An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Snapchat is great for sharing and receiving pictures that we don't want "living" for too long, but sometimes we'd like to hold onto those memories, whether the other party wants us to or not.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

This could happen when you trust a guy to hang out wet clothes. Ladies, beware, guys simplify housework simply because they don't care of it's a chore they just don't want. Watch and learn to be creative about the ways you spice your every day chores up. Most of all, laugh your head off.
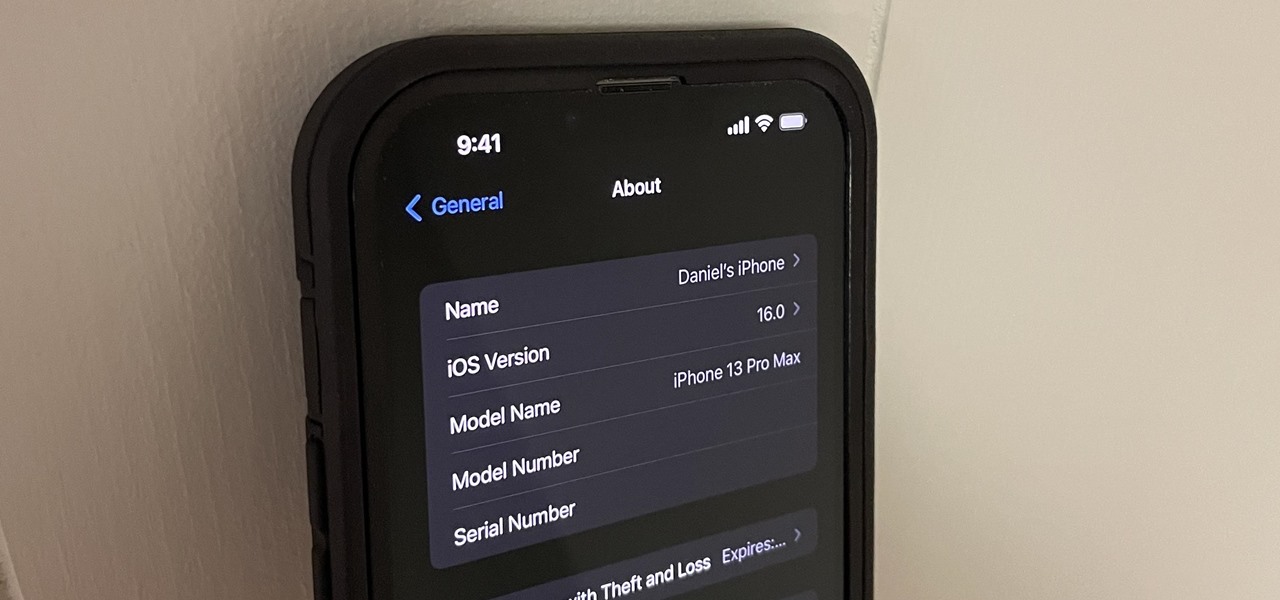
Beta software can be exciting because you get to experience cool new features before most other people. But it can have unwanted consequences such as bugs, UI glitches, and horrible battery life that'll make you wish you never installed it. If that sounds like you with iOS 16 beta or iPadOS 16 beta, you can downgrade to iOS 15.5 or iPadOS 15.5 for a more stable user experience.

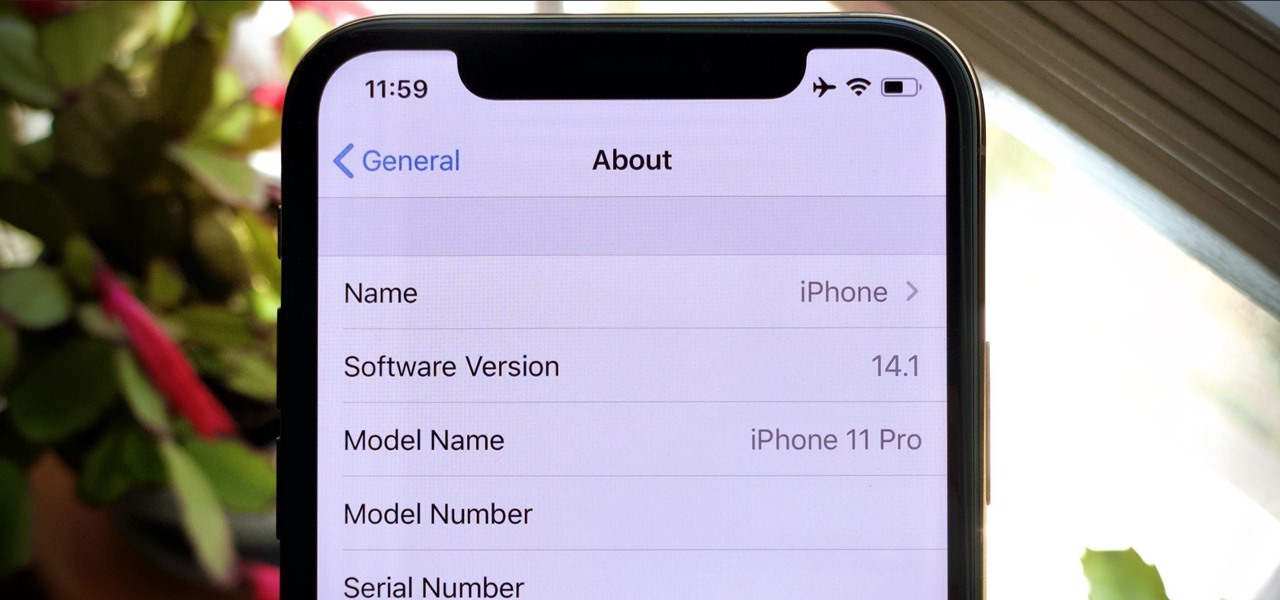
Apple's iOS 14.0 update has come and gone, and now we're sitting on iOS 14.2, the latest version of the iPhone's operating system. While it may be too late for you to revert to the last iOS 13 version, if the iOS 14.2 firmware is giving you problems or you're not just digging it, you can downgrade to iOS 14.1.

Making the jump from an older iPhone, or even an Android phone, to the iPhone 12, 12 mini, 12 Pro, or 12 Pro Max can be a big one. It's not just the change of a new smartphone — it may have had a huge impact on your wallet too. So whenever the device goes berserk, is unresponsive, or won't turn on, it's understandable to be worried. But DFU mode can help whenever you're in a dire situation.

Heartbroken? If your girlfriend threw in the towel before you were ready, there are a few ways you can try to win her back. Follow along with this tutorial and try to mend your broken heart.

Striking up a conversation with a group of people you don't know can be an intimidating task. Come prepared with some interesting comments and ideas and you will be able to make new friends out of any crowd.

There is a lot of stigma around prenuptial agreements but they can be a good chance to work on difficult issues as a couple and make sure you're on the same page. Prenuptial agreements don't have to be a horrible experience and can give a soon to be married couple some peace of mind.

Before you get started exploring a big new city or even just getting reacquainted with the one you live in now, make sure you aren’t putting yourself in any unnecessary danger. Memorize good traveler habits that will keep thieves and scam artist off your back.

Motivational speaker and leadership coach Tim Warneka teaches how to write a successful college essay in nine simple steps. Read and understand the directions and expectations the professor has for the assignment. Sit down and write whatever comes to mind on the topic. Edit your paper, making sure to use academic English. Allow yourself time to "sleep on it" and come back to re-read your essay with a fresh mind. When you come back to it, read the paper out loud to find any mistakes. Allow one...

No matter what your shape is, follow this advice to make sure you strut your stuff with style. You Will Need:

Not in the mood to do jumping jacks in your hideous gym uniform? There are ways to sit it out. You Will Need

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from foods.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

This is about how to make a rabbit become less wary of you and more trustful with you also. I myself have a Dutch that was released by its previous owner, then I rescued it. She never wants to be took out of her cage, but now she doesn't mind as long as I'm gentle and nice.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

The World Health Organization has declared the new coronavirus a pandemic, and the Centers for Disease Control and Prevention recommends video visits with a healthcare professional to reduce the risk of being exposed to the coronavirus that causes COVID-19. If you are experiencing mild flu-like symptoms, virtual doctor visits may also prevent you from endangering others.

Apple's innovations often involve more taking away than adding on. The company has released seven iPhones that omit the home button, the latest batch including the iPhone 11, 11 Pro, and 11 Pro Max. If you recently picked up one of these devices for the first time, you might be a little confused on how to enter DFU mode when your iPhone acts up.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

If you're running iOS 10 or lower, there is no built-in way to make a screen recording on an iPad, iPhone, or iPod touch directly from the device, but that doesn't mean there isn't a way to record your screen at all.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.