If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Today is the 10-year anniversary of the death of Apple co-founder and former CEO Steve Jobs. To commemorate the occasion, Apple has posted a message and a mini-documentary on its website.

The music you listen to is often a reflection of your personality, which is why people tend to use the artwork from their favorite albums as device wallpapers. But one lonely album cover may not look right on your iPhone's lock screen, and it's not indicative of your broader music interests. To combine cover art into one lock screen background, there's a shortcut that makes it easy to do for any playlist.
According to Apple, Siri serves 25 billion requests per month — an enormous number for a feature that was only released nine years ago. But when you think about how much work Apple has put into Siri over the years, it makes sense that the virtual assistant is being used more and more by users with iOS, iPadOS, macOS, watchOS, tvOS, AirPods, and HomePod.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Facebook's annual earnings call on Wednesday didn't come with any big surprises, that is, if you took everything at face value.

While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and lock automatically in the first place.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

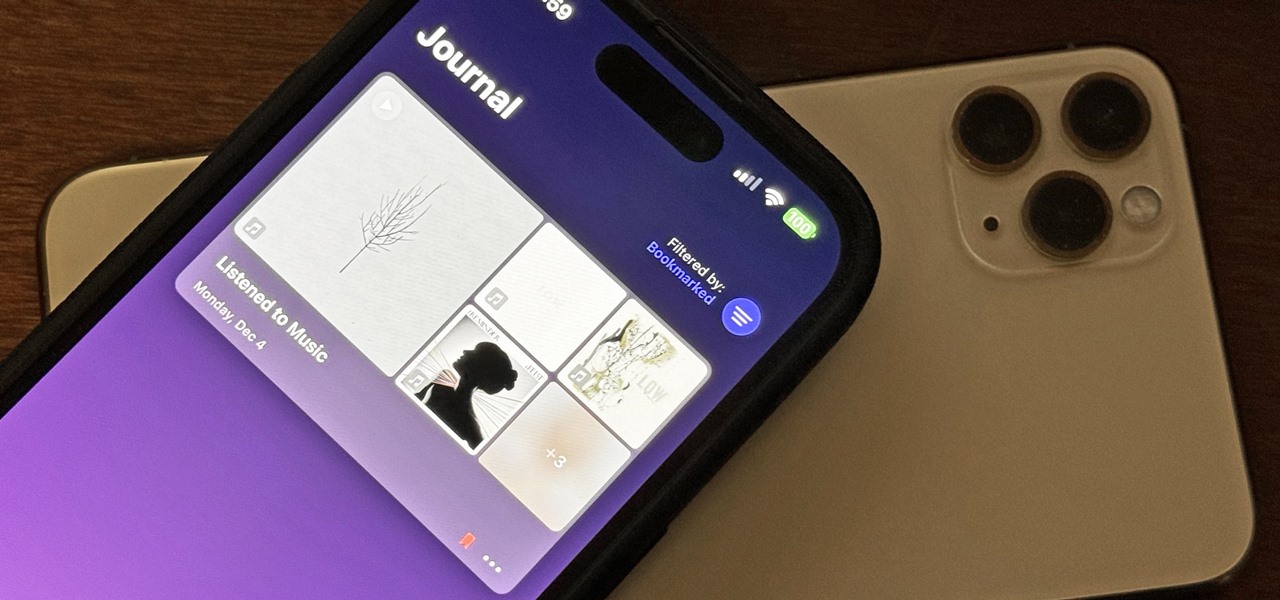
Perhaps the biggest new feature within Apple's iOS 17.2 update for iPhone is Journal, a new journaling app designed to help you take a moment to reflect each day using reflection prompts, recommendations via on-device intelligence, and suggestions for recent activities and events.

Apple Notes has received many improvements over its lifetime, but noticeably absent year after year was the ability to easily add quick links in notes to other notes for reference. The latest software updates for iPhone, iPad, and Mac finally address this with a simple note-linking tool.

You may not always want to, but there will probably be a time when you'll want to know if an email you send — like a job application or a support request — is opened by the recipient. It's actually easy to implement, and you may be using an email client on your device right now that supports email tracking.

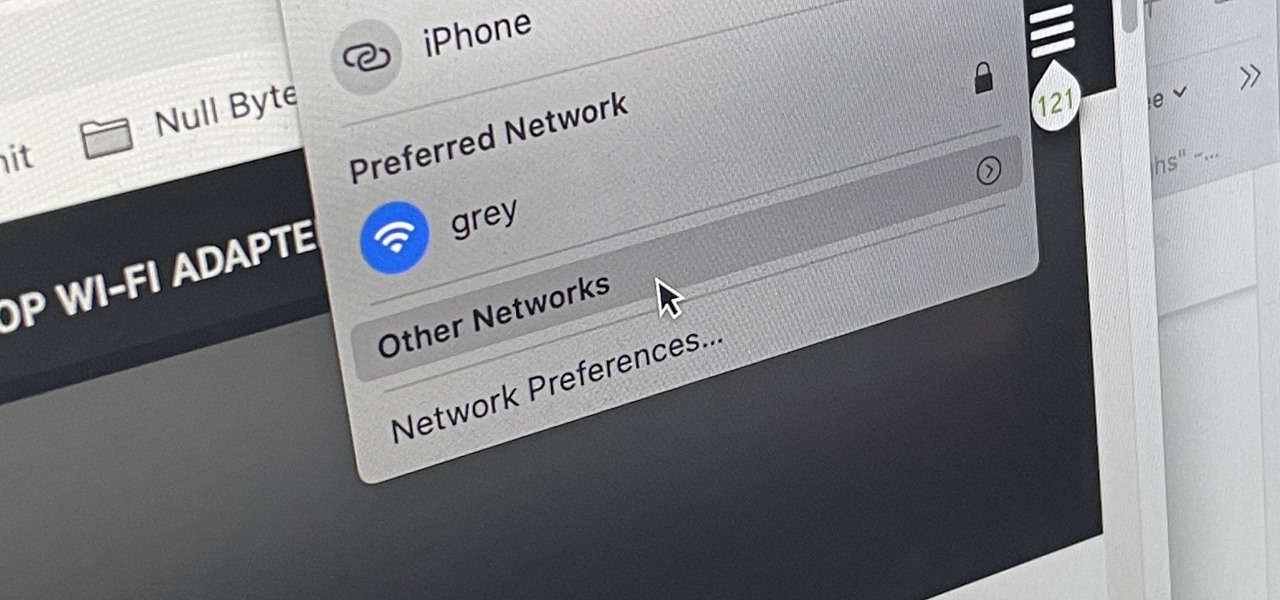
There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?

The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if you don't know what the target computer is, you might come up empty. That's where the WiFi Duck comes in handy.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used for pro-level videography.

While many of the features in the iPhone 16 and 16 Pro series build on what we've seen in previous iPhone models, Apple has packed the 2024 lineup with iOS 18 and plenty of fresh upgrades worth considering.

There are some important new features in the Photos app on iOS 17 and iPadOS 17 that will streamline editing, give your pets more recognition, help you learn about the world you've captured, and even add a bit of fun to your day. There are even a few hidden tricks that may surprise you.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

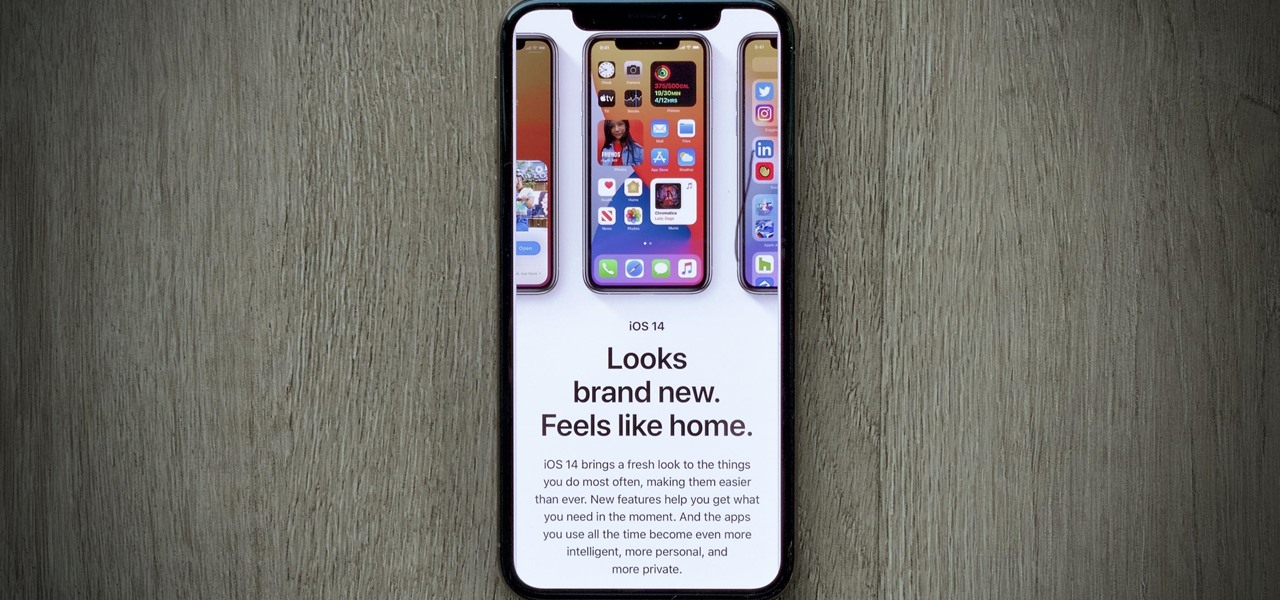
Apple's iOS 14 is here. With it, you'll see over 200 new features and changes hit your iPhone, including home screen widgets, inline replies in Messages, and cycling routes in Maps. Here's how you can get your hands on the brand new update.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

Apple just seeded developers and public beta testers the GM (golden master) for iOS 14 on Tuesday, Sept 15. The update (18A373) comes just after Apple's "Time Flies" event, and six days after Apple released iOS 14 beta 8 for both developers and public testers.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.
Yesterday senior State Department official Alec Ross publicly announced that the Obama administration opposed CISPA, but refused to entertain the notion of the bill being vetoed.

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. If you missed this Workshop check out the follow up tutorial Techniques in Architecture.

When the New York Times paywall first went up, there was a whole lot of balking. The idea seemed egregious to most, and the digerati's overwhelming conclusion was that the system would fail. But interestingly enough, there is speculation that the NYT is actually experiencing an increase in their print subscriptions, which according to Business Insider founder Henry Blodgett, is due to users feeling less guilt over buying the print media if, after all, the digital version is no longer free.

Artist Marshall Astor has made a fully functional Rubik's Cube out of bronze. What? No differentiated, colored sides? How do you play? Apparently there's reasoning behind it. Astor gets deep:

When you're looking for a glam, 'come hither' look, a metallic smoky eye is a great choice. Here's a quick guide to do it in less than 3 minutes: Foundation and Primer

If you've been reading, watching or listening to the news, you sure know about the Trayvon Martin case. If you visit this site often, you may also have noticed that I've not put up any news on this case. I have my reasons. And this post will describe why.

Amazingly, a lot of people I know haven't even heard of SOPA or PIPA. Now, every English-reading person with an internet connection will finally have those two four-letter acronyms emblazoned in their minds. For the entire day today, Wikipedia's English-language site will be in total blackout in protest against the proposed legislation in the United States. And that's not all. MoveOn, Reddit, BoingBoing, Mozilla, WordPress, TwitPic and other popular websites are down today in protest.

I've been unreasonably excited about Dungeon Defenders (NOT DUNGEON DEFENDER!) for almost a year. Playing it at PAX did nothing to damper that enthusiasm. I had a chance this week to speak with co-founder/development director Jeremy Stieglitz and marketing diretor Philip Asher from Gainesville, Florida based developer Trendy Entertainment to find out a little more about the game, and how it came together.

Not every DIY project is as executable as, say, making a potato gun. Occasionally, we observe a quixotic project that is just plain wonderful. Consider rich guy Philip Anschutz and his eponymous Anschutz Entertainment Group (AEG). His ambition to bring an NFL team to Los Angeles is a Fitzcarraldo-sized DIY project that, if the stars align, might happen in time for the 2016 season.