In this Tuesday's Brief Reality report, there's a trio of stories from the healthcare world where augmented reality is helping out with surgical microscopes, asthma treatment, and other diagnostic and treatment tools. There's also something for all of you AR/VR storytellers out there.

Uber wants you to forget about cars and start thinking about fully autonomous flying as an alternative—a more "economically favorable" way of getting to your grinding nine-to-five.
Vodafone India has merged with telecom company Idea Cellular to become India's largest mobile player this week.

Having control of your basic motor functions is something most people take for granted, but for individuals with Parkinson's disease, that is not the case.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

A little-known company in India is making waves after announcing that it will sell an Android 5.1 Lollipop smartphone for less than $4 (or, more precisely, 251 rupees). The Freedom 251, from Ringing Bells, sounds almost too good to be true. Is that because it is?

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Marmite: either you love the stuff or hate it. ("Love" meaning you are British and grew up eating it, and "hate" meaning you are everyone else.)

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

This year's NFL playoffs have been nothing short of spectacular. With Super Bowl XLVIII coming up on Sunday, February 2nd, people are already gearing up for another classic showdown between the NFC and AFC, and this time it's the Seattle Seahawks versus the Denver Broncos.

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.

Rooting a mobile device may not be a big deal these days, but not being able to root definitely is. Even the Library of Congress, National Telecommunications and Information Administration, and White House can agree on that.

Nikola Tesla is one of the most tragic figures in the history of science, a history that is practically filled to the brim with tragic figures. Francis Bacon, a 16th century philosopher and scientist, caught pneumonia and died because he was trying to stuff snow into a dead chicken. Marie Curie died as a result of her long-term exposure to radioactivity, and her papers from the 1890s are too radioactive to touch without protective gear to this day.

Is "Last Resort" Steampunk? Well, no. I mean, how could it be?

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

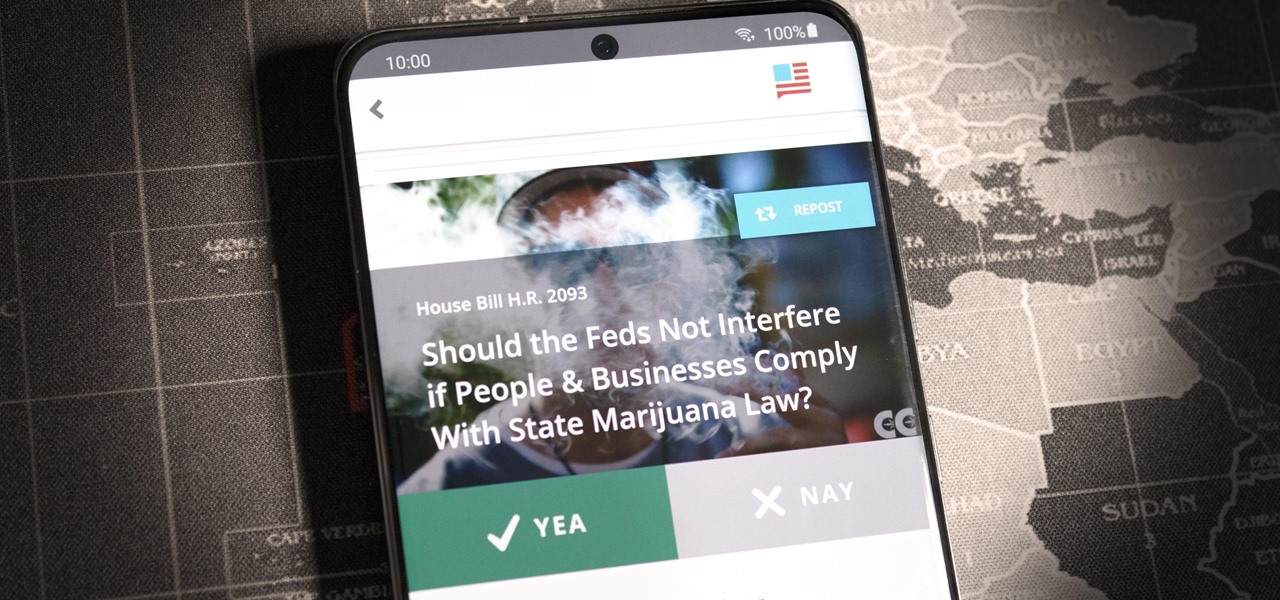
If you live in the US, it's your civic duty to understand our governing bodies and the political system that puts them in place. It doesn't matter what your age is, knowing who to vote for is as important as voting at all. That starts with policing your own representatives to help decide whether or not we should re-elect them.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

Amid the coronavirus chaos, two companies at the forefront of augmented reality technology took starkly different approaches to their upcoming developers conferences, as Facebook has canceled its annual F8 conference and Magic Leap plans to invite a limited number of attendees to its Florida headquarters for LEAP Developer Days.

In recent years, the US military has been utilizing augmented reality as a training tool, giving officers and soldiers an opportunity to train and hone their decision-making, tactical efforts, and weapons accuracy via virtual scenarios.

While Magic Leap has remained mostly silent regarding its plans for its Magic Leap One successor, the software team continues to makes strides with improvements to the device's Lumin OS and SDK.

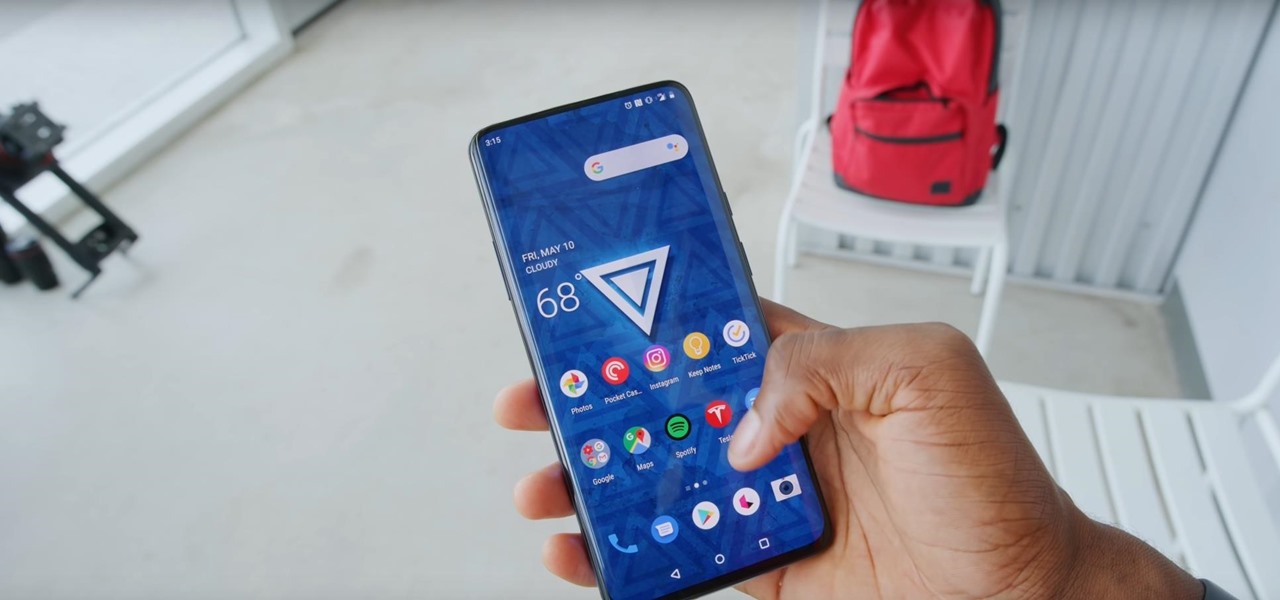
We've all been there — using Google Maps for navigation and waiting for the app to find our location. As we drive around, we keep hoping it will get a lock in time to make the next turn. Well in the US, we finally have a solution to this problem, and it's the OnePlus 7 Pro.

The recent announcement of a $480 million US Army contract awarded to Microsoft over Magic Leap for supplying 100,000 augmented reality headsets shows just a how lucrative the enterprise (and government) sector can be for AR.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Despite Huawei's ongoing battle with the US government, the Chinese company has continued to release phones in the US under its Honor brand. The Honor X series has been consistently released for several years, offering midrange specs at ridiculously low pricing, and the Honor 8X is no exception.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

UPDATE: The P20 and its variants are officially available now. However, there's no official North American variant. You can purchase the international version of the P20 Pro or P20 Lite on Amazon, but be aware that it may not work perfectly on US carriers.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.