Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...

This two-part series (second part here) will teach you literally everything you need to know in order to make pretty much anything out of leather.
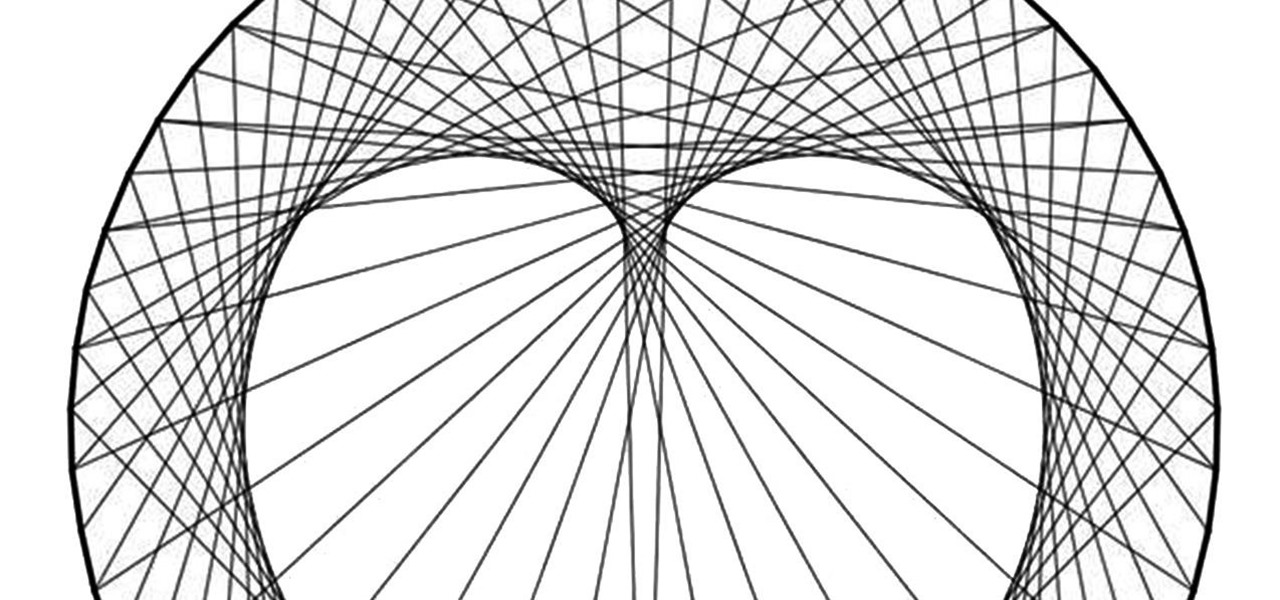
Using only a circle and straight lines, it's possible to create various aesthetic curves that combine both art and mathematics. The geometry behind the concentric circle, ellipse, and cardioid dates back centuries and is easily found in the world around us. From an archery target to an apple, can you name these geometric shapes?

I admit, when the new iOS 5 update for Apple devices was coming out, I had iTunes open all morning with my iPhone 4 attached... waiting... waiting... waiting until finally the new version of iOS was available for download. I stopped everything I was doing and quickly initiated the process of updating my device. After two excruciating hours, my iPhone 4 was finally ready to go and I couldn't be anymore happy. Who needs an iPhone 4S when you've already got iOS 5?

As the best-selling toy of all time, the odds of you once playing with a Rubik's Cube are pretty high. And if you're like me, or even the cube's inventor Erno Rubik, your first attempts likely ended in futility. Every twist, every turn, the cube just gets more and more mixed up. Is there really a solution?

Some iOS and iPadOS apps offer alternative app icons you can switch between. Beyond that, you'd have to create aliases in the Shortcuts app to customize the look of the app icons on your Home Screen. But that would mean two icons for each app in the App Library. Now, in a new software update, Apple has given us a middle ground for Home Screen icon customization.

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

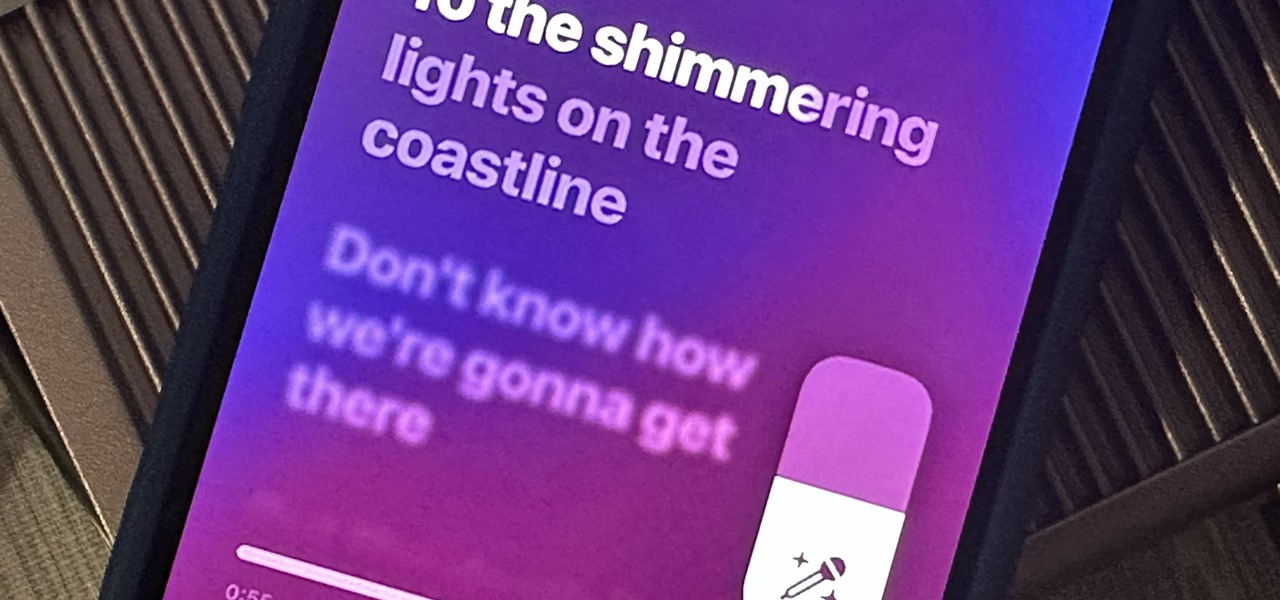
Apple just delivered an early Christmas present to Apple Music subscribers and karaoke fans in the form of Apple Music Sing, a singalong mode that lets you take over as lead vocalist for your favorite tracks.

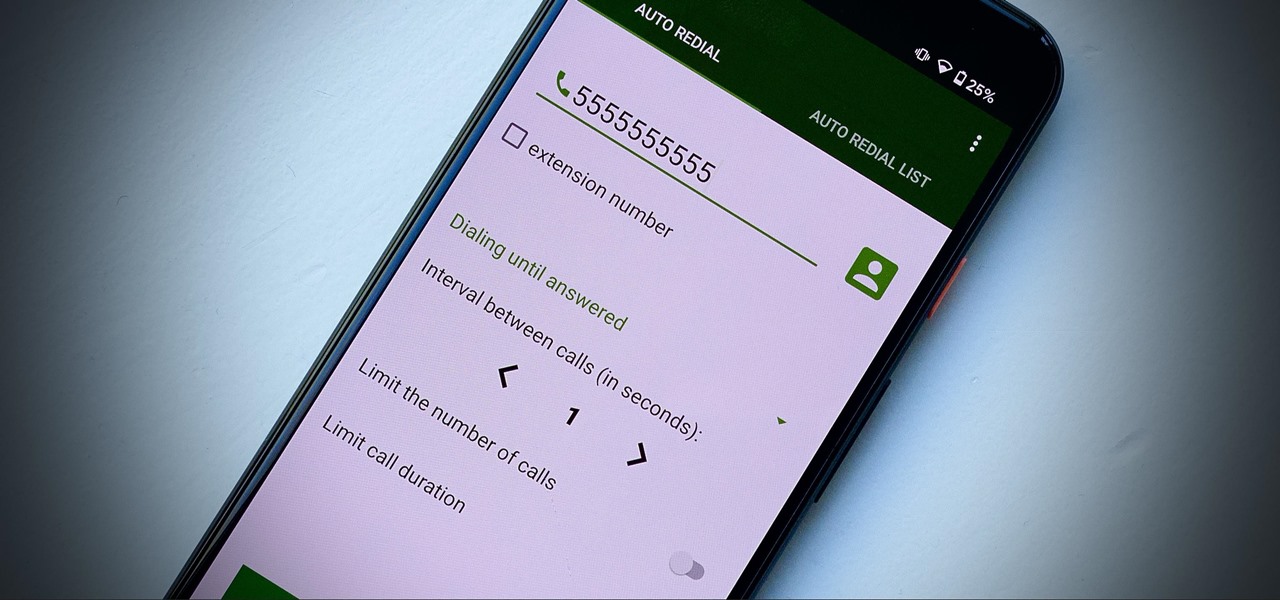
Some phone lines make it nearly impossible to get past the busy tone, whether it's a viral call-in giveaway, your state's unemployment office, your local post office during the holidays, or the repair office for a broken warrantied product you have. Thankfully, there are apps you can use to help break through the noise.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

In our review of Amazon's non-augmented reality Echo Frames smartglasses, we made the case for audio virtual assistants being the linchpin for AR wearables.

For its latest augmented reality trick, Snapchat has brought the world an AR Lens that has become a bit of a viral hit on Twitter as users turn themselves and their favorite movie stars into characters out of a Pixar movie.

Metadata might be a bigger concern than you might realize. In its continuous push to be a privacy-first company, Apple has released several new features with iOS 15 that allow you to adjust and permanently change the metadata stored within the photos and videos you take on your iPhone. But why would you want to do this?

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

Screen mirroring software has been around for ages, allowing you to mirror your iPhone to a projector, laptop, TV, or another device. It's useful to have during lectures, presentations, and meetings, so it's no wonder why Apple created its AirPlay technology. However, AirPlay doesn't work in all situations.

Among the various components of the emerging augmented reality space, the most lucrative is the advertising market. The prospect of turning every object, every location, ever signpost in the real world into a discount code or virtual transaction interface is why AR will ultimately be more profitable than VR.

While Touch ID has been a part of the iPhone's legacy since 2013, Apple waited until 2016 to add biometrics to its MacBook lineup, and it's not as impressive. An iPhone with Touch ID can register up to five fingerprints, but Macs can only register a maximum of three per account. If that seems unfair, there's an easy trick to doubling that number, meaning six of your fingerprints could unlock your laptop!

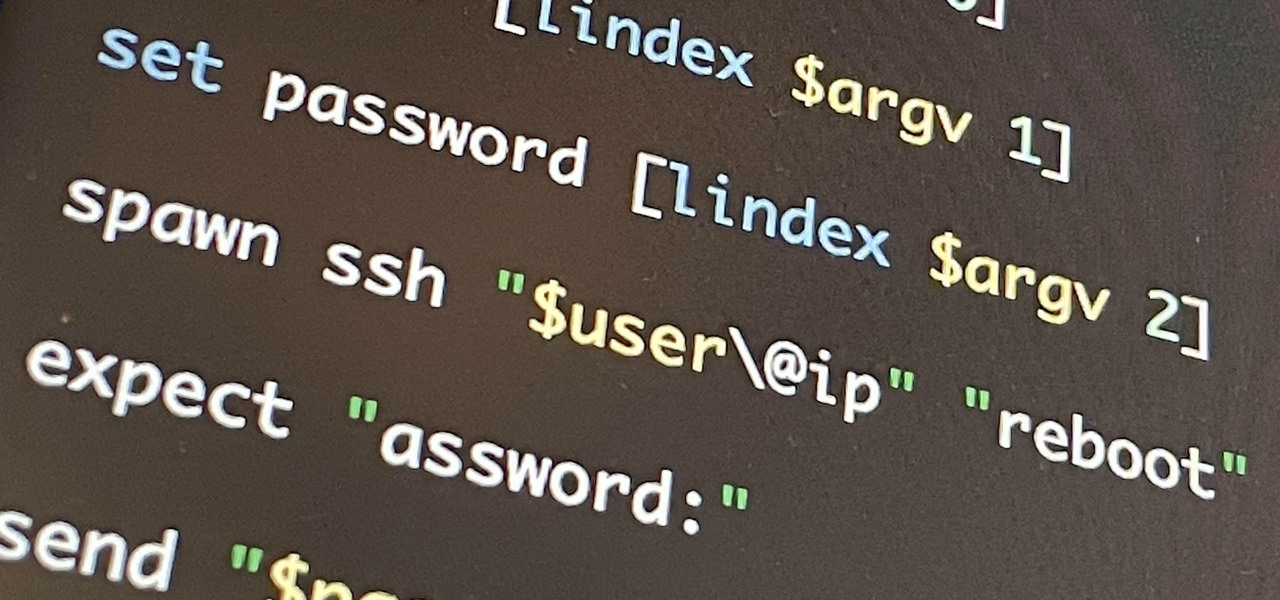
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate delivering an SSH payload with an "expect" script.

What does it mean when a software company obsessively focused on innovating the way we use our mobile devices to see and communicate with the world adds virtual voice agents? Possibly e-commerce magic, with a powerful layer of augmented reality.

For some, one of the coolest new features in iOS 14 is the Picture in Picture mode, which had previously only been available on the iPad. With it, you can continue watching a video from an app in an interactive floating overlay window on the home screen or within other apps. But for others, it can be annoying when it appears unexpectedly all of the time, and there's a way to stop it.

Apple released the first beta for iOS 14.2 to iPhone developers on Thursday, Sept. 17. A significant new feature that iOS 14.2 brings to the table is a new Control Center tile for Shazam music recognition. A simple tap of the tile will launch the operating system's built-in Shazam capabilities, scanning for music playing in the immediate area.

Group chats, particularly ones with many active participants, could bombard your iPhone with hundreds of texts in a single day. It can get overwhelming real quick unless you take precautions to hide all notifications for that conversation. But there's another option now, one that'll make sure you only get alerts for the messages that matter to you most in the thread.

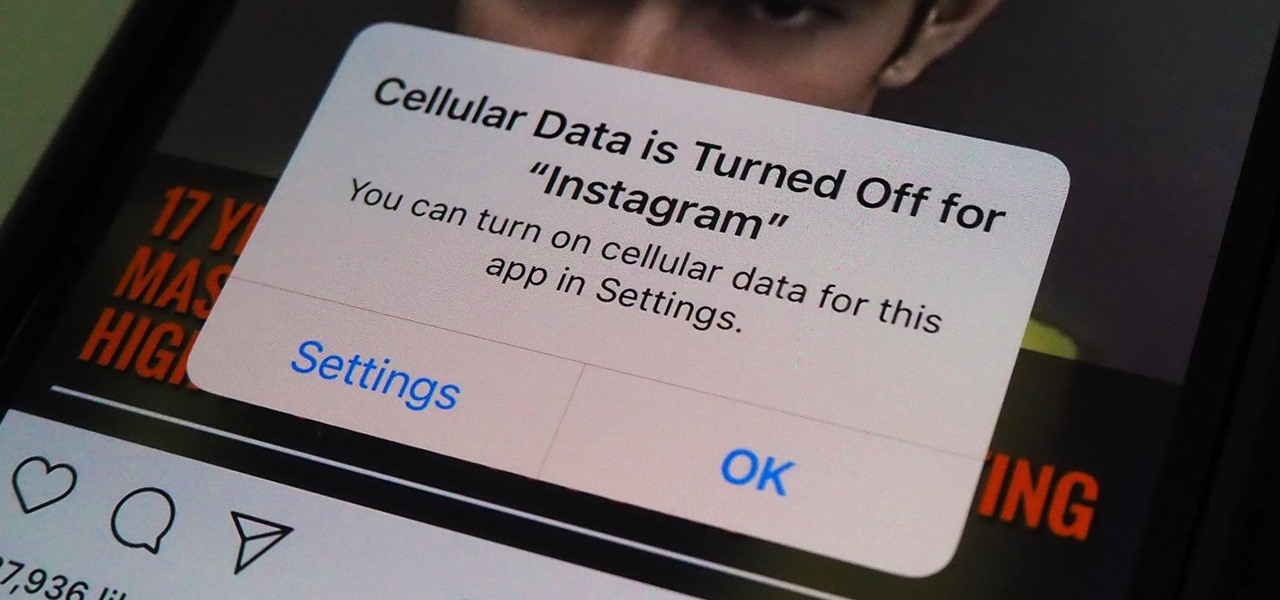
If you're on a cellular plan with a low data allotment, being thrifty with your data can help you avoid a higher bill. But even if you have an affordable unlimited plan from wireless carriers such as T-Mobile or Verizon, going over a certain amount of data may throttle your connection, leaving you with slow web speeds. One way to prevent hitting these thresholds is to keep certain apps in check.

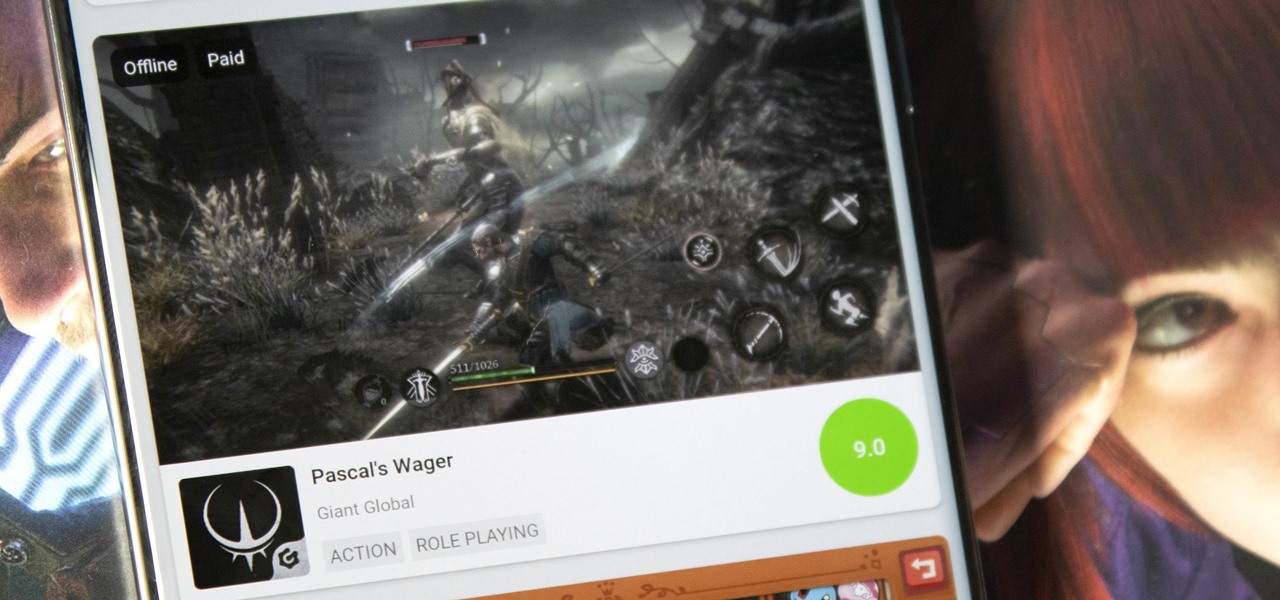
Discovering great mobile games is difficult. With over 300 thousand games on the Play Store — not including the hundreds more available by sideloading — finding the right one to invest your time and money in can be hard. The Play Store's rating system is helpful, but ratings are often skewed by external factors.

I've been steadily making my way through the series Hannibal, which arrived on Netflix in June. I've just now made it to the back half of the third season, which introduces us to a new villain who (spoiler alert) seeks to become the Great Red Dragon.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

Since we wouldn't have Android without Google, everyone has come to realize that the Pixel smartphones are a prime example of what an Android smartphone should be. With so many unique software related features, no wonder people want that Pixel experience.

Typography is an important aspect of the video editing process. You deal with it when adding captions to news clips, giving on-screen recipes in food videos, creating burned-in subtitles for short films, making no-sound-needed videos for social media, and so much more. Enlight Videoleap for iOS makes this all easy.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.