmented reality technology had more successes than failures to talk about.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Android does a great job at multitasking. Split-screen mode and picture-in-picture are terrific at letting you manage more than one app at a time. But there are some limitations. For instance, when you're playing a video and you open a second video in split-screen, the first one pauses. Thankfully, Samsung has a fix for this.

The iPhone XR is the best bang for your buck option among the 2018 iPhones. Splitting the XR and XR Max right in the middle with screen size, it makes small compromises to to keep the price low. However, with the release of the Galaxy Note 9, Samsung has their own formidable middle option as well, the Galaxy S9+.

The ongoing war between Apple and Samsung fans will rage on once again. With the release of the iPhone XS Max, Apple has presented a stronger adversary for the Samsung Galaxy Note 9, released earlier. Both stack up well against each other, providing two of the best experiences on their respective operating systems.

With this year's iPhones, Apple built upon the success of the iPhone X in a somewhat iterative manner. All three phones borrow from the 2017 flagship's design, which many praised as being the best in years. They also tried to help those of us who don't have more than a grand to spend on phones, creating a new product with a few compromises.

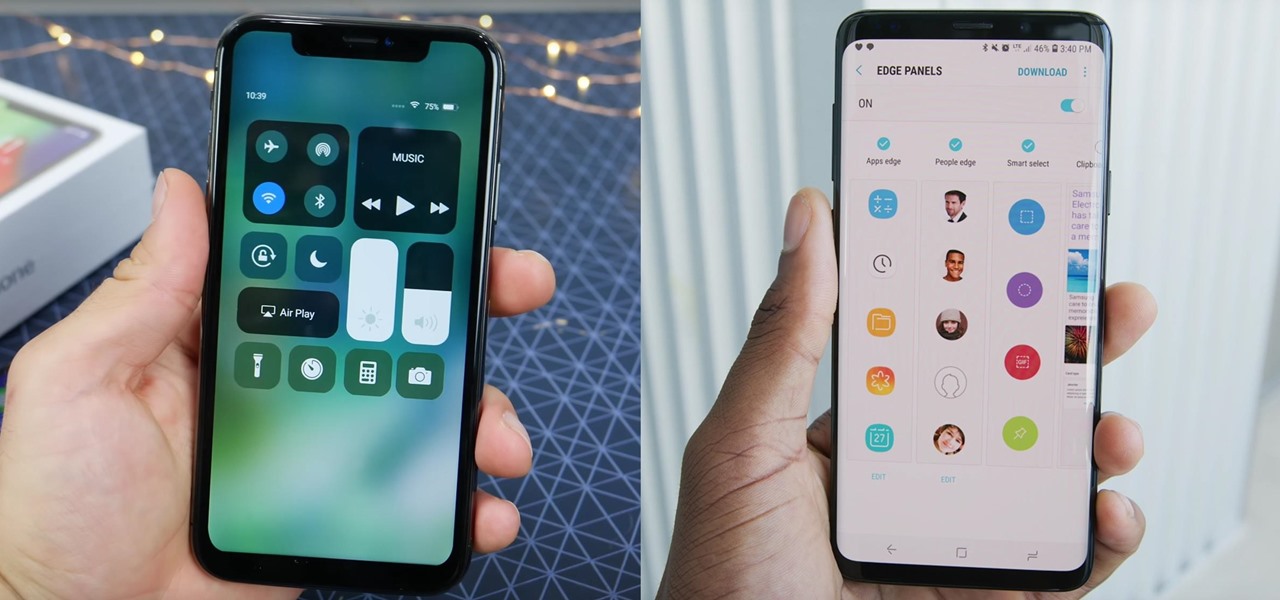
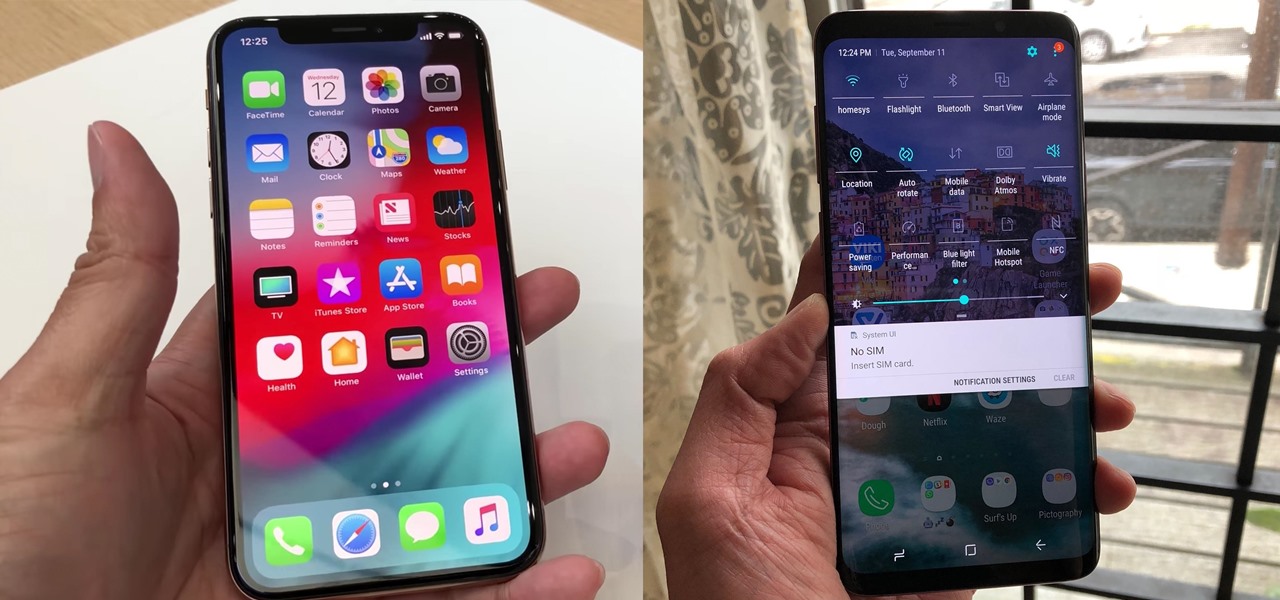
Until next March, the iPhone XS and Samsung Galaxy S9 will be the only phones considered by many. Whether you're an Apple fan wanting to see how your new phone stacks up against the competition or a buyer on the fence, here's how the latest flagships from the two biggest brands compare.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

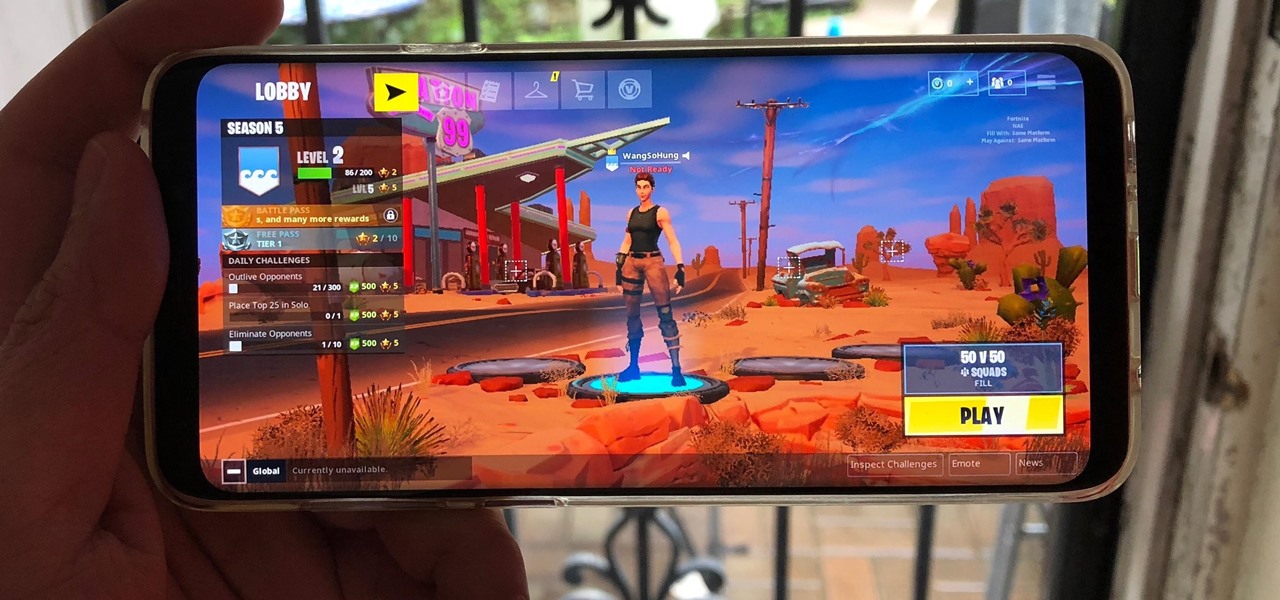
Fortnite's long awaited arrival on Android has ramped up excitement among gamers who are installing the beta version in astounding numbers. With so many midrange and budget devices running Android, however, it's important to stay on top of your device's performance to ensure smooth and uninterrupted gameplay.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

While Sony as a company is well-known in the United States, it smartphones are not. For years, Sony has stuck with a boxy design with sharp edges and large bezels — however, they're finally getting with the trends. As a result, the Xperia XZ2 Premium offers a rare combo: A super powerful phone which is also pretty sexy.

Some of the big guns developing augmented reality technology fired shots at their competitors with announcements and leaked plans this week.

Before starting any drive where you're using Google Maps for directions, it's vital to make sure the app is functioning correctly, specifically, navigation prompts. After initiating turn-by-turn directions on your Android or iPhone, the last thing you want to worry about is Google Maps not audibly telling you where or when to turn, especially in an unfamiliar area.

After delaying its launch by four months, LG revealed its 2018 entry to the flagship market on Wednesday, May 2. After years of an underperforming mobile division, the LG G7 ThinQ is the first product since a shakeup within the division to get things back on track, and it brings a number of upgrades over its G6 predecessor.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

Great ideas often strike at random times, but messaging friends and loved ones at an inopportune hour not only risks their wrath, but also increases the chances of your message not being paid proper attention to. Thankfully, there's an app that lets you create and post WhatsApp messages at the time you wish for maximum effect.

Earlier this year, Nokia released the Nokia 8 Sirrocco overseas. The new device served as an upgrade to the 2017 model with a minor specs bump and a more modern design. However, HMD isn't done with the 8 series. A rumored Pro version is coming later this year that brings innovations the iconic brand is known for.

Since making waves at Mobile World Congress 2018, Android Go devices have slowly trickled their way onto US shores. Only one device was officially announced for the US at MWC, but several OEMs have extended availability to the US in the months since, and it looks like we just received another.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

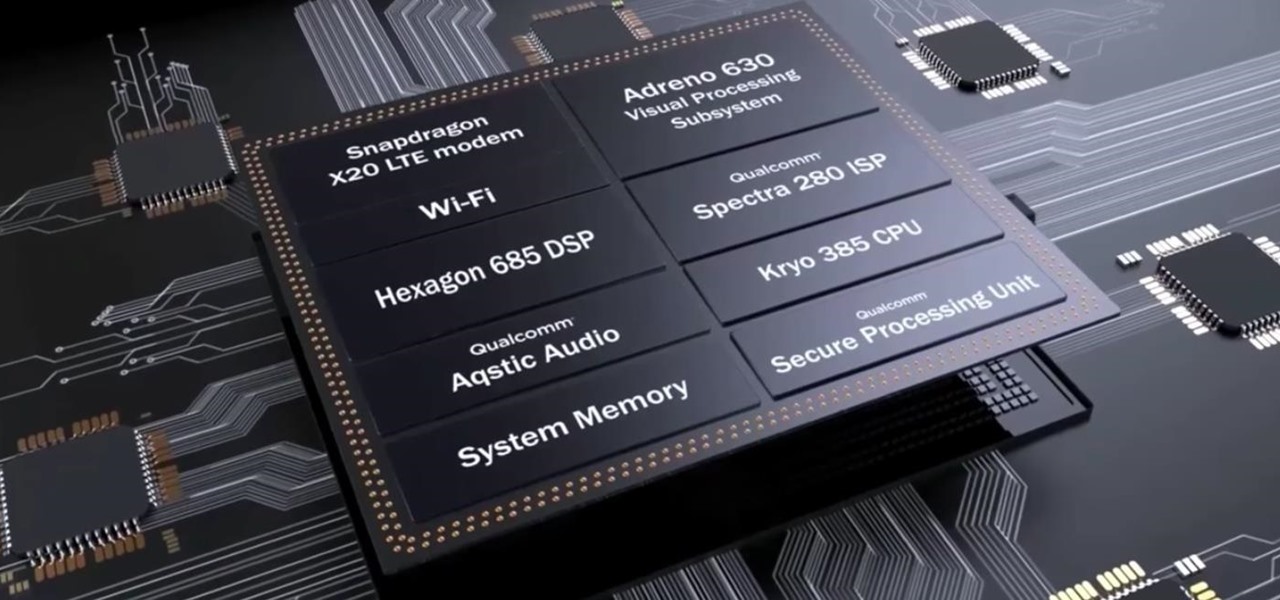
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

2017 was a down year for HTC. First, the U11 and U Ultra were widely criticized. Later, Google purchased a large chunk of HTC's manufacturing division, leaving the Taiwanese company running with a skeleton crew after losing 2,000 key employees. But that's not stopping HTC — their flagship U12+ was just announced, and it's quite impressive.

UPDATE: The P20 and its variants are officially available now. However, there's no official North American variant. You can purchase the international version of the P20 Pro or P20 Lite on Amazon, but be aware that it may not work perfectly on US carriers.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Over the years, Nova Launcher has widened its audience. No longer is it simply a tool to return your home screen to a more stock look. With Nova, you gain customization tweaks and functionality unavailable with the stock launcher. One example of this is all of the cool stuff you can do to organize your app drawer.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

Apple's Mail app for iOS isn't a bad email client by any means. However, it just doesn't cut it for iPhone users that want a more intelligent and advanced email solution. If you're in the market for an app like that, Spark is absolutely your best bet.