How To: Use Team Building Tools Efficiently
In the business world, it is always best to have the people you work with. For you to become the best you could give, here are at least 5 tips in using team building tools.

In the business world, it is always best to have the people you work with. For you to become the best you could give, here are at least 5 tips in using team building tools.

It's fitting that students at the University of Washington can catch a glimpse of the new, 135,000 square-foot computer science building in augmented reality before construction is completed.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

There are already hundreds of glitches out there for Grand Theft Auto 5 Online, but most of them are useless. Most of them don't do anything to benefit your gameplay, but they're still pretty fun to mess around with. One such glitch, shown off by YouTuber AquibTV below, lets you inside any building in Los Santos. Los Santos is a big ass city and there are tons of buildings that you cannot get into without using a glitch like this one.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.
Alright, calm down and take a breath! I know the object creation chapter was a lot of code. I will give you all a slight reprieve; this section should be a nice and simple, at least in comparison.
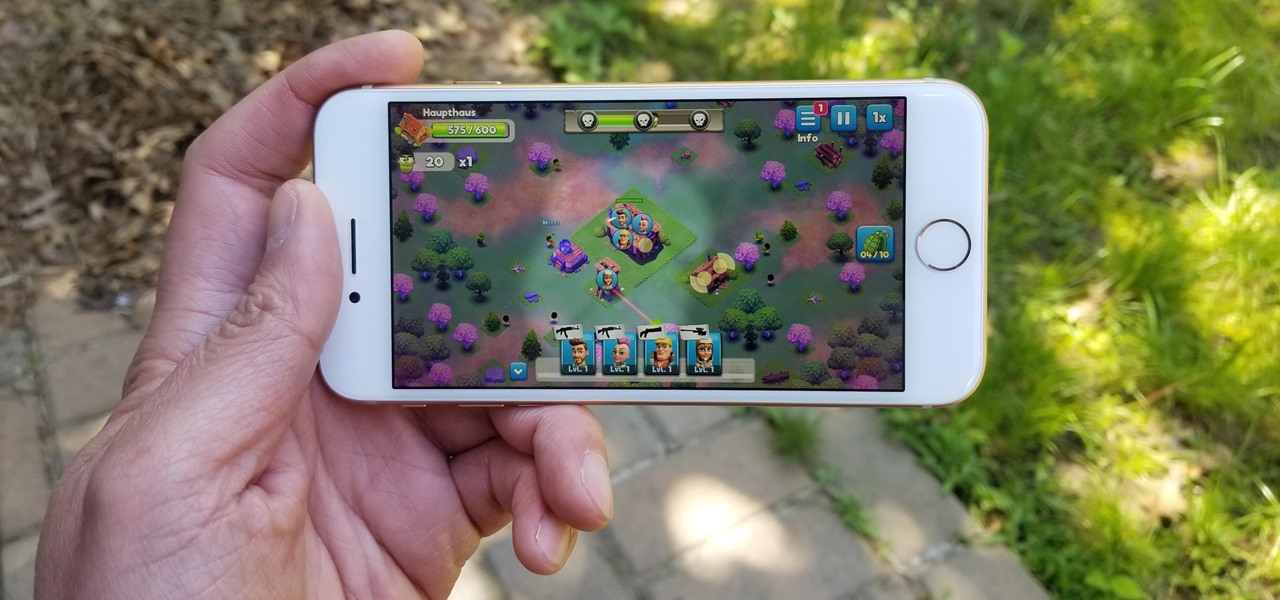
With tons of titles to choose from on the iOS App Store, you'll never be lacking when it comes zombie shooters. Unfortunately, the same can't be said if you're more interested in base-building and defending against the undead. PlayStack aims to change this, and they've soft-launched Survival City in the Philippines for further development. With a simple hack, you can try the game yourself right now.

Now, you can prevent Donald Trump from building that idiotic wall from the comfort of your smartphone. Well, in theory, you can, thanks to a hilarious new gaming app called — wait for it — Trump's Great Wall.
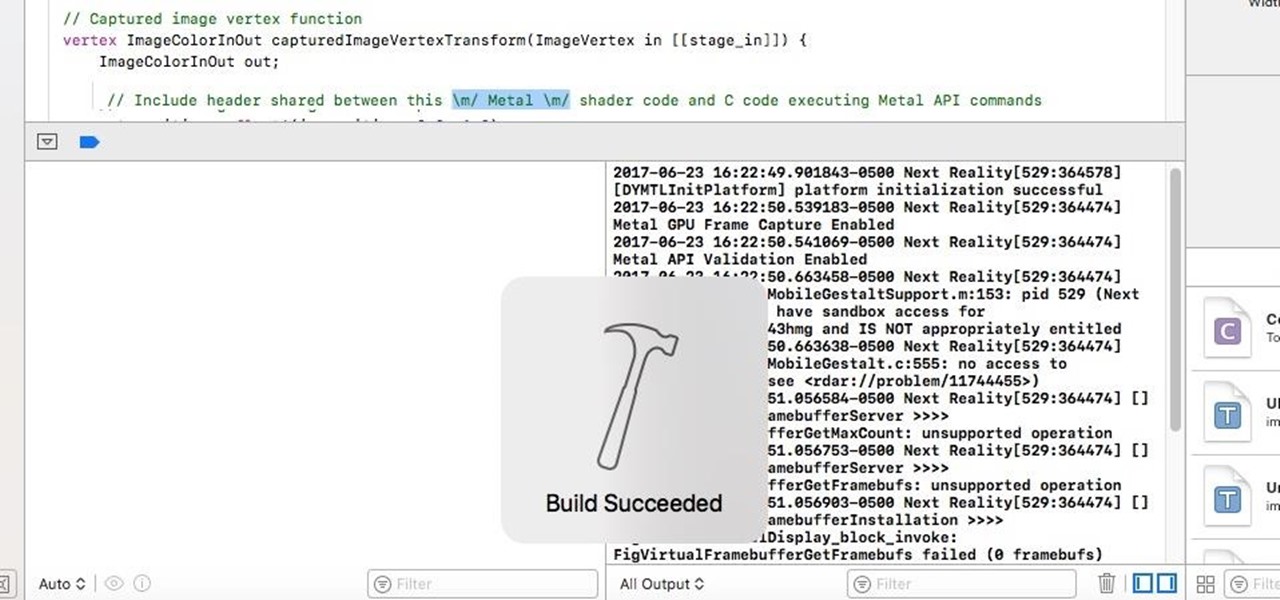
In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step.

Time-lapse videos are a recent phenomenon to the mainstream audience—in movies, on television shows, and even in commercial ads. These sped-up and blurred images are a microcosm of many of our lives in which we're constantly in a hurry to get somewhere. We like everything fast: our work, our coffee, and our news.

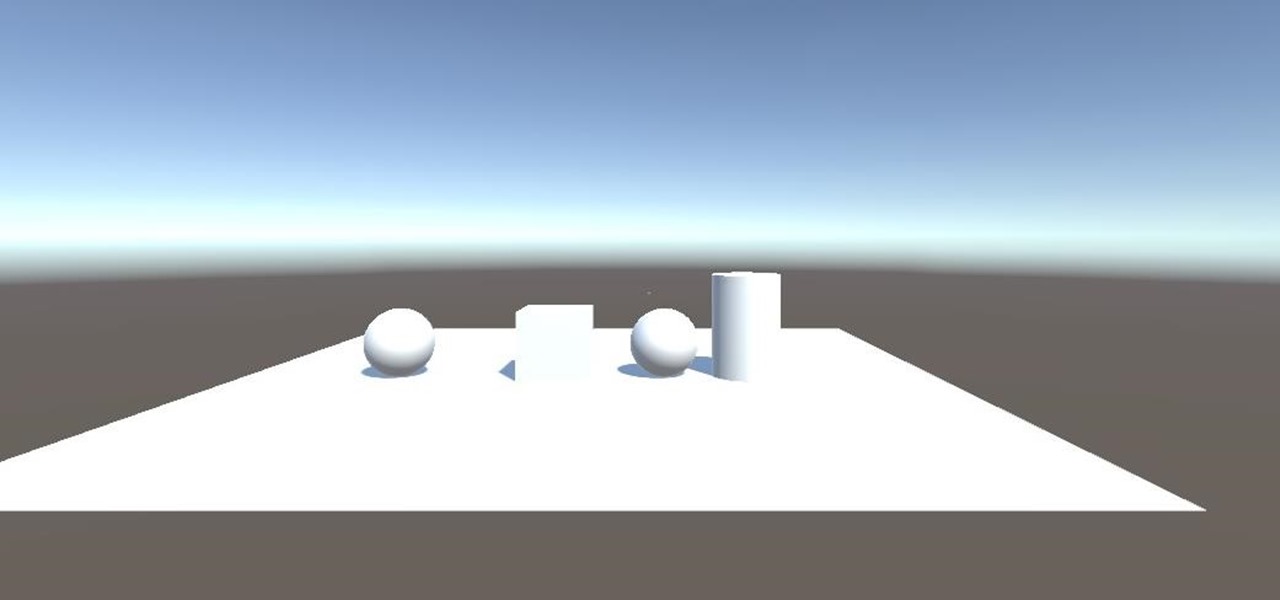
After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.
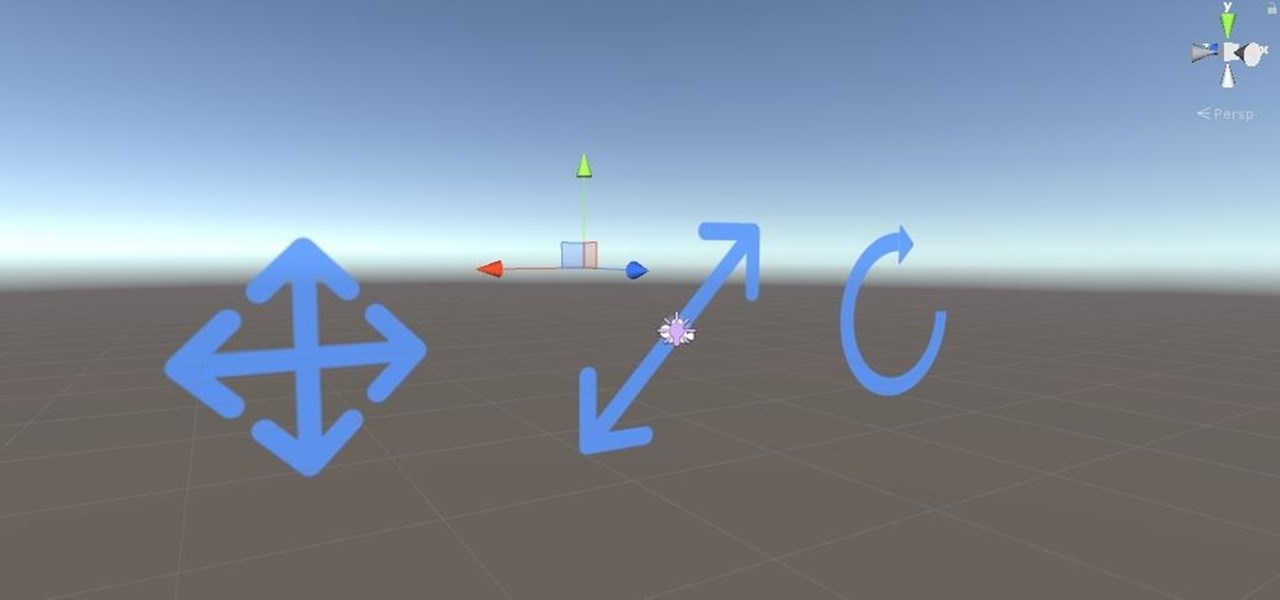
Now that we have installed the toolkit, set up our prefabs, and prepared Unity for export to HoloLens, we can proceed with the fun stuff involved in building a dynamic user interface. In this section, we will build the system manager.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.
To revise a line from the Blues Brothers, when it comes to ARKit apps, we've got both kinds — home utilities and games. As such, two more candidates for each category have made their way to the app store.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.
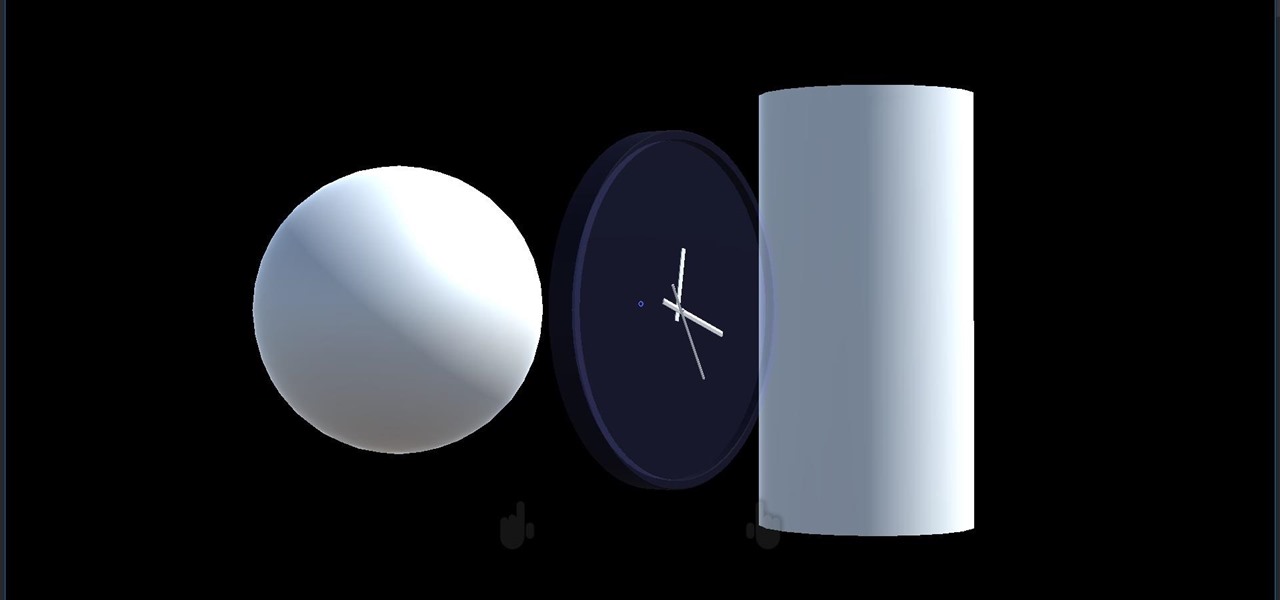
We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.
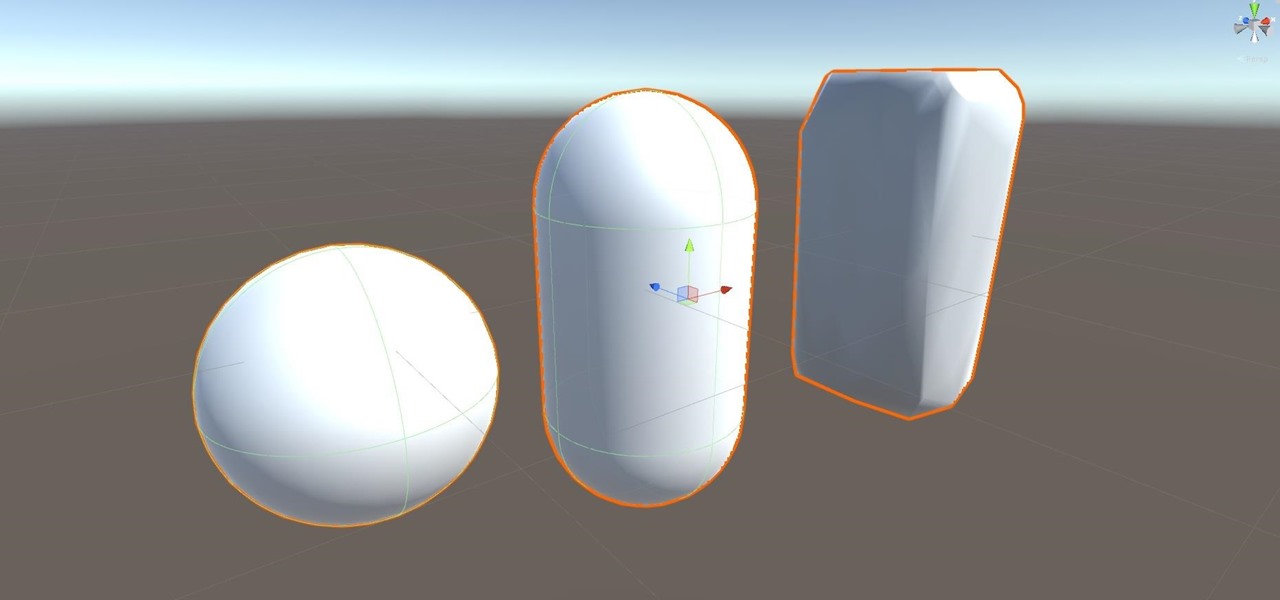
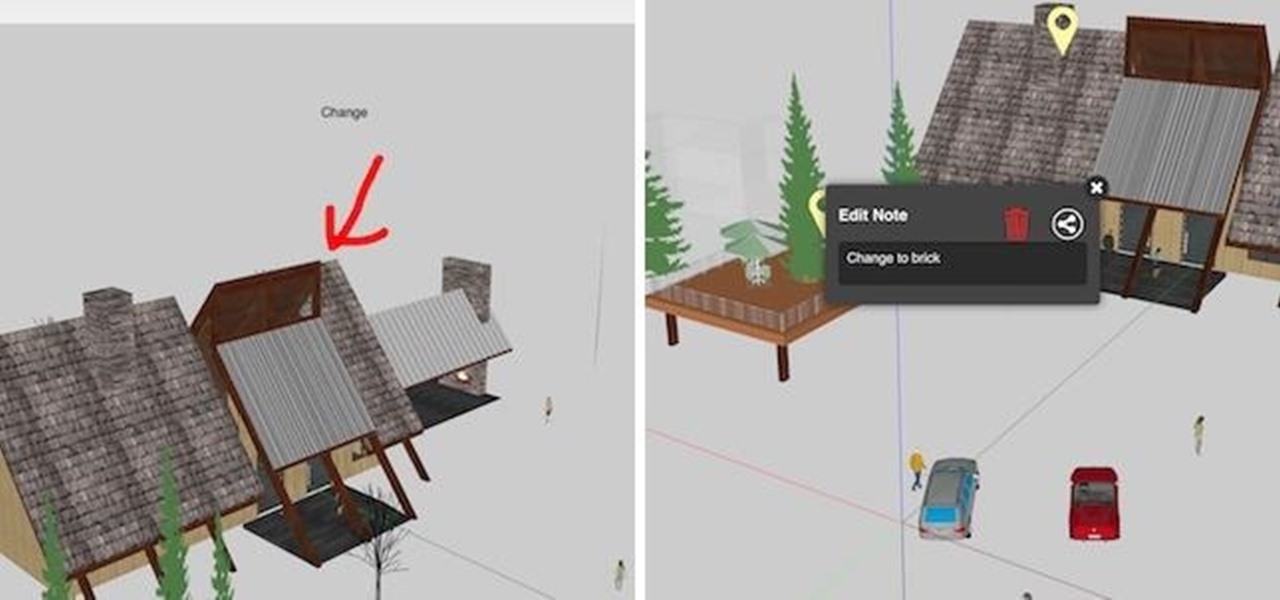
Alright, let's dig into this and get the simple stuff out of the way. We have a journey ahead of us. A rather long journey at that. We will learn topics ranging from creating object filtering systems to help us tell when a new object has come into a scene to building and texturing objects from code.
I currently am and have always been what one might call a PC/Android guy. Many that know me well would likely even go so far as to say I am anti-Apple. About an hour after seeing the ARKit demo during the day-one keynote at WWDC, I became the owner of a brand new Mac.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.
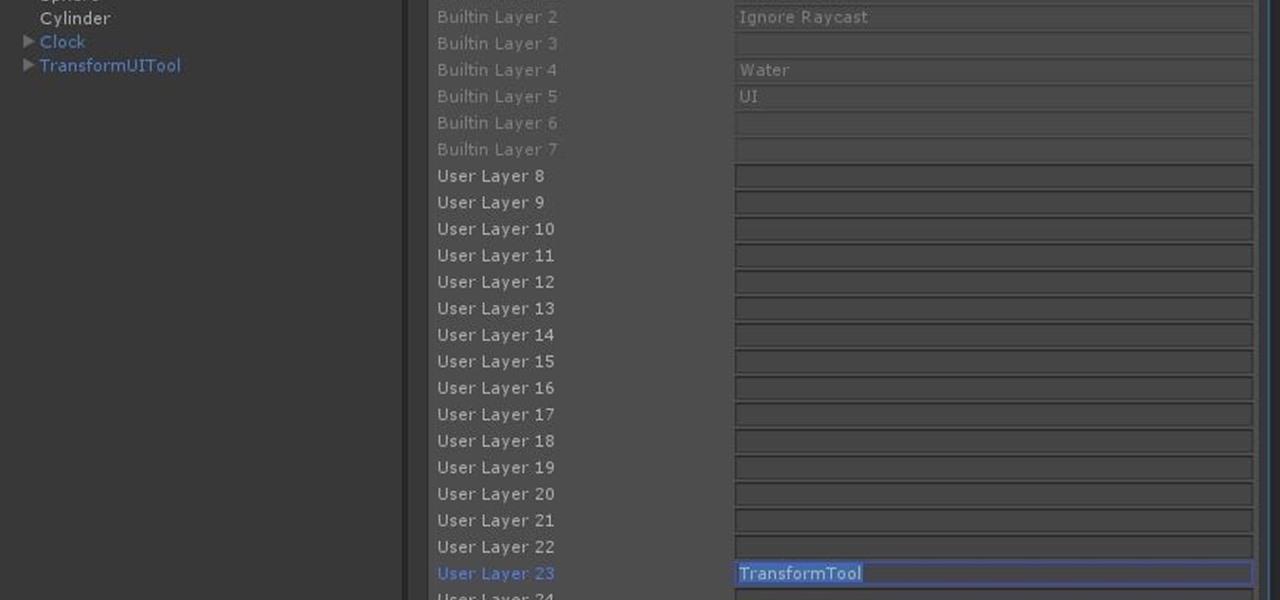
Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.

Using ladders (Rakes) to build your gable overhangs on the shed is one of the fastest and easiest ways to do this. Henry shows you how to layout, build and install the ladders on our shed.

Henry shows you how to build homemade trusses. This video includes instruction on how to layout your truss jig to make sure all trusses are identical. After you watch this video, you'll see how easy it is to build your trusses!

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.
The reveal of Apple's new ARKit extensions for iPhones and iPads, while not much of a shock, did bring with it one big surprise. By finding a solution to surface detection without the use of additional external sensors, Apple just took a big step over many — though not all — solutions and platforms currently available for mobile AR.

We've got Google Maps to help us out when we need to navigate outdoors, but Google can only map out so many indoor locations without getting creepy. And that's where Stimulant comes in. This "innovation studio" built a HoloLens app that lets you map out an area, define locations, and use the headset to get instant directions to any defined location.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Augmented reality software maker Upskill has released the latest version of their Skylight platform, adding a number of new tools to ease implementation and improve functionality for enterprises, including a new application builder.

Generally speaking, in terms of modern devices, the more simple you make an interface to navigate, the more successful the product is.

Here's how to build a sexy looking water-fuel generator that will convert your tap water into an extremely powerful, clean burning gas!

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Greetings my fellow aspiring hackers,

Greetings my fellow aspiring hackers,

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.