The Netherlands are a hotbed of indie game development, which seems appropriate for such a brilliant and eccentric little nation. Two man Dutch indie developer Vlambeer have found themselves in the news more often than most companies of their size, thanks to two great games and a third on the way.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

The HP Touchpad 64 GB is out in action with a robust processor and additional applications in the market. Using the best technology on earth, it is looking forward to give a tough fight to the Apple’s iPad 2. The 64 GB HP TouchPad sound more promising to its predecessors. The experts feel that the two device, HP TouchPad 64 and Apple’s iPad-2 is more or less the same. Let’s have a glance over the device by discussing the various features it encompasses.

The lack of a search function within Google+ is driving me crazy. It takes me way too much time to find the posts I want to save and refer back to, and it's counter-productive for Google to launch their social networking product without an integrated search.

It's been an eventful week for Google+. Facebook decided to up its game and start rolling out several major updates intended to address privacy concerns. We got a glimpse into the future of Google+ via an insightful discussion between +Bradley Horowitz and +Tim O'Reilly. And Google decided to integrate the +1 button more fully with Google+ by allowing users to share directly from the +1 button. That's not all, though—scroll down for more news & updates that occurred in the past week.

We've covered Chrome browser extensions that make your Google+ experience richer and more useful, but there are still many users who prefer to use Firefox. To that end, I've gathered 13 Firefox add-ons to aid in the enhancement of your Google+ experience.

Stewart Butterfileld is one of the last great old-fashioned tech billionaires. He founded Flickr, and then sold the company to Yahoo! for a stupendous amount of money in 2005. Like Mark Cuban and others before him, he was left wondering what to do with the rest of his long and fabulously wealthy life. Cuban bought the Dallas Mavericks and turned them from unabashed losers into beloved champions. Butterfield decided to try his hand at game design (something he had attempted with the ambitious ...

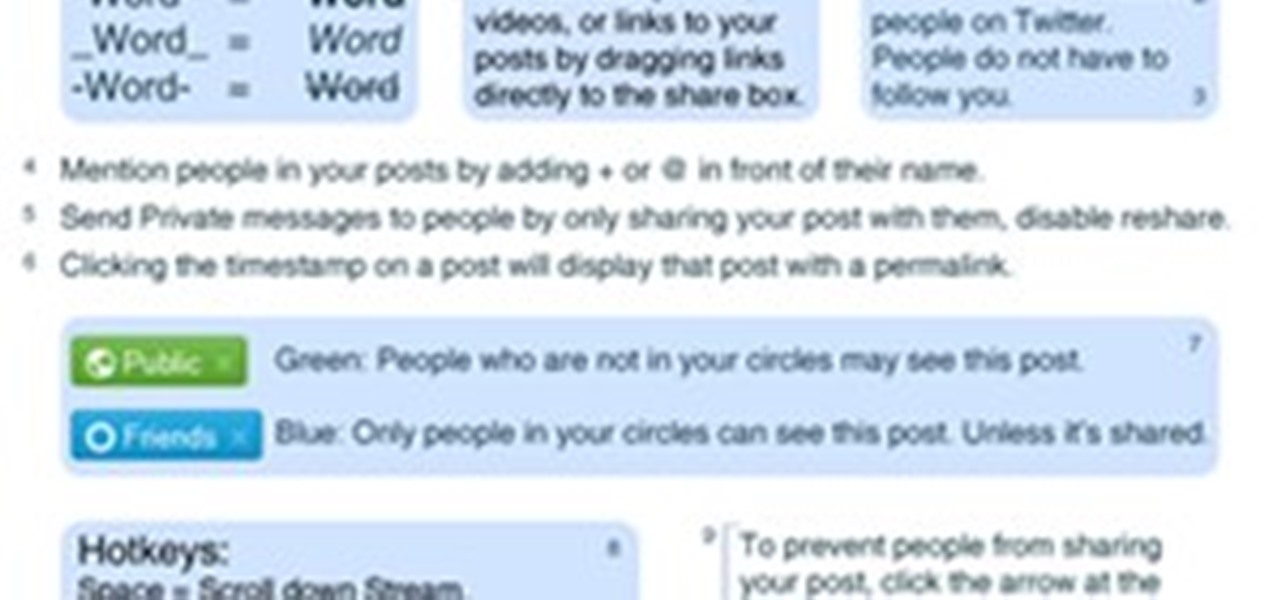
With the Google+ team members being generous and free-flowing with advice on some of the more advanced features of Google+, we'll be publishing a weekly summary of the latest pro tips. Chances are, if you've been following the Google+ team members, you've seen some of these already but you don't have them all in one handy place.

Google+ is the most exciting new social network to come around this decade, and the only product with a chance of challenging the monopolies we know as Facebook and Twitter. As an Internet addict, I've joined every major social network there is - from Friendster (who?) to MySpace (so ugly) to LinkedIn (yawn) to Twitter (irritating) and Facebook (annoying to manage). Competition is delicious, especially between well-financed monopolies. Google+ really seems to have identified an Achille's heel...

Though it could be argued that Apple's popular and widely used iTunes media player was responsible for the growth and explosion of podcasting, I would argue that iTunes is not the best way to manage and listen to your podcast subscriptions—if you're a iPhone, iPad, or iPod Touch user. Instead, you will find that a $1.99 mobile app called Instacast (iTunes App Store link) is a much better method. Below, a short video introduction to Instacast, plus a written breakdown of its features. Mobile L...

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

INTRODUCTION In this Digital world now almost every one knows the a, b , c of computer. From a child of 5th grade to an old man, everyone knows how to operate computer and do simple work on it. Thats why you need to have something which makes you different from others.

INTRODUCTION If you are a part-time blogger and owns a blog which is hosted on blogger, then the first thing which you could want to do is to convert your blog layout to a professional looking website. You can either edit the XML file yourself or you could choose to use a template designed by others. If you have no idea of XML editing and neither you want to use a template created by other, then hopefully there's a way to convert your blog into a website.

Thanks Anonymous User For This Article, Not Bad Ok SoftzZz...!.!.!.: Step 1 Antivirus
Do you want to be that cool person on the web? Heh. Actually, did you just want to try spicing up your embedded YouTube videos? Try it in HD, or have it in autoplay or different sizes! With this code, you will be able to play music, or display your latest vlog as soon as you get a viewer, as long as they allow embedding!
USE WINDOWS 7 ULTIMATE x64 w/ all the latest updates always OF COURSE AND... USE THE ASTON 2 SHELL REPLACEMENT, MENU, DESKTOP, W/ THEMES...

Update This issue has been resolved

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

We all want a faster, more efficient web browsing experience. Some immediately flocked to Google Chrome as soon as it was released, because of its super fast speeds. Others restrained themselves and continued to wait for Microsoft and Mozilla to play catchup. And the time is almost here for all Internet junkies to improve their game.

This weekend, I was on a trip to Binghamton. In the midst of unpacking my toiletries at the hotel, I found that my brand new razor blade had lost its cap. How did I find that out? Well, when I pulled my hand out of the bag, I found that my right pointer finger was missing a bit of its tip and dripping blood on everything. Thankfully, Nathan G. H. Shlivovitz was with me and knew what to do, but the experience helped me to realize that everyone needs a little first aid knowledge in life. Here a...

How to use uTorrent First of all we need to understand what uTorrent is. uTorrent is a file or a Micro-Torrent that helps you, the user, download stuff like documents, pictures, videos, or e-books. uTorrent is very, very, useful when you know how to do it. so hope fully this tutorial helps you learn to use uTorrent.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

This is a tutorial showing you how to easily hack flash (.swf) games! You only need two things:

Over the past few months I've written up several helpful How-To guides to help you with various FarmVille related issues. It's about time I put them all in one place so they are easy to find, learn from and share! It has been a pleasure writing for you all and I do hope I have helped you find ways to meet your personal gaming goals!

This is my list of programs that I must have on my PC, but I think you can also use them, so here is the list:

I recommend you take a look into this issue and suggest that your friends delete their association with Gamers Unite and any other cheat providing site. This post is meant only as my advice for how to remove Gamers Unite or any other spammy app. This is all based on my personal feelings about the snag bar and websites that would hand out such cheats. I've provided this as INFORMATION ONLY. Please decide on your own what you think of the whole situation.

Who doesn't love Star Wars? No one, that's who. And if you love Stars Wars, logic would follow that you like lightsabers, so central are they to the tale's mythology. It's part sword, part laser, and makes a sound like a humming motor have multigasms. If I saw one in real life, I would struggle not to lick it, even though that would mean death.

Everyone's been in the following situation. You're sitting there at a nice bar, chatting up a smoking hot member of the opposite sex when all of a sudden they drop this bomb: "Can you engrave on wood in Photoshop?" The next thing you know, the night spirals into blackness and you wake up in a puddle of your own tears with some half-eaten beef jerky hanging out of your mouth.

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security, because X10 is here.

This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project to do not too far back, and a good bit of practice for a beginner to programming. It teaches that you can do useful stuff with programming. However, a while ago Twitter started using something called OAuth to access the...

Google+ is the greatest social network to emerge since Facebook annoyed everyone into joining, but that doesn't necessarily mean that our relationship with it is all rosy. Although Google+ has amazing innovations, like hangouts and circles, users are spending a lot of time begging for core features that take what seems to be an eternity to emerge.

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

Last week's round up was all about third party services that sprang up to fill any Google+ voids. This week, I'll let you know how to keep up with the latest Google+ updates, and give you some great tips for interacting with your followers.