A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!
Basically, this article is a true life experience writing from the introspective mind of the writer and do share more knowledge on how to deal with introvert lifestyle.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.
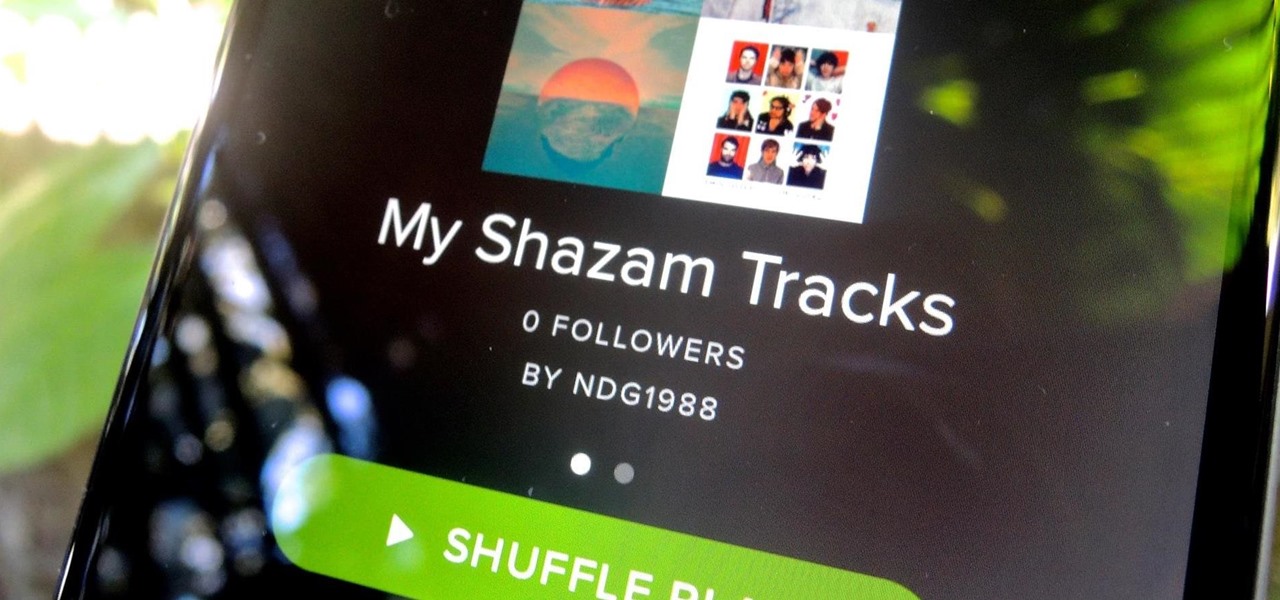
We recently showed you how to recover your Shazam history from Siri, which is a lot less intuitive than finding the songs you've tagged directly in the Shazam app. But with a subscription to Rdio or Spotify, there's no need to even locate your history. You can Shazam songs and have them automatically added to a newly created playlist titled "My Shazam Tracks."

Whether you're a serious, sweating athlete or just need to recover after a night of drinking, chances are you've replenished your body's fluids with a sports drink at some point. Those electrolytes aren't the only thing entering your systems, though. Sports drinks are sugary, sweet, and loaded with calories—but there's a way you can still recharge your body without ingesting the unhealthy additives.

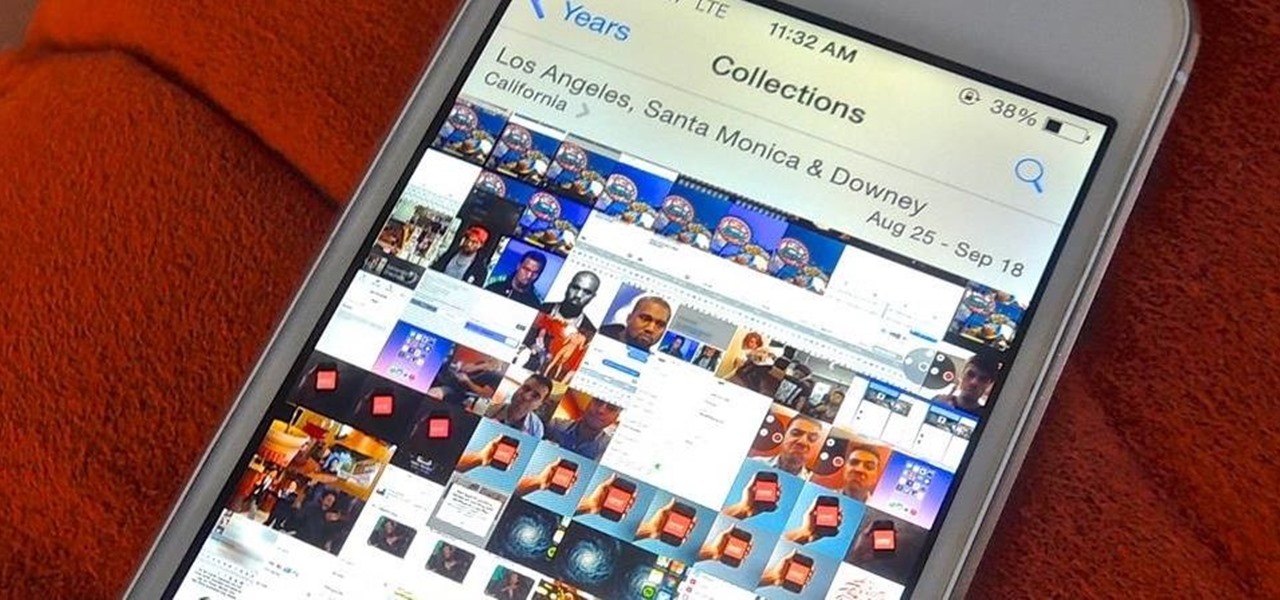
After updating to iOS 8, some of you have probably noticed that a lot of your pictures and videos are missing from the Photos app. Even if you were to restore your iPad or iPhone to your last backup, they would still be missing. But don't worry, that's just because albums work differently in iOS 8—all of your old photos are still there, just not as in your face as before.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

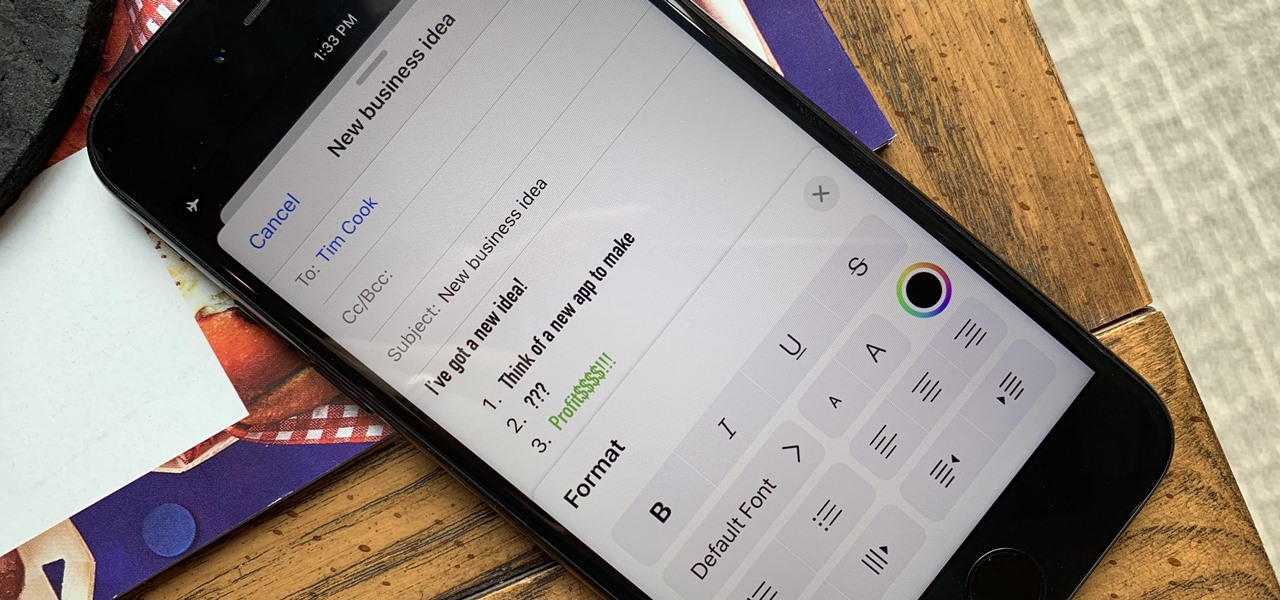
Staying on the move while managing email is a priority for many of us, from parents to students to business professionals. Seems that Apple had this in mind when improving the stock Mail application in iOS 8, which now includes swipe gestures that make marking messages as read/unread, as well as flagging and deleting, a whole lot quicker.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

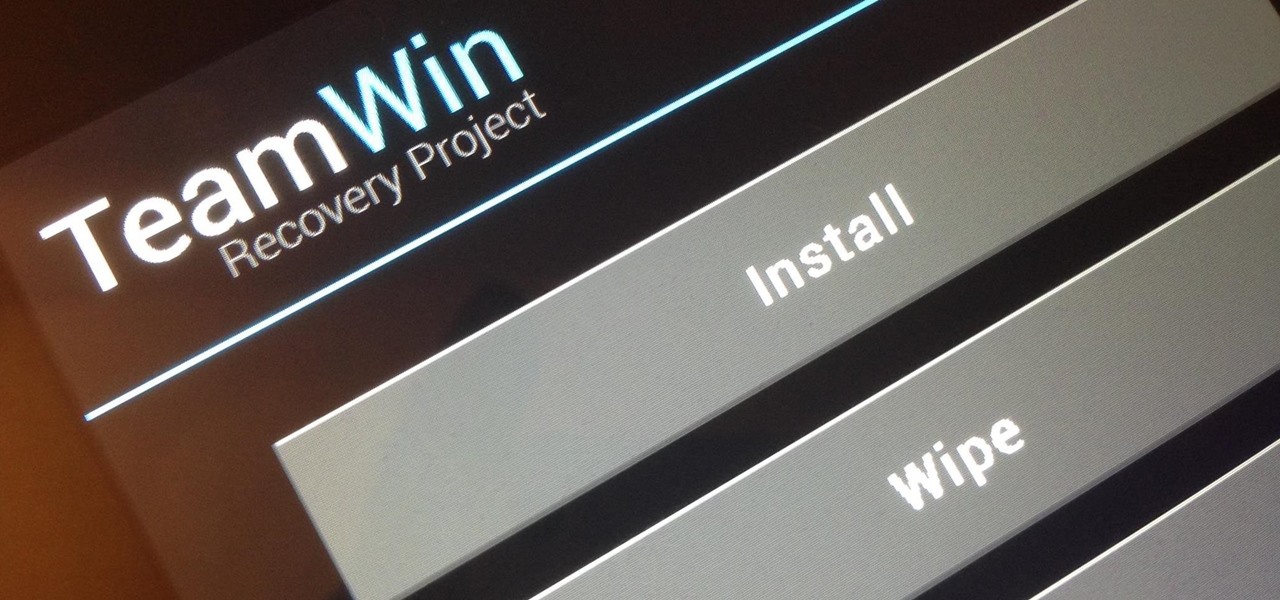
If MacGyver had a Nexus 7, he'd most definitely have TWRP installed. It's the softModder's Swiss Army knife for all things modding. You can flash custom ROMs, install add-ons, recover from a disaster, and much more.

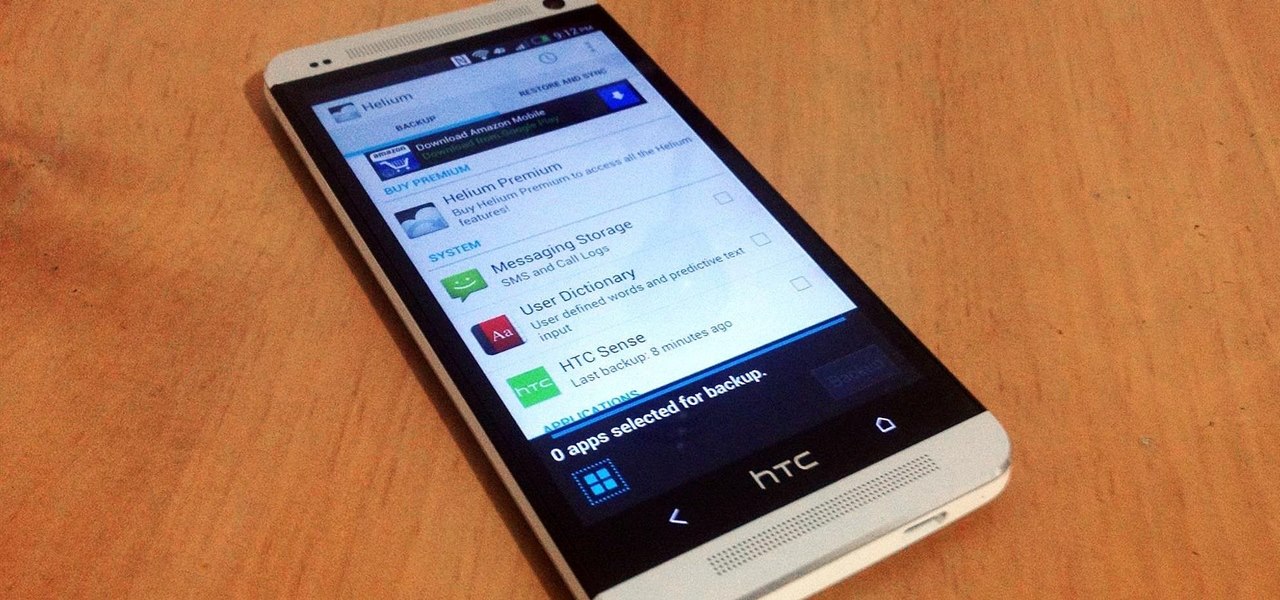
When you upgrade to a new Android smartphone like the HTC One, you can have browser bookmarks, Wi-Fi passwords, and other settings quickly transferred over from your old device using your Google Account backup. However, you'll still have to download apps individually from your Google Play list, and not all of your saved progress will be transferred over. Fortunately, there is a third-party app that will allow you to backup and restore your apps—with all their data.

Last month, Alexander Heit drifted into oncoming traffic after being distracted from the road. His sudden correction forced his vehicle to roll and flip over. He was pronounced dead at a local hospital shortly thereafter. All because of a freaking text message. He was only 22 years old.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

I had my wallet stolen a few months ago, and I knew I would never see it again. My biggest gripe was not the credit cards in there, since they're easily cancelled, but the gift cards. I had some pretty good gift cards in there, and there's no way to get those back.

See how to make a paper gun -- this six-part video tutorial will show you how to make a pistol paper gun. It's not that hard to make your own paper gun, so why not try out this paper pistol? You can even make paper bullets for the paper handgun.

See how to make a paper gun -- this four-part video tutorial will show you how to make a MAC-11 paper gun. It's not that hard to make your own paper gun, so why not try out this MAC-11? You can even make paper bullets for the paper MAC-11.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

Multitasking often seems like a good idea until you find yourself exhausted from all the back and forth between apps. In the latest software updates for iPhone, iPad, and Mac, Apple has streamlined the process for its Calendar and Reminders apps — making it easy to create and manage both calendar events and tasks from a single location.

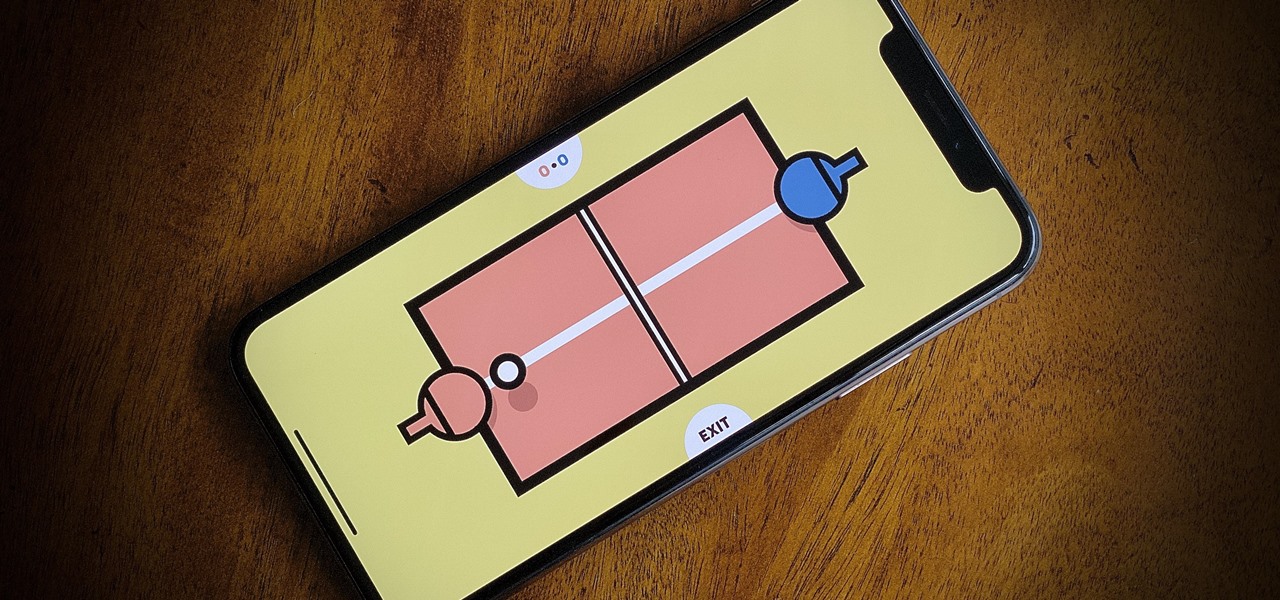
If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.

Although Mail didn't get a massive update in iOS 13, the new formatting and attachments toolbar makes it easier to stylize your messages and get quick access to files you'd like to send. It even includes the excellent document scanner built into iOS, so you can use your iPhone to turn a physical document into a PDF and attach it to your message — all from within the Mail app directly.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

Learn how to use the S-31 Lego gun from this video tutorial. This video shows how to make the Lego brick bullets, grease the S-31 Lego gun, load the toy weapon as well as how to fire it.

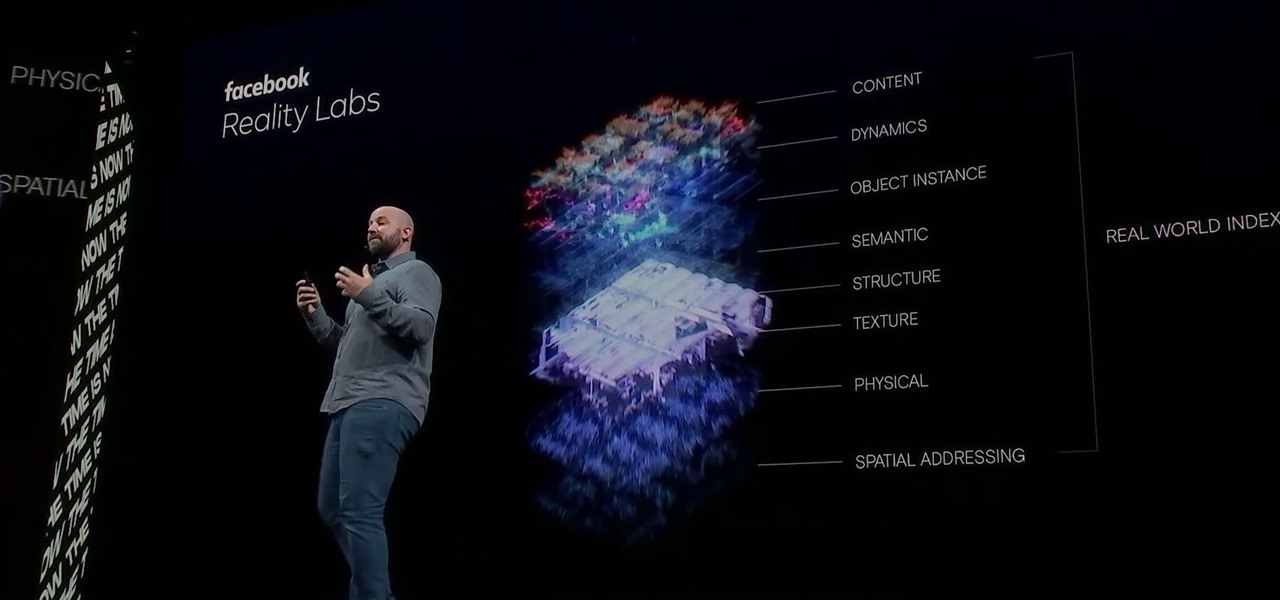
Facebook had a pretty big week in terms of augmented reality, with much of its news coming from the Oculus 6 keynote presentation. But Mark Zuckerberg's social media company found other areas of impact outside of Oculus 6 as well.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

So, it's Halloween time, and you feel like playing around with some augmented reality apps? Well, you've come to the right place — if you have an iOS device.

Some types of bacterial infections are notoriously tough to treat — and it's not all due to antibiotic resistance. The bacteria themselves are rugged and hard to penetrate with drugs.

A 'superbug' fungus is currently running riot in the hospitals of New York and New Jersey. This outbreak of Candida auris has contributed to 17 deaths in NYC, according to recent reports.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.

Last week's tech roundup featured iPhone 6 clones, an all-in-one sleep tracker, Xbox One updates, and other cool gadgets. This week, there's a lot more to show off, and a bunch of stuff that I need to get my hands on! Everything from app updates to putting stickers on your favorite items, I can't help but squeal at how much the "future" is right now.

To-do list and reminder apps are a dime a dozen on Google Play, so trying to find the right one for you could take hours as you sift through hundreds of similar apps and widgets. Well, search no more, as we've found one of the most well-designed and easy-to-use reminder apps out there.

A mustachioed Italian plumber collects coins and battles bullets, plants, fish, mushrooms, and turtles in strange environments to save a princess held captive by a crazy, spiked-shell, bipedal tortoise.

This most recent school shooting, one of the worst in history, has devastated our country. That such an act can be performed not by a begrudged child, but by one or more adults, is nearly unthinkable.

Computer crashes, fried hard drives, red rings of death, delinquent memory cards... nothing is worse than dysfunctional technology. In just a minute, your favorite and most used device has become the biggest headache of your life, frustrating you to the brink of madness. But what's worse than your electronics just giving up on you?

Dr. Parris Kidd explains how the dietary supplement GPC (GlyceroPhosphoCholine) can benefit the brain health of people of all ages, from children to adults. It can also help those recovering from brain damage.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.