Okay, Mr. Thrifty, you reserved the least expensive hotel room that you could. But your inner Donald Trump doesn’t want to settle for low-frills. Go ahead, it never hurts to ask. Watch this video to learn how to get a hotel upgrade.

Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there that just give you the busy signal over and over again. In those cases, there's a jailbreak tweak that can help.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you've read or watched anything Harry Potter before, you know friendship and teamwork are huge parts of the story. The same goes for Harry Potter: Wizards Unite, with its "Wizarding Challenges." Here, you can tackle Fortresses full of Foes alone, but why do that when you can battle with up to four other friends at once? Here's how it all works on Android or iOS.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

We're nearly there — Apple released the seventh iOS 12 beta to developers Monday, August 13. While not totally unexpected, beta testers understand the struggle of predicting the next update, as Apple has switched haphazardly between two-week, one-week, and irregular release schedules for both the developer and public betas.

Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

If you own a Blackberry Pearl, you know that the trackball can be one of the best and one of the worst things about the phone. It's great for navigating your phone, but sometimes it can get very sticky. This tutorial will show you how to change or repair the Blackberry Pearl trackball. Only attempt this if you're willing to take apart your phone.

Did you know that you can pick a padlock using simply a paperclip and bobby pin? All it takes is a little wiggling, tension, and precision, and you should be on your way to opening up a padlock. It's recommended that you only perform this on your own lock as attempting to break into other people's locks is illegal.

Before attempting to build a house on your own, watch professional tradesmen and experts do it first. Watch this video tutorial which demonstrates how to join plaster battens.

Do want to learn how to do a hand stand? Watch this video which demonstrates how to do one. For beginners, before attempting to do one, make sure you have a handstand expert supervising you.

How to Disc Swap after moding a Playstation 2 Slim. Mod must be done before attempting to do this.
Although a business plan is a technical document, remember that this first draft will not be. The audience and author of this document will be the owner/manager of the small business. The purpose is to get as much information written as possible so this draft can be used as a starter for versions of the business plan that are crafted for other audiences. It eliminates the possibility of the first business plan you write for other audiences actually looks like your first attempt. Since the lat...

If you're interested in nabbing superhero memory strength, the secret behind training your brain is not necessarily what you might expect. Your standard G-rated brain strengthening exercises range from crossword puzzles to Sudoku to calculating fairly simple math problems to improve short term memory, but the real clincher used by some of the pros is essentially... porn. Yep, you read right.

Cartwheels are so much fun! Who doesn't love to twirl around? If you don't know how to do one of these fun moves, check out this video! Step by step, this tutorial will teach you how to relive your childhood or release your inner gymnast.

Splits are popular in dance and cheerleading, do you think you can do one? Practice, practice, practice and check out the helpful tips in this video to avoid injury.

Prepare for the ultimate Wizard101 walkthrough. These 14 videos show just about every aspect of Wizard101 gameplay. So get ready for an educational know-all guide.

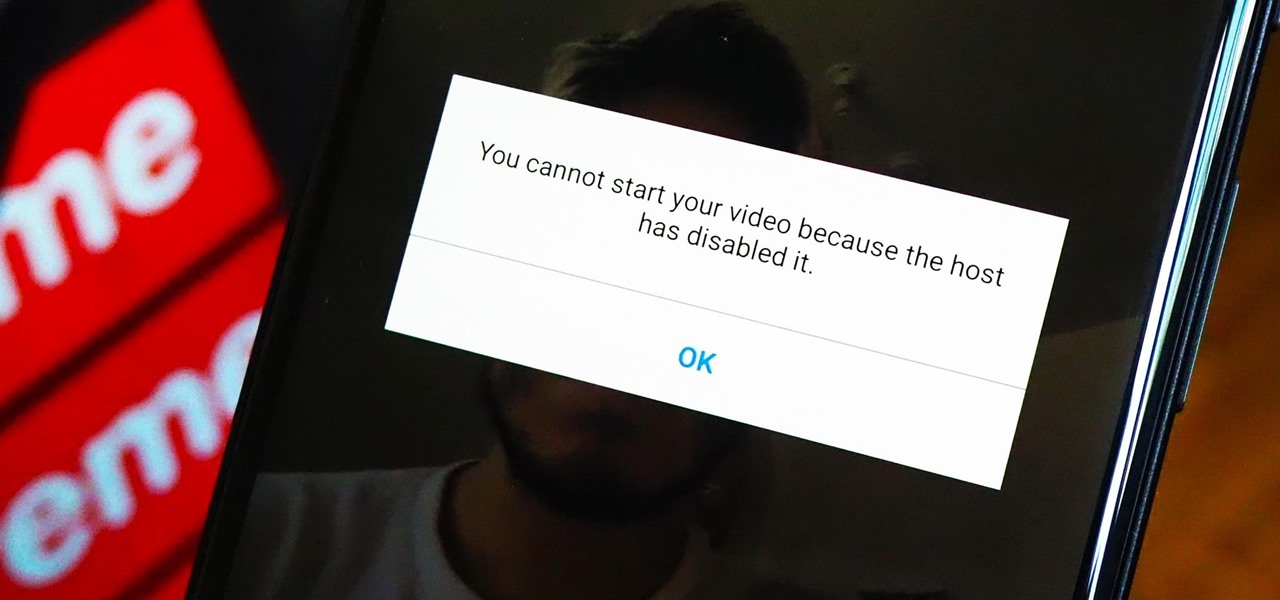
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

The entire wireless industry is working overtime to convince the world that 5G, and the higher prices associated with the faster speeds it affords, will not only be worth it but will deliver never-before-seen wonders. But few companies have produced such a stunningly well-done sales job as Three, one of the leading wireless giants in the UK.

Like other popular social media apps, TikTok features a tagging system — dubbed TikCode — to follow people in your immediate vicinity. Instead of searching for their username, you can scan their TikCode, and TikTok will launch their page immediately. Of course, you have a TikCode of your own, so you can share yours with others in the same way.

Lego has shipped several apps and products that add an augmented reality dimension to their playsets. But it has taken a reality TV show from Fox to allow brick fans to build with virtual bricks in augmented reality.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

The HoloLens 2 hasn't even reached most of the market, but it's already a big-time TV star. Microsoft's augmented reality device made its primetime debut on FOX TV last night on an episode of the hospital drama The Resident.

At Next Reality we mostly focus on augmented reality, but that doesn't mean we're not also absolutely obsessed with virtual reality, too. If the thing that's been keeping you from diving into the deep end of VR has been clunky tethered headsets or the expensive but necessary gaming PCs, then it's time for you to try the Oculus Quest, which is currently available to buy here for less than most gaming systems on the market.

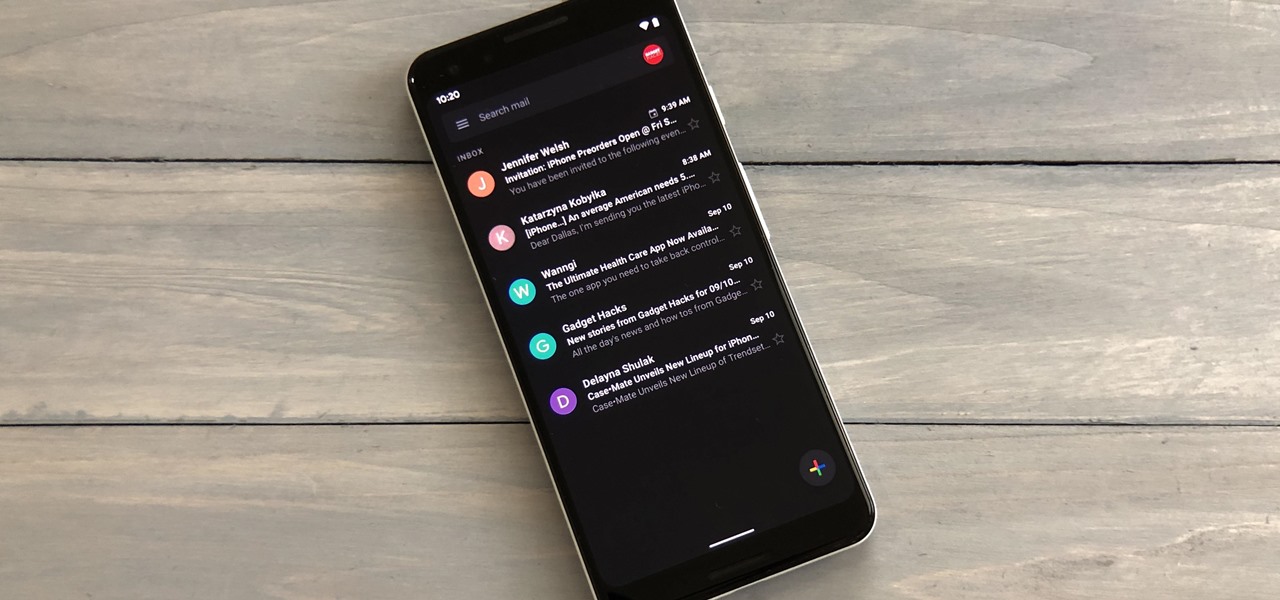
Google's strategy for updating its apps with dark mode options is apparently "one at a time" and "as slow as possible." Even after the company added a dark theme to many of its apps for Android and iOS, such as Calendar, Chrome, Keep, and Photos, Gmail seemed to remain "light" for the longest time. However, the app now supports dark mode on both mobile OSs. Here's how to enable it.

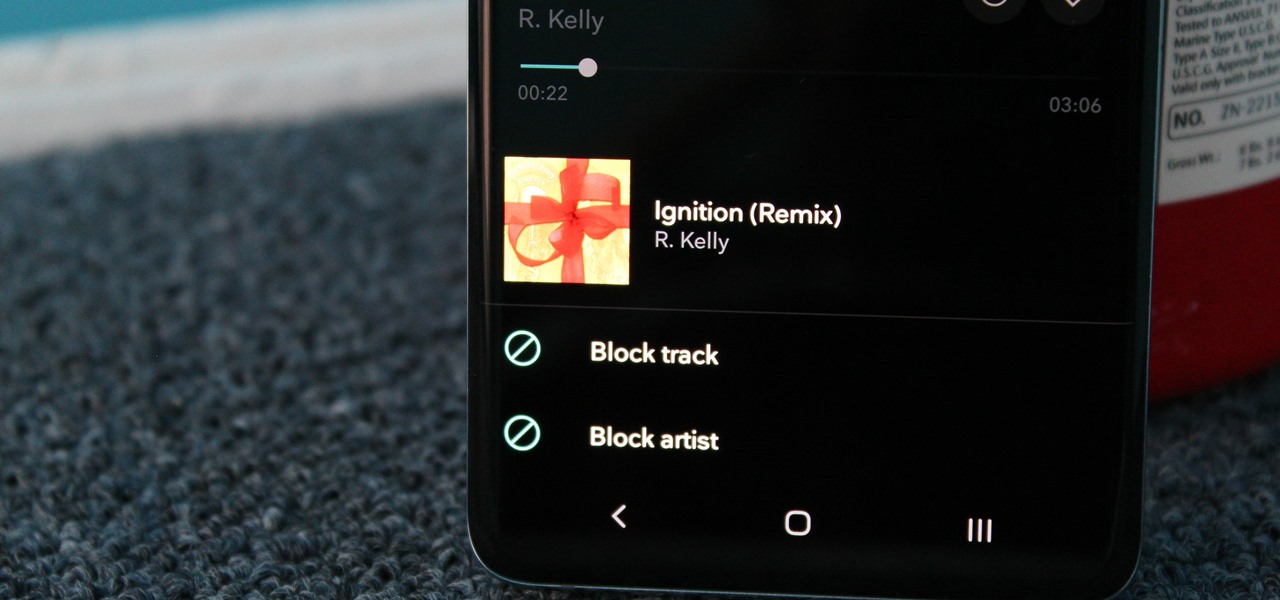
From XXXTentacion to R. Kelly, many artists have been accused of inappropriate actions, so some of us just don't want to hear their music anymore. However, each time streaming services attempt to ban such artists, they face heavy backlash. Recognizing this, Tidal decided to offer a different solution.