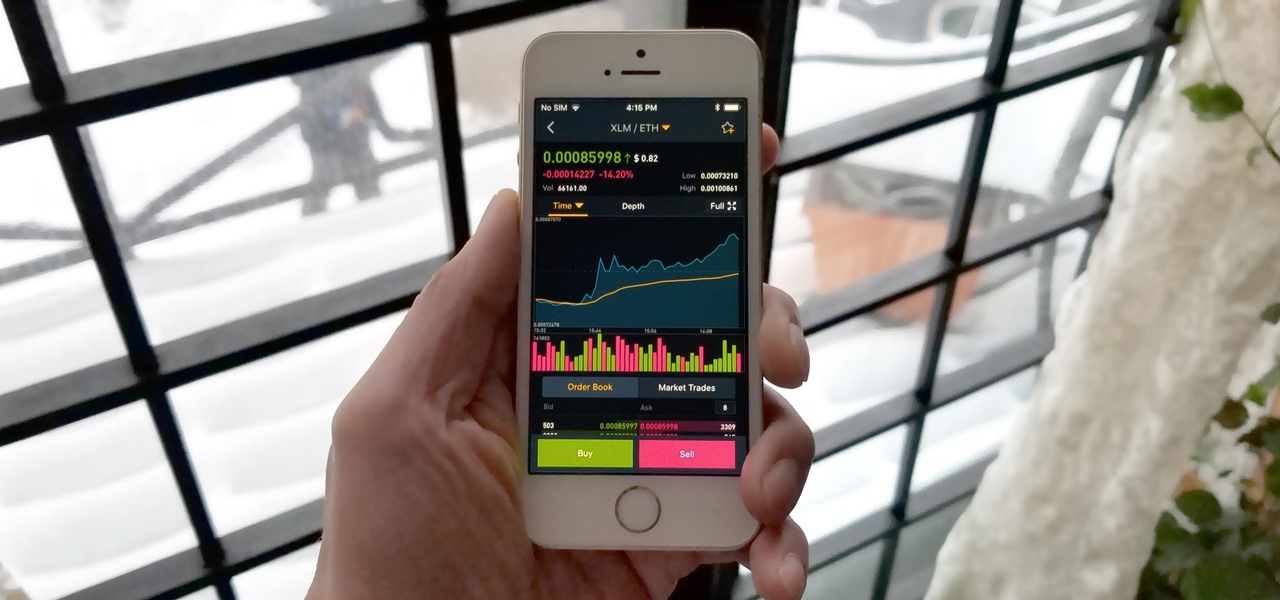
Binance, a China-based cryptocurrency exchange, is rapidly gaining popularity thanks to the sheer selection of digital currencies you can purchase — Ripple (XRP), Tron (TRX), IOTA, and Stellar (XLM), to name a few — using both Bitcoin (BTC) and Ethereum (ETH). Binance has an iOS app, and there are a couple ways to install it. Either way, you can trade cryptocurrency from your iPhone today.

Coinbase sets itself apart from other wallet apps by making cryptocurrency transactions incredibly convenient. You can easily withdraw cash from the app and deposit it into your bank account within days — and now, if you want to cut the time from days to mere minutes, Coinbase has you covered as well.

Thanks to Metaverse, it has never been this easy to create your own AR game.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

Update 10/14: Developer paphonb has added rootless Google Now integration to the leaked Pixel 2 launcher, so now, anyone running Android Nougat or Oreo can get the full Pixel 2 home screen experience. For those running Lollipop or Marshmallow, we've left the unaltered leaked version linked out below, but we've added a new link for the tweaked version with Google Now integration.
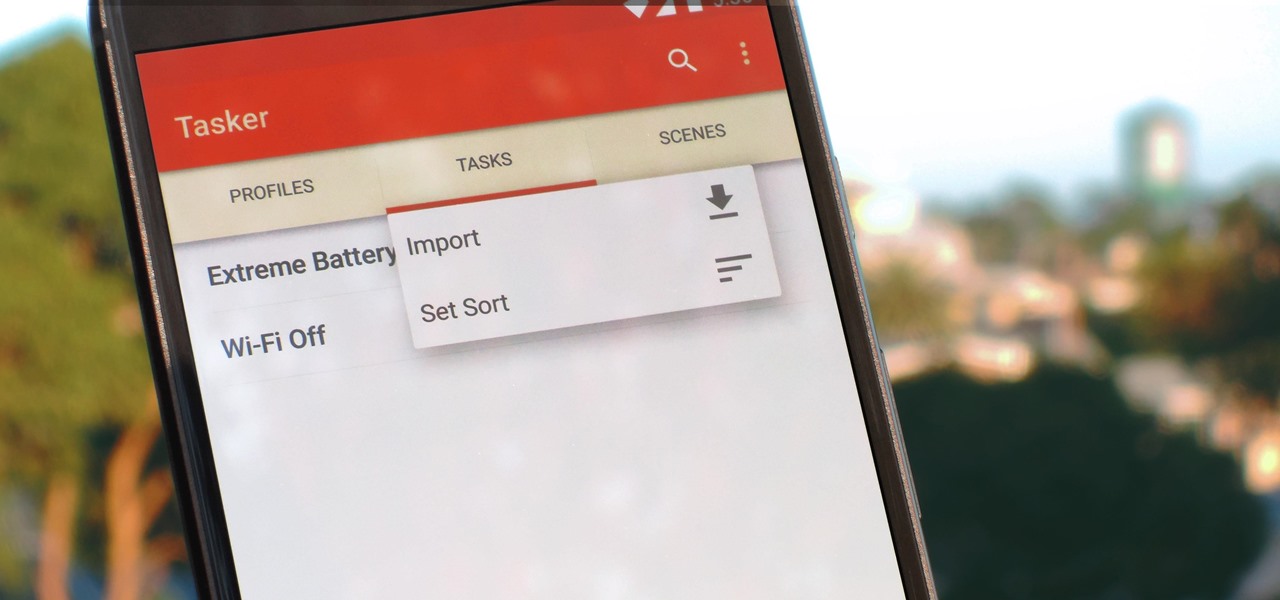
Regardless of what you're trying to accomplish with Tasker, there's a good chance that someone else has already walked through the same steps. If you're unfamiliar with creating tasks and working with profiles, simply importing someone else's work would be a great shortcut. After all, there are 2 billion Android devices out there, so someone must've created a setup that suits your needs, right?

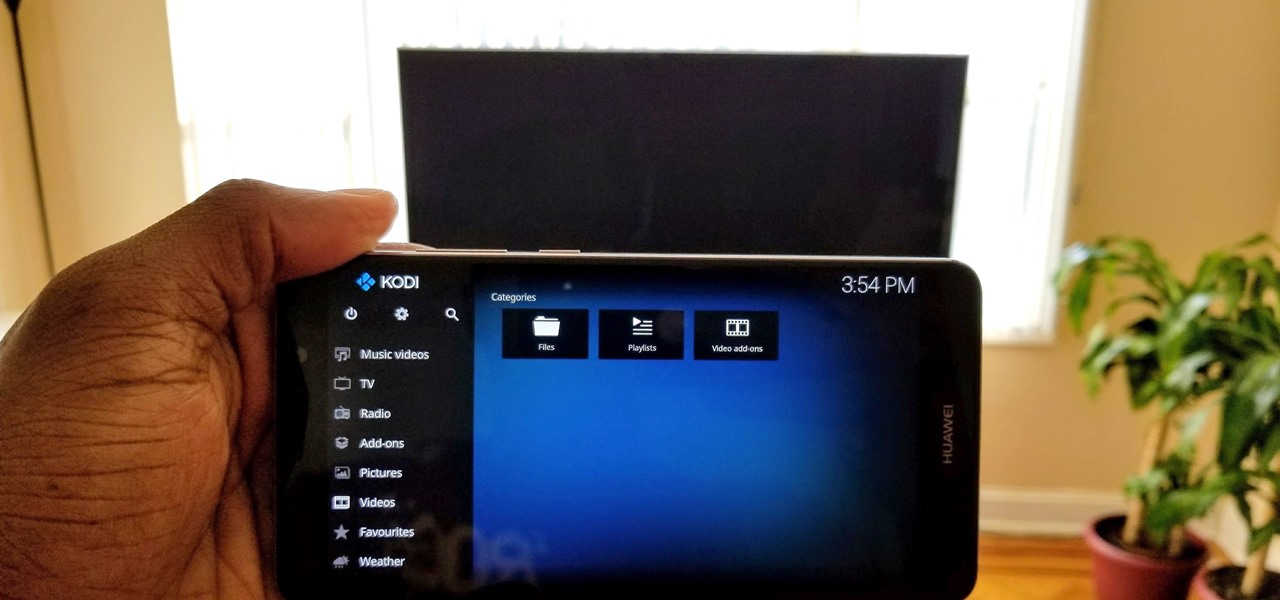
Over the years, Kodi (formerly XBMC) has become one of the most popular media players. It provides all the essential functionality needed for any home theater setup while remaining open source and free. However, Kodi is not limited to just your living room. With the Kodi app for iOS or Android, you get a streaming media player that can act as a video player, music player, picture gallery, and so much more.

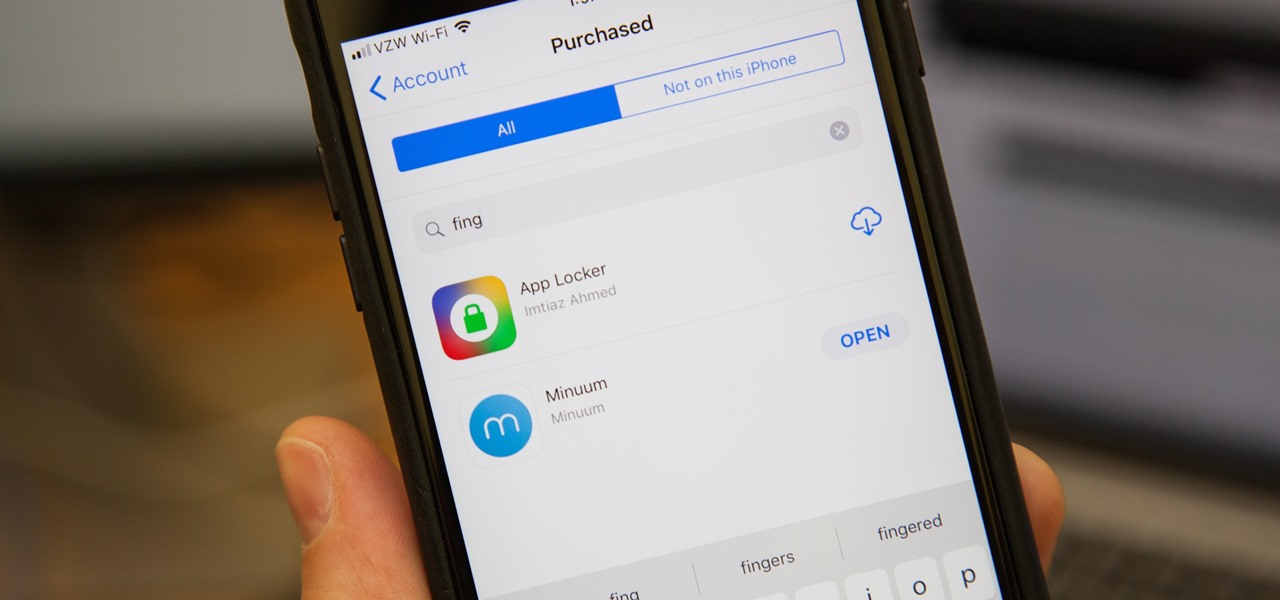
In the new iOS 11, Apple lets you hide purchased apps from the App Store no matter if you have "Family Sharing" turned on or not, which is an interesting change from iOS 10. It's a fairly easy task to hide an app from your list of purchases, but unhiding it is anything but easy.

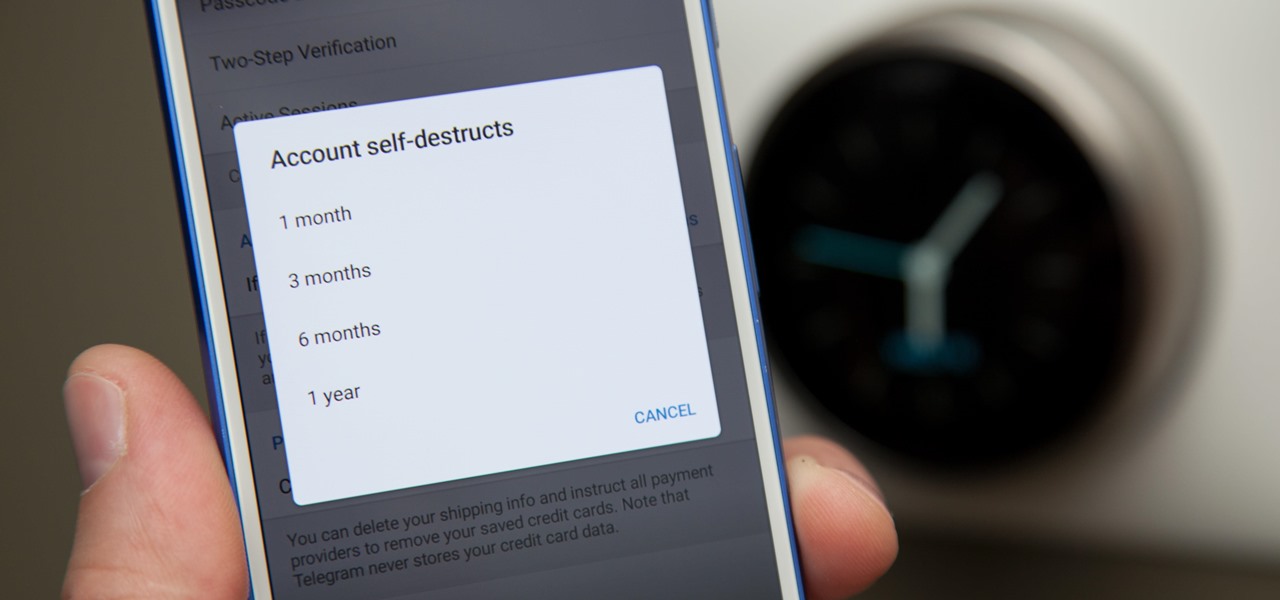
You can send self-destructing messages in Secret Chats, but that's not the only thing that can destroy itself in Telegram after a specified amount of time. Your whole account can disappear after a certain amount of inactivity, so it's important to adjust these settings to give you more time or to kill your account even quicker.

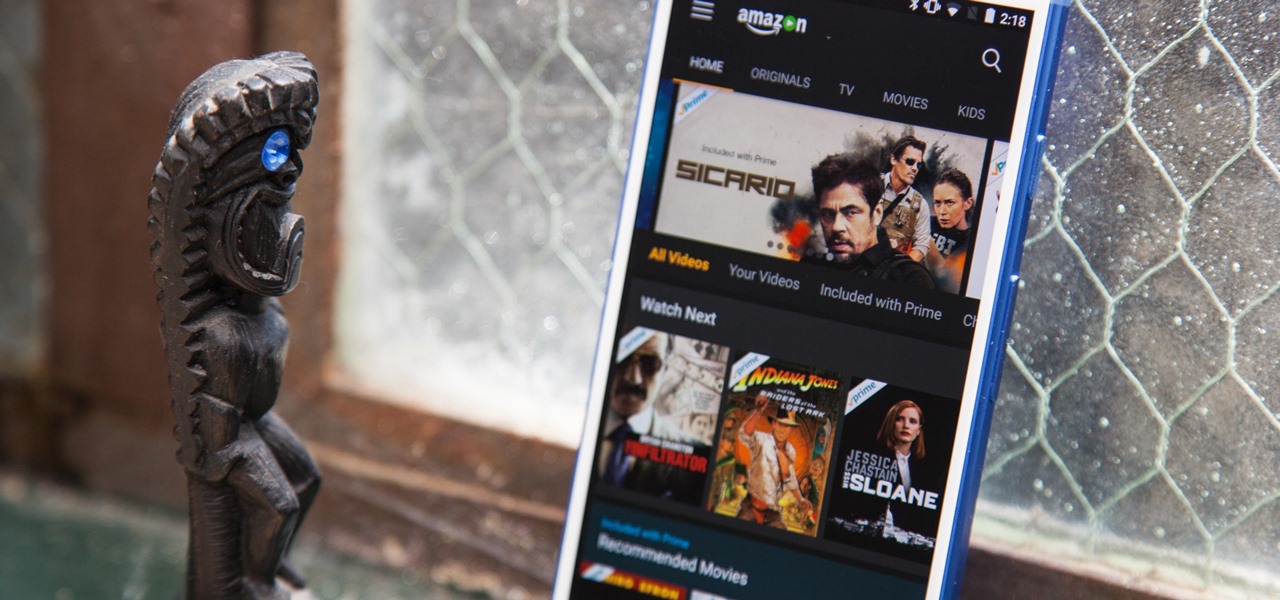
When it comes to watching movies and TV shows in Amazon's Prime Video service on an iPhone, it's as simple as installing the Amazon Prime Video app, signing into it, then playing content. However, on an Android phone, it's a lot more complicated.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

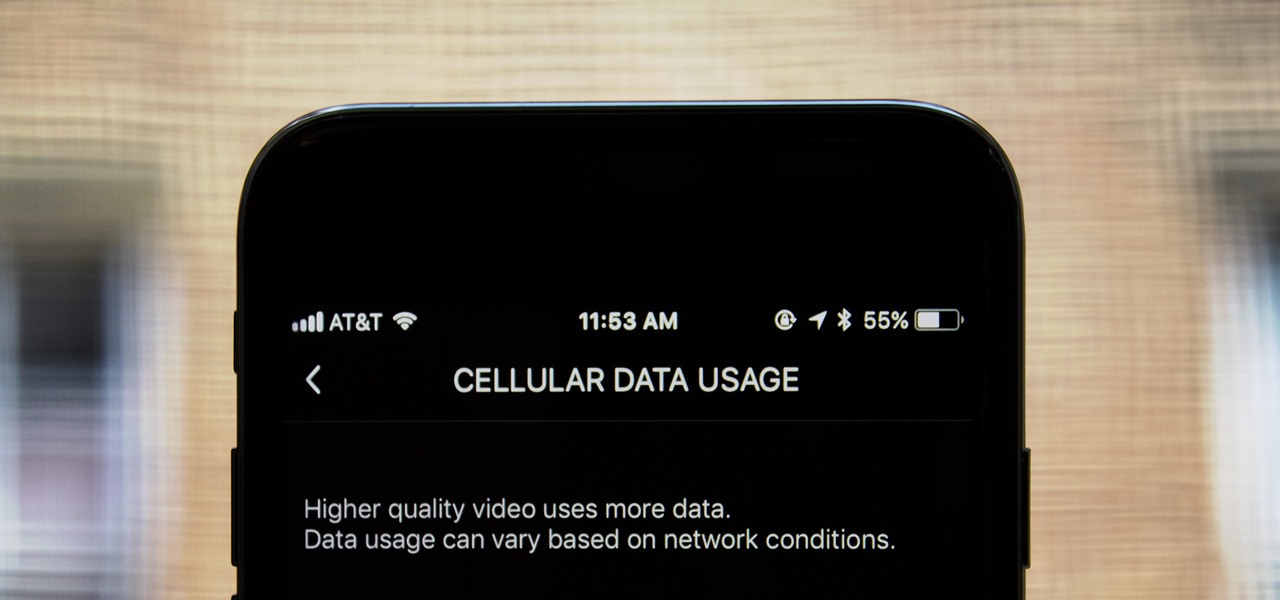
If you don't have any home Wi-Fi, like to watch videos on public transportation, or just always find yourself streaming Netflix when there are no hotspots available, your cellular data is probably gobbled up fairly fast. For limited data plans, watching the next episode of your favorite TV show could mean overage charges on your cellular bill, but it doesn't have to.

There is an Indian story called the Legend of Paal Paysam, and while it doesn't seem like it at first, it has a lot to say about what motivated Paul Travers in the augmented reality space.

Google has an exclusive launcher for its Pixel devices, and it's pretty slick. But even though we've found ways to get this home screen app on other phones, certain features simply wouldn't work unless you were rooted. That's finally changed.

Carrier-branded Galaxy S8 models come with a ton of bloatware that you usually can't get rid of without rooting. If you dig a little deeper, however, there is a way to debloat your S8, and it's relatively hassle-free.

Augmented reality is quickly becoming a popular tool for marketing use cases, as demonstrated by new projects serving the automotive, entertainment, and tourism industries this past week.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

The Galaxy S8 and S8+ haven't even hit shelves yet, but some of the stock apps from Samsung's latest flagships have already been leaked. The biggest one so far is the new Samsung Experience Launcher, which replaces TouchWiz Home, and is quite a bit different from anything you'll find on previous Galaxy models.

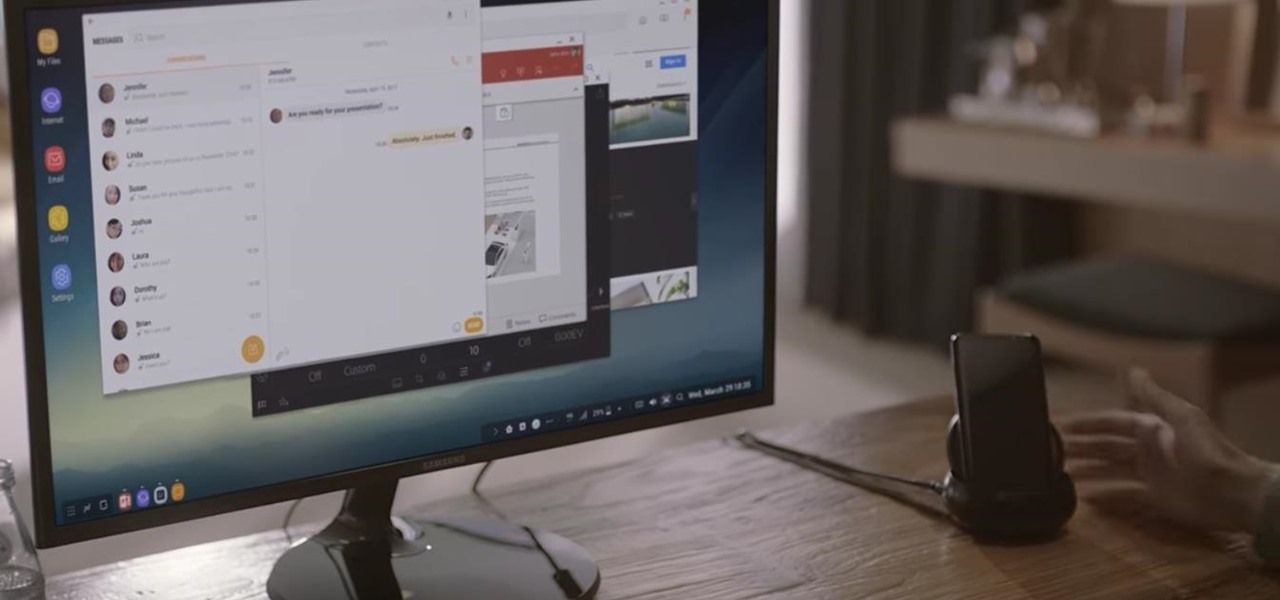
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

The LG V20 went on sale on September 29, 2016, and is the second flagship phone in the V series to be released by LG. Both the V20 and its predecessor, the V10, have been audio-oriented phones from the start, but the V20 has a much nicer Hi-Fi Quad 32-Bit DAC, which makes the output audio from the 3.5 mm headphone jack sound amazing. It's loud, it's crisp, it's full, and everything from the higher frequencies to the lower ones can be heard.

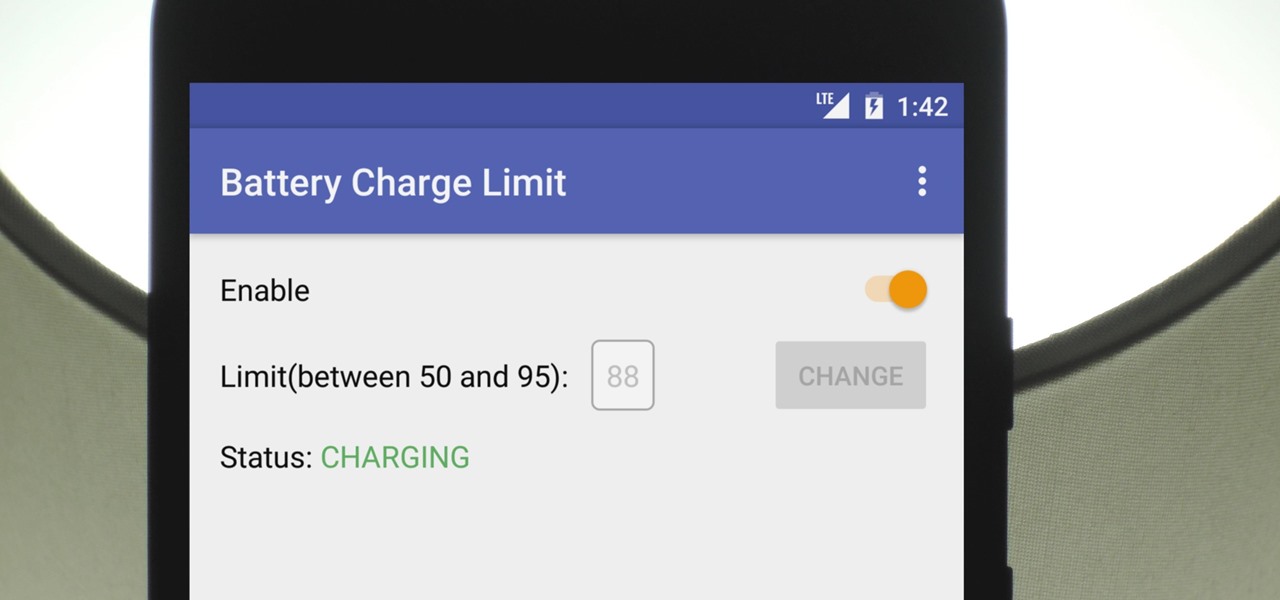
There's a lot of conflicting information out there when it comes to the best habits for charging a smartphone's battery, so let's clear some of that up right off the bat. Lithium ion batteries (the type used in most modern electronics) start to lose their ability to hold a charge over time, and the two biggest factors that contribute to this are excess heat and overcharging.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

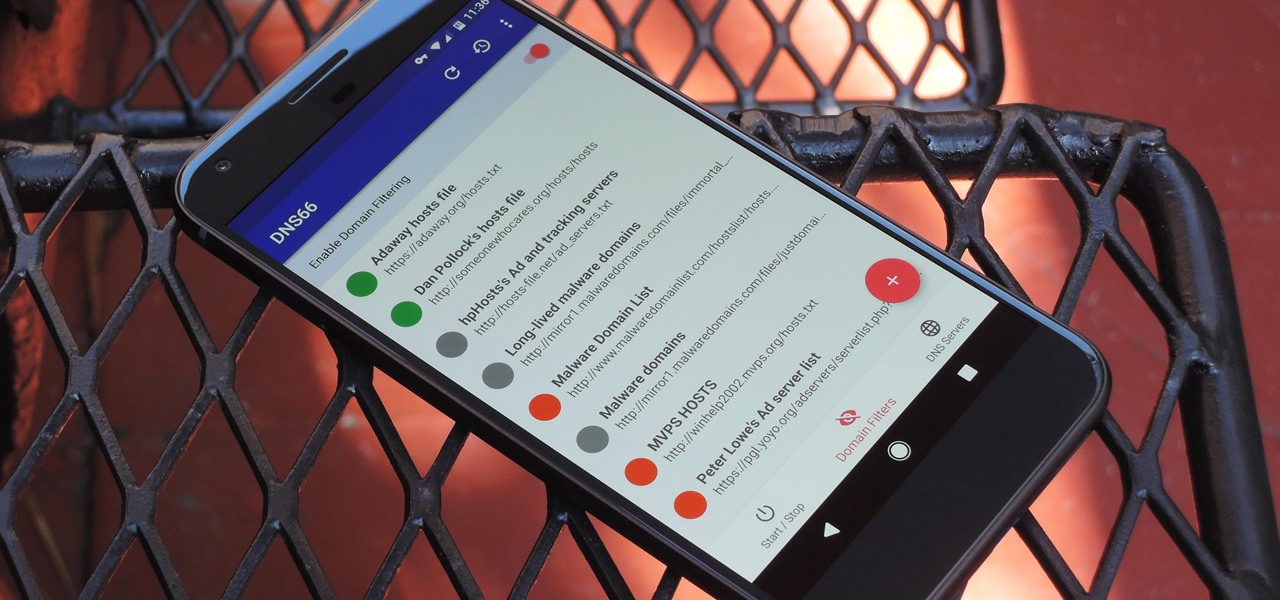
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?

Virtual reality holds the promise of electronically visiting distant places we'd otherwise struggle to reach, but that teleportation-esque ability isn't possible without the right content. YouVisit created a platform that makes it easy for almost anyone to create immersive 360-degree experiences so we can map our lives and see the world through the eyes of our fellow humans.

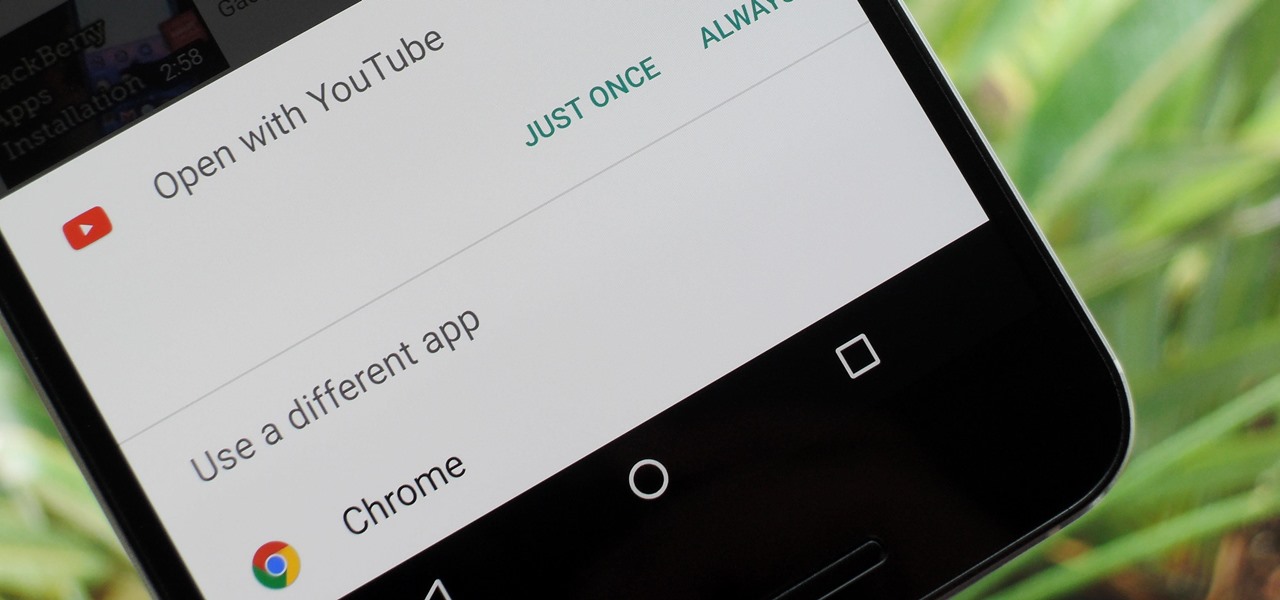
One of Android's biggest strengths relative to iOS is the fact that you can use any app to open compatible links, not just the stock ones that come preloaded on your device. When you tap a link that two or more of your apps are capable of opening, you'll see a message asking which app to launch it with—and from there, the choices are "Just Once" or "Always."

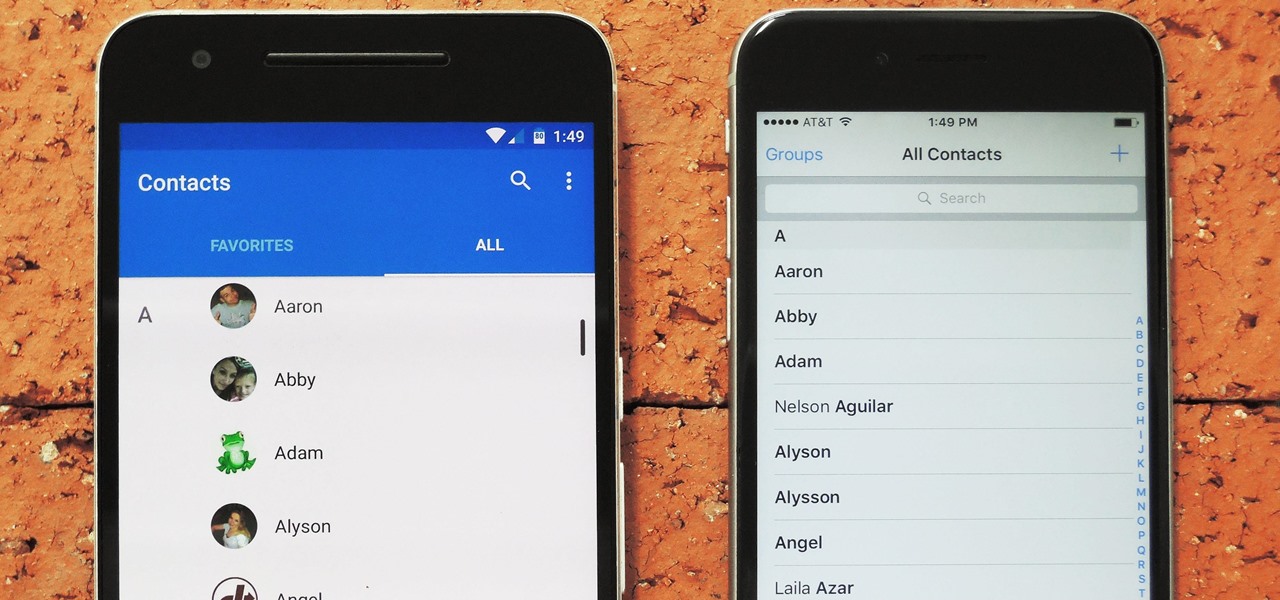
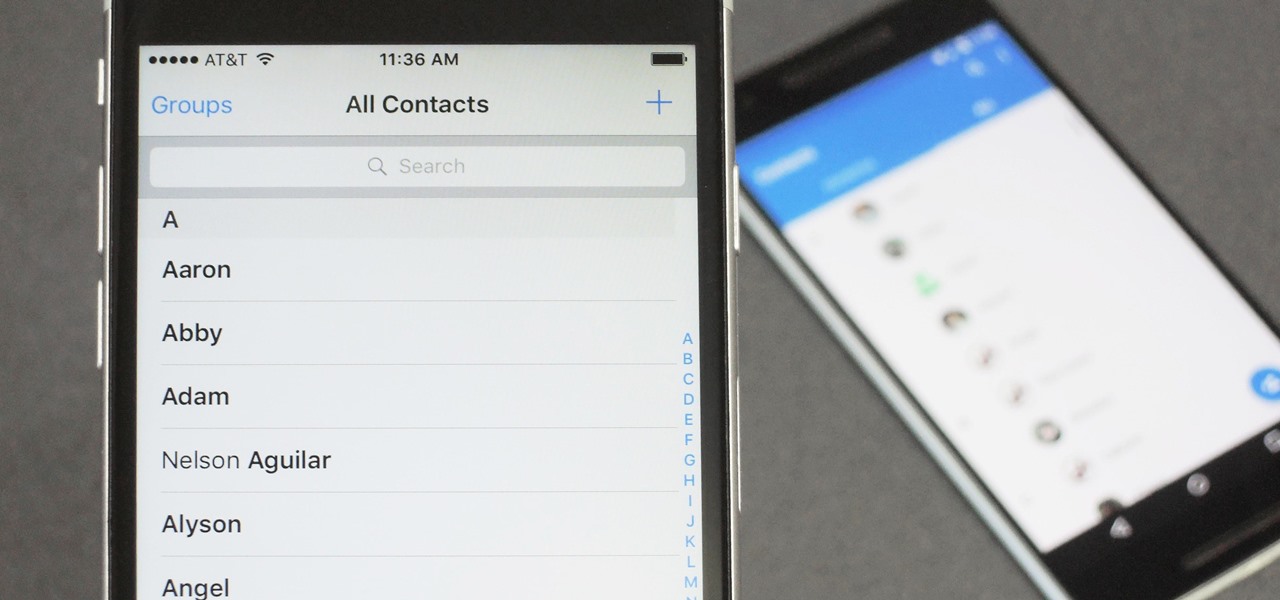
Switching between mobile operating systems is fairly easy, but there are a few bumps along the way that you're bound to encounter. One of the first issues you'll run into is that the contacts on your old iPhone don't easily sync with your new Android device.

When you change smartphone ecosystems, there are a lot of minor hurdles to clear along the way. It's definitely not hard to switch from Android to iOS, but little things like making sure your contacts get transferred over can take a bit of work.

Imagine if you combined Tasker with your favorite live wallpaper—that's roughly the gist of a new app from developer feedK. With this one installed, your home screen background will finally be aware of its surroundings.

For the most part, when you take a screenshot, it's because you intend on sharing it with someone. And, of course, we all take pride in our smartphones, so we want to show them off as much as possible. But the downside here is that regular screenshots are pretty boring, so they don't do a great job of showing anything off, really.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Out of nowhere, Google released a preview build of the upcoming Android N release back in March—a full two months early. As if that weren't enough excitement for one day, they topped themselves by following up that announcement with the debut of a new "Android Beta" program that allows users with eligible devices receive preview builds as a regular OTA update, meaning no losing data or manual installation.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!