Huawei is making a fresh attempt at launching into the US market to challenge Apple and Samsung's monopoly on premium smartphones. In its latest attempt to break into America, Huawei is trying to get its Chinese mobile chipset accredited by AT&T.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.
The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

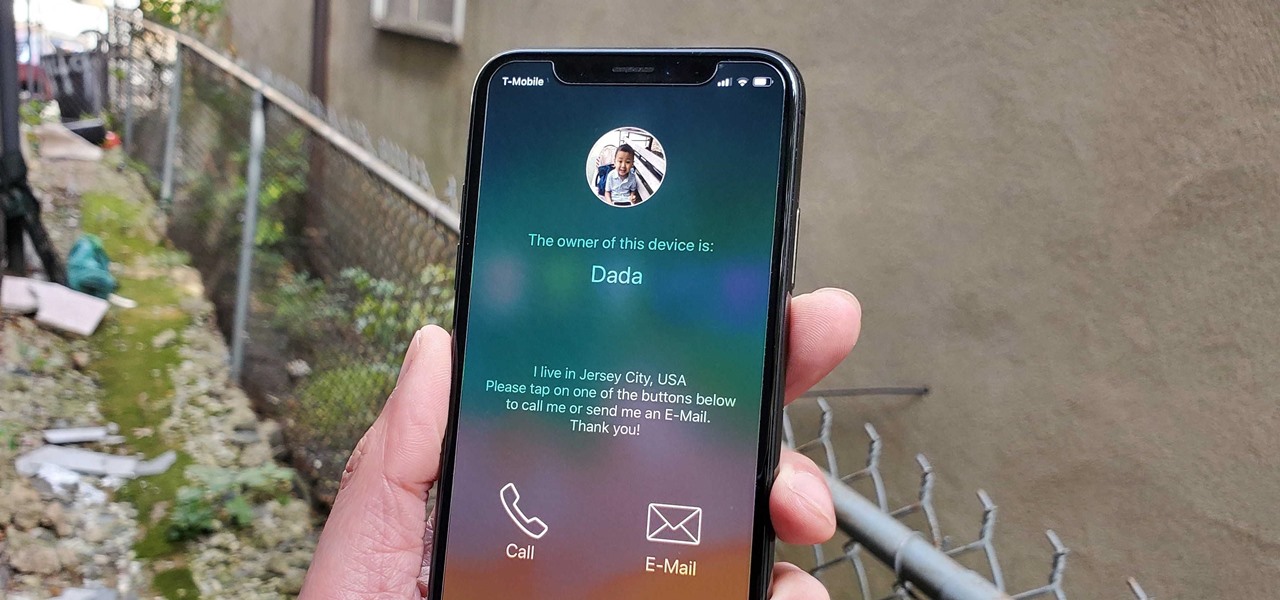
The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.

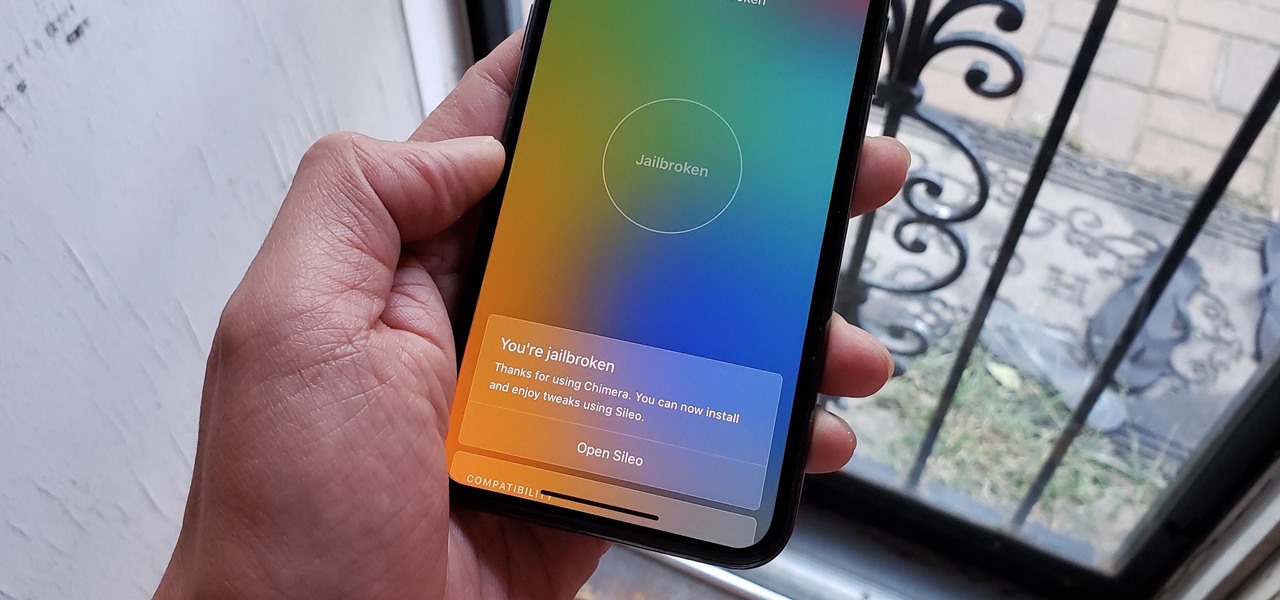
Compared to fully untethered jailbreaks, semi-untethered methods like Chimera for iOS 12 have one major handicap: you need to re-enable the jailbreak every time your iPhone turns off or restarts. As intimidating as it seems, however, kickstarting the mod and restoring your tweaks is still pretty easy.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Google updates the Play Store periodically, but the changes are usually subtle. A recent server-side update, however, is shaking things up quite a bit.

Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.

On Wednesday, Snap, Inc. unveiled a revamp of its Snapchat app that draws a hard line between content from your friends and content from professional media organizations.

Face ID is possibly the iPhone X's make-it-or-break-it feature. Apple is asking previous iPhone owners to put a lot of faith into their home button replacement, and so far, the results seem pretty good. That is until CNN tested the security feature with identical twins.

Nope, it's not 2016 again. Samsung is giving it another go at beating its competitor by attempting to unveil their new Galaxy Note 8 before the new iPhone. Because it worked out so well the last time.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

Out of all of the "odd couple" food pairings you could imagine, this has got to be one of the outright weirdest.

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

A little less than a year after announcing "Project Astoria," Microsoft announced Thursday, February 25th, that it will end the "Bridge," which would have brought Android apps to the Windows Store.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

We all know that opening our work emails at home is a bad habit. Yet reading and responding to emails every time your iPhone dings is worse than you might realize. Not only are you extending the workday, but you are also sacrificing your ability to perform on a daily basis.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.

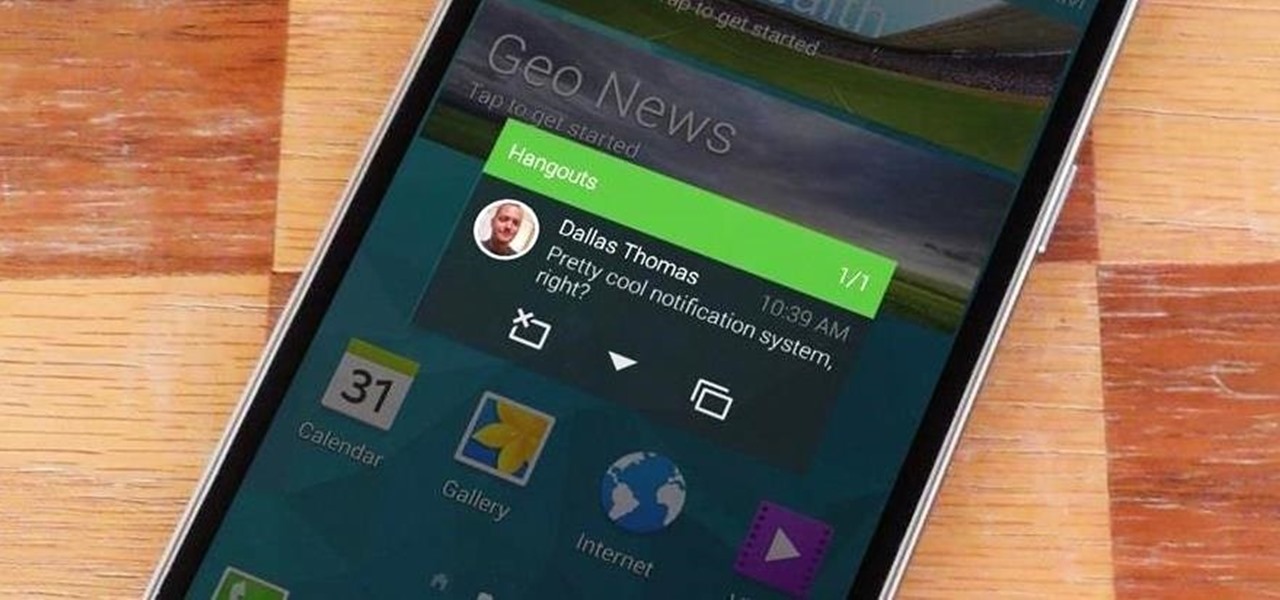
Notifications are an integral part of our day-to-day smartphone usage. They allow us to easily see and act upon all of the latest information that comes our way. Well, most of the time, that is.

The volume is maxed out, but that doesn't stop me from hitting the volume key on my Nexus 7 in hopes that it will magically get louder. This happens to me everyday as I watch videos or play music. The simple fact is that a Nexus 7 tablet just doesn't get very loud. At least, not loud enough for me.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Here's a technique I used to whip up a batch of super cheap and easy to make smoke flares! WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

As a doctor, sometimes it will be necessary to perform a neurological examination of your patient to rule out any neurological disorders. Your objective is to identify abnormalities in the nervous system, to differentiate peripheral from central nervous system lesions, and to establish internal consistency. This is a great video less that outlines the complete neurological exam procedure. It's great for medical students or doctors, and even nursing students can learn a thing or two.

First of all you have to check the three red lights as shown because it indicates that the Xbox is broken and needs repair immediately. However if you open the Xbox the warranty is invalid and it takes six weeks to get it repaired. So go to eBay and buy the repair kit with printed manual for ten dollars. Remove the top and the bottom covers. It shall make a loud slap and it should be expected. Now use a key to unscrew the top cover and then remove it. Now remove the white color fan part. Now ...

If you're a serious diver, especially anywhere cold, then your dry suit is probably a near and dear friend. If something goes wrong with it, you may think that you need to pay someone a lot of money to fix you baby. But no! They're actually pretty easy to fix yourself. This video will show you how to fix the neck seal on an OS Systems drysuit yourself with just some spare parts that you can order from the manufacturer.

Performing a proper dump and flash on an XBox 360 disc drive should not be attempted by those without advanced technical knowledge, including how to solder and work with computer hardware. If you want to though, you could not hope for a much better set of instructions than this. This three-part video series will show you, in painstaking detail, how to dump and flash the LiteOn 93450c and 93950c disc drives used in some XBox 360's. Be very careful when following these instructions and you will...

In this tutorial, learn how to make one of Betty's favorite desserts of all time: Butterscotch Meringue Pie. This recipe is quite simple and absolutely delicious and if you choose not to make the pie crust, it can also serve as a great pudding! Follow along with Betty and serve up this special dessert for your family.

Software manufacterers always advise you to read the instruction manual first before attempting to do anything on a new program. But who has the time to obsess over ever little boring detail in a 300-page tome when just playing around the controls on your own gets you attuned to the program immediately?

Solo camping is a scary and exciting prospect. Alone in the woods at night, no one can hear you scream. But for those who crave solitude and love the wilderness, there can be no greater thrill, no greater connection to the primitive part of yourself. In this nine-part video, we learn all kinds of useful survival and camping skills by watching our host Colhane experience a three-day solo camping trip in the Brazlilian bush. You will learn how to cook, how to make fire, how to prepare a campsit...

Ruth demonstrates how to wind a bobbin successfully every time you attempt. Place the spool of thread on the machine and wind the thread between the two disks on the spindle (found in all machines). It is better to wind the thread twice to avoid the thread come off the spindle. This does not damage the machine in any way. Pull the thread towards the bobbin and pull it through the hole in thy bobbin inside-out. Place the threaded bobbin into the winder making sure the extra thread is on top an...

If done wrong, a backflip could be devastating. But if done right, a backflip just might make you the coolest person ever. This is a unique backflip tutorial that uses both video examples and instructional text. See how to do a backflip. Follow these steps, one by one, to see what you're doing wrong.