
How To: Jab dribble, step back, and shoot in basketball
This video shows you how to use a great faking technique for a Fast Break situation - the jab dribble, step back and shoot basketball drill.


This video shows you how to use a great faking technique for a Fast Break situation - the jab dribble, step back and shoot basketball drill.

Got a big research paper? It’s not nearly as daunting if you break it down into steps.

Learn how to make K'NEX axles that can hold more weight without bending or breaking for your RC Car Trailers.

Instead of buying expensive peat pots to plant your seeds in, make these spiffy planting pots by rolling recycled newspaper around a glass or jar. The finished pots are sturdy and will break down quickly once they've been planted in the soil.

The summer's fading fast and it's back to school time again. This week we're breaking you off some tips to help you become the most fashionable in your class, plus we show you how to transform last year's threads into this year's cool, new school gear. Class is now in session!

Chopping up downed trees and sending them to the landfill isn't ideal. It's better to use them as firewood or have them chipped up and use them as mulch material or for a walkway. Never combine woodchips with the soil because they rob the soil of nitrogen, phosphorus and potassium but they're great walkway material and will gradually break down providing nutrients for the soil.

Watch banjo expert Geoff Hohwald teach you how to play the banjo arrangement "Roll in My Sweet Baby's Arms." This is a good lesson for beginners as it has easy measures. This video breaks the arrangement into pieces for accelerated learning

This video is a demonstration of proper shifting technique on the cello. Learn the different hand shifting methods: The underhand and the overhand. Each movement is broken down and explained in detail.

After you can do a nosepick, you can try a toothpick. You want your weight centered and you should use your front breaks for a toothpick. They help stabilize you.

This lesson is for advanced guitar players and there are some sticky moments in the chorus. Follow along and see how Justin breaks down playing The Offsprings "Pretty Fly for a White Guy".

Straight from south India, coconut rice is enoyed with or without gravy. A few simple ingredients of rice, coconut, broken chashews and Indian spices make this a very tasty side dish to your Indian meal.

Biscotti is a tasty afternoon snack and also goes great with a steaming cup of coffee. Learn how to make almond biscotti at home. You will need almonds, baking powder, salt, flour, sugar, eggs, vanilla extract, and almont extract. Happy coffee break. This is an Italian snack.

This video is a demonstration of how to play the main riff from Eric Clapton's classic song Layla. Each part of the riff is broken down and explained slowly. Playing the riff involves power chords, pull offs and hammer ons.

The number-one question people ask me is, how can I update a room without breaking the bank or enduring a complete remodel? The answer is-you guessed it-in the details. The changes I'm suggesting fall into four main categories: lighting, furniture, walls

Learn how to repair a broken or loose joint on your chairs or other furniture for long-lasting stability. Chairs take a real beating over time and it's only natural that over time one of those glue joints is going to fail. What do you need? Well to start with you need some common, everyday carpenters' glue.

This clip shows how to make a swan using a single piece of paper. It is broken into separately titled sections with brief written instructions. The video that follows performs those instructions shows the folds and the results of the intermediate steps.

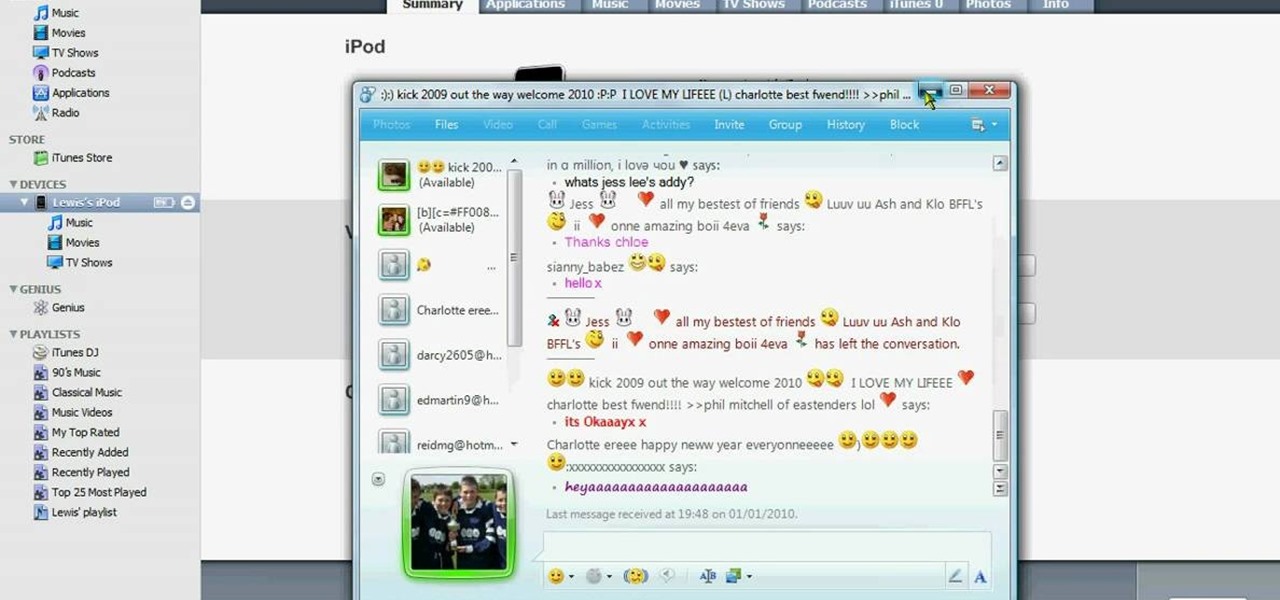
In this video tutorial, viewers learn how to transfer music from an iPod device to their iTunes library using the program, Senuti. This application is only available for the Mac computer. Begin by opening your main browser and go to the site: Senuti. Then download the application and open it. Now insert your iPod device. Then select all music files in your iPod device and transfer it to your iTunes library. This video will benefit those viewers who use a Mac computer, and would like to learn ...
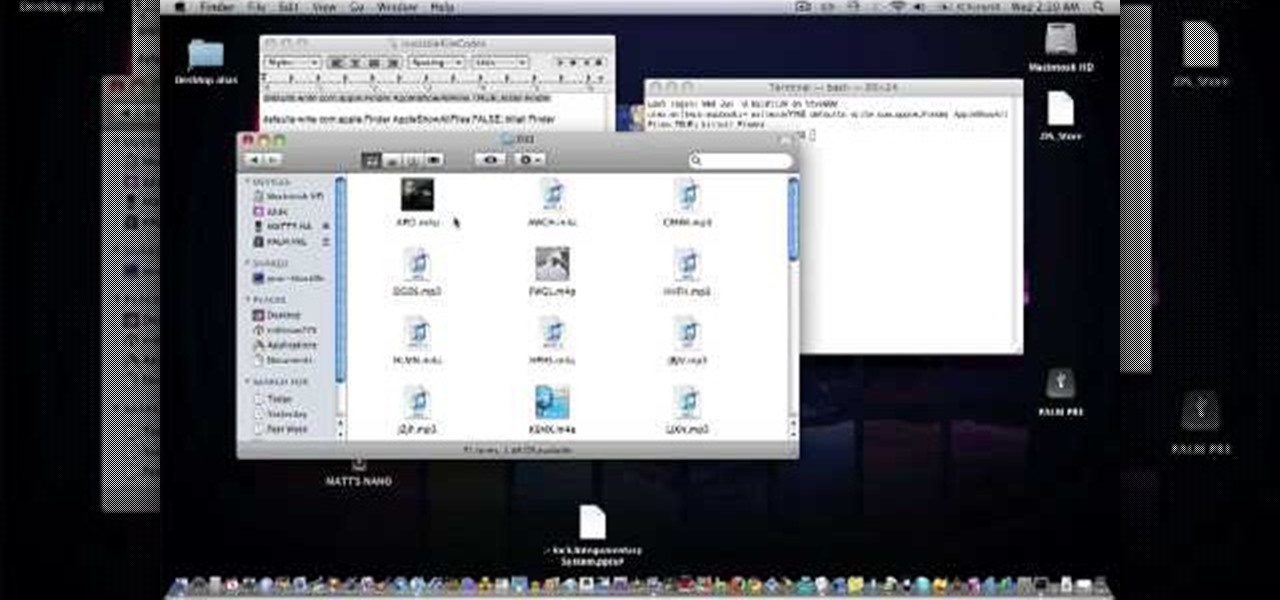
In this video tutorial, viewers learn how to transfer music from an iPod to a computer with using any software. Begin by plugging the iPod device into the computer. Then go to My Computer and open the Folder Options. under the View tab, check "Show hidden files, folders and drives". Now open the iPod device's drive. Click on iPod Control, select Music and copy all the files located in that folder. Those files are the music files, but they do not display the music names. This video will benefi...
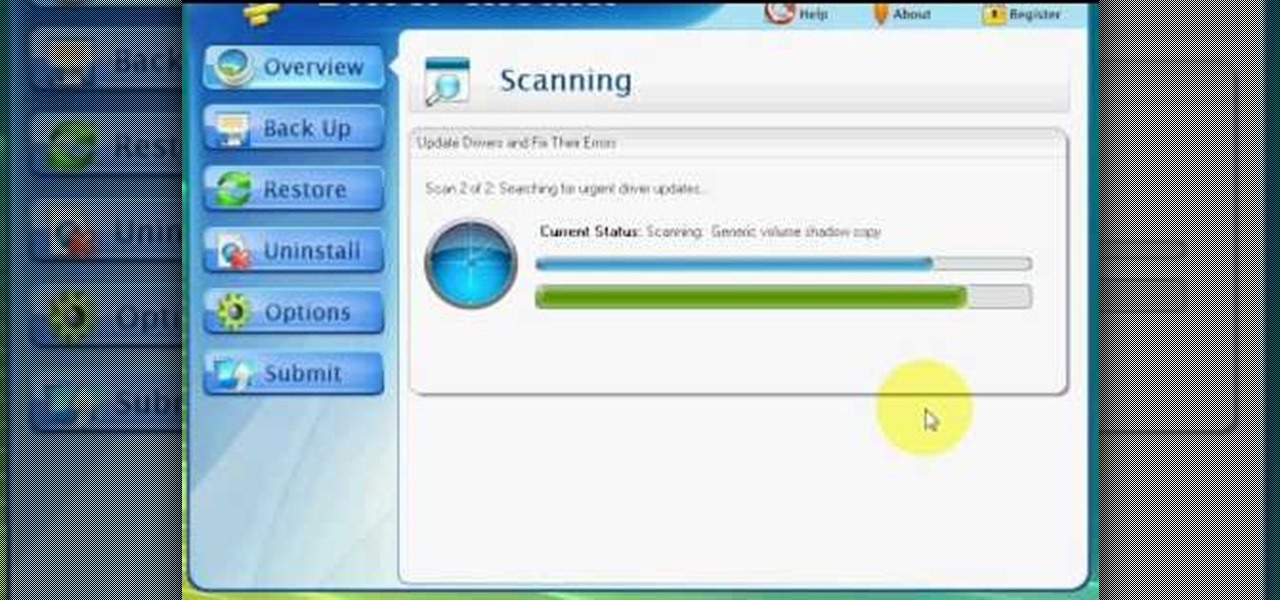
This video shows us the method to find and install Windows PC drivers. Install the software from www.DirectDriverChecker.com. Click on 'Start Scan' to list the drivers you have and which ones need an update. Choose 'All Drivers' to see all drivers and 'Outdated Drivers' to see the outdated ones. Check the drivers and click 'Next' to update them. Use the 'Back Up' option to back up the drivers in case of a malfunction in the computer. Use the 'Restore' feature to restore the saved drivers whic...
In this how-to video, you will learn how to update your iPhone or iPod touch to 3.1.2 firmware for free. First, make sure you have iTunes installed on your computer. Download the correct firmware for your specific model on the internet. Once this is download, open iTunes and select your device. Hold the shift key and click restore. Select the firmware file and open it. Hit the restore button in the new window. This will then update the device. This may take a while. Once it is done, the updat...

Have you ever dropped your iPhone or iPod in water? Learn how to fix it here. Water can be very damaging to electronics because of its conductivity. You can avoid short circuiting your device by following the directions in this tutorial. Discover why water can hurt your electronics and how to dry out a wet device from the inside out. Find out how to open the device and access the logic board. With materials as simple as a hair dryer and guitar pick, your device can be as good as new!

Cover brows with wax or glue stick and concealer that is a lot lighter than your skin). Place some of the much lighter concealer under your eyes. Stroke concealer all over face for an extra layer. Apply full coverage foundation. Set makeup with powder. Use something that'll look very fake when done. Add cream blush product in bronze shade. Apply with finger to warm it up; apply to cheeks, forehead & nose. Use mineral type skin highlighter all over face. Paint on eyebrows with black liquid eye...

Thanks to modern "smart phones" and the internet, media by the people, for the people is finally a reality. Here's how to use your phone to be a mobile journalist.

Check out this video tutorial to see how to tansfer blood specimens with the BD Blood Transfer Device.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

With the early launch of Google Stadia for cloud-based gaming, there was bound to be a slight learning curve for most people. Many didn't realize that the average TV is not suitable for gaming by default. This is why there is a separate game mode you must use when playing on the big screen. Luckily, your Chromecast Ultra can actually take care of this for you automatically.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Did Google CEO Sundar Pichai kill Google Glass for non-enterprise users? That's the obvious first question following news that non-enterprise Glass users will no longer have access to Google's core apps after February 2020.
Your phone is loaded with contacts you've collected over the years. They're an asset, and you should use your library of connections outside the confines of your mobile device. Luckily, your Pixel uses a standardized medium to store contacts that can be used by the likes of LinkedIn, Outlook, Hubspot, iCloud, and more.
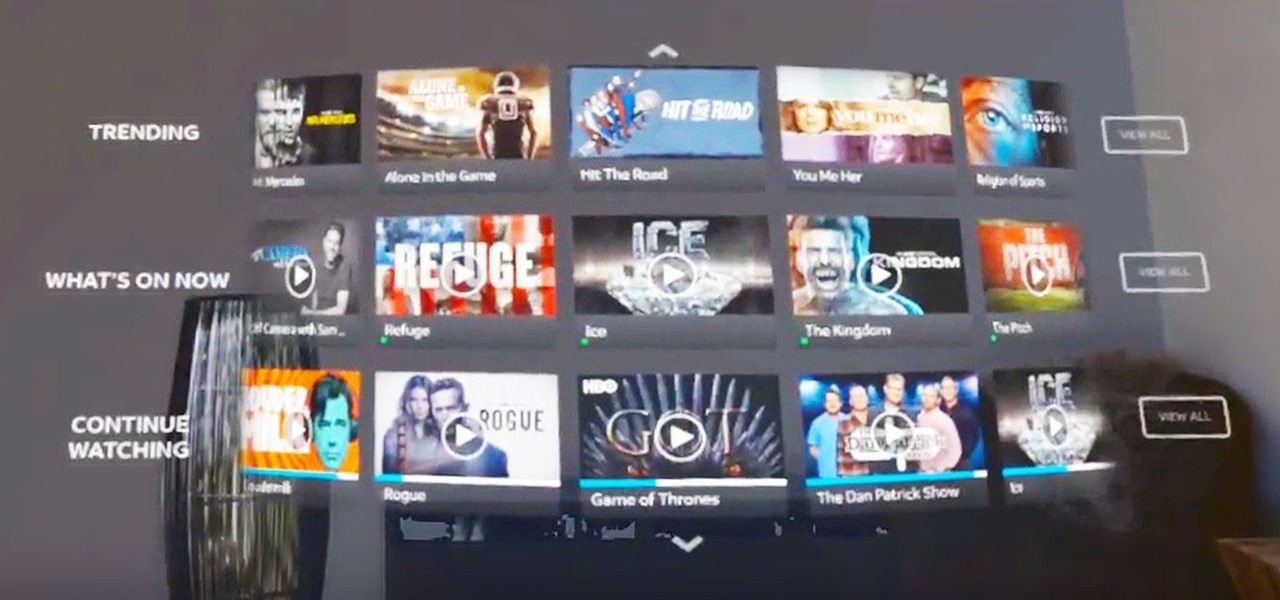
The streaming content vision from Magic Leap recently underwent a quiet but major update, courtesy of AT&T.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

In this era of smartphones, we all know very well how easily we can get addicted to our devices. Spending hours each day doing the endless scroll through Facebook and other social media sites just because we feel like we'll miss something if we don't. Both Google and Apple are aware of this and are trying to help control smartphone addition in their own way for Android and iOS.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

If you're an Apple fan, AirPods are the must-have wireless headphones to own. They know when they're in your ears, will pause music when one is taken out, and when you pair them with your iPhone they'll already work on your Mac, iPad, and iPod touch using the same Apple ID. However, whenever you use them on any other device, you have to manually reconnect them later to your iPhone.

Returning to the spotlight after its debut at last year's CES, augmented reality smartglasses maker Rokid is back with a new update.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.
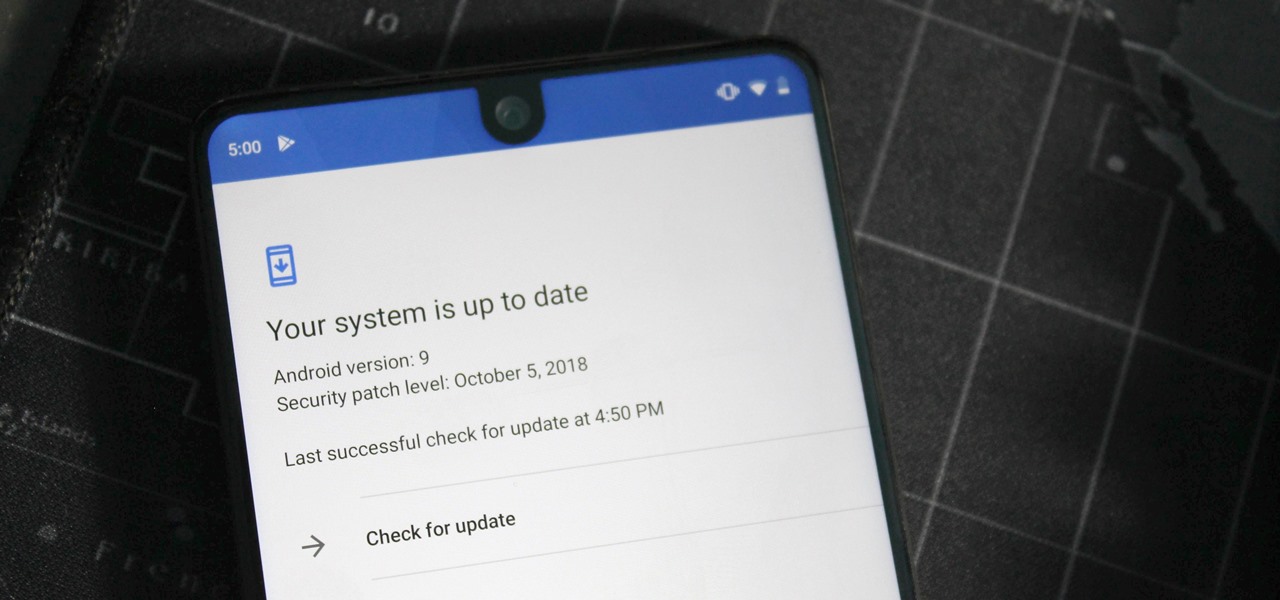
One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.