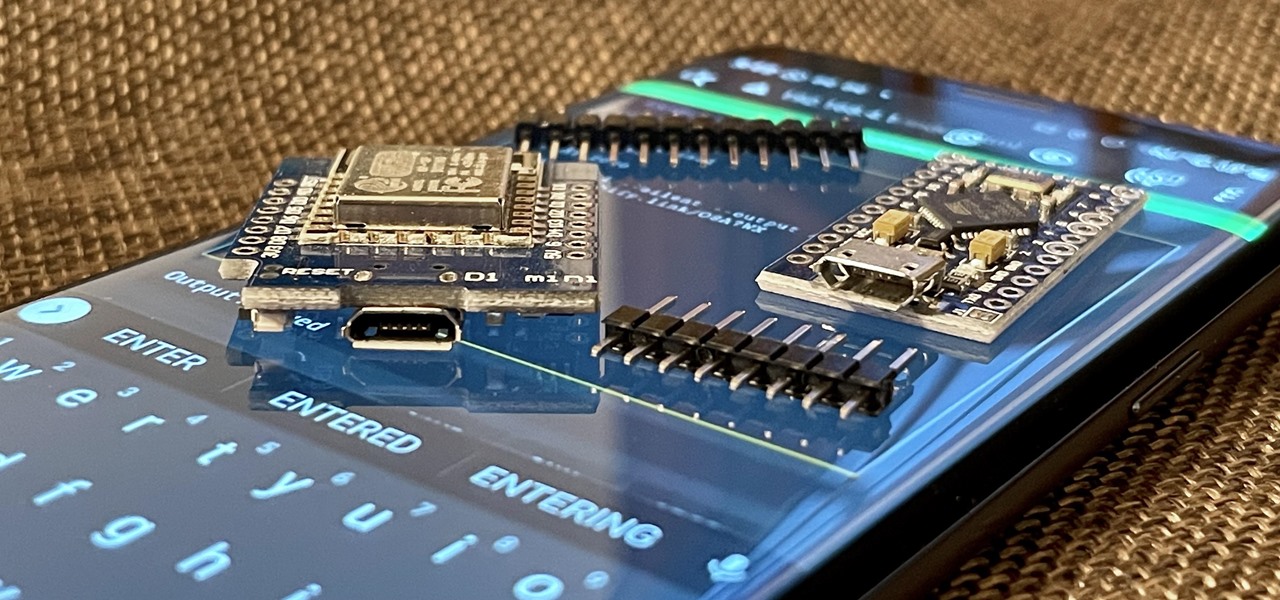
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

Apple's latest big update to iOS 14 has a lot to be excited about. While iOS 14.2 had some fun new features, such as new emoji and wallpapers, People Detection in Magnifier, and a Shazam control, iOS 14.3 brings on the heat. There are new Apple services and products that are supported, ApplePro RAW is ready to go, the TV app makes searching better, and custom home screen app icons work even better now.

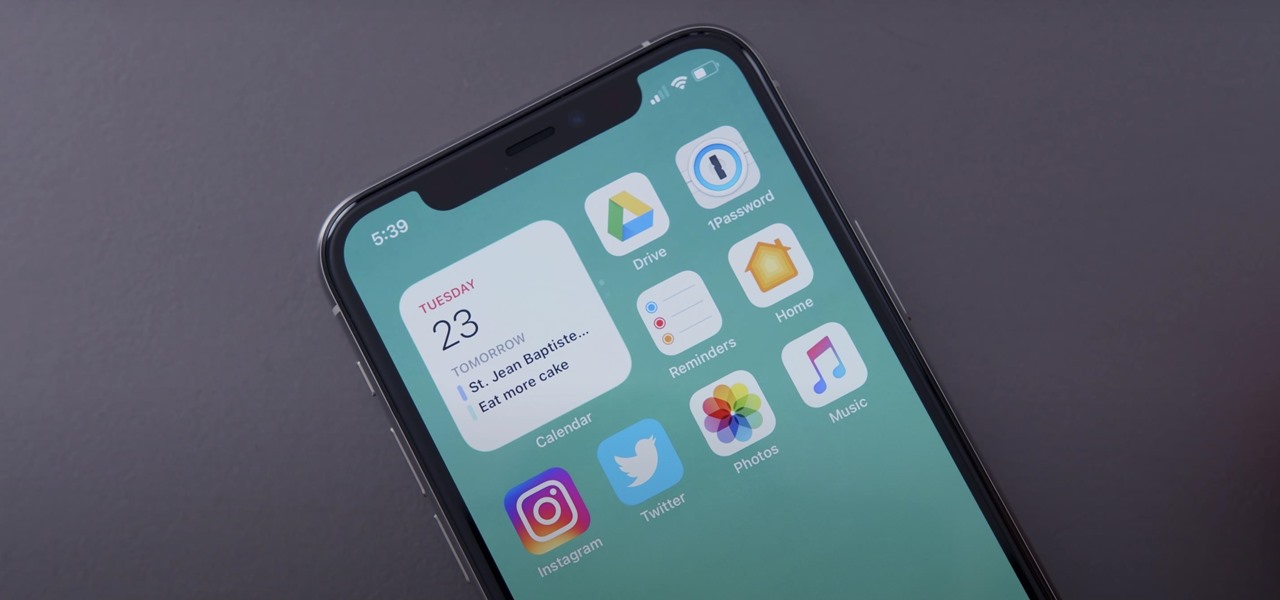
The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.
Apple's iOS 14 is here. With it, you'll see over 200 new features and changes hit your iPhone, including home screen widgets, inline replies in Messages, and cycling routes in Maps. Here's how you can get your hands on the brand new update.
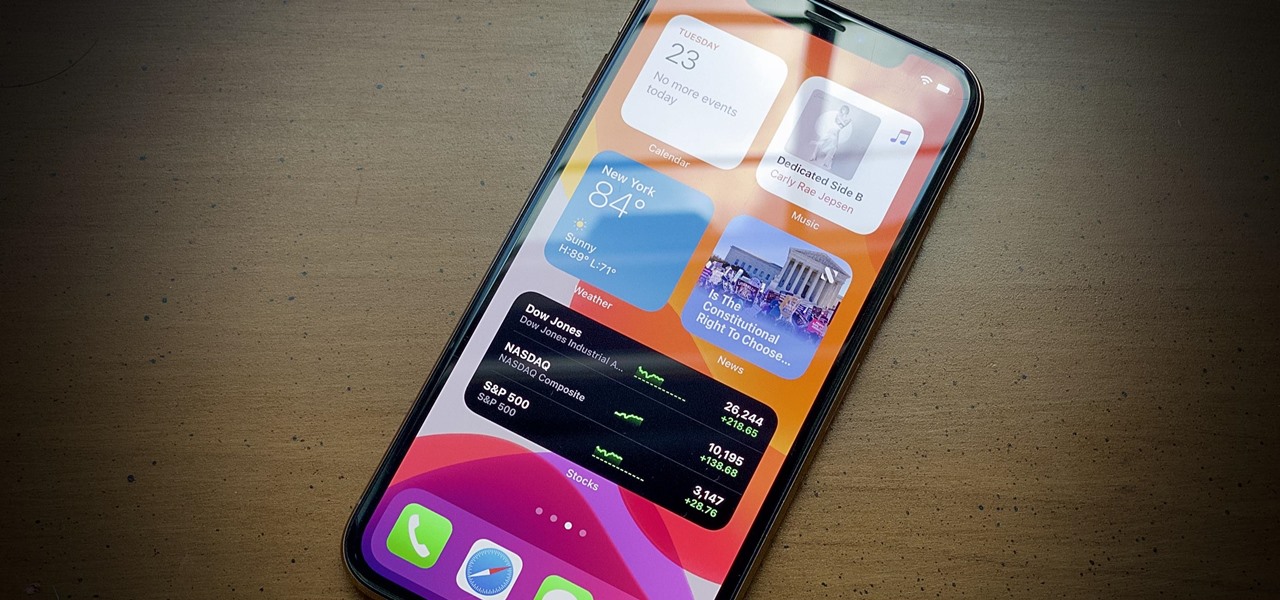
Chief among iOS 14's excellent new features is the overhauled home screen. Now, you can add customizable widgets that live alongside your traditional apps, and both first-party and third-party apps can take advantage of it. Talk about an upgrade. They even work in the Today View and lock screen, so you can have the reinvented widgets for one or the other — or both.

Apple just seeded developers and public beta testers the GM (golden master) for iOS 14 on Tuesday, Sept 15. The update (18A373) comes just after Apple's "Time Flies" event, and six days after Apple released iOS 14 beta 8 for both developers and public testers.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

Apple just released the fifth public beta for iOS 14 today, Wednesday, Aug. 19. This update comes one day after Apple released iOS 14 developer beta 5. It follows iOS 14 developer beta 4 by 15 days, and iOS 14 public beta 4 by 13 days.

Apple just released the fifth developer beta for iOS 14 today, Tuesday, Aug. 18. This update comes two weeks after Apple released iOS 14 developer beta 4, and 12 days after the release of iOS 14 public beta 4.

Apple officially unveiled iOS 14 on June 22 at its first all-virtual WWDC. After months of beta testing, iOS 14 hit iPhones on Sept. 16, but that doesn't mean that Apple is done beta testing iOS 14. There will be new features to try out right up until iOS 15 comes out next year.

Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own holiday lighting animations on a string of NeoPixels with beginner-friendly MicroPython!

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

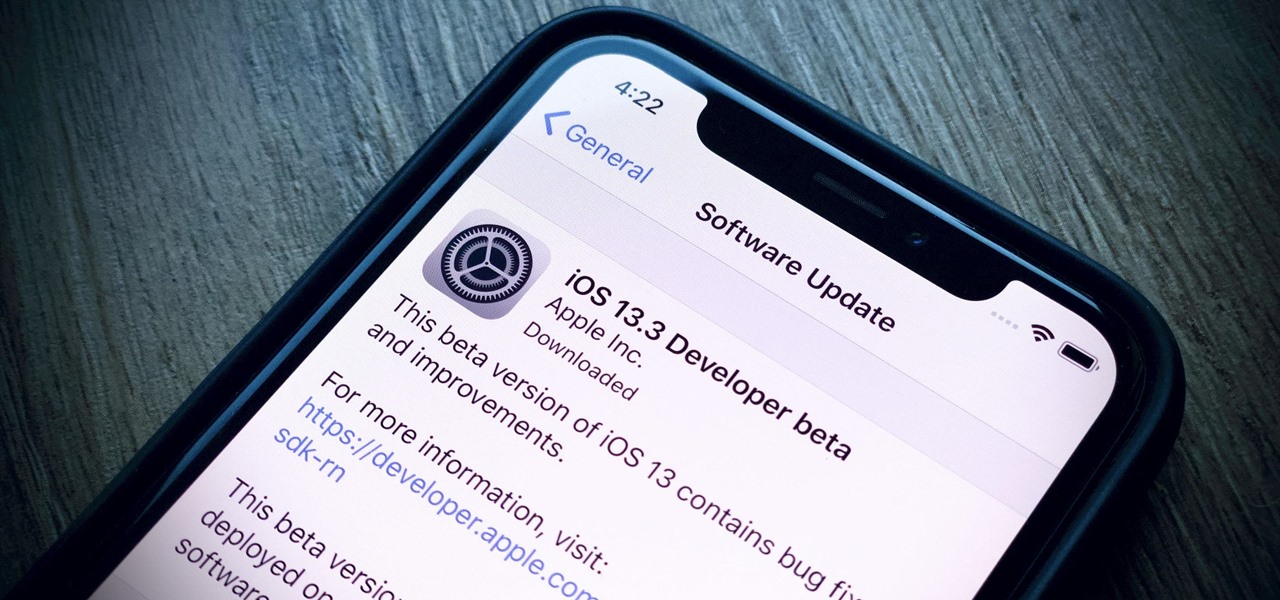
Apple's already gone through iOS 13.0, 13.1, 13.2, 13.3, 13.4, and 13.5 betas, and now it's time for iOS 13.6. If you want to try out new features on your iPhone before the masses, install either the developer or public beta.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

UPDATE: Due to increased, uncontrollable spam, submitting anything other than comments on WonderHowTo and its affiliated network of sites is temporarily closed. Only current and past members who have previously submitted helpful news and guides may be able to submit forum posts.

The biggest problem with Netflix (which is hardly a real problem) is the overwhelming amount of content available for streaming. Browsing through profile-specific categories might help narrow down your search on something to watch, but some of those categories come and go without warning, and it's impossible to find them again—but not anymore.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

Ordinary invasive fingerprinting techniques, such as dusting, are prone to damaging evidence. Micro-X-ray fluorescence images fingerprints without touching them. By stimulating atoms to emit signature wavelengths of light, MXRF also provides chemical information -- such as traces of soil or saliva left in the fingerprints -- in addition to the print pattern itself. Avoid invasive fingerprinting techniques.

Applications are finally beginning to make use of Android 6.0's fingerprint authentication, letting users access sensitive information without having to enter (or unsafely store) complicated passwords on their phones.

WonderHowTo house favorite, Sam Nouyoun gives the lowdown on "fuming" super glue to develop latent fingerprints on smooth surfaces.

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.

Forget backpacking through the Himalayas— Google lets you enjoy the vistas from the comfort of your own home with Google Earth. Forget about snorkeling on your next trip to the Bahamas— you can go under the sea without even getting wet with Google Ocean. Forget about stargazing with your portable telescope— Google Sky brings a million stars to your fingertips. Forget about that application to NASA— you no longer have to be an astronaut to enjoy the terrain of nearby planets, thanks to Google ...

Learn Visual Basic programming by creating a working program in 10 minutes—your own Web browser. This video shows you how to create a Visual Basic project, put the user interface together, add a line of Visual Basic code that gets the Web pages, and then test your program. Create a basic web browser in Visual Basic.

Some cops already have the ability to extract data from your cell phone using handheld forensic devices, but soon police officers will have a new mobile data collection toy to play with—an Apple iPhone. Actually, it's an iPhone-based device that connects directly to the back of an iPhone, which is designed to give law enforcement an accurate and immediate identification of a suspect based on their facial features, fingerprints and even their eyes.

The Blackberry Curve can be used for internet access any time, anywhere. The internet browser can bet set up to with bookmarks and can be updated with popular feeds, to increase ease of use. Watch this video cell phone tutorial and learn how to access an internet browser on a Blackberry Curve. Use an internet browser on a Blackberry Curve.

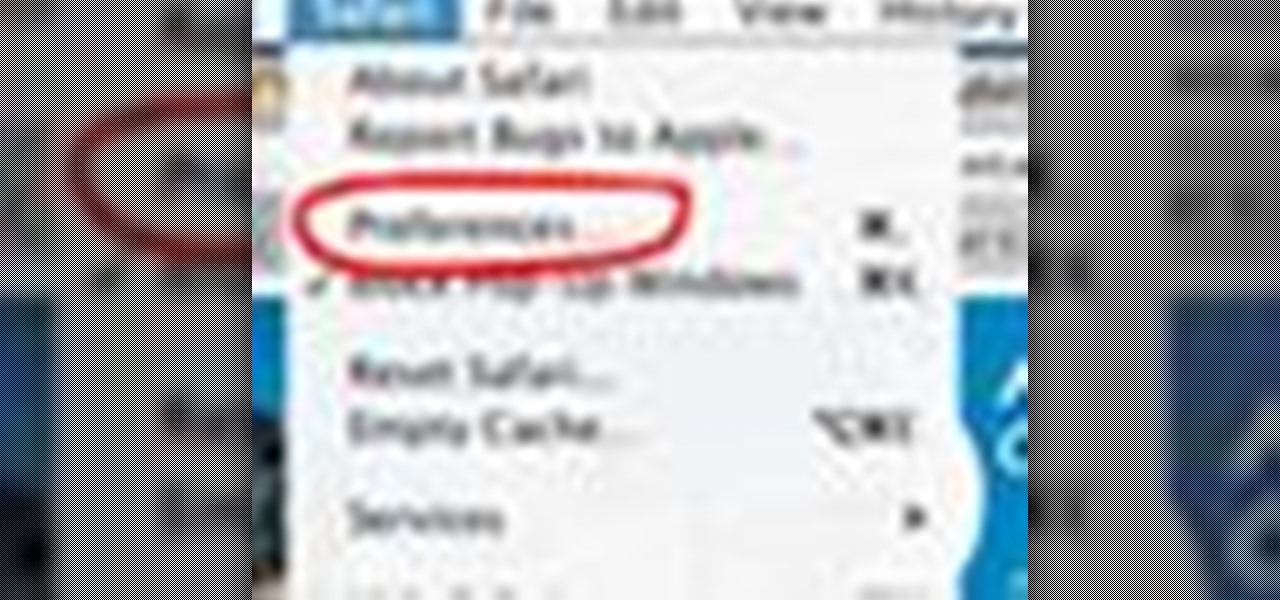
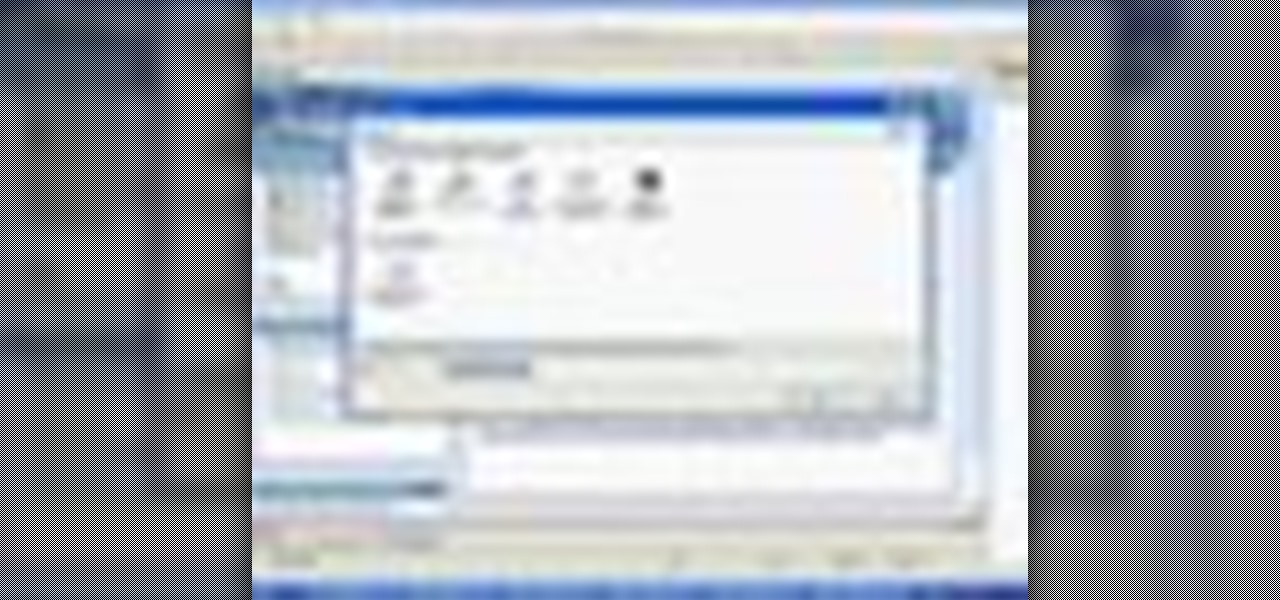
If you're wanting to turn off an extension in Safari, this short video will show you what needs to be done. You'll see how to disable and uninstall single extensions, as well as how to turn off all extensions, in the Safari web browser. It's a simple process— you just need to know where to go— preferences. Disable and uninstall extensions in the Safari web browser.

Safari v1.0 is a web browser for Mac OS X. This simple video explains how to disable accepting cookies in the Safari web browser. There are only 4 very easy steps to follow. Open your Safari web browser window. On the your Safari browser left menu tab click on Safari, a drop down will appear once you click it.

Tired of seeing all of those ads in your browser? The flashing ones make for a terrible browsing experience, and those rollover ones are just downright annoying. If you don't want to be bothered by them again, you've got a few choices, depending on what web browser you're using.

In this video tutorial series, you'll find instructions for using the UCSC Genome Browser. More specifically, this video addresses (1) getting DNA sequences, (2) using annotation tracks, (3) locating intron-exon boundaries, and (4) searching with BLAT. For further detail about any or all of the above topics, and to get started using the UCSC Genome Browser yourself, take a look! Use the UCSC Genome Browser - Part 1 of 4.

Watch this video to learn how to use the address bar of your web browser. The browser in the video is Internet Explorer 7, but the process is the same for pretty much any browser, including Firefox. Use the address bar of your web browser.

How to create a web browser like Firefox using Visual Basic . part 1. Make your own web browser using vis basic =] simple coding and its all yours ! Program a web browser using Visual Basic - Part 1 of 3.

M2 All About the Mobbing Browser App Download it Today its Free & There's more App's to check it on the Tool Help Bar all These Are already Installed.

It's not listed as one of the features on the updated Nook e-reader, but there is a web browser hidden inside Barnes & Noble's newest device, you just need to know how to access it. The eBook Reader shows the clandestine web browser on the Simple Touch Reader in the video below, and it's fairly easy to access. Just open up the Nook's search function, type a URL into the search bar and hit the go button. It's that simple.
Hello again ! This is the second part to Fingers from a Hand Analysis perspective.Where as the first Video just covers basic introductions to the Fingers, this part two Video takes things a little bit further and examines ......Finger Shape ;- Length suggesting mental speed, Methodical or Speedy thinker ?Finger Width ;- Suggesting which level a persons interests may lay, Mental or Practical realms ?Finger Prints ;- Amazingly interesting area to explore , Fingerprints do not change.. They star...
Microsoft office 2010 is the successor version of office 2007 and is code named as office 14. It is the first 64 bit version of office which is only compatible with Microsoft service pack 3, Windows vista and windows 7. It was released on April 15, 2010. It is the first Microsoft application which offers free online version of word, excel, PowerPoint and one note. These can be easily used with all the popular browsing software. The various functionality which are added in office2010 are descr...

With palm reading! Think it's hokey? We were skeptics, but found out that palmistry is actually founded in science. Think of it as an anatomical fortune cookie!