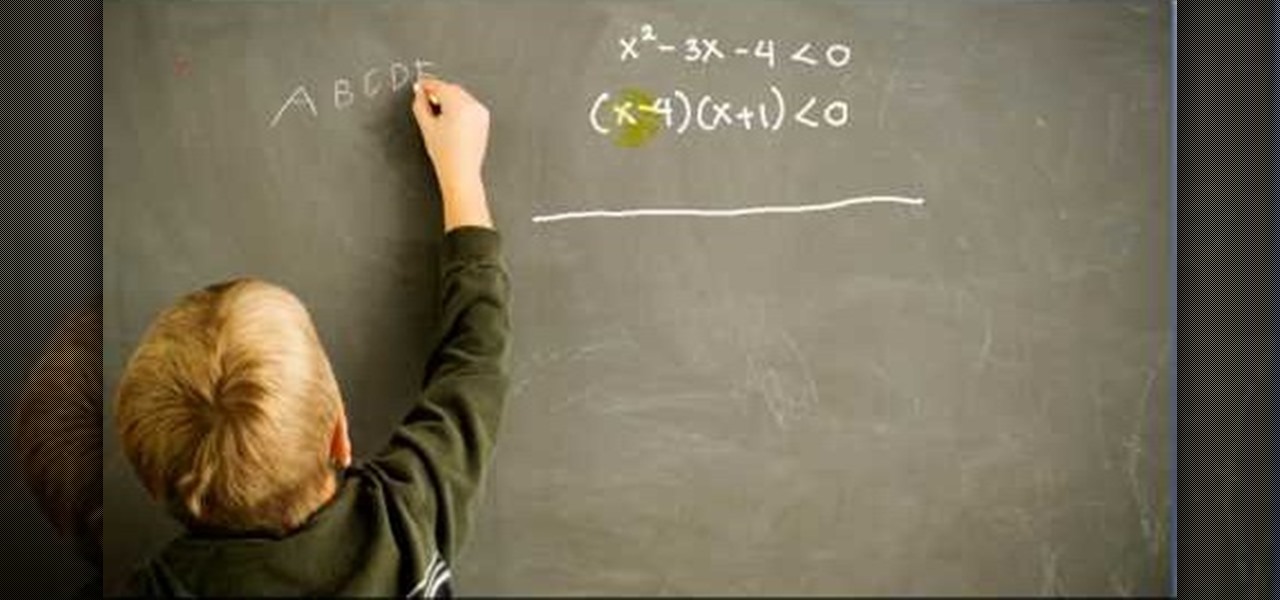Scarlett Johansson is one of the most gorgeous women in the world, so she doesn't need much help beauty-wise with makeup and styling to look good. But for her recent ad campaign for Dolce and Gabanna makeup, she totally turned up the bombshell factor and went all out with sizzling Sophia Loren-inspired eyes and plush nude lips.

Want to look like a blond Playboy bombshell? This tutorial goes into a red rust/silver smokey eye that complements blue and gray eyes (you can always wear contacts in those colors if you have them). The look is inspired by Kendra from "The Girls Next Door."

Watch as amazing make-up artist, Kandee Johnson transforms herself into Barbie with this step-by-step tutorial on how to apply the make-up and look of this famous blond bombshell doll! The following eyeshadows were used to achieve this look: MAC in Pen & Ink, Da Blng, Carbon, Vibrant Grape, Indian Ink, Fig 1, and Deep Damson. LARENIM mineral eye shadows in Bedazzle & Lust and Urban Decay's eyeshadow in Grifter were also used. Additionally used: Hot pink blush as eye shadow, Make-Up Forever ho...

Dovid Krafchow, the author of Kabbalistic Tarot, explains the meaning behind the Mayan calendar according to Jewish knowledge and scientific investigation. Check out this video to learn how to understand the Mayan calendar.

Victory rolls are probably not very familiar to you, but they would have been had you lived about, oh, sixty years ago. Victory rolls, or tight, thick ringlets centered on the crown of the head and sometimes done up in a Bettie Page style bang, were the style du jour of the '40s and '50s.

Being patriotic for the Fourth of July doesn't mean you have to completely surrender your fashion sense! Gianny L, master DIY fashion guru, will show you in this video how to snip a bikini out of an old tricolored shirt.

Today on the Victoria's Secret Fashion Show runway you'll definitely see more smoky eyes than you can count. But don't expect to see your run-of-the-mill black and brown smoky eyes. Rather, this year it's all about amazing, dazzling color.

The Victoria's Secret Fashion Show airs tonight, and we're pretty damn sure that by the end of the sparkling, lingerie-filled affair you'll be in ripe mood for some sexy bombshell hair and makeup looks.

We always knew that Taylor Swift was a bombshell, but it wasn't until her 2010 VMAs performance that we saw just what a retro doll she could be. While Swift usually favors light and bright makeup colors that emphasize, rather than overwhelm, her natural beauty, she went all out for the awards show.

We seldom see Kim Kardashian on camera - whether it's formally at a red carpet event or just being captured by the paparazzi while shopping - without a full face of makeup and perfect ringlets in her locks.

Illustrator Frank Frazetta knew women. At least, he knew what men desired in the "perfect" woman physically: Sumptuous curves that made men weak in the knees with a single shake, deep-set eyes, and bombshell assets.

This video makeup lesson demonstrates a Halloween look for fairy or princess inspired makeup. This look was achieved with the following cosmetic products Bare Minerals foundation, Ben Nye e/s in: Ice, Cosmic Violet, Amethyst, Cosmic Blue, MAC Blue Flame e/s, Revlon Colorstay liquid eyeliner, false lashes, rhinestones & glitter from the craft store, Ben Nye Glitter Glue, Duo glue, Ben Nye Neutral Set powder, Nars Desire blush, Rimmel Indian Pink lipliner, MAC Bombshell lipstick, and NYX Salsa ...

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Calculus can be a bit tricky, but don't worry, Watch Math is here to help you out. Watch this math video lesson to learn how to solve quadratic inequalities in calculus. There's no better way to learn mathematics than from an advanced mathematician, like this PhD.

Austin Paranormal Investigations shows how

In the old days, makeup was so glamorous. This tutorial makeup will teach you how to look glamorous in an old sense, just like the Blonde Bombshells of the red carpet. Watch this and learn to apply your face just like the beauties of old.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

In this video from TheCurrentCustom she teaches how to enhance your breasts. First she says you need to measure your breasts to figure out the right kind of bra for you. Take the measuring tape below your bust, and wrap around back, and then measure right above your bust. Round down to the nearest even number if you get an odd number. Then measure your bust size by wrapping the tape measure around the largest part of your bust, typically where your nipples are. Then subtract the bust size fro...

Uber has lost market share to Lyft, its main competitor. Uber's US market share dropped from 84% to 77% between January and the end of May this year, and the ride-sharing company has continued to run into legal, public-image, and internal trouble. Lyft, on the other hand, has been growing.

In March, we wrote about the growing threat of yellow fever in Brazil. At the time, the disease had killed just over a 100 people. Unfortunately, the disease has only spread since then with many more people infected and more killed.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

A lot of girls fear red lipstick and retro pin up girl looks for one main reason: they're simply too over the top. But skipping out on this classic and timeless makeup look means skipping out on one of the sexiest ways you can dress your face.

Smash glow? What the heck is that? That's exactly what you'll find out… watch this science video tutorial from Nurd Rage on how to make smash-glow crystals (triboluminescent crystals) with Dr. Lithium.

The one man Sam Fisher trusts, Victor Coste, has some information for him. To find out the intelligence, Sam has agreed to meet in person. Find out what the important intel is in this walkthrough for the Washington Monument (Mission 5), and where that lead Sam next.

Take a trip into the past as Sam Fisher gets captured by terrorists in the Iraq War. Instead of playing as Sam, you'll be playing the part of Victor Coste — the only man Sam trusts. Find out how Coste saved Fisher's life in this walkthrough for the Diwaniya, Iraq (Mission 4). What happens that day in Diwaniyah? Find out.

While conducting an OSINT investigation, it's important to be able to pull in information based on any clue you uncover. In particular, license plate information can turn up everywhere, from photos to live data to on your own street. You could use that data to find the VIN, see if a Tinder date has hit anyone, find out who's blocking your driveway, and so on. Skiptracer can help get the ball rolling.

An older man dies of Zika. A younger man who cares for him catches Zika — but doctors cannot pinpoint how the disease was transmitted. While proximity to the patient is sufficient explanation for the rest of us, for microbe hunters, it is a medical mystery. Why? Zika is not known to transmit from person-to-person casually.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

In recent light of Obama's assertion of executive privilege over important documents concerning the Fast and Furious operation, here's a brief article concerning this controversial power.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

On June 11, 2016, an Arizona woman died from what appeared to be several infections, including pneumonia. She likely caught at least one of these from her dog.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.