Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Feeling unprepared for the next earthquake? In this tutorial, learn what to do and what not to do to survive "the big one". You'll be surprised to learn that hiding in a doorway is a myth!

It was bound to happen with all those numbers floating around in your brain – you've forgotten your Windows password. Here's how to recover it.

Ditch those namby-pamby clichés like skeleton decals and peeled-grape eyeballs. This year, give your guests a real scare.

Watch this video to put your Eee PC in advanced mode, which makes it look like XP. The steps are as follows

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

They say it is always darkest before the dawn. If that's the case, then perhaps there's a light ahead for Magic Leap after more unfavorable news in the form of executive departures.

The future of smartglasses for consumers seems ever dependent on Apple's entry into the market. Coincidentally, the exit of Apple's long-time design chief Jony Ive has shed some light on that eventual entrance.

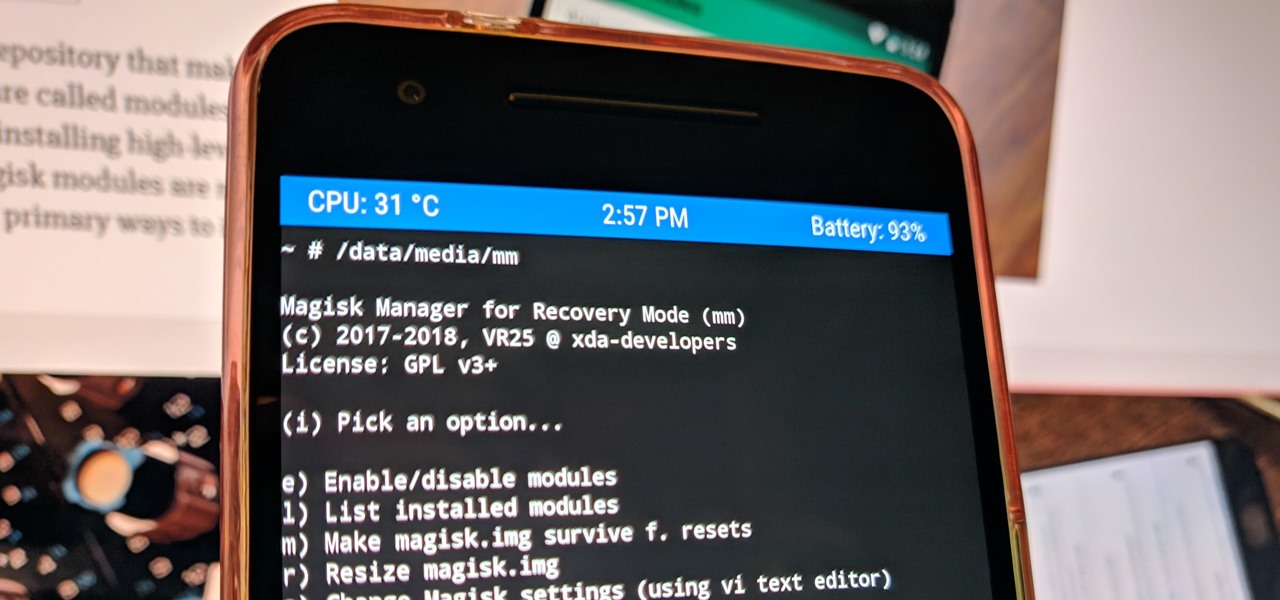
When it comes to customizing Android, there's nothing quite like Magisk. You can potentially combine dozens of modules to create a one of a kind user experience tailored to you, but not all modules will work well together. You might run into a bootloop by accident once in a while, which could cause some issues on its own.

While the notch on Apple's newer iPhones started a wave of notches across the smartphone market, there are still plenty of users who don't like screen-obstructing zone up top, and you may be one of them. While it may soon disappear in future iPhone models, or at least get smaller, there are things you can do to hide the big notch you have right now.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

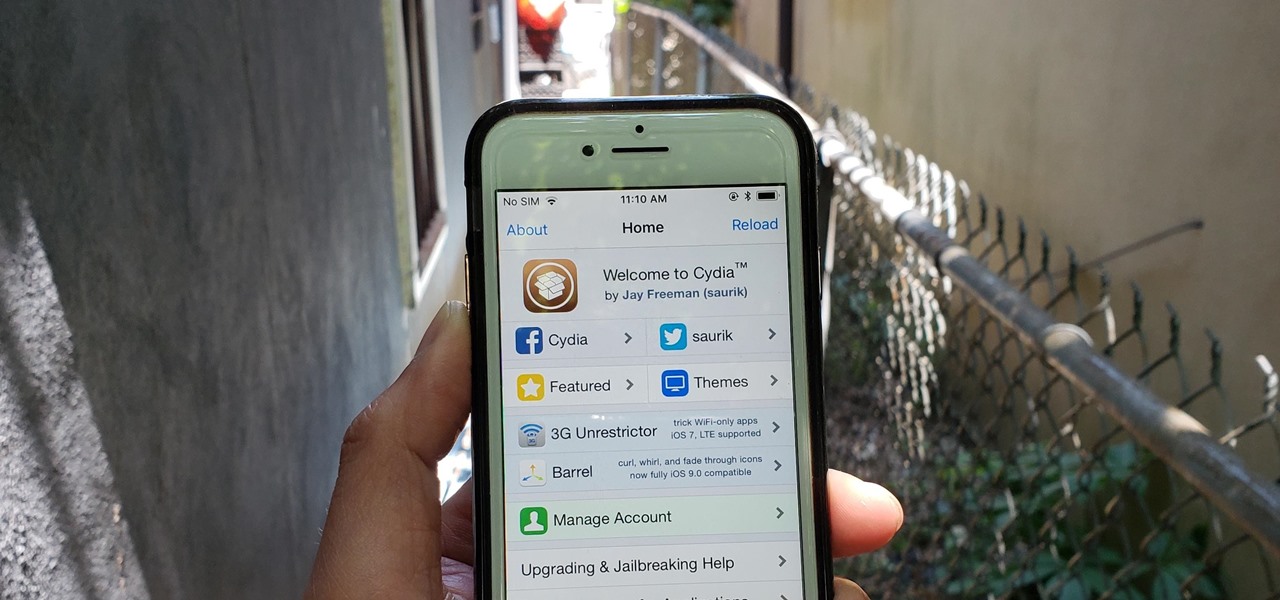
It's been a long road, but the guys over at CoolStar have finally come up with a stable, semi-untethered jailbreak for 64-bit iPhones, iPads, and iPad touches running on iOS 11.2 up to 11.3.1, with the latest update extending coverage to 11.4 beta 3. So if you've held off on updating to the latest iOS 11.4.1, your patience has finally paid off.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Before Google I/O 2018, the Google Assistant for Android and iOS had only two available voice options to choose from — a robotic female and male voice. But there are now six additional voices, and these ones sound way more natural than any other mobile voice assistant (plus, John Legend's voice is coming later this year).

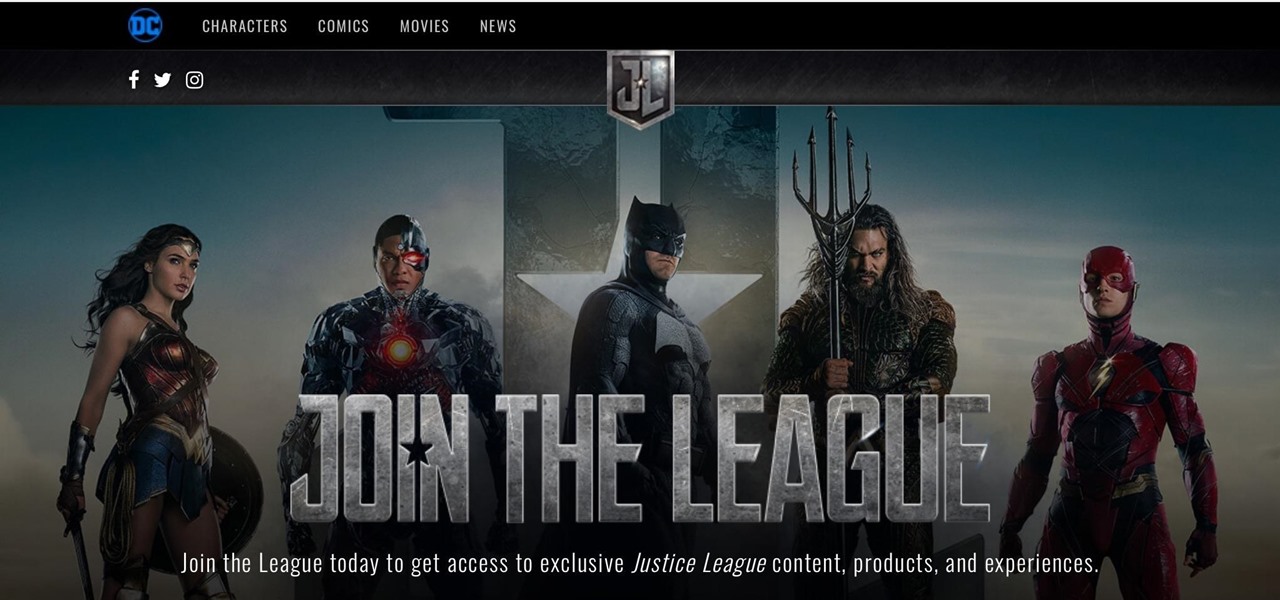
This fall, DC Comics fans will be treated to an augmented reality experience promoting the Justice League movie. Likewise, history buffs will be able to enjoy their own augmented reality content by way of the Terra Cotta Warriors exhibit at The Franklin Institute in Philadelphia, Pennsylvania and an in-store promotion featuring famous convicts from 19 Crimes wines.

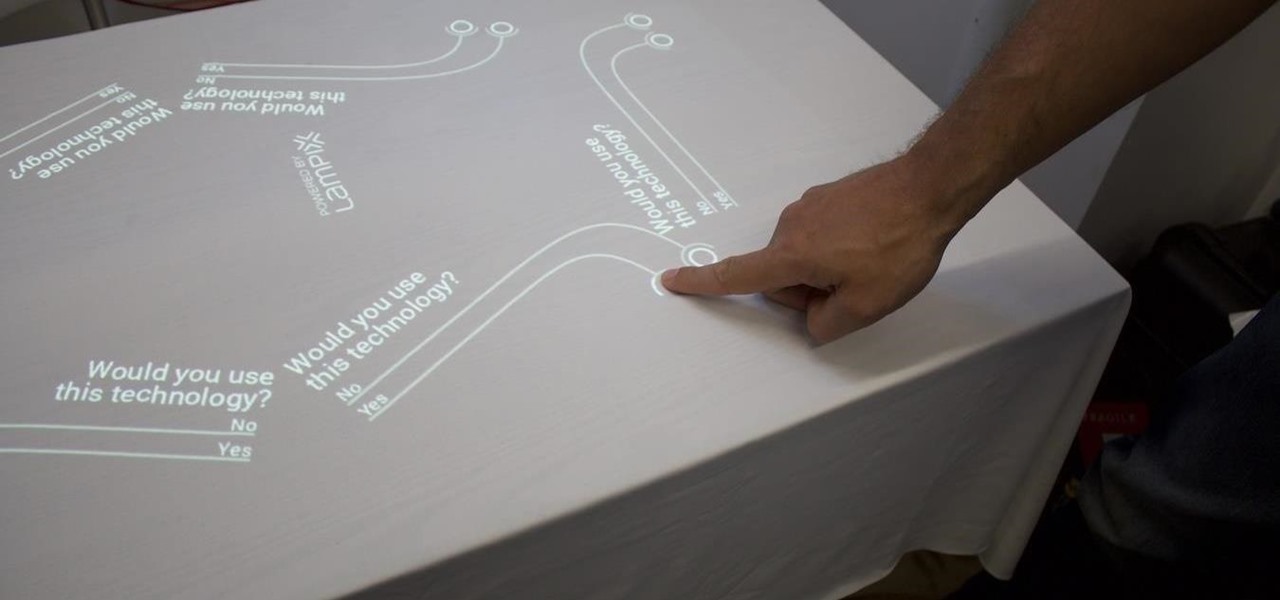
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

Widgets are great ... if you actually use them. A quick swipe right on the lock screen will reveal the Today view and its widgets, and it's very easy to accidentally open. Plus, others can see your widgets without any authentication. You could manually remove every widget, but that wouldn't prevent the right-swipe from opening the Today view. There is a way, however, to disable the page entirely.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

Why did I write this when they're tons of scanning tools available.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

If you're like me, you spend a lot of time on your computer, which can be damaging to your eyes in the long run. Studies have shown that staring at a computer screen or television up close for extended periods of time can have harmful effects on your vision.

There are spontaneous times in everyday life that just scream to be recorded on video. The crazy guy yelling obscenities on the bus. Your favorite actor at the supermarket check-out register. Maybe even your kids just being super adorable.

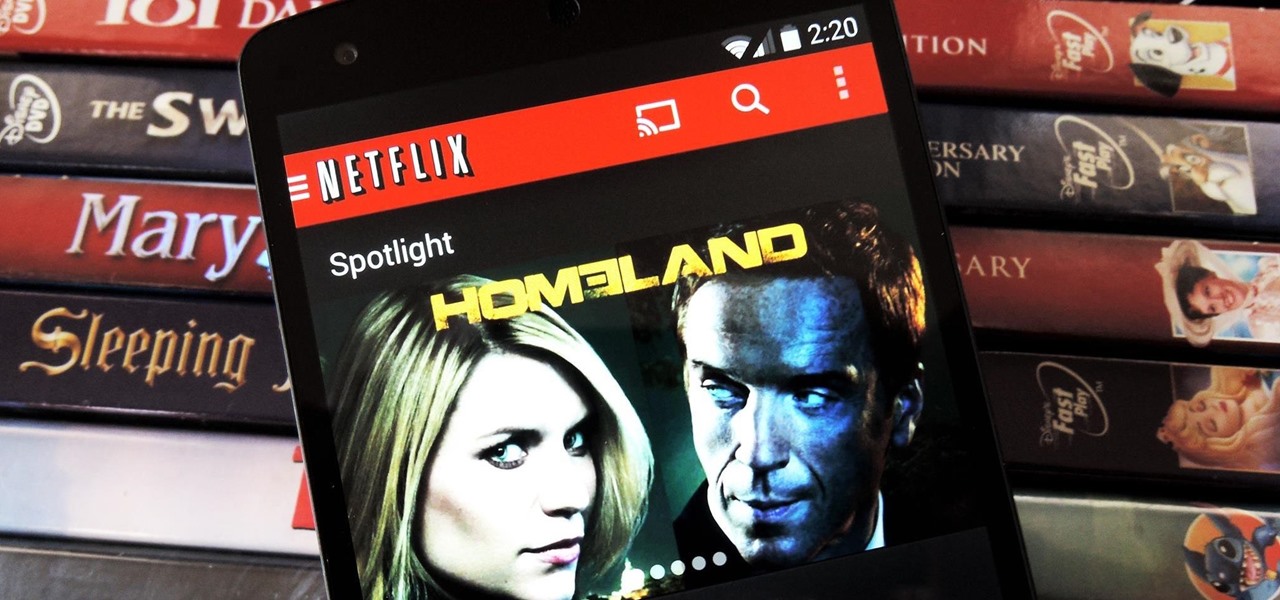
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

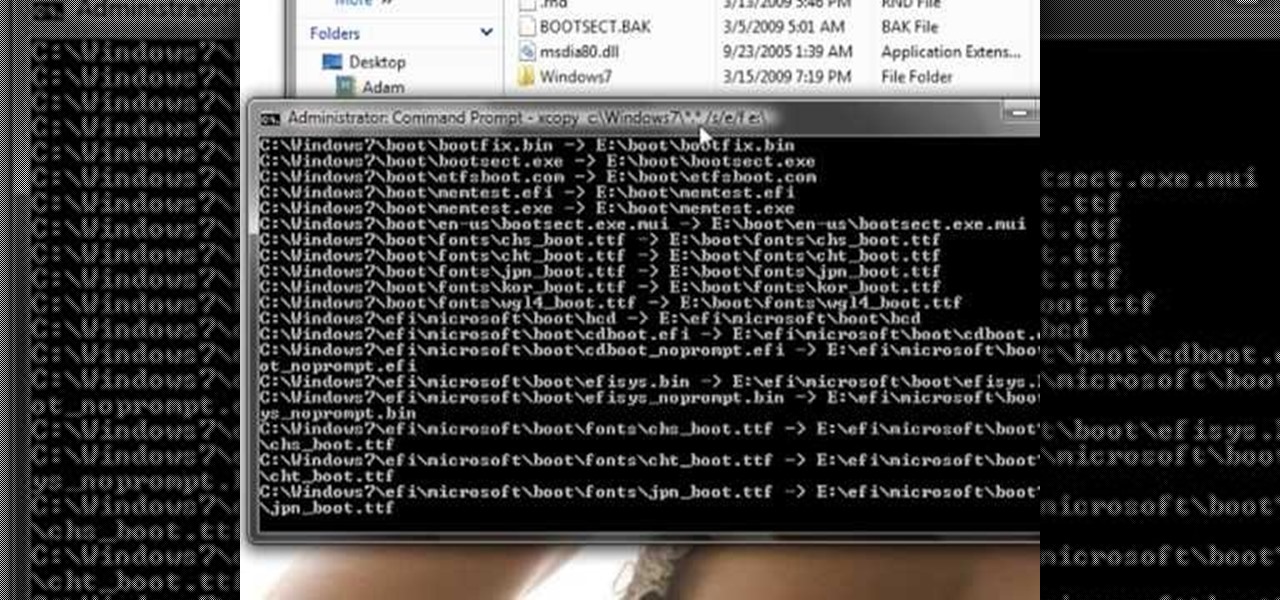
This guide works 100% for Vista & Windows 7, unlike most of the guides out there. The method is very simple and hassle free. Needless to say, your motherboard should support USB Boot feature to make use of the bootable USB drive.

Check out this video iPhone tutorial and learn how to enable MMS pciture messaging on your 3G/GS. Windows XP/Vista 32 Bit Tutorial

Now that everyone has an Android or iPhone in their pocket, there's no excuse for being late to an appointment or job interview. Thanks to that GPS receiver in your smartphone, navigating your way through city streets and highways is a cinch, in or outside of your vehicle. But once you get inside a building, that fancy GPS feature doesn't know what to do. Which direction is the elevator? How do you get to room 819? Where's the nearest fire exit? The bathroom?

Whether you are protecting your children or hiding personal information, there are ways to block unwanted websites from your computer. Follow this tutorial and learn how to accomplish this on a Windows PC easily.

If you need to capture a still image of some high-speed action, Burst mode is the way to go. Burst shots take photos in rapid succession, providing a range of pictures to choose from and ensuring that at least one great shot comes out of it. You might notice, however, that your new second-generation iPhone SE doesn't seem to sport Burst mode as your old iPhone did. Is it gone? Not at all.

Recovery mode and download mode are useful for modding and they can come in handy in a pinch. Booting into recovery mode to do a factory reset or wipe cache fan save your Galaxy S20 from a soft brick, and entering download mode lets you install firmware with utilities like Odin and Smart Switch.

The powers of the Nreal Light continue to increase incrementally with each passing week. Now, the latest feature added to the device is possibly the most requested feature for anyone who has tried the Nreal Light: hand tracking.

The UK has officially exited the European Union, completing the long and tumultuous Brexit story and putting the storied nation once again on its own on the international stage.

The deadly Wuhan coronavirus outbreak has not only has claimed lives in China but also has caused disruption around the globe, particularly in the tech industry. To date, the virus has claimed more than 1,000 lives in China, according to the country's officials.

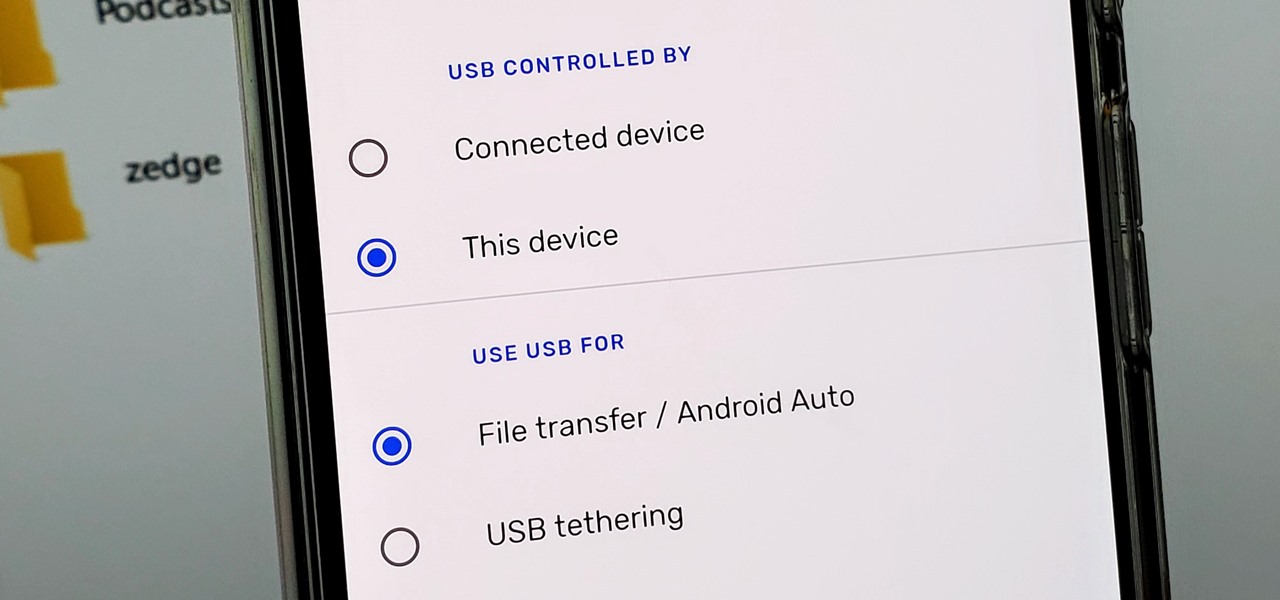
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

Screen recording on your iPhone is one of the easiest ways to share what's happening on your screen with family and friends. The problem is, everyone knows it's a screen recording when you pull open Control Center to tap the record button. What if we told you there's a better way to end a recording, so what you're left with is a clean video?