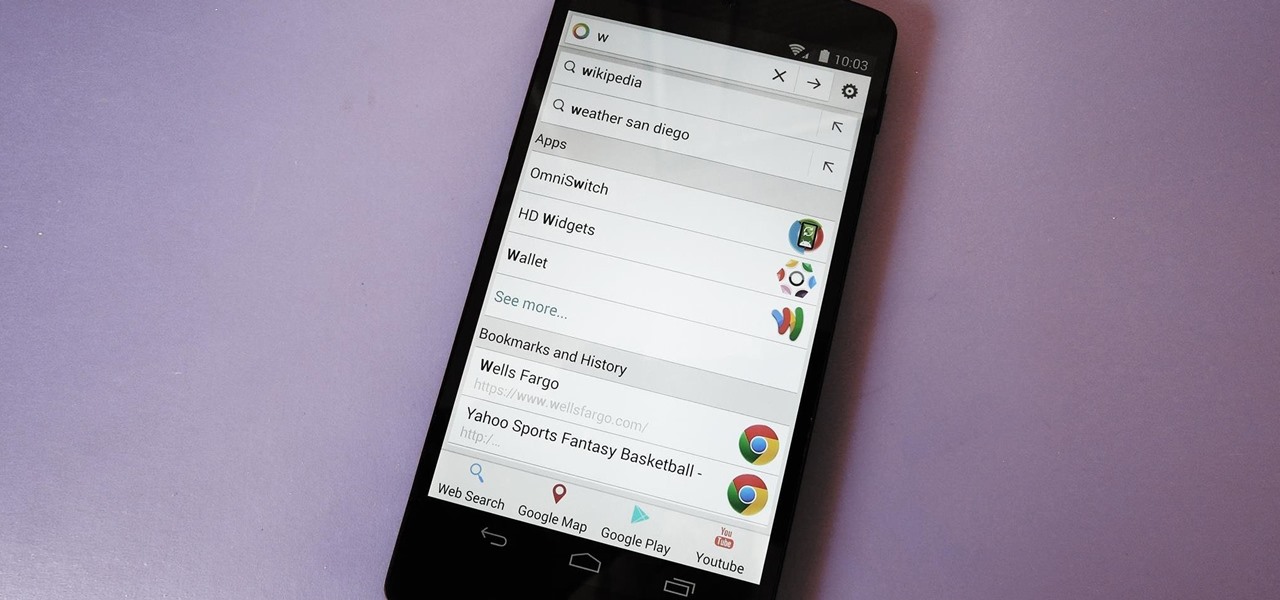
Prior to the release of Android 4.0, most devices had a dedicated search button. This functionality allowed you to search Google from your home screen and app-specific content from within any app. Eventually, though, this dedicated search button was ditched in favor of an icon in the action bar of apps, and a search bar on the home screen.

While you may look ridiculous doing the potty dance and crossing your legs back and forth, holding it in can be worth the discomfort when you've got an important decision to make.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

Most days, getting through an eight-hour work shift is a struggle. There are a million places you'd rather be, and none of them include your desk. It's difficult to find the motivation to tackle the growing number of emails in your inbox when your mind is back at home, comfortable in front of your gaming system.

Someone does't really like you. I don't know who or where they are, but they exist. If you want to change that, simply ask them to do you a favor.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

You can read at 500 words per minutes. Don't believe me? Here, see for yourself. This amazing technology comes from the startup Spritz, and they're ready to unleash it onto the smart device world, starting with the Samsung Galaxy S5 and the Galaxy Gear line of smartwatches.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

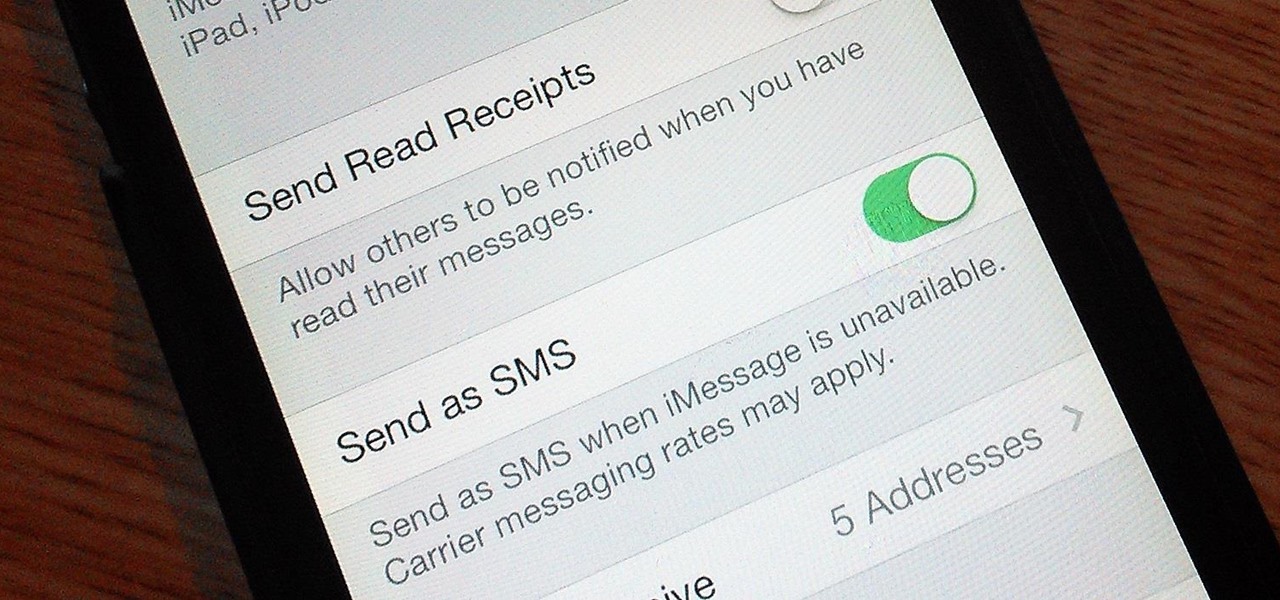
If you're an iPhone user, iMessage is great for cutting down on SMS costs from your carrier, but it doesn't always work right away.

Give me a paintbrush and easel and you'll be sorely disappointed, but give me a Samsung Galaxy S3 and a new app called Let's 8-Bit Art and you might call me the next Picasso.

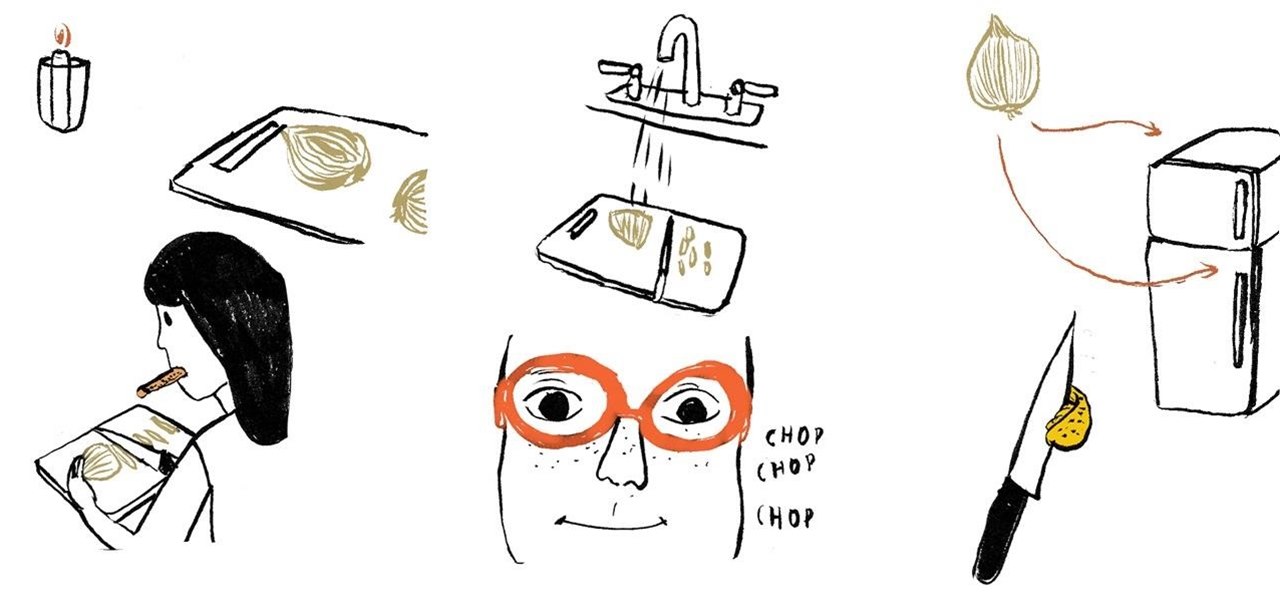
Is it possible to cut or chop onions in the kitchen without stinging eyes and looking as if you just watched the saddest movie ever? Before we get to that answer, it's important to know why we tear up when cutting raw onions in the first place. What is this irritant? Are you reacting to the odor? The answer to the latter question is "no," and the irritant responsible is amino acid sulfoxides.

Cinema is a matter of what's in the frame and what's out, according to director Martin Scorsese, who asserted that when describing his life's work. Getting the perfect shot can turn an otherwise ordinary scene into something great, both on and off screen.

Shark jumps Steampunk, experts unsure of the meaning. Cape Town -- In an unprecedented move today, a Shark have jumped a steampunk couple as they were attempting to work on their hobby steamboat.

Now that there's a working jailbreak for every iOS 6.1 device, there are more and more people jailbreaking their iPhones (including me) for better customization. But for those of you who have no desire to jailbreak, you can still do some pretty cool tweaks.

Many people that I know who have gone to see the Hobbit have come back unimpressed or annoyed with the film. I LOVED it. When those non-specific people, cough Loziers cough, gave me their reasons for not liking the movie, I was very annoyed... I considered the demands that they were placing on Peter Jackson and his team to be very high and unreasonable. So, as a method of venting my anger, here is how to watch the Hobbit. If you’ve read Lord of the Rings and the Hobbit, please, go back, and R...

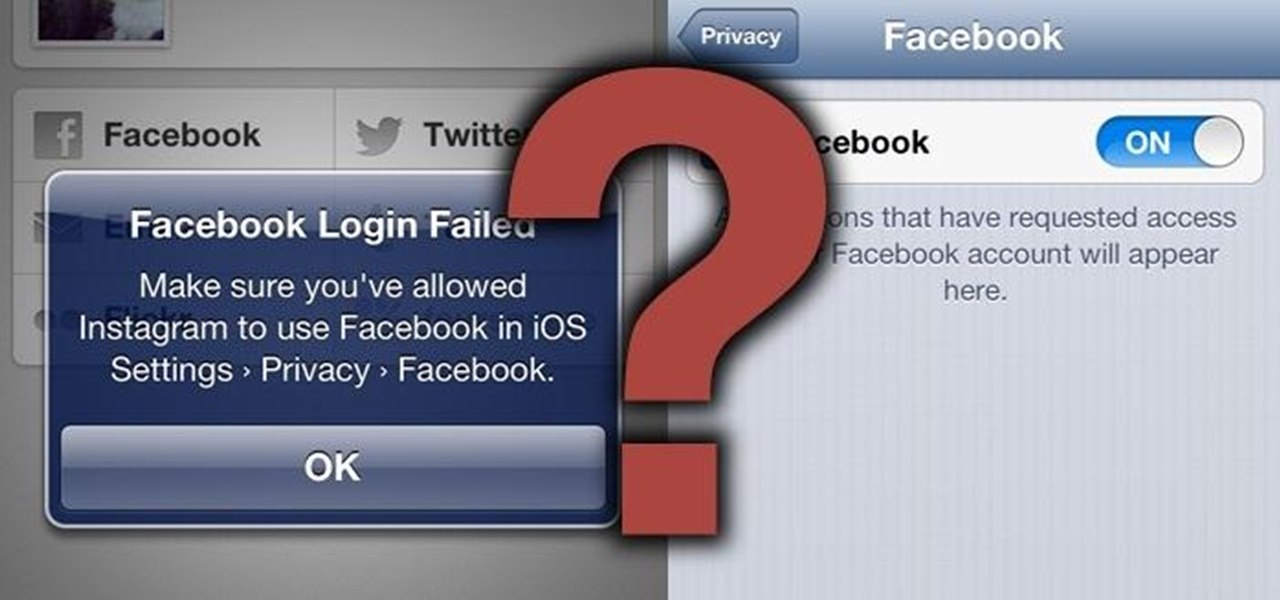
I recently ran into a problem connecting my Instagram app on my iPhone 5 to Facebook, and neither Instagram's or Facebook's help pages were as helpful as they claim to be.

Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Halloween costumes.

You've had your Xbox 360 for a few years now and your game collection is pretty extensive. Maybe it's not that extensive, but it's still substantial. Now imagine that you live in Europe and you're moving to the United States. I don't know why—maybe your dad got a job offer. Don't ask me, ask your parents. They're the ones that are making you move. Anyways, as most Xbox users know, games are coded by region. Games that work in Europe might not work in the United States. Does this mean you shou...

It can be extremely frustrating when you've forgotten the pattern you use to lock your smartphone, and even more so if someone has managed to prank you by changing it. Luckily, there's an easy fix if you know the username and password for the Gmail account you used to set up the lock.

Redbox recently announced a partnership with Verizon to bring a new streaming video service called Redbox Instant to an already crowded table. No prices have been released yet for the service, but with Netflix, Hulu, Amazon, YouTube, iTunes, and many others all attempting to get a hold of your dollars, what are currently your best options? Subscriptions Services

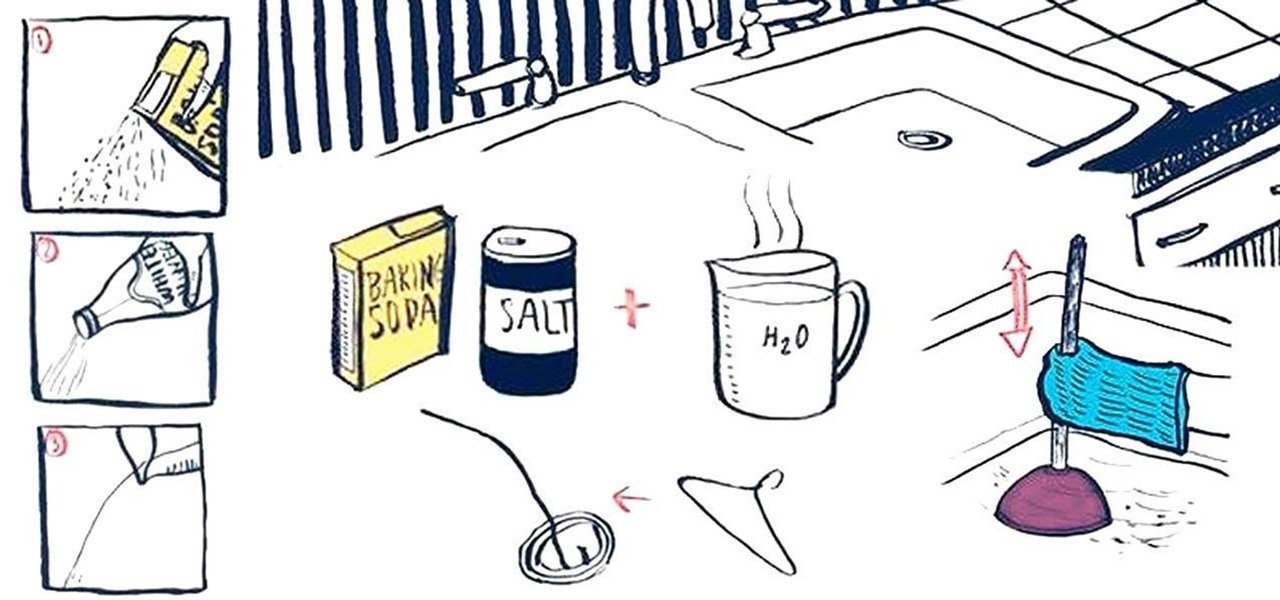
Oh, boy. A stopped-up drain. It'll inevitably happen with any home plumbing system and your kitchen sink is no exception. That clog won't go away on its own and will require immediate attention to keep any standing water from rising. But you don't have to resort to calling an expensive plumber or using a bottle of hazardous chemicals. Using simple kitchen staples or common household objects, as well as some determination, you can unclog your kitchen sink on your own without paying a dime.

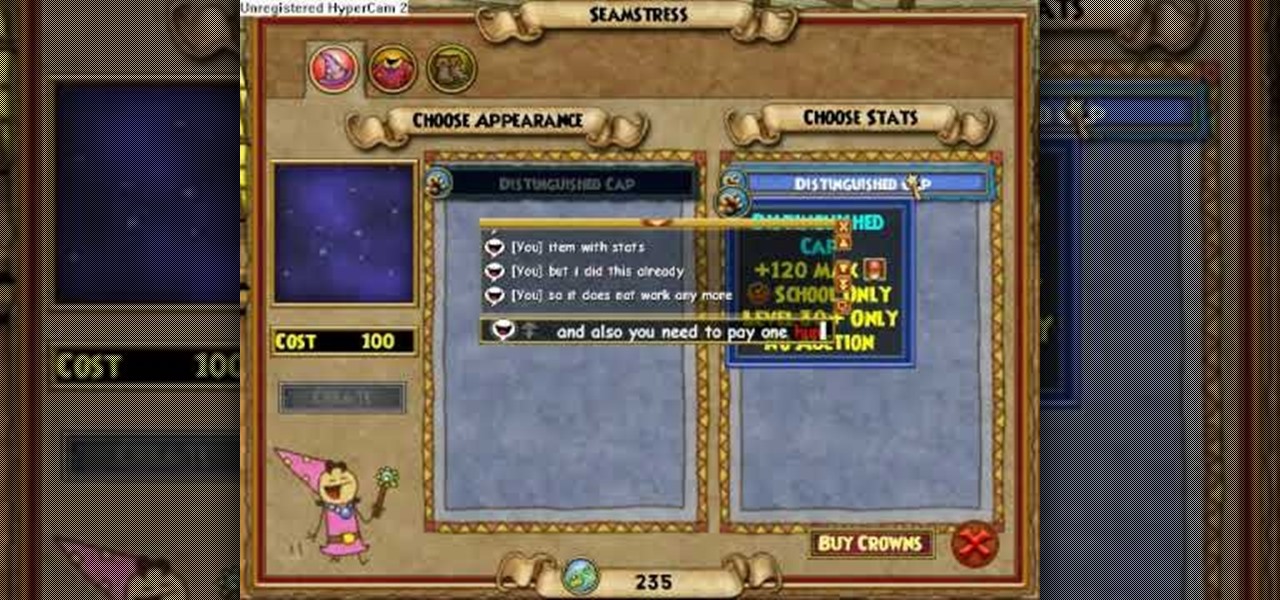
Hemming and stitching in Wizard101? Yep, learn how to stitch itms together and make an awesome wizard-like costume.

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to get into Nightside without beating streets in Wizard101. You don't have to beat all of the streets to get to Nightside in Wizard City.

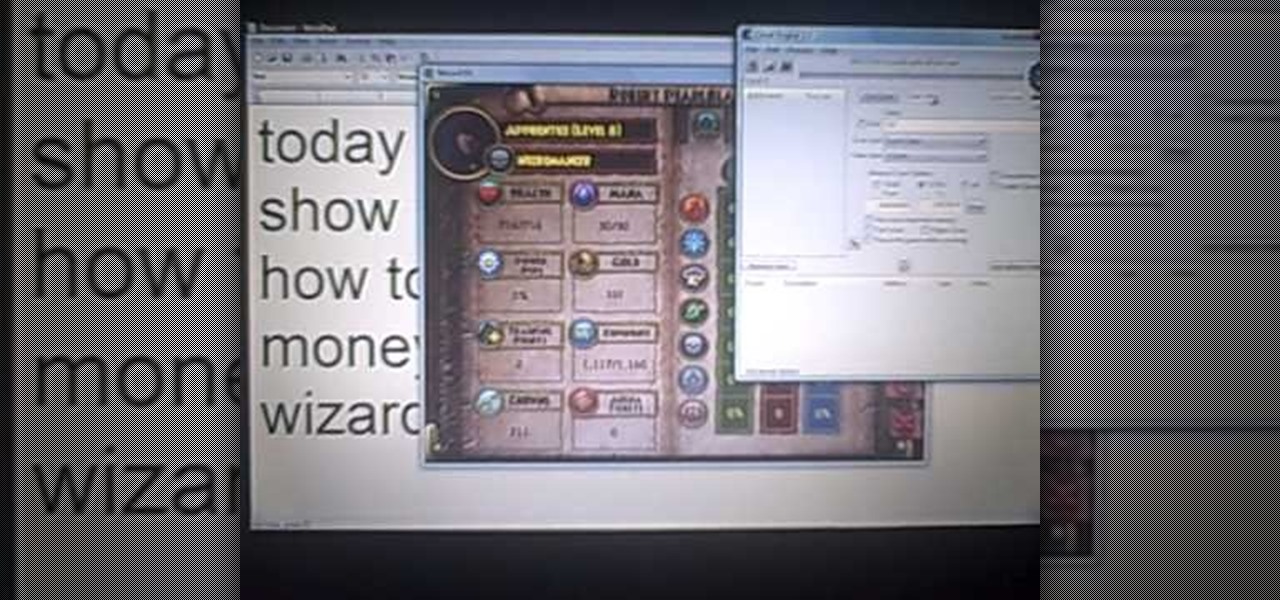
Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to hack Wizard101 money with Cheat Engine (09/27/09).

This four part how to video teaches you more advanced steps of the Charleston. You must have the ability to do the basic steps of the Charleston before attempting the dance steps in this tutorial. Watch this dance lesson and you will be able to do the Charleston in no time.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

These easiest way to create contact pages for your WordPress blog is with a plugin. Not fuss needed. These two videos attempt to tell you how you can create contact forms in your WordPress blog with the Contact Form 7 plugin. The "contact us" page made easy!

Love the beauty and fresh fruit of trees but have limited space? Try your hand at dwarfing a tree. You can enjoy all the benefits of a tree without any worry of the tree outgrowing the area or roots damaging side walks and property. Plus, they just look adorable.

Show your antique porcelain and pottery a little TLC. Spruce up your favorite antiques with these safe cleaning techniques. Remove the dirt and let the beauty of porcelain and history shine through. Just because your pottery is old, doesn’t mean in needs to look like it came out of a tomb.

This is one of a series of videos offered on iPod Nano repair. This video describes how to replace the battery on an iPod Nano. The instructor cautions that this process is for advanced iPod users only. The techniques he demonstrates are good for four generations of the iPod.

Get more money and experience in Fish World with this simple Facebook Fish World cheat using Cheat Engine 5.5. Easy to perform.

Are you a secret shopper? Well, you could be in Wizard 101. You have to earn the Secret Shopper badge to be one, and if you don't know how, you're in luck.