The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

With barely a whisper of augmented reality during the first day of its developer's conference, Samsung came out swinging on day two with the introduction of its version of the AR cloud and a partnership with Wacom that turns Samsung's S-Pen into an augmented reality magic wand.

Who doesn't love a refresh? Samsung's upcoming One UI makes it easier to use your device with one hand and adds a fresh coat of paint to the formally "Samsung Experience" skin. While you're probably looking forward to installing One UI on your phone, not all Galaxies are equal — your device could be one of the first to receive the update, or it could never see One UI at all.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Although the Magic Leap One: Creators Edition is currently officially available in only six US cities, those living outside of Magic Leap's designed US cities now have a roundabout way to order the device.

In recent days, I've twice talked about brining the Magic Leap One out into the world with me to test its mobile capabilities. But you may have been wondering how I carried the device with me. Did I just stuff my brand new $2,300, hard to obtain device in a backpack and hit the road? Hardly.

Time to play — Fortnite is now officially available on Android. However, the game won't be available across the Android ecosystem right away. Fortnite Battle Royale launches on Samsung devices first. That means if you have a Galaxy S7, S8, S9, Note 8, Tab 3, or Tab 4, you can download the game right now.

Google's Pixel smartphone had a decent head start as one of the first devices to offer ARCore, but that early exclusivity has been frustrating for some Android device owners. Some of that frustration was relieved when Google added more Android devices to the ARCore list in February.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Earlier this year, with the Developer Preview, we got a tantalizing glimpse of Google's upcoming Android 9.0 Pie and a whole slew of new features that comes along with it, such as iPhone X-like gestures and improved security features, to name a few. With its announcement at Google I/O, Android Pie just got a lot more accessible.

With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

No smartphone is immune to software issues, even one as advanced as the Galaxy S9 and S9+. Bugs can be caused by a multitude of issues, such as third-party apps that just refuse to play well with your device's OS. Thankfully, there's a simple way for you to check if your S9's bugs are due to uncooperative apps.

The fourth beta for iOS 11.3 was released by Apple to developers and public beta testers on Monday, March 5. The update comes just under two weeks after the company released beta 3 on Feb. 20, which mostly added bug and stability patches. It appears that beta 4 is much of the same, but we'll learn more as we sink our teeth into it.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

One thing that makes Apple great is the connectivity between its products. Many tasks you do on an iPhone can be switched over to a Mac or iPad quickly and easily. The Notes app is no exception to this advantage, but you need to make sure you're set up so that your notes sync properly on each device you have.

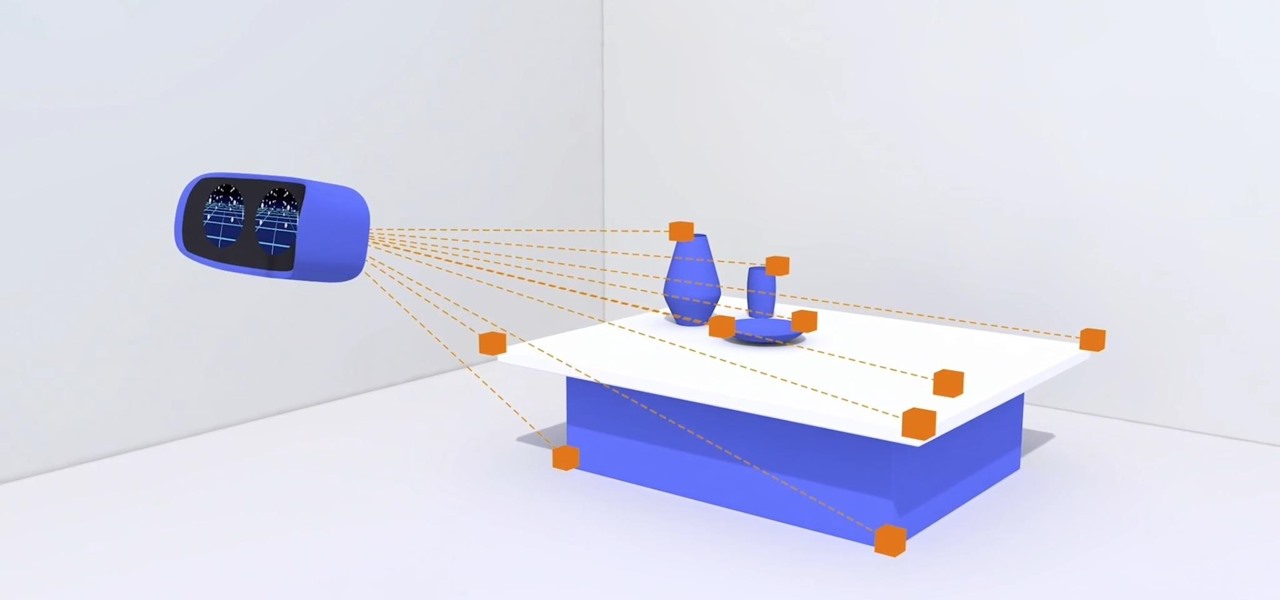
Digital imaging company OmniVision Technologies and the Hong Kong Applied Science and Technology Research Institute Company Limited (ASTRI) entered the CES fray this week with a new reference design for an augmented reality headset capable of 60 degrees field of view (FoV).

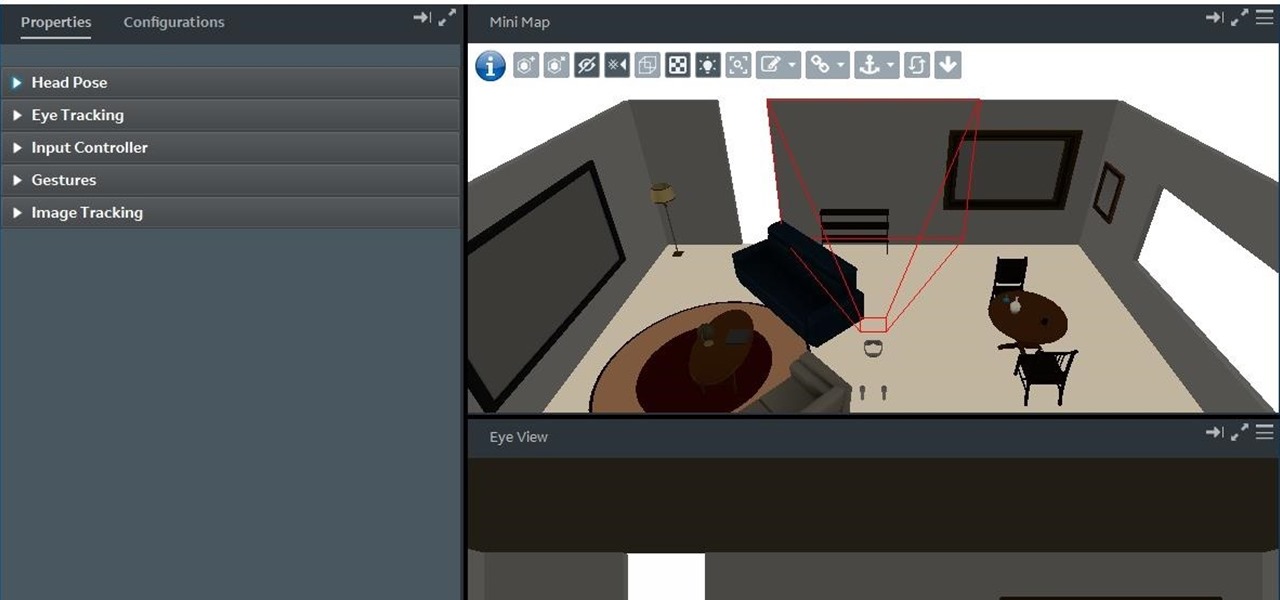
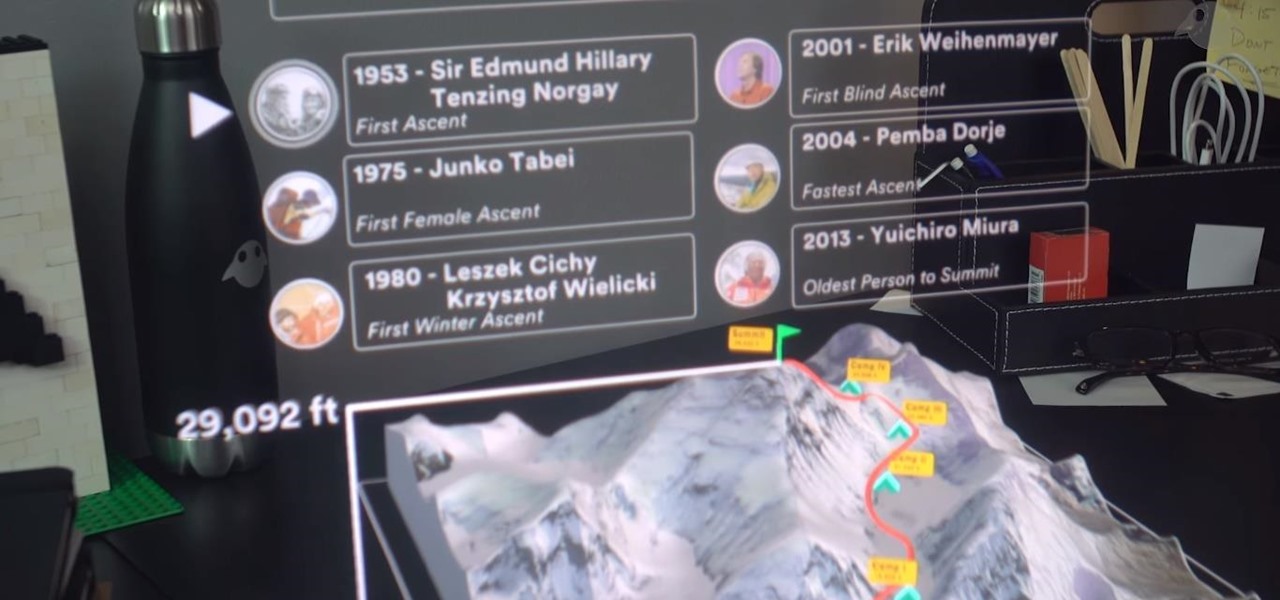
Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

So you're thinking about downloading the Galaxy S8 Oreo beta, but you're not sure if it's stable enough to use. It is a beta, of course, so you might want to wait for others to give it a try. Over the past ten days I've used the Galaxy S8+ running Android Oreo as my daily driver, running down the best new features. Let's take a look at the bugs, the performance, and the battery life.

As expected, Magic Leap closed a Series D round of equity funding, raising $502 million from new and existing investors. Less expected, however, were a fresh set of rumors that the company's first devices could ship within six months.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

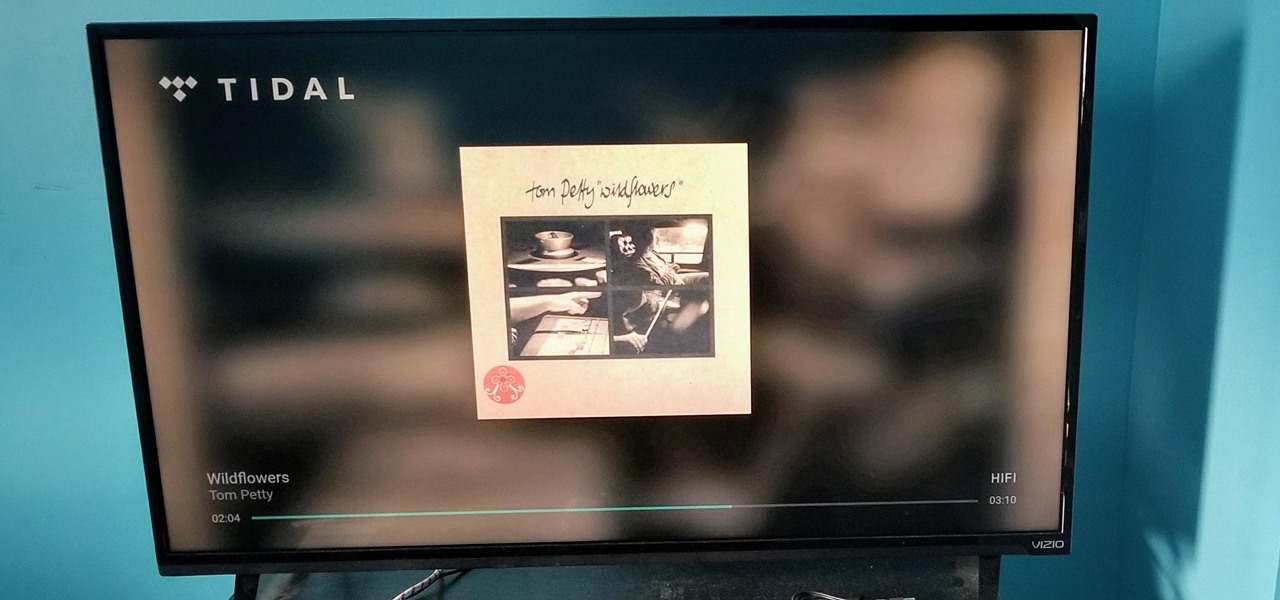
With so many Chromecast-powered devices available, chances are, you're near something with casting abilities right now. Whether it's Android TV, Google Home, or any one of the various gadgets with Chromecast built-in, you can use a more powerful speaker to play media from your smartphone. The only caveat is that the app you're streaming from needs to support Google Cast, but thankfully, Tidal does.

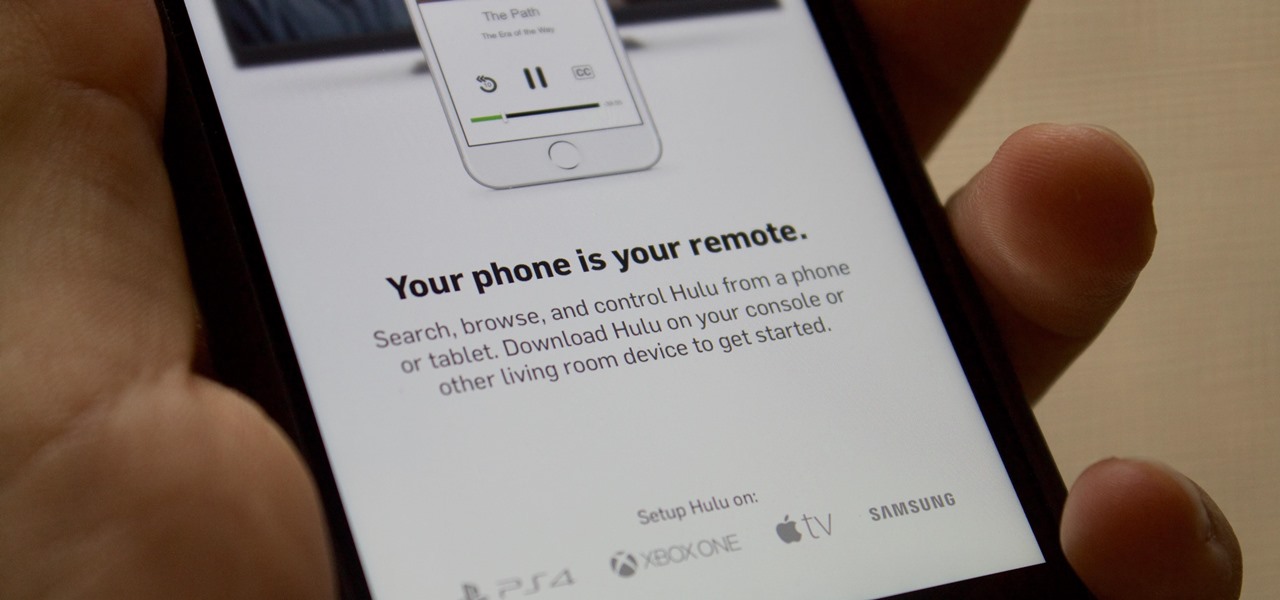
Your smartphone is the perfect place to watch Hulu on the go. Whether you're looking to catch up on your shows in a hotel, or your phone is the only screen available, mobile streaming can be a lifesaver. But what about when you have access to a TV? Wouldn't you rather watch your favorite Hulu Original on the big screen than on your comparatively tiny smartphone?

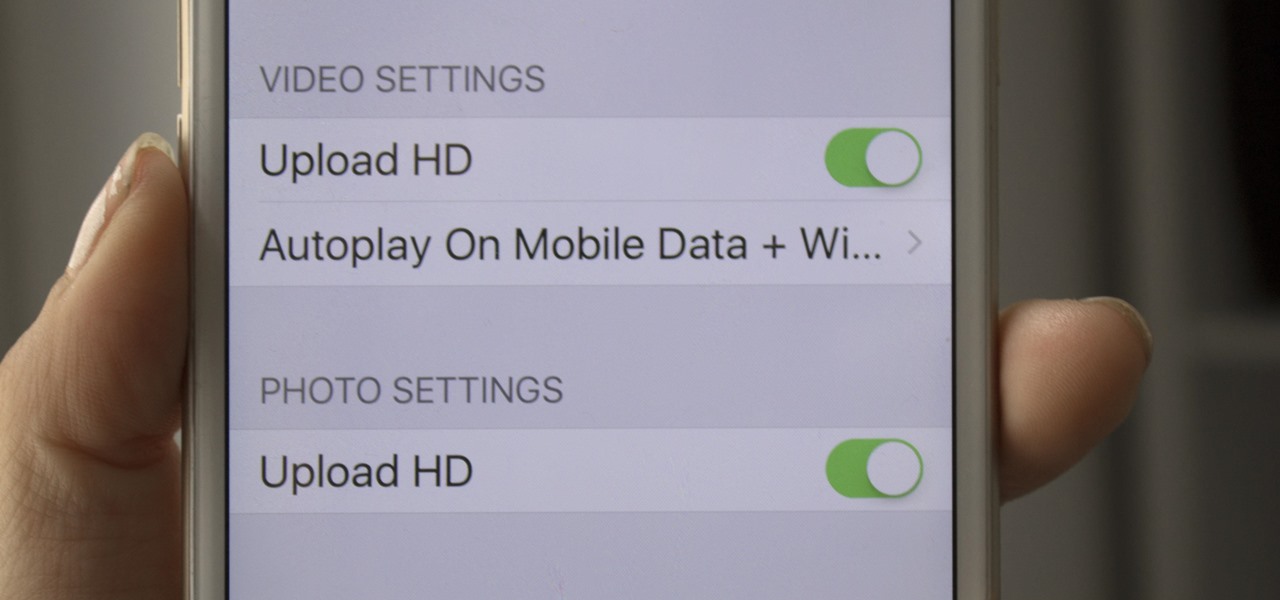
If you are a frequent poster on Facebook, then uploading your photos and videos in HD is essential for your viewers. There's nothing worse than realizing that the Boomerang you just uploaded is grainy and probably won't get any views.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Update 6/15: Netflix responded to our request for comment: This [download limit] may vary depending on the title and licensing agreement. There may be limits to the number of titles from the same licensing agreement that you can download at the same time. We will only enforce these limits in cases where our licensing agreements require us to do so.

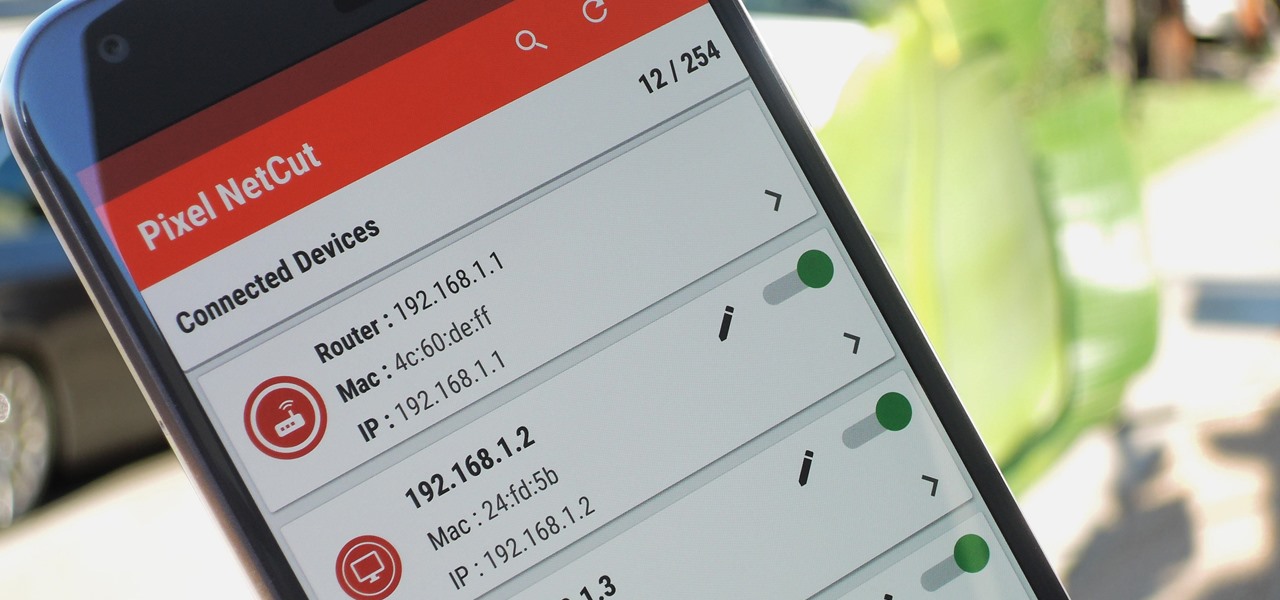
It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.

Google announced several new devices (as well as updates to existing devices) that will take advantage of the company's augmented and virtual reality platforms.

If you're a parent of a toddler (or have a friend that acts like a toddler), you occasionally need to take a break just to preserve your mental health. The perfect way to buy yourself some "me time" in this scenario would be to pull up an episode of Dora the Explorer on Netflix or YouTube, then hand your phone or tablet over to your child (or child-like friend) and try your best to relax while they're occupied.

Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

Several Samsung phones have a feature that turns the screen black and white when the battery is getting low. This takes advantage of the AMOLED display in these devices, because unlike red, green, and blue pixels, no battery power is used to display black pixels on this type of screen.

Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

If you're running iOS 10 or lower, there is no built-in way to make a screen recording on an iPad, iPhone, or iPod touch directly from the device, but that doesn't mean there isn't a way to record your screen at all.