The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

If you're an avid programmer or developer, your time is likely spent creating apps and perhaps the occasional website. And while these go-to coding endeavors are exciting and occasionally lucrative, more and more coding pros are turning to careers in cybersecurity and ethical hacking — thanks to the high pay, flexibility, and unparalleled opportunities.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

Cybersecurity is an industry that isn't going anywhere. After the mass move to online work, the need for more cybersecurity professionals skyrocketed. That demand isn't going away because more and more industries are keeping online and cloud services going for their workers.

Ethical hacking is a useful skill that can make you stand out in the field of cybersecurity. Whether you're just entering the field or are already established and are looking to stay current, learning the fundamentals of the white hat is an essential skill for your professional development.

When choosing a camera lens, use a telephoto lens for a zoom or a wide-angle lens for a broader view, which allows photographers to fit more of a subject into a photo. Choose the right lens for a specific photo with the tips in this free instructional video on photography tips from a professional photographer. Lens are very expensive, so make sure you are educated before you buy a new camera lens.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

First of all you need to place your palms on the floor and place your feet upside and touch the wall. Now start walking on your hands backwards towards the wall and at the same time moving your legs higher on the wall. Try to get as close as to the wall. Once you are into the basic hand stand then hold this position for sometime. After this get out of the hand stand position and then again repeat this exercise and holding for five to thirty seconds. Do it five to ten sets. And do it five to t...

How should you write in copperplate? Hamid will show us how write E and e in copperplate. First we need a book and a pen specially to write in copperplate. This type of font has letters with narrow edges and it gets broader in the middle. For capital 'E', it will be in curved form with the font's unique style of thickness. The small 'e' more looks like a 'c' with a closed loop. It will help in improving your handwriting style and add some grace.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.

In this video tutorial, viewers learn how to dress to flatter their body shape. The female body has three key physical inflection points. These points are: the chest, waist and hips. There are four basic body types. These body types are: apple, pear, hourglass and banana. The apple shape has a full face, broader shoulders, fuller breasts, undefined waist, narrow hips, flat rear ends ans shapely legs. The pear shape has slender neck, narrow shoulders, narrow back, small or medium bust, defined...

First of all you have to put some clay over the potter wheel. Now add some water and then press hard with your fingers at the bottom. Now slowly release the pressure of your hands and bring your hands upwards while slowly releasing the pressure. This shall form an inverted cone shape. Now apply pressure with your thumbs at the top to depress in the top and then wash your hands with water. Now use your thumbs to make this hole bigger. Now put a little water in this hole and then use your finge...

This video shows how to draw an anime Fox Furry. First, draw the outline of the face, neck and straight-up ears. Then draw the eyes with eyebrows and make them prominent, to look nice and real. Then draw the nose and mouth. Then give borders and shades to ears to look prominent. Then outline and draw the hairs over the head, a little on the face and also side hairs. Then for finalizing the eye part, adding pupils to the eyes to look a little real, and more bordering the eyebrows. Then, draw t...

Learn how to do wide grip lat pull downs. Presented by Real Jock Gay Fitness Health & Life. Benefits

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

The overarching and expanding field of data science and analysis has become virtually inseparable from areas such as programming and development.

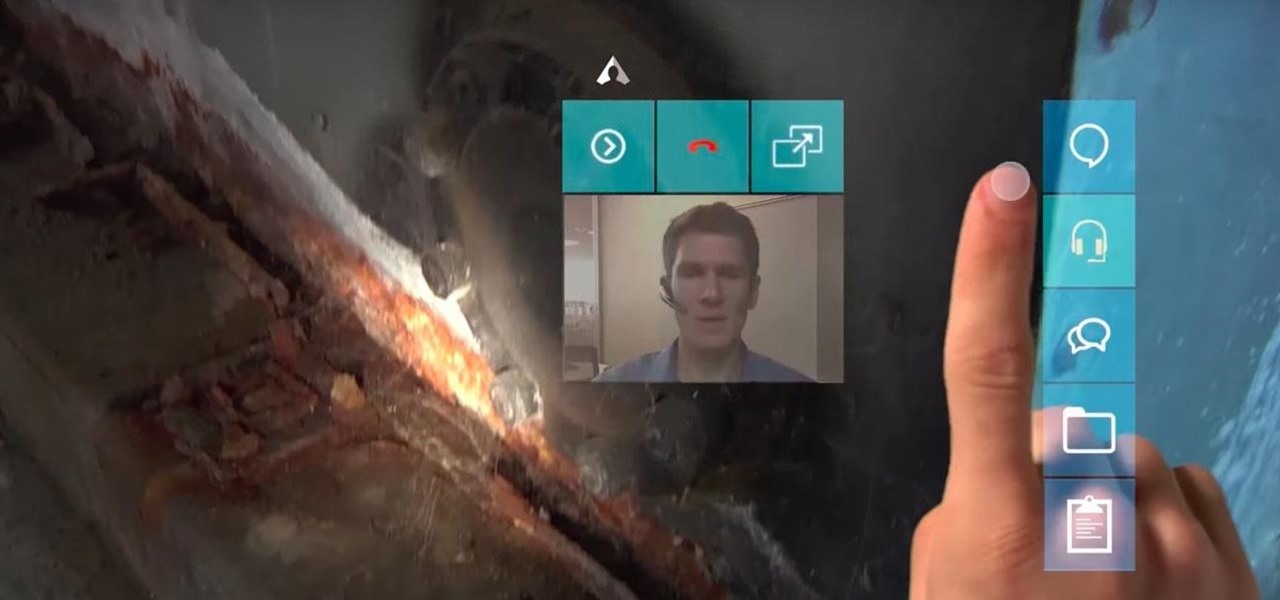
What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

A thesis is the basis of any paper or essay. The thesis statement sets the tone and subject of your paper and starts you off on the right foot. In this tutorial, learn how to write an impressive thesis statement and get an A on your next paper!

After leaning on augmented reality for its outdoor advertising, HBO has called on augmented reality again via Snapchat to promote its Watchmen series.

It appears that the floodgates of consumer-grade augmented reality smartglasses from China are now open, with Mad Gaze being the latest company to rush its product through.

The research team at Google has found yet another way for machine learning to simplify time-intensive tasks, and this one could eventually facilitate Star Wars-like holographic video.

Data visualization has many applications in virtual and mixed reality, since a third dimension literally adds important depth to the represented information. A new app called HoloFlight is a good example of this, combining flight-tracking data and the Microsoft HoloLens to surround you with a look at every plane in the sky.

If there's anything we've learned during 2020, it's that working and learning from home is going to shift the way we do business. With Microsoft announcing that its staff will be allowed to permanently work from home, expect more businesses to follow suit.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Drive.ai (a startup founded by Stanford University graduates), Waymo, General Motors, and serial entrepreneur and author Vivek Wadhwa are featured in today's top news.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

The last few months have delivered some great new Magic Leap releases, but that doesn't mean the development team is resting on its laurels when it comes to the platform itself.

Not all enterprise augmented reality tools require a high-end headset and heavy computing power. Sometimes, a smartphone can do the job just as well. Along those lines, software maker Atheer is now bringing its workforce AR platform to iPhones and iPads via a native app.

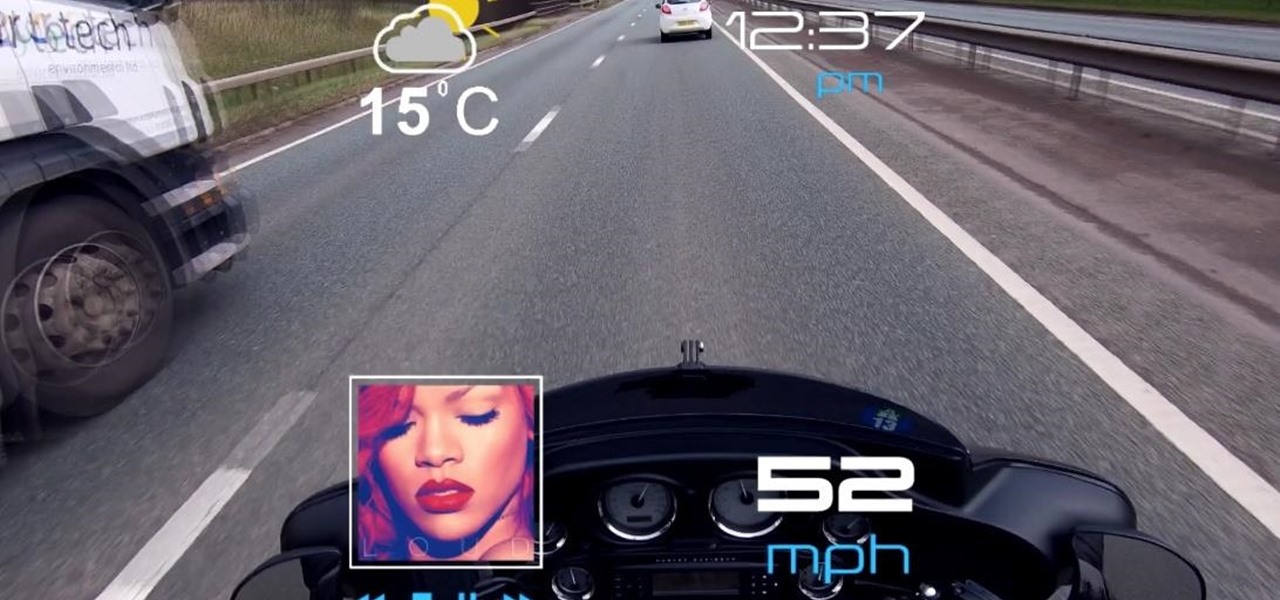
Less than a week after securing a $25 million Series C funding round for automotive HUDs, DigiLens has introduced a new waveguide display for motorcycle helmets that's thinner, lighter, brighter, and manufactured at a lower cost.

Department store chain Target is the latest retailer to offer an augmented reality cosmetics app for customers to virtually try on lipstick.

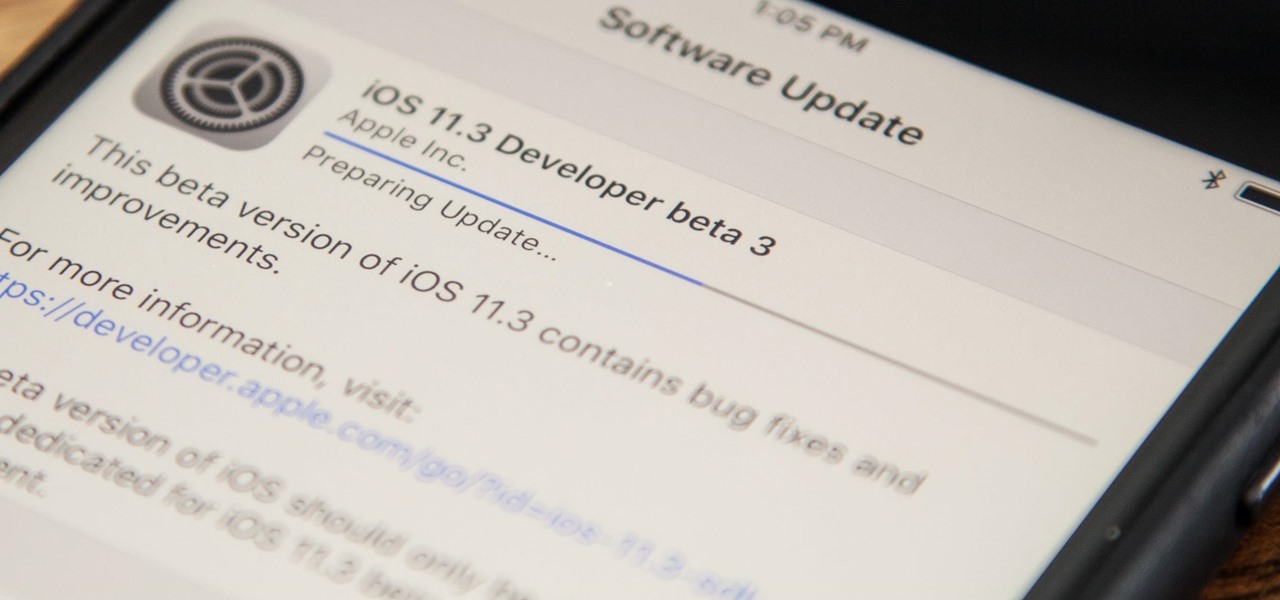
Apple just released the third beta for iOS 11.3 on Tuesday, Feb. 20, which comes exactly two weeks after the release of iOS 11.3 beta 2 that brought battery health data and performance-throttling controls. At first glance, iOS 11.3 beta 3 seems to be mostly under-the-hood improvements, but we'll know more as we dive into it.