Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

For those not used to it, working from home can be a difficult transition. Everything around you can be a distraction, and distance from your boss and coworkers means less pressure and incentive to get things done. So it's not surprising to see a major drop in productivity during a period of self-quarantine, but your phone can help you stay on track instead of sidetracking you.
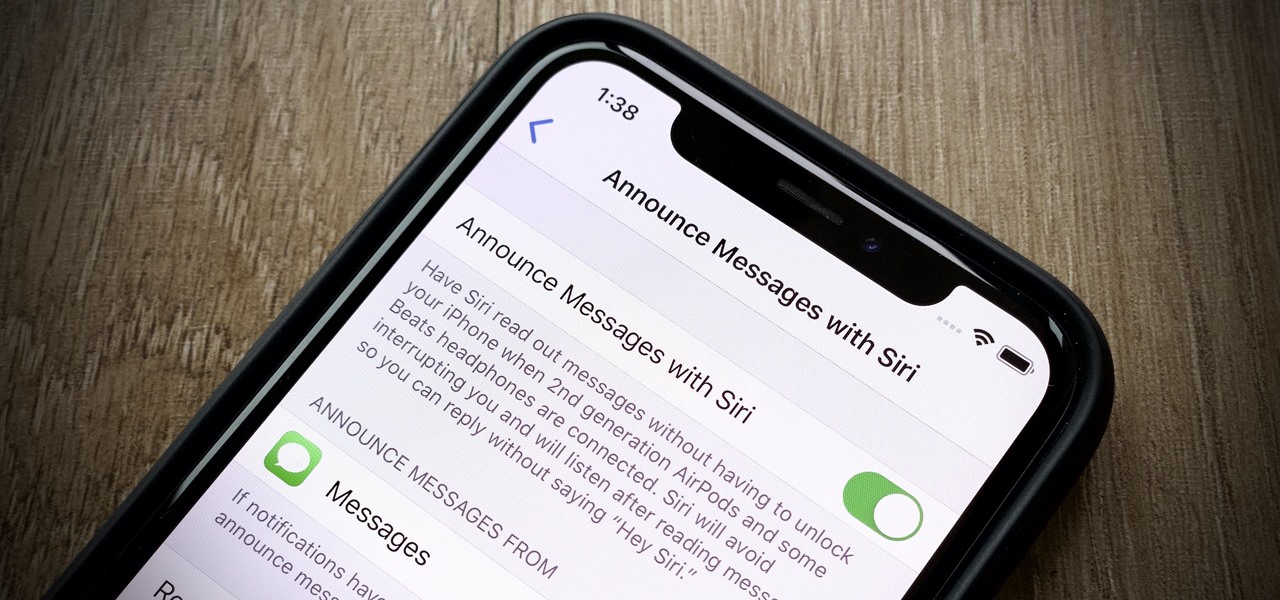
Apple's iOS 13 has been quite the disrupter. The initial update featured over 200 new features and changes, while its successor, iOS 13.1, brought another 22 to the mix. With the company's latest update, iOS 13.2, you'll see an extra 22 amendments on your iPhone, including new emojis, Deep Fusion on iPhone 11, 11 Pro, and 11 Pro Max, and Announce Messages with Siri, just to name a few.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

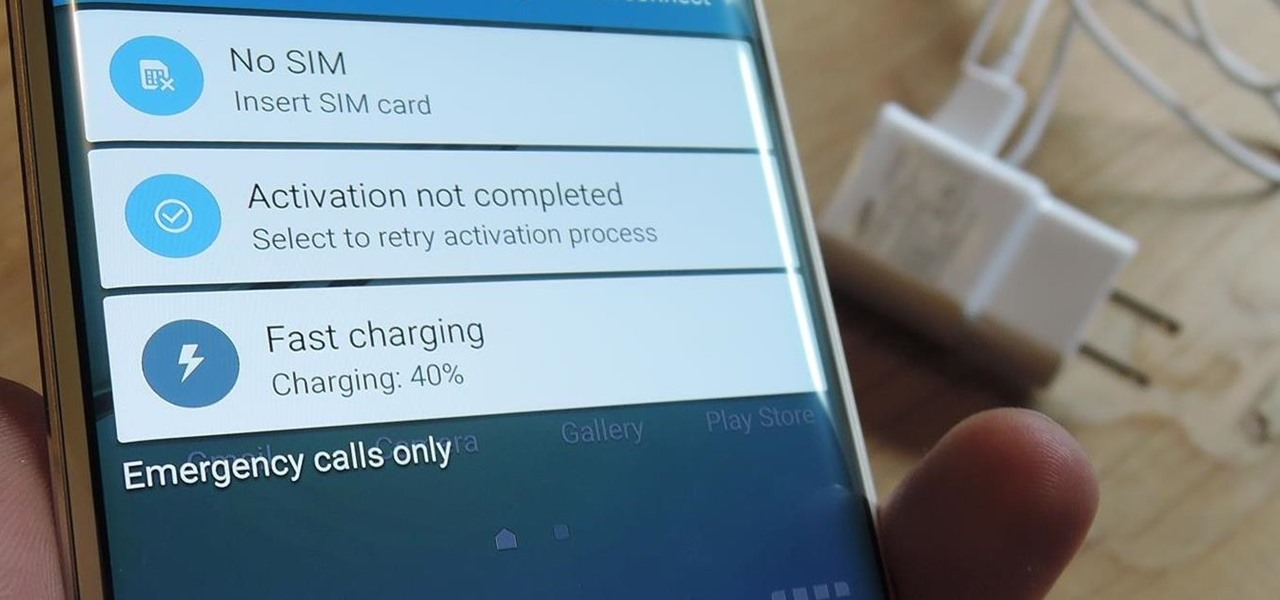
So, you want to install the Oreo beta on your Galaxy Note 8 but you're not sure if it's stable enough. It is a beta, of course, so waiting until others have tried it out sounds safer. Well, over the past five days, I've used the T-Mobile version as my daily driver and there are a plethora of new features, as well as a few glitches. Let's take a look at the bugs, performance, and battery life.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Malaria is a massive worldwide health problem. The Centers for Disease Control and Prevention estimate that 212 million cases of malaria occurred worldwide in 2015 and 429,000 of the infected people died.

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

While Lyme disease can be disabling, the wrong treatment for the infection can be fatal.

Citrus greening disease — caused by a bacteria spread by psyllid insects — is threatening to wipe out Florida's citrus crop. Researchers have identified a small protein found in a second bacteria living in the insects that helps bacteria causing citrus greening disease survive and spread. They believe the discovery could result in a spray that could potentially help save the trees from the bacterial invasion.

Even though the Ebola virus was discovered as recently as 1976, over 30,000 people have been infected since, and half have died a horrible death. Since there's no way to cure the infection, the world desperately needs a way to prevent it — and the five similar viruses in its family, the ebolaviruses.

It hasn't even been eight years since Candida auris was discovered—cultured and identified from the ear canal of a patient in Japan—and now it's drug-resistant, setting up residence in hospitals, killing patients, and wreaking havoc across the globe.

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

I used to brag that I could make a swan out of an apple, but chicks don't dig swans—they dig roses. So now I'm going to brag about making apple roses, because you would, too, if you could get them to look like this: Now that's an apple tart that will win the ladies over. (And definitely 100% tastier than the usual bouquet of roses, and 100% less greasy than a bouquet of bacon.)

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

I was bored when I found this piece of literature: ==Phrack Inc.==

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

From our work life to our home life, we have an awful lot of projects, tasks, and activities that require more productivity than play. After working for an entire day in the office, no one wants to face even more that needs to be done at home.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

I picked up my Galaxy S6 Edge on release day and have loved it ever since. Did I spend an extra hundred bucks for the mostly-aesthetic Edge display? Yup! Did I have buyer's remorse about my frivolous spending? Not even a little.

Super Bowl Sunday is just around the corner. With 111.5 million viewers tuning in last year (112.6 if you count streaming), which broke another record that it previously set for the most-watched television event in U.S. history, it's safe to say that most of us will be watching Super Bowl XLIX on February 1st, 2015, whether via TV, web, or mobile.

Lasagna, that layered, creamy baked pasta dish, is a lovely comfort food that's great for a crowd. But if you've ever made it, then you know you're usually left with some leftover lasagna noodles. (Although that's always better than the frustration of running out of the noodles while you're still making a traditional lasagna.) Still, what do you do when you're still left with a bowlful of the wide ribbons?

A little cooking mistake can lead to tough meat, spoiled food, and even a bacterial explosion in your kitchen if you're not careful. These five simple, easy-to-fix kitchen mistakes are some of the most commonly made in households around the world. Luckily, you can correct these innocent errors with just a few minor tweaks.

If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home.

Phantom phone vibrations. You might feel them in the pocket of your jeans, or when your handbag is on your shoulder—even when you're holding your phone in your hand. When you do, you immediately wake it up to see who texted or what app just had an update—but there are no alerts.

You've been there. Those precarious few seconds between dropping your expensive smartphone right on its face and reaching down to survey the damage. Or maybe you got thrown in a pool while your device was in your pocket, or you dropped that sucker right into the toilet bowl. Heck, I've managed to accidentally wash two devices by leaving them in my pants pocket when throwing in a load of laundry.

Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Sugru is some pretty versatile stuff. The company's slogan is "Hack things better," and for good reason. It sticks to aluminum, steel, ceramics, glass and plastics, it's waterproof and heat-resistant, and it can be molded into any shape you can imagine. Anything from your kitchen cabinets to your bicycle can be improved with some Sugru and a little creativity, and gadgets are no exception. Here are 10 of the coolest hacks to fix or upgrade your smartphone, tablet, or camera.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

Need to remove wrinkles from your shirt but don't want to bust out the iron and ironing board (or don't even have one)? Well, with a little bit of do-it-yourself ingenuity, you can "iron out" that wrinkly top in no time.

Prepaid phones are becoming more and more popular, and tons of people can see the benefits of switching now that some companies are offering prepaid services that are on par with the big players. For a lot of folks, the only thing keeping them from switching is the huge early termination fees that service providers charge to break a contract early.

When a phone has only one main button, it can be pretty frustrating when that one button doesn't really work anymore. If you have an iPhone 4 or 4S, you know exactly what I'm talking about. Yep, the Home button, which is prone to unresponsiveness and lag. Most users blame the Home button issues on either dirt, moisture, or misalignment. No matter what the reason, having a busted Home button sucks, especially for those of you no longer under warranty. But that's okay, because there are a few t...