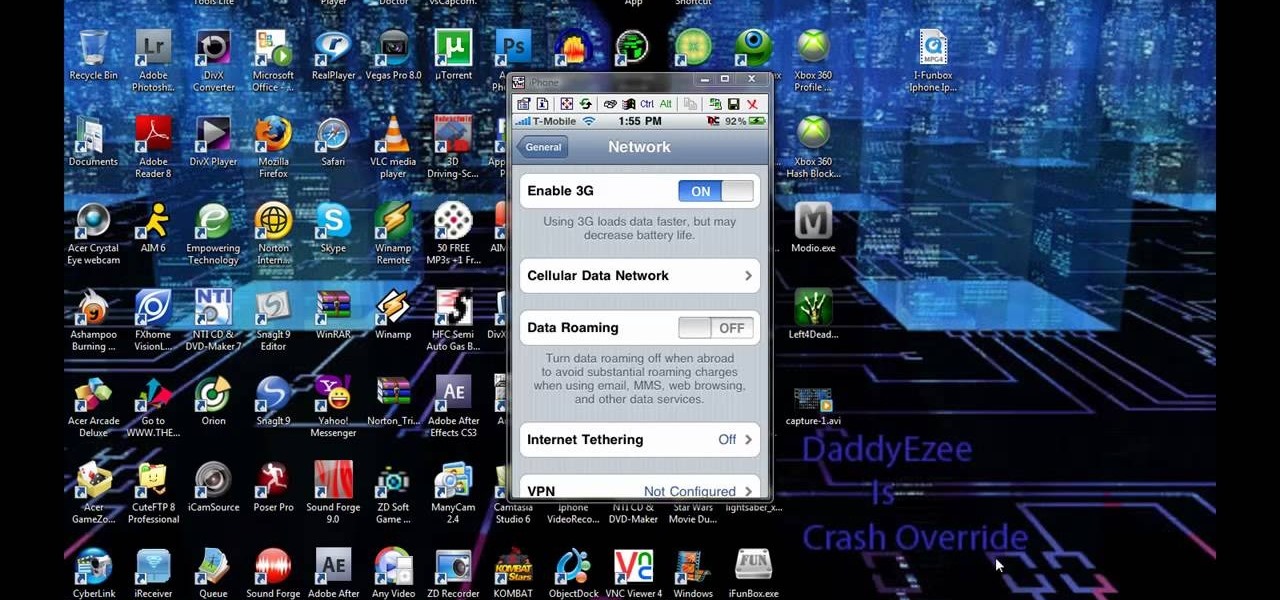
How To: Enable MMS iPhone 3G with T-Mobile
Check out this video to learn how to get MMS on iPhone 3G for T-Mobile on 3.0 firmware. This works on T-Mobile's Network only!


Check out this video to learn how to get MMS on iPhone 3G for T-Mobile on 3.0 firmware. This works on T-Mobile's Network only!

This video tutorial shows how to get MMS on iPhone 3G for Tmobile on 3.0 or 3.0.1. Not that this works on T-Mobile's Network ONLY

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.
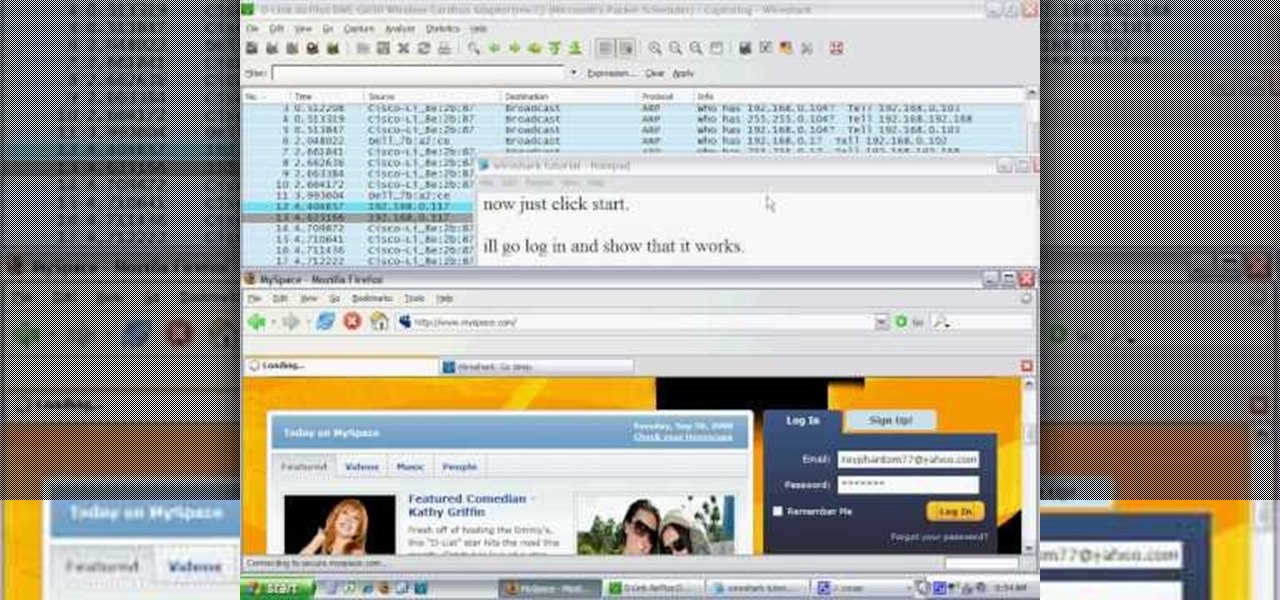
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only doing it to test a network's security, or for your own educational purposes. Check out the video, follow the steps and see how secure network is. Hack, hack, hack!
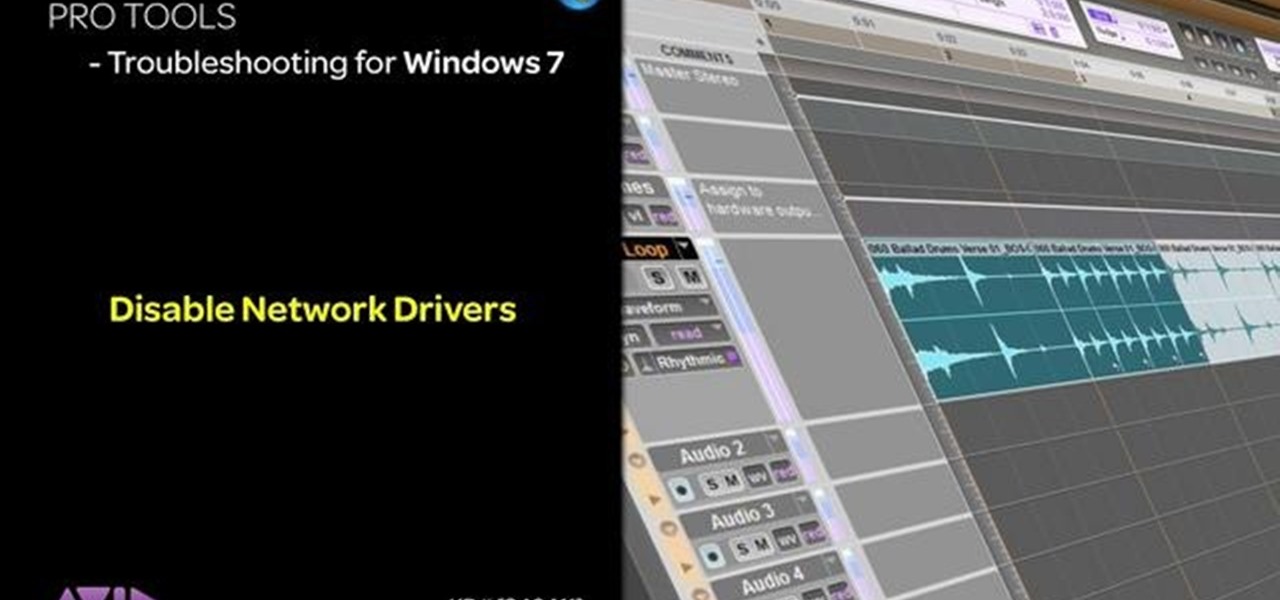
This tutorial is aimed at users of Pro Tools, but anyone interested in improving their computers' performance can use it, too. It's possible that an incompatible network adapter might give you an error message in Pro Tools, and this tutorial shows you how to disable it.
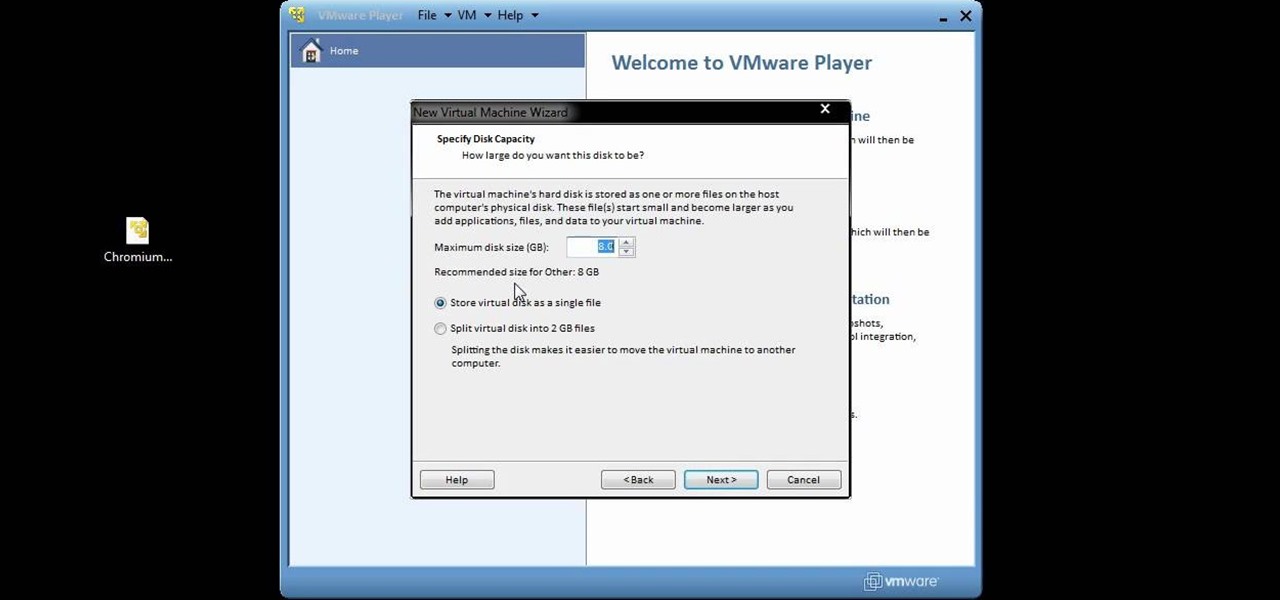
You can setup Chromium OS in a virtual machine. So first go to the download site for Chromium OS and VMWare download for the VMWare Player. Now run the VMWare Player and click on "create a new virtual machine" and select "i will install the operating system later" and click next and then next.

Learn how to create a branching network within C4D with this video tutorial. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, including complete instructions, watch this 3D modeler's guide.

In this clip, learn how to make zucchini and potato pancakes with a side of salmon infused cream cheese. Giada de Laurentiis, the host of the Food Network's "Everyday Italian", shows you how to make these delicious hot cakes. Enjoy!

In this video, learn how to make a delicious baby spinach salad topped with fried broccoli and cauliflower. This Italian favorite is presented to you by the Food Network's Giada De Laurentiis and is as easy to make as it is delicious. Enjoy this outstanding salad today!

In this clip, the Food Network's Ellie Krieger shows you how to make a deliciously healthy mango salsa. You can eat this salsa alone or slap it on a chip. Either way, you will melt when you taste how yummy this super simple dish can be. Enjoy!

In this tutorial, make a super easy no-fuss guacamole dip that anyone can do! This dip is made in true Mexican style and is so simple that it's basically fool-proof. If you enjoy Mexican snacks and need something to spread on your chips or tacos, then make this wonderful dip with help from the Food Network's Robin Miller.

In this clip, learn how to use PDA Net to tether your rooted Droid 3G smartphone to a WiFi network. By tethering your device, you will be able to use it as a portable, wireless modem for anything from other phones to computers to hand held gaming systems. Anything that is WiFi enabled can be tethered to your mobile network with this hack.
Use the Microsoft Office 2010 Social Connector tool to reach out to friends in your favorite social networks. Whether you're new to Microsoft's popular email and scheduling application or a seasoned MS Office professional just looking to better acquaint yourself with the Outlook 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started using the Outlook 2010 tool for yourself, watch this free video guide.

This video tutorial teaches how to find homegroup password in Windows 7. For this you should be using the computer which is part of the homegroup. The way to check this is by going to the control panel and clicking on network and internet link. In the ensuing window the network and sharing center link is clicked. This will show if the computer is connected to the home group. On confirming that the computer is connected to the homegroup, now navigate back to the network and internet link, and ...

Mark from Minneapolis Best Buy Mobile Team walks you through the excellent Vlingo BlackBerry application, which allows you to better manage your favorite searching and networking sites from your mobile phone. Mark explains how Vlingo will get you navigating Twitter, Google, Yahoo, and Facebook with your BlackBerry faster and more efficiently than ever before. Stop fiddling around with your thumbs and free your hands for other things by effectively controlling your email, web searching, networ...
Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.
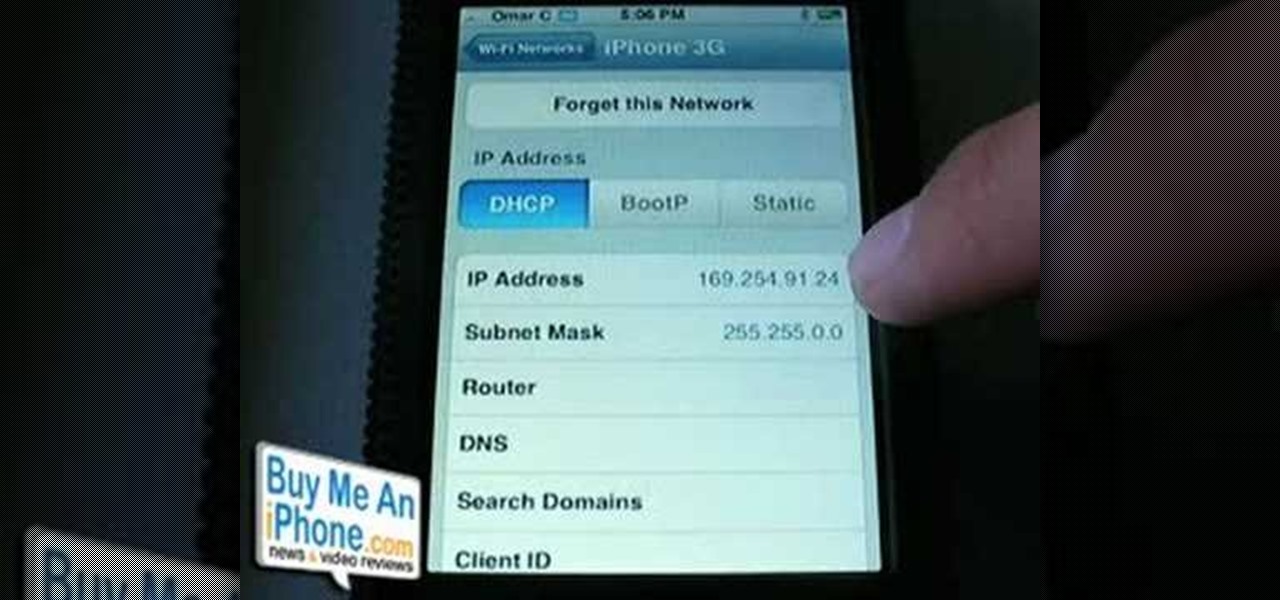
This is a video demonstration on how to tether your iPhone 3G to a Mac laptop to use the 3G network for surfing the web on the laptop. This is against AT&T's policy so try at your own risk. This is in place of the NetShare app that keeps getting removed by Apple or ATT. This let's you connect your computer to the 3G wireless network by using a proxy on your jailbroken iPhone.
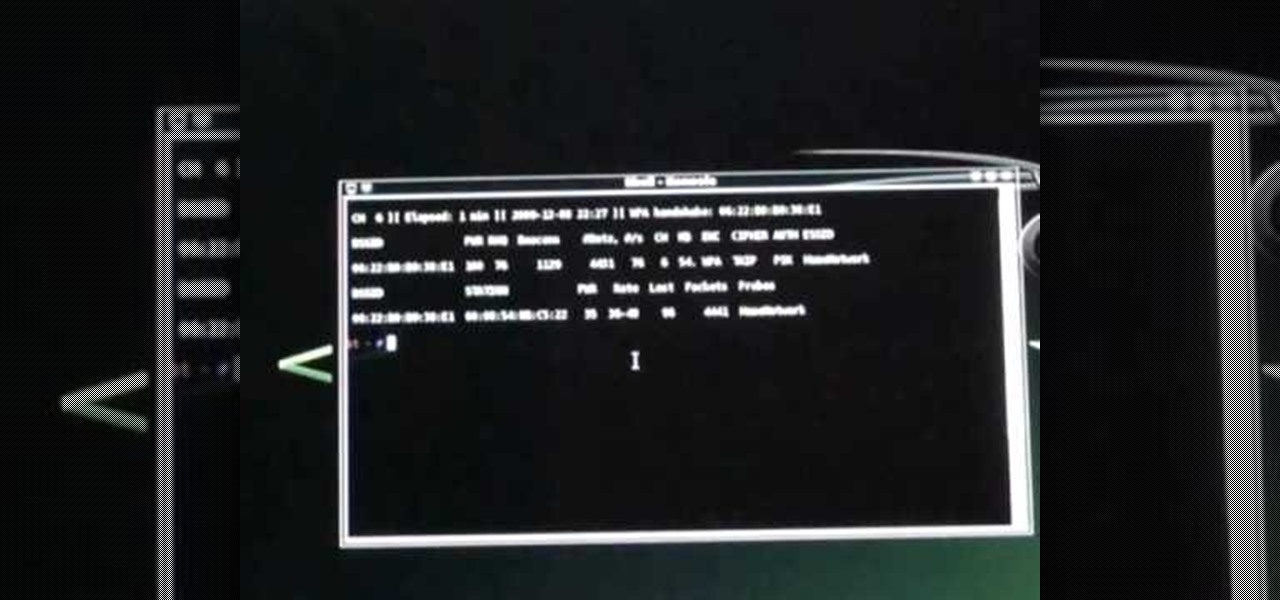
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.
Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Nokia, the Finnish telecommunications company, is about to shake things up a bit after its networks sales in the final quarter of last year declined 14% compared to sales in 2015.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!