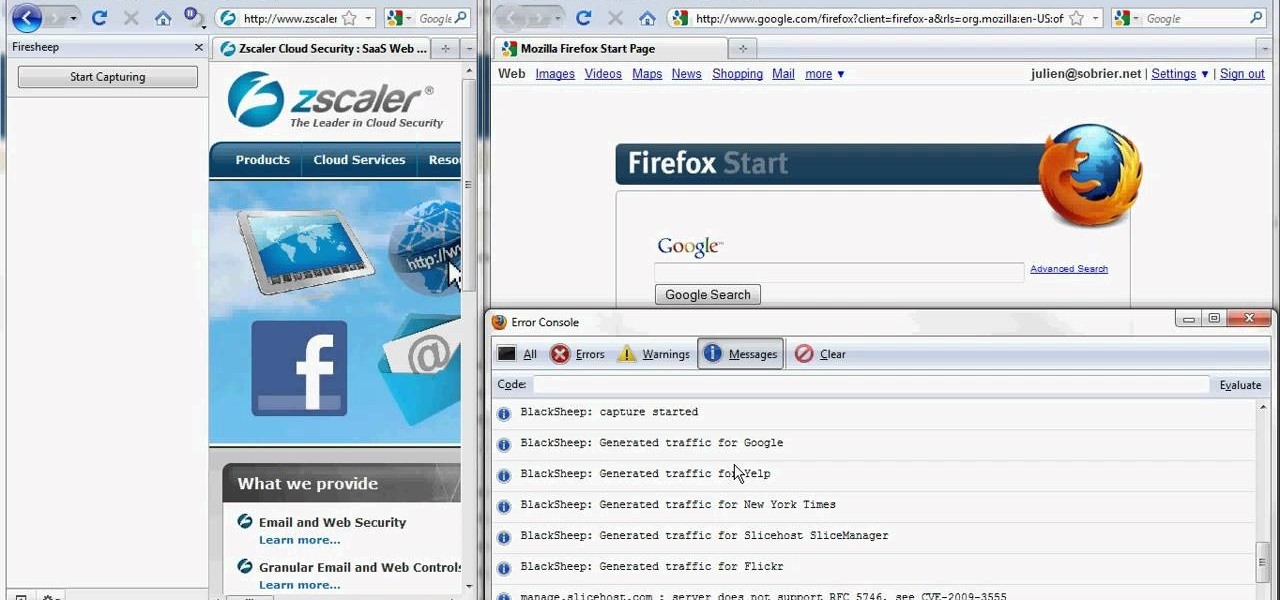
If you're scared of using public Wi-Fi networks with Firesheep out and about, then maybe you should fight back. Don't switch to another web browser— keep using Firefox safely with the help of a new Firefox Add-on that combats Firesheep's password stealing capabilities. It's called BlackSheep, and when installed and running, it will alert you whenever Firesheep is active on your network connection.
In this tutorial, learn how to save yourself the money you'd pay someone to unlock your Google G1 phone from T-Mobile and do it yourself in just a few quick minutes. This is actually a very easy process and this clip will walk you through the process step by step so you can freely use your phone on any network and not be limited to T-Mobile. This is also helpful if you wish to give away or sell your phone to someone on a new network.
In this clip, learn how to tether your rooted Droid to a WiFi network and use it as a modem for your other Wireless devices. This process is pretty easy and only requires a network and that your phone be rooted.

In this culinary how-to from the Food Network's Ellie Krieger, you'll learn how to bake delectable, almost-healthy carrot cupcakes using whole carrots, lemon zest, canola oil, brown sugar, two eggs, 3 quarters of a cup of whole wheat pastry flour, 1/2 cup all-purpose flour, 1 teaspoon of baking powder, 1/2 teaspoon of cinammon, 1/4 teaspoon of nutmeg and a 1/4 teaspoon of salt.

Watch this video fashion design lesson to see who took second place in the Generation-t tee recon contest with how-to make a wrap shirt. All you need is two t-shirts and the steps, so follow along and get sewing.

Watch this fashion design lesson to see who took third place in the Generation-t tee recon contest with a how-to for making a no-sew fringe halter top!

This week Meg takes us back in time and shows us how to make an amazing Starburst mirror. Follow along with the home interior how-to video, and learn how to add a little vintage flair to your own home decor.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.

Mike Biggly shows us how to set up our home internet and networks. Part 1 of 20 - How to Set up your home internet and network.

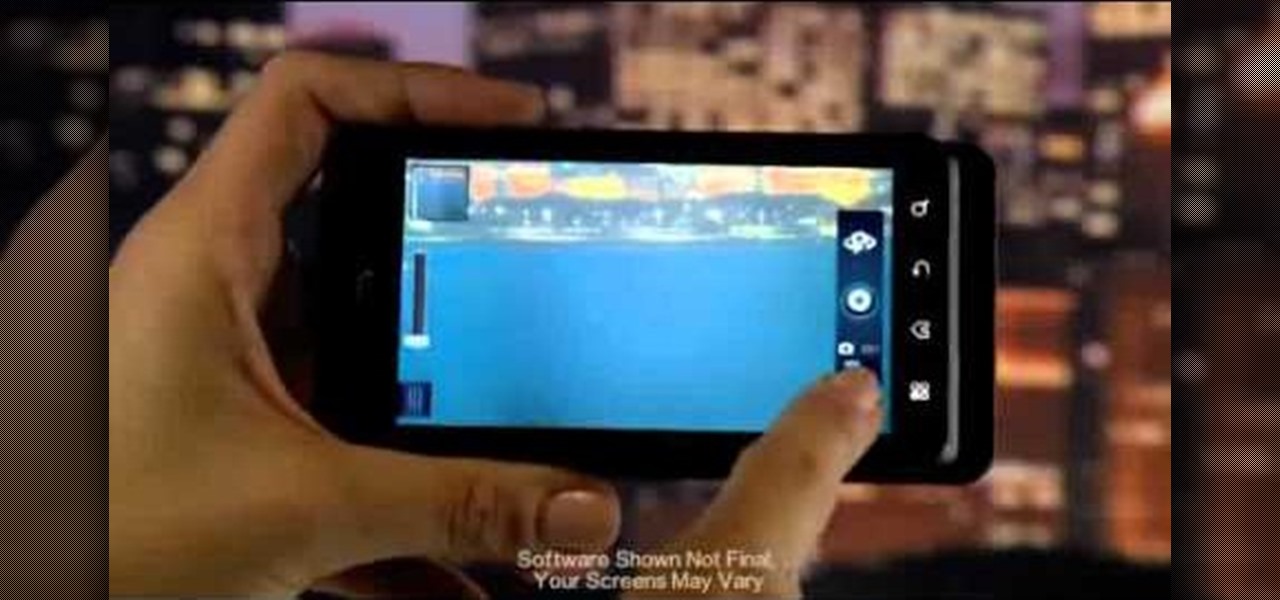
The Droid 3 smartphone from Verizon has a great camera perfect for taking beautiful photos. If you want to learn how to perfect your on-the-go photography, take a look at this tutorial from Verizon Wireless that features instructions on all the different settings in the Camera app on the Android device.

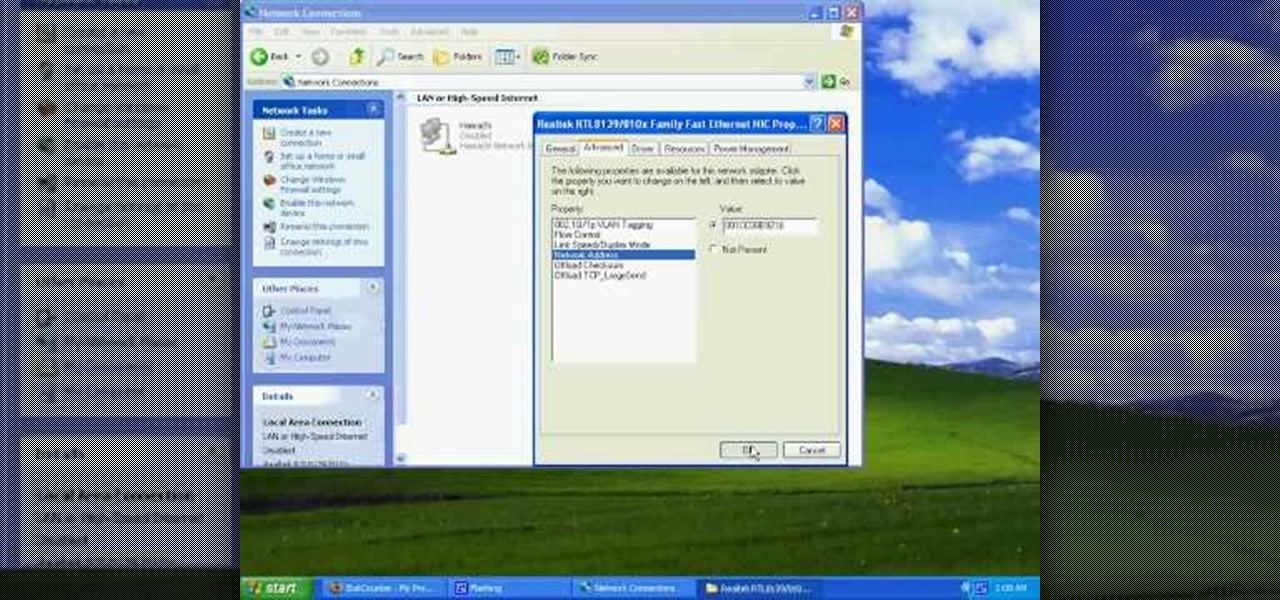
This video tutorial from tarunkumarsinghal shows how to change Mac address on Windows XP. Click Start menu and then Control Panel. Make sure control panel window is in classic view mode. If not, change it to classic from the left pane.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

In this video, we learn how to pull a compilation of computer pranks on a friend. The first trip is a mouse prank where you will open up the control panel and find the mouse settings. From here, you can switch the buttons from left to right and change the speeds of the mouse. Next, you can do network pranks by running cmd.exe as administrator. Then, go and see who is on the network and type in "msg /server:(ip address) and message". You can also do a ghost typing prank, which you will create ...

First click the explore button, this will open a fold in which you will click homegroup and the second computer in the network. By clicking on that you will see what is in the homegroup. For example clicking on the video icon shows you all the videos available. If you right click on the video you can choose to watch it, open it, send it to different places, drag it onto your computer or copy and paste it into another directory.

Today we learn how to brine pork and poultry with the Food Network. You only need to have salt and water to make your brine for your pork. First you need to grind up your salt into a fine powder, which will make dissolving easier. Now dissolve your salt into your water. Complete submersion is very important when soaking your meat. If you're soaking a turkey or a goose use a cooler for full submersion. Let it soak for ten hours. Now your cuts of meat will be more juicy and tasty.

Facebook is one of the most popular social networking sites out there, so make sure you are being safe! Susan Kline shows you in her Facebook Essential Training series how to Restrict certain aspects of your profile. Login to Facebook and view your Privacy Settings. From there you can pick your About Me, Personal information, Wall Post, Photos and more and restrict showing it to people. You can pick everyone, certain friend lists, Networks, and even individualize it down to one person.

Do you long for a Polynesian vacation? Do you wanna go back to your little grass shack in Hawaii? Well, if you can't afford that, you can at least have a stylish "staycation" at home with your own homemade tike bar. You'll learn to build one in this Decor It Yourself video tutorial.

Save the trees! Have a few extra wire hangers hanging around? Make your own retro Christmas tree for your next holiday season out of old hangers, wiring, and shiny tinsel. With help from ThreadBanger's Decor It Yourself, your new Christmas tree will be done in no time, standing tall and eco-proud!

Have you ever heard of wet felting? Well, it's the oldest form of textile making and relatively easy to work, thanks to this tutorial by ThreadBanger. Learn how to create a classic-looking beret for this winter season. No sewing required!

ThreadBanger give us a great recipe to make a unisex bomber hat using just a flannel shirt, white faux fur, a measuring tape, the bomber hat pattern, a sewing machine, and two and a half hours of your creative time. Add pom-poms at the ears to give it extra flavor! Super cool look for both dudes and ladies.

This week Corinne shows us how-to make a classic back to school accessory that can be worn by both the guys and gals. This quick and easy tie is sharp, and will start the school year off right. Just follow along with the steps in this how-to video and you'll be on an honor roll.

The Great Zenovka and her lovely assistant show us how-to make a cowl neck halter top. Just get an old t-shirt, follow along with this how-to video, and you're ready to go in style.

To kick off T-shirt Madness week, Threadbanger forum member ArtCrazed shows us how-to make an adorable purse out of two old tees! Follow along with the steps in this how-to video and learn how to refurbish some old clothes into something new!

This week Megan Nicolay returns to show us how-to make a sexy halter with a plunging neckline from her new book, Beyond Fashion. So get out the old tees and get to cuttin'.

You wanted more summer lessons, you got em. This week learn how to take an old mens shirt and turn it into a rockin new rockabilly swim suit. Just follow along with the steps in this video and take your new stylish suit to the beach.

Weddings, and wedding dress especially, can be very expensive. This how-to sewing video shows how to customize and personalize an affordable option. This week, Rob and Corinne answer a viewer question and show us how-to make a $10 wedding dress out of tee-shirts.

In honor of Rob and Corinne's trip to Makerfaire, we visit Zoh Morrigan of Morrigan NYC for a lesson on how-to make spats. Steampunkin it up!

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.