I love making beeps and bloops with the Arduino pitches library, but sometimes archaic 8-bit tunes just don't cut it. Whether you want your robot to terrify your enemies with a demonic synthetic voice, you just need a pocket boom box on the go, or you want to a miniature guitar amp, a simple LM386 amplifier can crank up those signals loud enough to play through any speaker.

Whether you're in an airport, restaurant or waiting room, the insidious grip of televisions on human life is omnipresent. Sometimes it's nice to talk to other human beings while looking at them directly—actually hearing what they have to say.

Valentine's Day is almost here, and if you're like me, you're scurrying to do something special for your mate. The standard chocolates and flowers just isn't cutting it anymore, and you can only make so many homemade cards before it becomes banal and meaningless. So, what can you do that shows you put some work into it, while not breaking the bank?

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

Use this safe and easy technique next time you need to replace a shattered light bulb. You Will Need

In these music lessons on video, learn how to play a funk groove on the piano. Get some tips for playing effective bass lines and using rhythm techniques like stab breaks, hangs, stops, and glissandos.

In this expert video series, let Malik Haddadi show you some fun office tricks and pranks. Using a combination of deception and skill, Malik illustrates some tricks that will truly confuse your fellow co-workers. For instance, stump your friends with some logic games and puzzles. Also, learn how to magically tie ties or break a pencil with an index card. With this series, you can make your co-workers laugh and groan at the simple tricks they fell for. So, what are you waiting for? Begin the f...

Ultimately a doctor’s note is the only necessary proof needed to show your boss that you really did go to the doctor’s but if you feel like making an airtight case you can always take a few extra steps to make sure there’s not a shadow of a doubt.

In this video series, watch as screenwriter and producer Chris Cobb teaches you how to turn a script into a production board. learn how to break the pages down, how to transfer the scripts onto the breakdown page, how to color code the script, and how to put together the production board.

In this video series, our expert will teach you how to sew a zipper. If you've ever thrown away a piece of clothing because of a broken zipper, this is the video for you to watch. Get step-by-step instructions for sewing three different kinds of zippers, including an invisible zipper, side zipper and center zipper.

This is a great series for anyone who is or is thinking of becoming an offensive player and will need to know how to run a reverse play. Our expert will go through every aspect of this trick play from possible stances to how to hold the ball as you run to breaking tackles. There are also more advanced moves covered that pros use such as the spin move and the stiff arm. If you can master these there is no stopping you!

In this video series, our expert Nathan Bugh will tell you about the history of Balboa swing dance, and explain the dance itself. Nathan will teach you how to lead and follow the basic Balboa swing step, how to hold your partner, and how to do a break. He will also show you how to do a Charleston step, a kick, and how to bounce.

Learn the basics of doubles tennis from our expert in these instructional videos. Watch as Tyler Thayer teaches how to score doubles, the different strategies to watch for while playing doubles tennis, how to serve, how to rush the net, how many sets are in a doubles tennis match, how to break a tie, and when and where is the best time to watch tennis.

This video series is great for the beginner and expert breakdancer. Our expert, Jonathan “Xcel” Escotto, has been "breaking" for years and will show you basic moves and how to mix them with more challenging ones.

In this video series, watch as school theater expert Peggy Charlton teaches theatrical staging basics. Learn how to build sets, the location of he different areas of the stage, what a cyclorama is, how to use the curtains on a stage, how to design a set, how to identify the apron area, and how to break down a set.

In this series of Latin dance video lessons you’ll learn the basic footwork a beginner needs to dance the Mambo. Expert dance instructors Kelly-Anne and Steeve Vean Louis will teach you all the basic steps of Mambo, including tips and techniques for finding the rhythm and a variety of breaks, crossovers, and turns that will have you dancing like a real pro in no time.

With this video series you will be able to learn about the bass guitar and everything you need to know to start playing. Begin by learning the parts of the guitar. Our expert will break down the parts of the bass guitar so you understand what each part does.

Are you tired of the same old thing for dinner every night? Food in a bucket doing a number on your waistline, eh? Well, take a little break from your routine and invest a few minutes in learning how to make some traditional Asian cuisine. Our expert Chef, Ian McSwain, will guide you step-by-step through two easy Japanese recipes

In this video series, our expert will show you how to replace, repair and maintain your motorcycle brakes. You will get step-by-step instructions on disassembling your wheel, and brake components, cleaning the brake caliper and master cylinder, repairing broken parts, and finally, reassembling your motorcycle when you are finished. Our experts instruction will give you the knowledge to fix and maintain your own motorcycle brakes, as well as enhance the general understanding of your motorcycle...

The team over at Spatial isn't done innovating its way through augmented reality in 2020. Just days after adding a mobile option to its groundbreaking Spatial virtual collaboration product, the company is releasing Tele, a new app geared toward more casual, AR-powered video chats.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

Typography is an important aspect of the video editing process. You deal with it when adding captions to news clips, giving on-screen recipes in food videos, creating burned-in subtitles for short films, making no-sound-needed videos for social media, and so much more. Enlight Videoleap for iOS makes this all easy.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

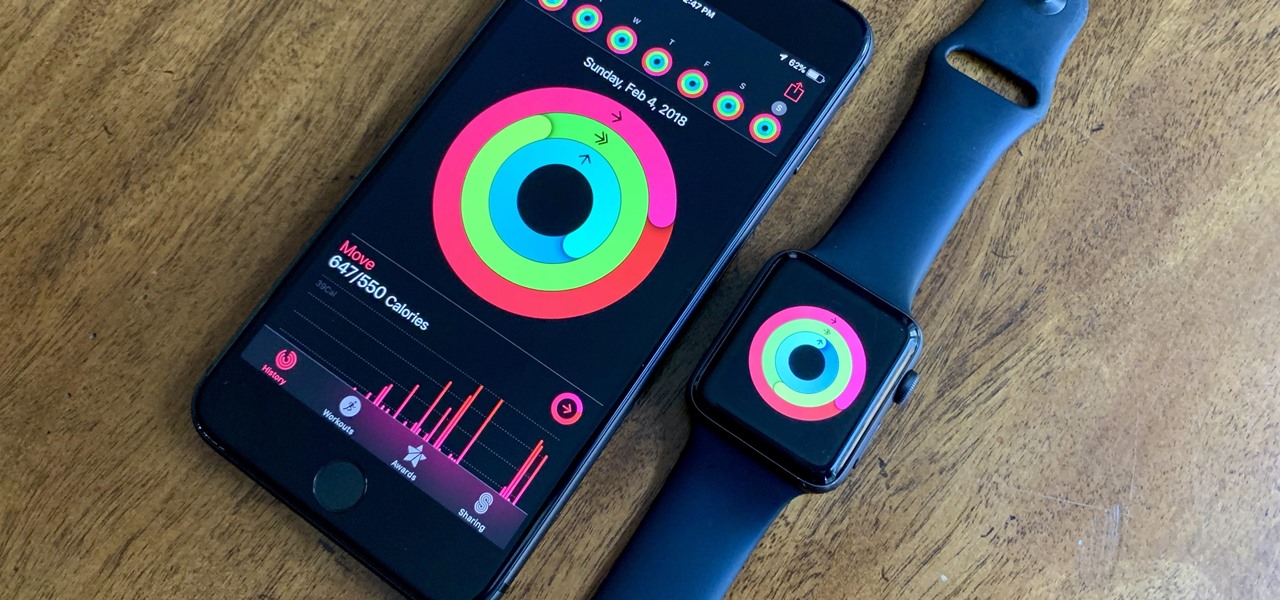
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

MoviePass was once the best subscription service on the market for getting cheap movie tickets. For the price and the number of films you could see and save money on, it was unbeatable, but recent changes to the service have made it less enticing. While it still works well for some users, others may have to rely on other options. Personally, I'm leaning toward the latter.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)