Have you ever fallen victim to a clever Jedi mind trick? Don't worry. It happens. There are evolutionary reasons as to why our brains sometimes give into the oldest tricks in the book. Fortunately, the more you understand the tricks of a salesman, the easier it is to avoid their gripping psychological influence. Clue #1: Too Much Specificity

Whether you call 'em soda, pop, fizz, or coke, carbonated soft drinks are among the least healthy beverages out there, yet they're consumed by millions of Americans every day. For those of you worried about your health, there are diet and zero-calorie options available, but are they really better for you?

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Ever drive a friend's car? Maybe a rental? Then you've probably found yourself in a very frustrating situation when you realize you need some gas. Heck, it probably even happens to you in your own car sometimes.

For the most part, nobody makes money off of Facebook. Sure, some people make a living by updating pages for businesses and celebrities, but hardly anyone gets a dime from the site itself.

If you're like me (and everybody else probably), you probably have a few nights of reckless drinking that you wish your could take back, or at least turn down a notch.

Using a second monitor is great for multitasking, especially if you tend to max out your computer's brain power on tons of simultaneously running apps that you want to see, well, simultaneously. That second screen becomes more like a lifesaver.

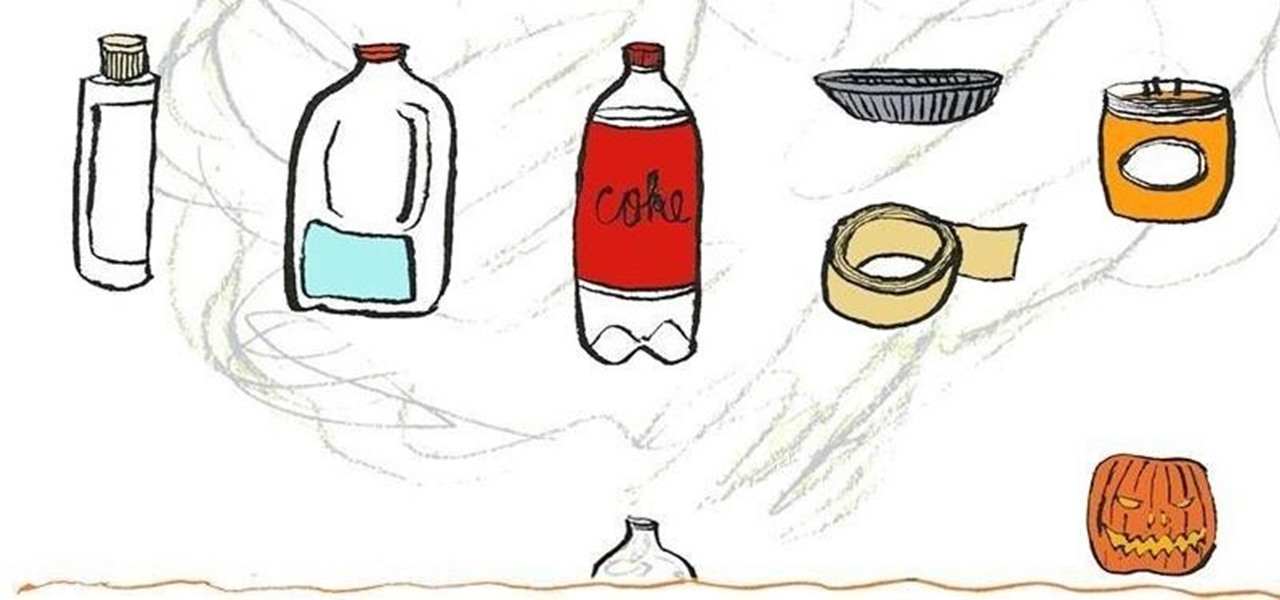
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle of cola, a disposable mini-pie tin, and a big candle in a jar.

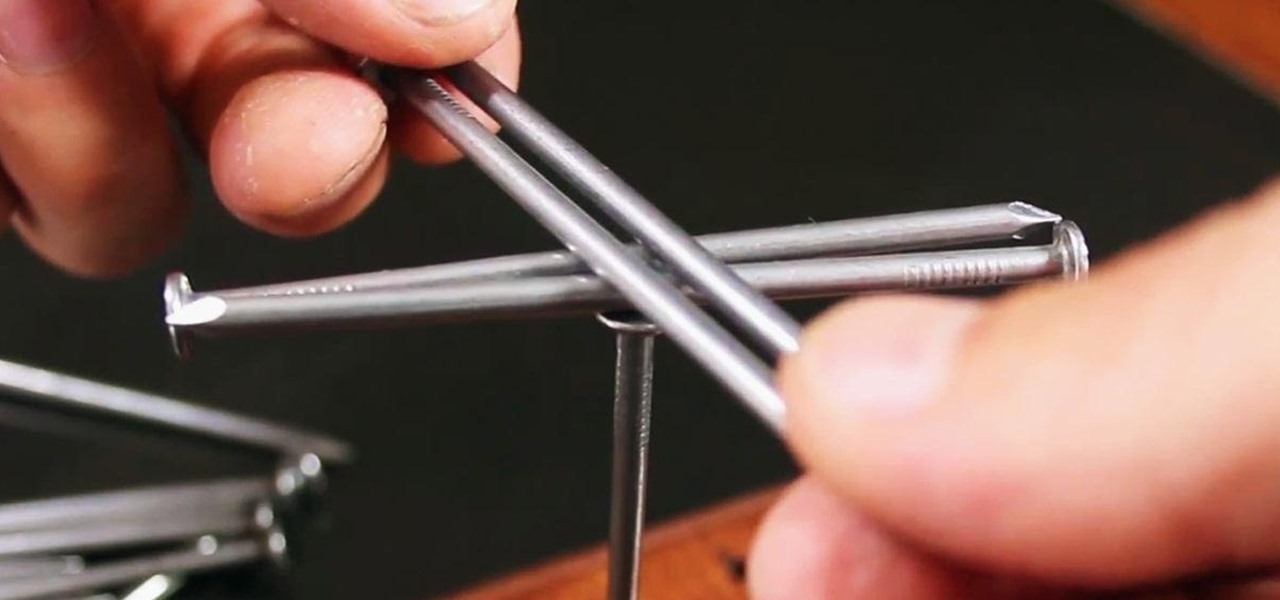
This little brain game is all about engineering a lower center of gravity. The idea has been around forever, but most people still don't know how to do it. Trying to stack nails above the balance point will raise the CG and make the structure unstable. Here's how you can lower the CG to make a very stable structure and impress your friends.

Let's say you forgot the code to your Master Lock combination padlock. What can you do besides buy another one? Well, there's a surprising abundance of ways to open a combination lock other than with just the combination, some of which will even let you reset the code. Of course, these hacks aren't limited to folks just looking to open their own locks, but let's just assume that's what you're here for.

If you've ever wondered what exactly goes into a McDonald's sandwich (or what the heck that secret sauce stuff is anyways), you might be a little surprised to learn that all of the ingredients are readily available at your local grocery store. In an interesting move, McDonald's has released a video featuring Executive Chef Dan Coudreaut showing, step by step, how to make your own Big Mac sandwich at home. Here is the video, and if you'd like to read along with Coudreaut's instructions, you ca...

Last week, we rolled out a major site-wide update on WonderHowTo, making it even easier to follow the subjects you're passionate about—and easier to share your creations with people who'll give you the kudos you deserve!
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

Are you a fan of the movie "Jerry Maguire"? Bruce Springsteen had a pretty awesome song called "Secret Garden" on it. In this video, you'll learn how you can replicate the song on your guitar. Play "Secret Garden" for your loved one.

You’re munching away on walnuts and, oh no, you notice you have a scratch on your wood floor. You already have the solution in your hand. The oil in nuts will fill in and make scratches on a wood floor disappear.

The secret nail gun is used to nail timber floor boards to floor joists or on top of a sub floor construction. It shoots nails on a 45 degree angle through the tongue of the floor which is covered by the next board. No nail holes are required to be filled by the floor polisher. Watch this video tutorial for a demonstration on how to use a secret nail gun.

While the stock market can be unpredictable, it's not a complete enigma. There are patterns to watch for that can make you a successful trader. Fortunately, there is an expert guide to becoming an analyst that's now available to everyone.

The incidence of tuberculosis (TB) is dropping in the US, but the World Health Organization (WHO) considers it to be epidemic in the rest of the world — there were over 10 million new cases in 2016.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

It's that time of the year, y'all—when the air becomes crisp, the nights grow long, and people crave hearty, warm soups and stews. And of all the season's offerings, my hands-down favorite has to be chili: It's versatile, meaty, and above all else, it's damn easy to make. (Thank you, Lord, for the slow cooker. Amen.)

Fast food is a guilty pleasure in which we all indulge. When you're short on time and long on hunger, being able to whiz through the drive-thru or run 'in and out' of a fast food joint can be a real lifesaver.

Valentine's Day is a day for love, but it also just happens to be the time when every flower shop in town hikes up their prices. Chocolates are still relatively cheap, but I never understood why you have to give the gift of bigger love handles when something more creative gets the job done at a much cheaper price.

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

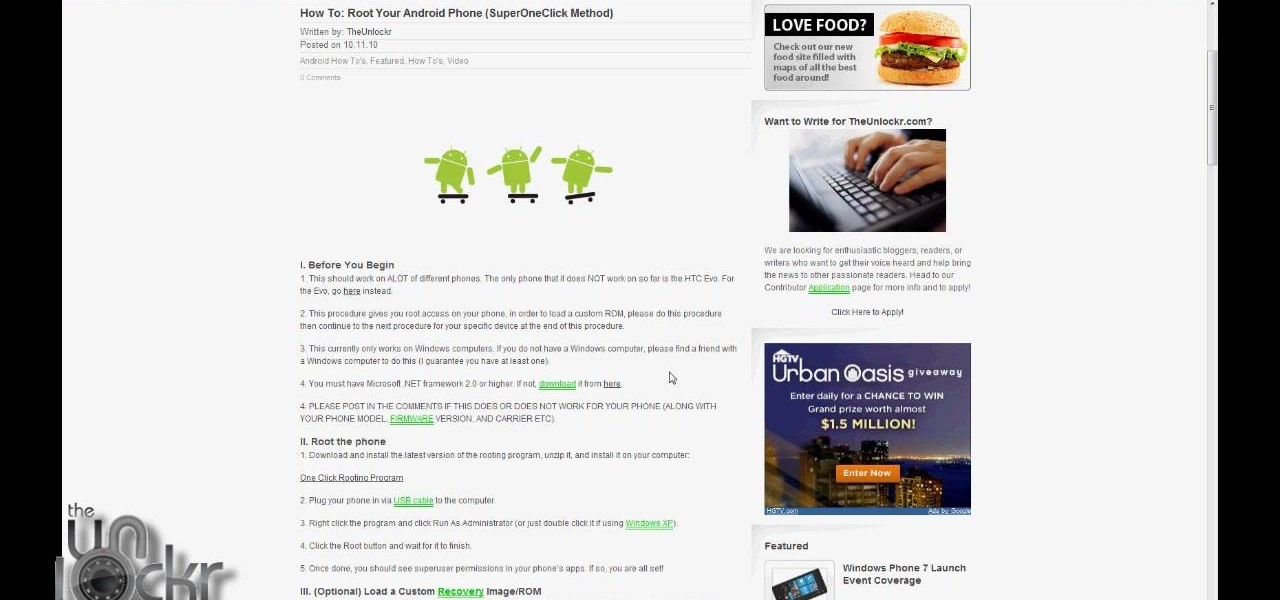
This is, by far, the easiest way to root your Android phone, and it's even got its own name— the "SuperOneClick" method. This is a universal technique that applies to most Android-based smartphones (minus the HTC Evo and T-Mobile G2/Vision). TheUnlockr shows you the secret behind rooting your Droid, so watch and learn. Anyone with an Android-enabled phone can do this.

Lady Gaga is definitely in shape. No one can deny that. But how does she do it? How does pop music's most popular artist stay in perfect shape? How does she get those great looking abs?!?

This ball isn't like any you've ever seen before. It's stubborn, it's unpredictable — it's practically immovable. Gravity cannot control this magic ball.

Magic is a wonderful thing. But so is science. So, which category does this mystifying candle trick fall in? Perhaps both.

The secret to making a good pot roast is to start with a good organic roast. With the meat at room temperature and sprinkle both sides with salt. Next chop a whole clove of garlic, put it in a bowl, and add some oil, black pepper, and cayenne pepper. Cut several slits or holes in the pot roast and poke the pieces of garlic into the holes on the top and bottom and sides. Put some of the vegetables in with the roast at the beginning of the cooking time: a leek, an onion, a carrot and a couple s...

Sloppy Joes are a great dinner when you don't have all night to cook. They're messy, so kids love them, and they pack in a whole bunch of 'secret' veggies, too! Use lean beef and make these healthy and delicious Joes along with Betty! Everyone will love them!

Use this rigged game to cheat your friends twice in a row! The game functions just like 31, only this time you'll always win if you follow the instructions in this video.

This week: a rigged game of skill & a simple sucker bet! Check out this video if you want to learn how to beat anyone in a simple game that can be played anywhere with coins and a napkin. Some might call it magic, others call it skill.

In this "super" video tutorial, you'll learn how to convert a Super Nintendo controller to PC controller. Now, dig deep into your garage and pull out those old SNES pads (or controllers) and get ready for some "super" modding!

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack cash in Restaurant City (07/02/09).

Magic Trick: The Cigarette Through Coin Have you ever heard of the Masked Magician? With the television series Magic's Biggest Secrets Finally Revealed, the so-called Masked Magician (Val Valentino) revealed secret after secret of the magicians repertoire. Valentino creates “the magic” then proceeds to reveal the reality of the illusions before a captivated television audience.

Can you solve the mystery of the sands? The Magic Sand Wand puzzle is a clear acrylic wand, partially filled with brightly colored sand, and containing a silver ball. All you have to do is get the ball from one end of the wand to the other.

This is a tutorial on how to make your hair look just like a Victoria's secret model.

This is a pretty cool little trick for your brain. If you stare at a negative image for a little, then switch it to black and white, it appears to be in color. Images can be downloaded here: http://s95.photobucket.com/albums/l13...

Have you ever admired those individuals that get so much accomplished in a day and wonder how the heck they do it? Now's your chance to learn their secrets. The Productivity & Motivation Master Class Bundle brings you everything you need to life-hack your way into leading a more productive lifestyle at home and work.