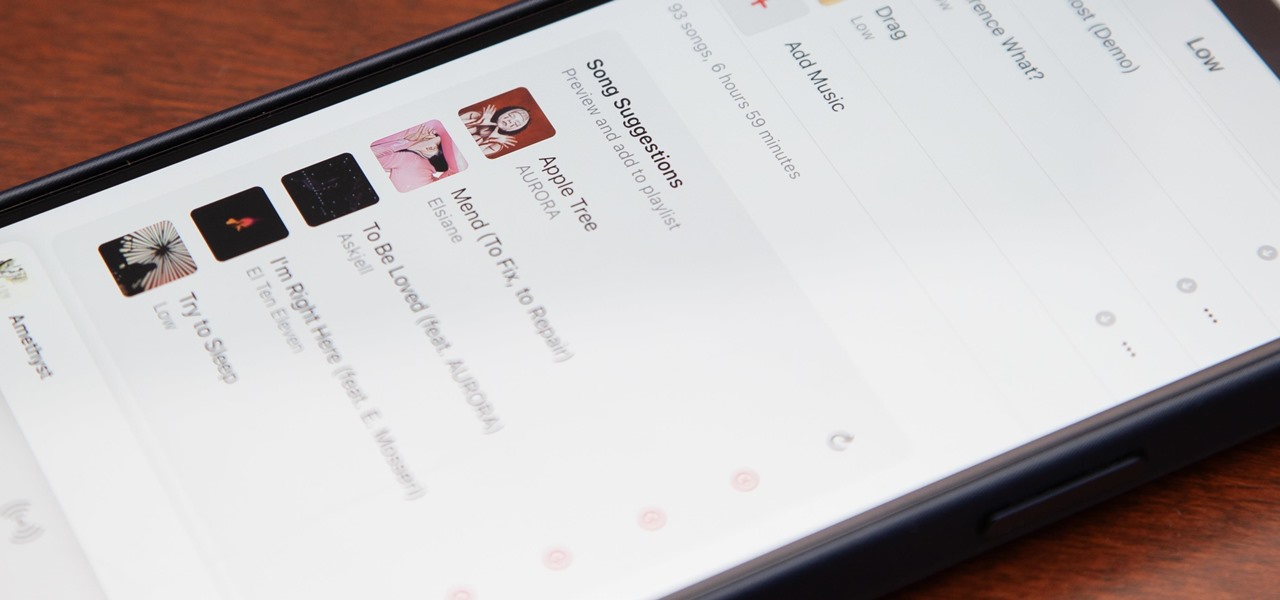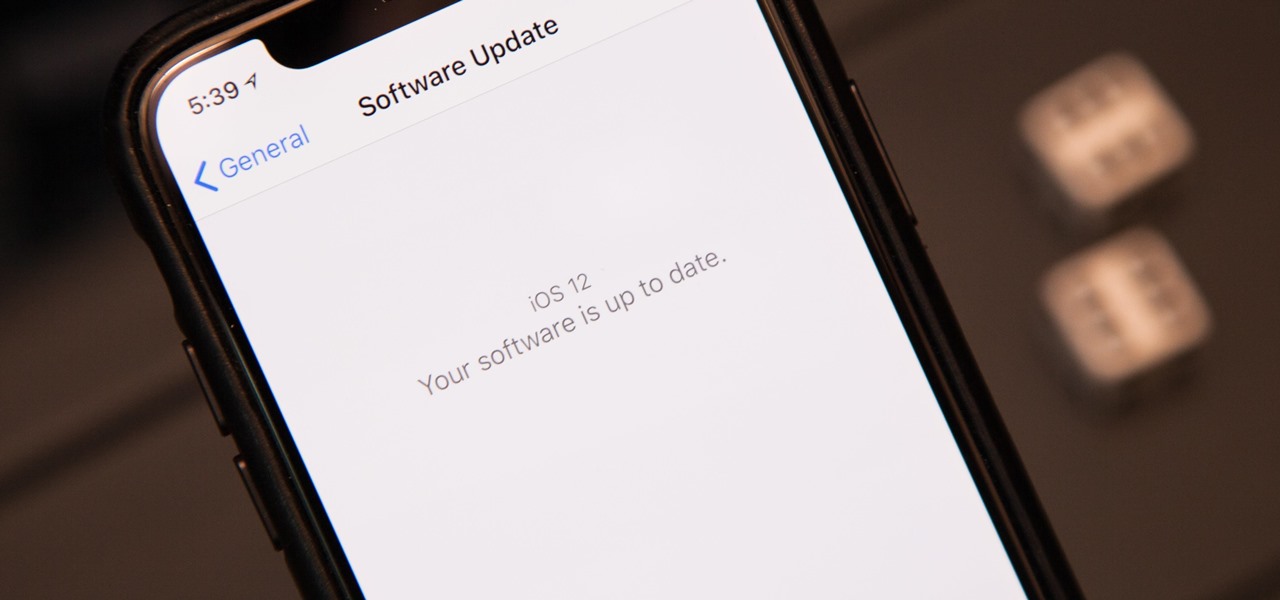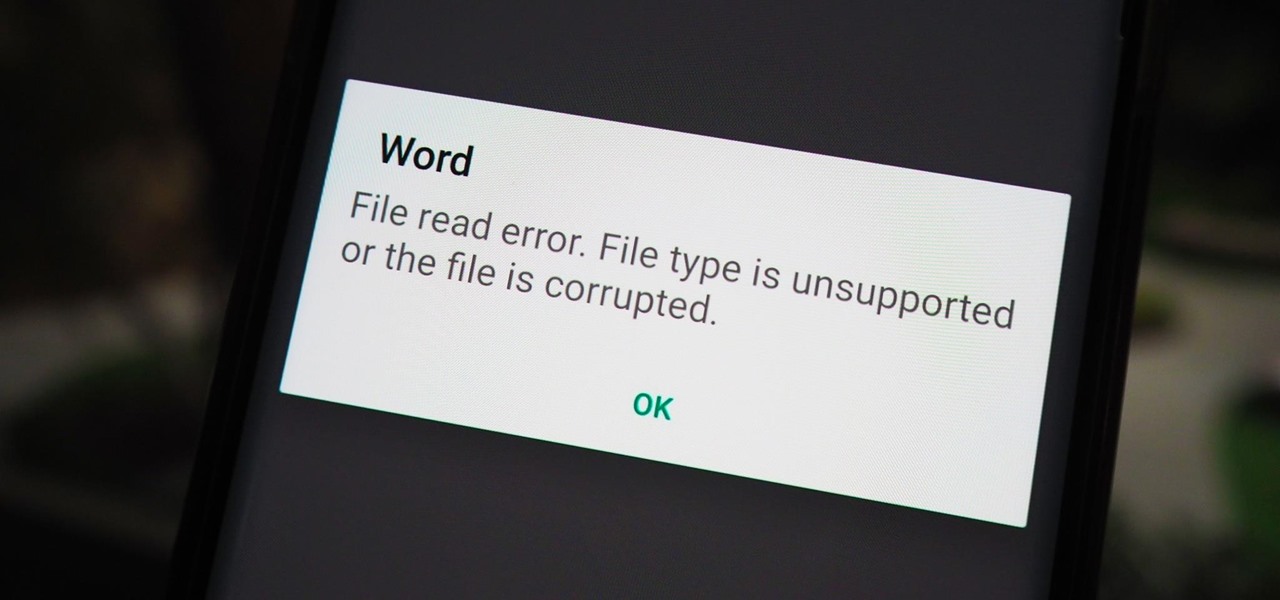
You have an assignment due, whether it's homework for school or a project for work, but you've only got a few hours left. There's no way you're going to finish in time and do a good job, and you don't want to turn in anything incomplete or half-assed. While it may seem you're out of luck, there's a simple way to buy yourself more time.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

Browser extensions are extremely useful since they can expand web browsers like Google Chrome and Mozilla Firefox beyond their built-in features. However, we don't always know who's behind a browser add-on or what it's doing beyond what's advertised. That's where ExtAnalysis comes into play.

The Snapdragon version of the Galaxy Note 20 and 20 Ultra — the one sold in the US — can't be rooted. Without root, the level of customization is limited. Such a large group of Android users shouldn't miss out on mods, and they don't have to.

Are you tired of endless rows and columns of apps on your home screen? Before iOS 14, your only option was to hide apps in folders, uninstall them, or use some sort of elaborate workaround. You could hide a few stock apps easily enough, but that's it. Now, in the latest version of iOS, you can hide apps for real, and even hide entire home screen pages, and still access the apps in one convenient drawer.

The future of TikTok in the U.S. is all but certain. Microsoft, Walmart, or Oracle could save the day by buying the company, TikTok may win its lawsuit, or China's new restrictions could halt everything — but all could fail. Just like Vine before it, TikTok could be on its way out, only for opposite reasons. But will it matter if TikTok gets banned in the States? With the competition heating up, likely not.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

The smartphone market is stagnating. Without hordes of new users rolling in every year, the best way to boost profits nowadays is to poach customers from the competition. That's exactly what Apple appears to be doing with iOS 14.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

After an update on Sept. 22, 2020, the Checkra1n jailbreaking tool expanded its compatibility to include iOS 12.0 to iOS 12.2, as well as iOS 13.5.1 to iOS 13.7. More importantly, however, it now can jailbreak iOS 14 on select iPhone models, with more support coming soon.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

Starting in iOS 13, Apple introduced a robust suite of video-editing tools to its Photos app. The majority of editing tools were only available for images in iOS 12 and older, but iOS 13 leveled the playing field to allow even a novice to tweak videos like a pro before sharing.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Whether you've celebrated multiple cake days or you're just now getting your feet wet with Reddit, it's a rite of passage to choose your preferred smartphone client. Quick spoiler: Your best option most certainly is not the official Reddit app.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Let's say you want to download an Instagram video to your iPhone. What do you do? While Instagram doesn't offer an official solution, there are backchannel methods that exist to get the job done. However, if you want native support for downloading Instagram videos directly to your Photos app, you can start by updating your iPhone to iOS 12 and installing Shortcuts.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveillance – Broadcast, or ADS-B for short.

Apple's first big iOS 17 point update for iPhone just came out, and it includes some of the features initially planned for the iOS 17.0 release last September. But there's much more to iOS 17.1 than that — exciting new features and changes are hiding within Books, Music, StandBy, App Store, Lock Screen wallpapers, Apple Wallet, and more.

There is a whole world of smartphone accessories out there, some of which are more quirky than others and don't get the recognition they deserve. But these sometimes strange, sometimes embarrassing products can really make life easier on your iPhone or Android phone.

Apple just made its most significant update ever to the iOS lock screen, with a lot of features to be excited about. The theme of this upgrade is customization, giving you complete control over the look and functionality of your iPhone's lock screen.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

The new iPhone 12 Pro Max is equipped with MagSafe, the iPhone 12 lineup's most talked-about feature. While Apple previously used MagSafe for its magnetic charging connectors on older MacBook models, it's given new life to it on the iPhone, and in a much better way. But can it do for you exactly?

If you're getting or already have a new iPhone 12 or 12 Pro, its big-ticket feature is MagSafe, something you'll definitely want to explore. While the technology is new to iPhone, Apple used the MagSafe name for its magnetic charging connectors on older MacBook models until USB-C replaced it. Apple's reenvisioning of MagSafe for iPhone is completely different and much more useful.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

Despite making great phones for years, Sony continues to struggle to penetrate the US market. Sales volume has fallen year after year, with 2019 limited to only 5 million units sold globally. To help alleviate this drop, last year, Sony released the Xperia 5, the return to compact smartphones. This year, rumors indicate a sequel is first on their agenda.

Christmas is just one week before Jan. 1. That means a lot of New Year's resolutions filled with promises to better ourselves with increased productivity, focus, and work ethics — but getting started can be challenging. Give the people in your life a leg up this holiday season with these smartphone gifts to keep them on-task in 2020.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

There's never been a better time for streaming videos on your phone. With so many options available (including a potential mobile-only Netflix tier) and so many new smartphones having large screens, there's a good chance you know someone who mainly use their phone for videos. And if you looking for a gift for them, there are some great options.

The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.