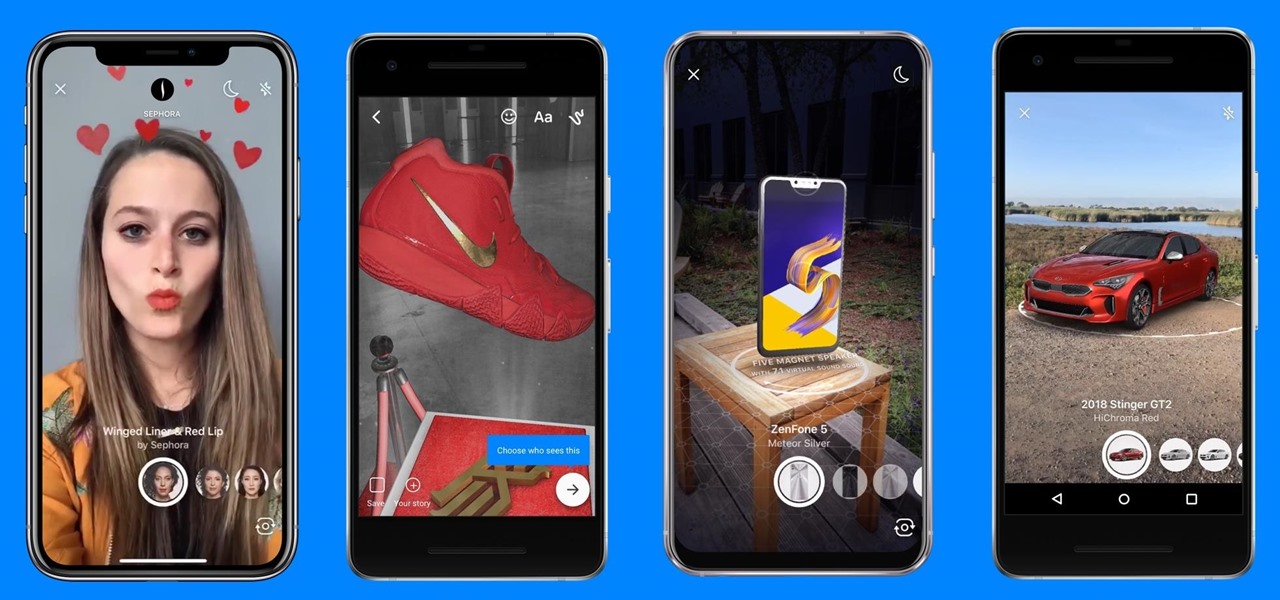
One of the most prestigious annual events for the advertising industry, the Cannes Lions is the ideal backdrop for Snapchat to show the brands and agencies in attendance what it's got.

As one of the leading 3D engines for augmented reality development, a new release of Unity is a significant event that carries the potential to facilitate huge leaps forward in AR content creation.

Ingress, the godfather of location based-AR games developed by Pokémon GO creator Niantic Labs, is getting a new lease on life via Ingress Prime, a reboot of the game built on the Niantic Real World Platform.

Less than 20 days after the launch of Magic Leap One, Mapbox has jumped at the chance to provide its map services to Magic Leap developers through its Maps SDK for Unity.

On Tuesday, Unity released the latest version of its 3D engine, which brings improvements to the Scriptable Render Pipeline that the company introduced earlier this year.
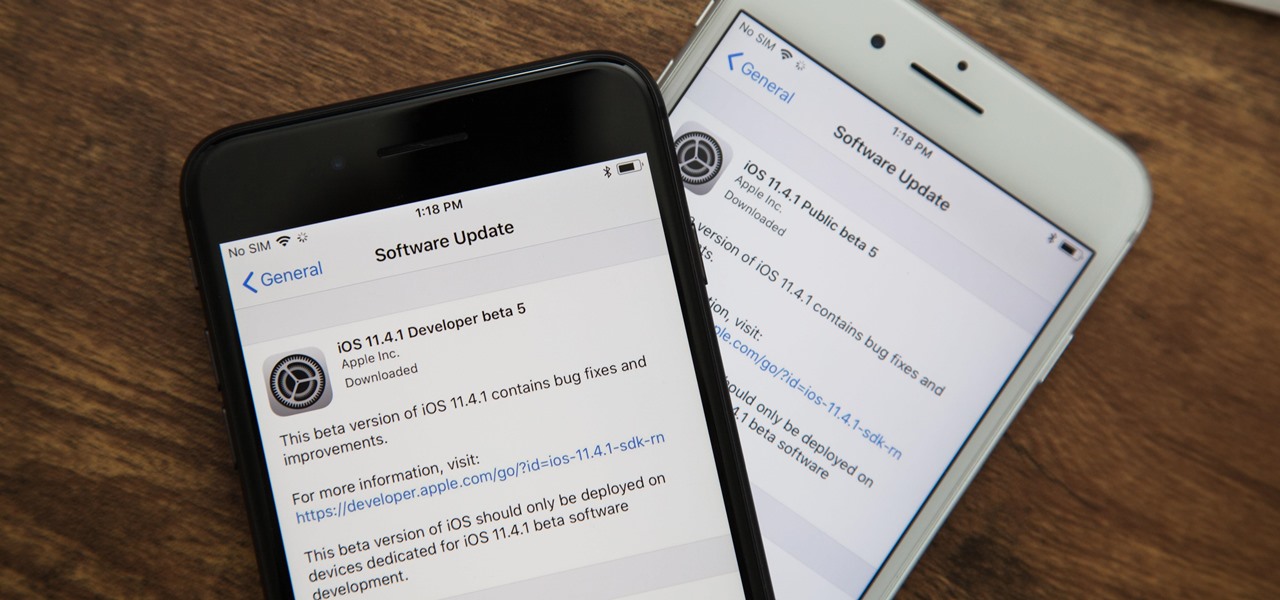
Apple has been testing iOS 11.4.1 for just over a month now, and so far, there's nothing to show for it except unknown "bug fixes" and under-the-hood "improvements." And that still rings true with the release of iOS 11.4.1 beta 5 on Monday, July 2, which comes exactly one week after beta 4. Now the question is, when will the stable update be pushed out to everyone?

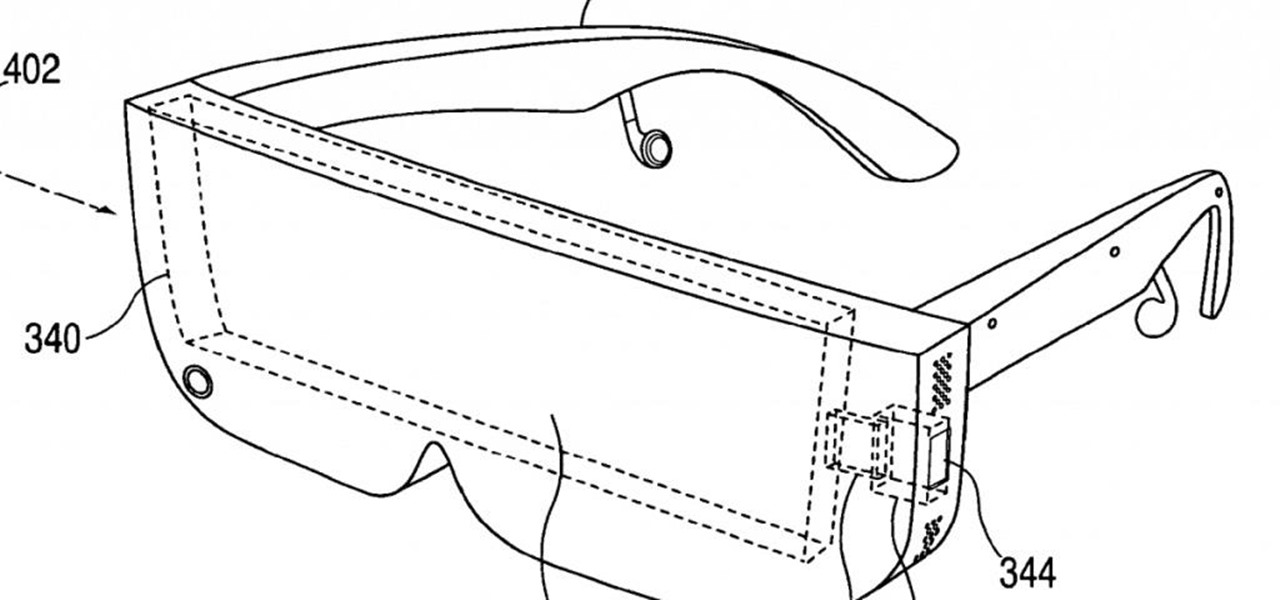
Between acquisitions, hirings, patent applications, and insider reports, all signs point to Apple building a smartglasses product that could ship as soon as 2020, but the company has not officially confirmed such plans.

We are still months away from Google unveiling the new Pixel 3 and 3 XL. As rumors continue to trickle in revealing more about what it will look like and its specs, we've learned an important aspect — who is actually manufacturing them.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.

On Tuesday, at Google's I/O developer conference, the company announced a huge update to its ARCore augmented reality toolkit that matches the latest features of ARKit, and surpasses Apple's AR platform via support for shared experiences.

On Tuesday, on the one-year anniversary of the announcement of its AR Camera platform, Facebook founder and CEO Mark Zuckerburg revealed at the company's F8 developers conference that the platform will be extended to the company's Instagram and Messenger apps.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

The Galaxy S9 is a great phone powered by the Android ecosystem. This includes Google's family of apps — many of which overlap with Samsung's in functionality. This can lead to redundant apps that siphon resources from your phone, but fortunately, there's a way to dull some of the noise and disable built-in apps.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The OnePlus 5T was just released, and it's packing several new useful features. While many OnePlus 5 buyers are feeling frustrated with the quick release cycle, lots of fans are still clamoring to buy the new device. Aside from the larger screen, most of the buzz around the 5T has centered around the new face unlock method. Thanks to a clever hack, you can now get this feature on almost any phone!

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

The advent of ARKit and ARCore has strengthened the demand for development tools to build augmented reality experiences for compatible iPhones, iPads, and Android devices.

To revise a line from the Blues Brothers, when it comes to ARKit apps, we've got both kinds — home utilities and games. As such, two more candidates for each category have made their way to the app store.

As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

The status of Uber's driverless program remains a big unknown amid the company's recent woes, but a reported multibillion-dollar shot in the arm by Japanese tech giant Softbank could change all that.

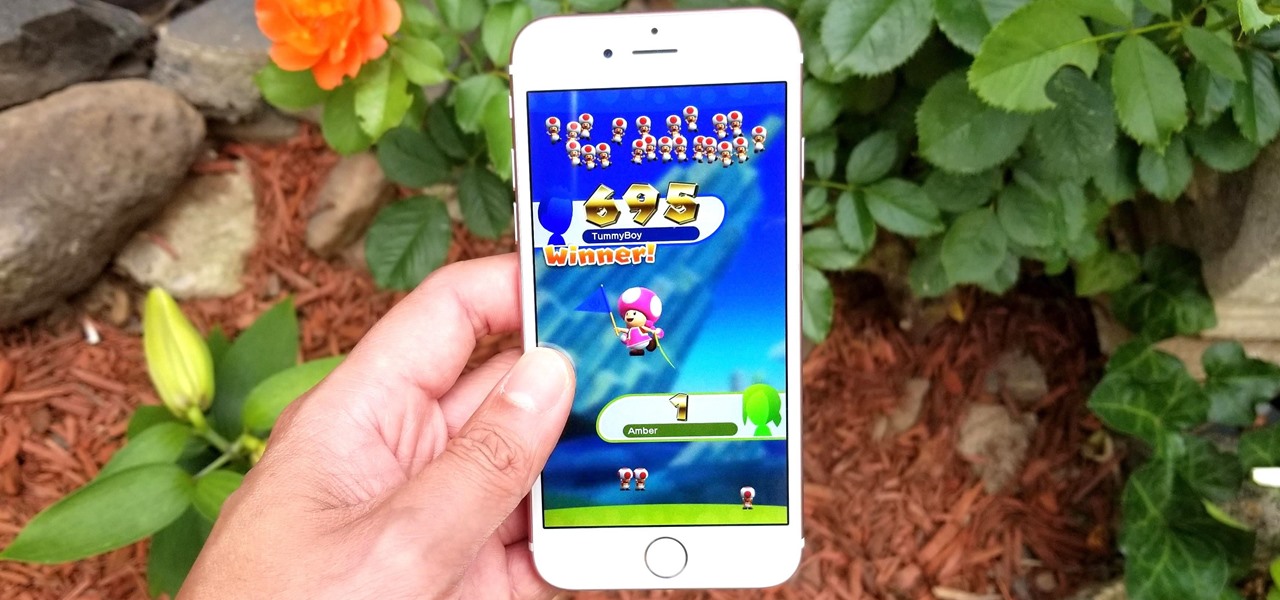
One of the best features in Super Mario Run is a multiplayer race that lets you test your skills against other players. Toad Rally, as it's called, pits you against other players in a battle for Toads. The more Toads you collect, the easier it is to build your kingdom and collect more rewards on your Android or iPhone.

Microsoft is bringing its developer incentive challenge Dream.Build.Play. After a five-year hiatus, Microsoft has announced the 2017 edition of the game development contest with the largest prize pool yet of $225,000.

The beta firmware for OnePlus devices lets you record calls from the stock Oxygen OS dialer, but this feature is never included in official updates. This is likely due to legal issues with recording calls in some jurisdictions, but thankfully, there's a way to get this feature without having to run beta software.

Now, you can prevent Donald Trump from building that idiotic wall from the comfort of your smartphone. Well, in theory, you can, thanks to a hilarious new gaming app called — wait for it — Trump's Great Wall.

Google's former driverless car boss Chris Urmson raised considerable funds to get his new startup company Aurora Innovation up and running. Axios initially reported that Urmson raised over $3 million to fund his brainchild in the wake of his Alphabet exit, according to an SEC filing.

Trimble is integrating its mixed reality applications into the DAQRI Smart Helmet to enable outdoor and on-site support for design, construction, and heavy industry as part of a collaboration the companies announced today.

3D modeling is usually a very long and complicated process. Manipulating the thousands to millions of vertices, faces, and triangles to the correct shape you want is just the first part of the process, and can take a good while depending on the level of detail needed. From there, you need to texture the model by applying the UV coordinates and placing the textures in the correct places. And all of this isn't even including the process of creating normal maps.

If you've ever been inspired to try out 3D modeling after enjoying computer-generated imagery in video games and movies, chances are you've checked out an paid applications like 3ds Max (previously called 3D Studio Max), or even free ones like Blender, then just went "No Way! It's way too complicated."

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Apple's plans for virtual, mixed, and augmented reality have remained a mystery for some time, but now we at least have some idea of what they're thinking about. UploadVR uncovered a patent showing a VR headset design that looks like a thick pair of sunglasses and utilizes an iPhone to provide an experience similar to the Samsung Gear VR.

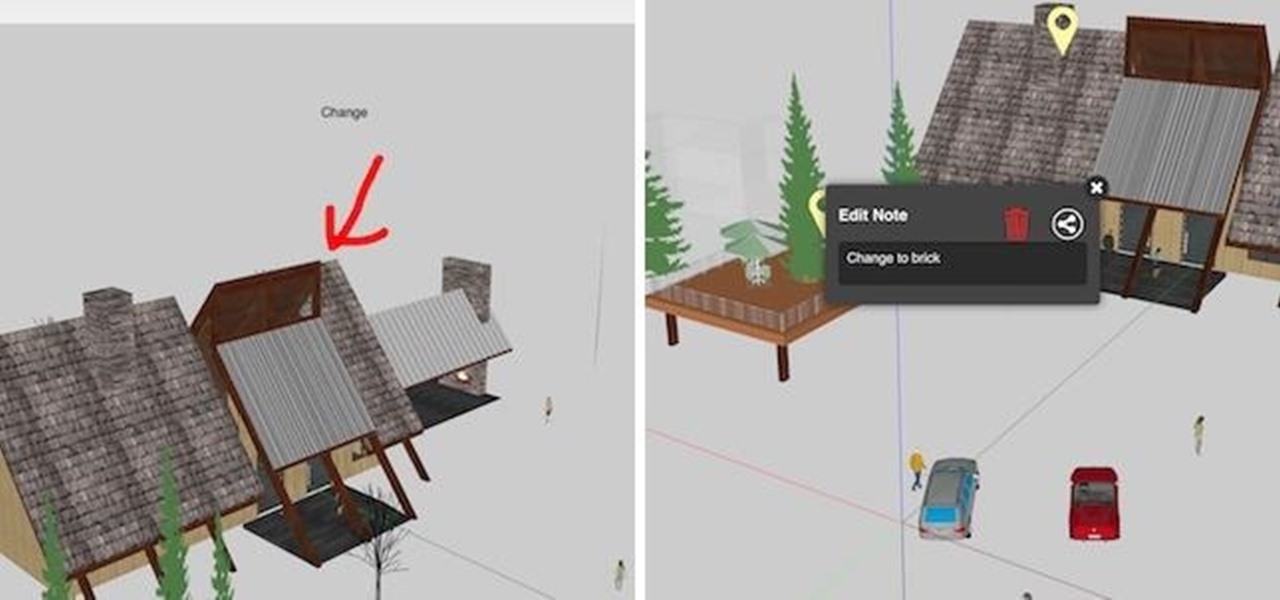
Would you like to know what your next house is going to look like? With the HoloLens, you can just plop a hologram down in an open outdoor area and find out.

We've got Google Maps to help us out when we need to navigate outdoors, but Google can only map out so many indoor locations without getting creepy. And that's where Stimulant comes in. This "innovation studio" built a HoloLens app that lets you map out an area, define locations, and use the headset to get instant directions to any defined location.

It's been known for a while that Google was opening up their Android N preview to OEMs, but we didn't think any manufacturers would actually take advantage. Well, we were wrong. Sony had just announced that Xperia Z3 owners will be able to install and run the N preview build. This is the first time a major manufacturer has offered Android previews on their phones. The preview build is only available for Xperia Z3's international models (D6603 and D6653), so those of you with T-Mobile's US var...

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.