You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

This Achievement Hunter video showcases the steps necessary to unlock the 'Bulletproof Windshield' achievement in the new L.A. Noire DLC: Nicholson Electroplating. This video helps to walk you through the process of stopping two cars before the driver gets out.

Working on filling your PS3 trophy collection with L.A. Noire achievements? This video is your guide to earning the Bulletproof Windshield trophy from the Nicholson Electroplating DLC for L.A. Noire. Watch and learn how a detective gets the job done.

'Enemies Among Us' is one of the longest, most involved quest in Dragon Age 2, and this walkthrough of it spans a whopping five videos. Stick with it, it's really goods stuff and great viewing even if you aren't stuck on this quest.
Build a web page to collect information from the user with the Wizard control, validate that information, and use the System.Net.Mail classes to send a confirmation email message. Check out this video tutorial to see all about making a 'contact us' page on a ASP.Net website.

LG's new KnockOn feature for the G2 wakes the phone up just by tapping on the screen twice, in lieu of using the power/lock button.

Need an outrageous and beautiful look for Halloween or attending one of Ke$ha's concerts soon? Then you'll definitely need to amp up your makeup game with lots of color and a Claire's store worth of glitter.

Callowlily is an urban artist who creates drawings of women who are society types with a dark edge. So you'll typically see her depict beauty queens with vampire fangs and blood splattered all over her dress. While these girls are more messed up than straightlaced beautiful, they do make great artistic inspirations.

Smoky eyes are all the same, right? Wrong. While it's true that 99.9% of smoky eyes consist of some form of smoked out black, brown, silver, and sometimes purple, you can make your smoky eye interesting by adding an unexpected pop of color.

Hey, coffee drinkers—your morning cup of joe is killing your metabolism.

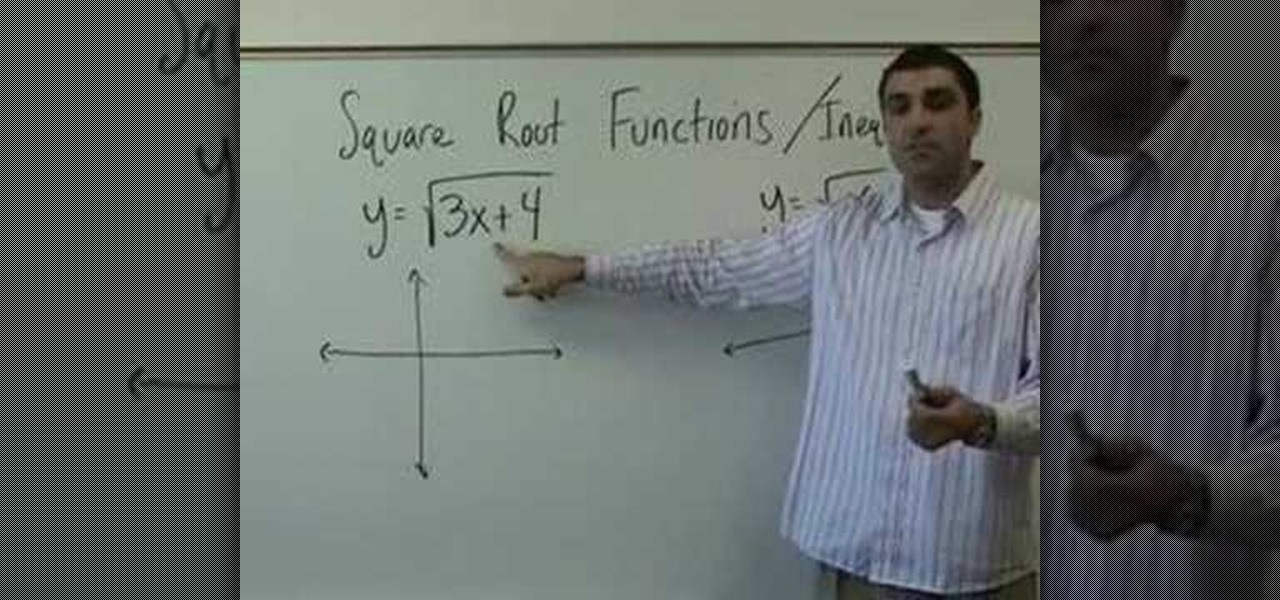
On Yay Math, Robert Ahdoot, founder of Yay Math, will show you some square root functions and some inequalities. He begins with the problem y=x². Then he makes a sketch with two intersecting lines in a t shape. The problem is illustrated by a curved U shape, the U's bottom resting on the horizontal bar, which represents x, while the center takes the vertical line. The vertical bar represents y. This U is directed up because the x² is a positive number. If the number were negative, the U would...

HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

When it comes to resistance to the elements, Samsung seems to believe in the old saying "if it ain't broke, don't fix it." They've carried over the IP68 rating under IEC 60529 that was first found on the S8 all the way to their tenth-anniversary flagship, the Galaxy S10. While this certainly sounds great on paper, it's natural to want to dig a little deeper and find out what the rating means.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

In Call of Duty: Modern Warfare 2 (COD4), there are titles that you can unlock for use on your Callsigns. If you want to know how to unlock all of the titles, this three-part video list them all and how to achieve them.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.

OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

Fifty-four percent of Americans 18 and older drink coffee every day, and why not? With 100 milligrams of caffeine per six ounces of drip coffee, it's just the morning beverage to wake you up and kickstart your day. You can feel the caffeine surge through your body like the Holy Ghost, making you aware, focused, and ready for action.

Coffee! It's so amazing that J.S. Bach wrote a comic opera about caffeine addiction. Meanwhile, more than half of Americans 18 years or older start their day with a cup of the hot stuff. Most of us take coffee for granted, but it's a bean that can surprise you. Read on to understand more about coffee and how to take advantage of all that it offers.

Jailbreaking gives you root access to the iOS file system, allowing you to install third-party apps and tweaks on your iPhone that aren't available in the App Store. It opens up a whole new realm for what your device can do, but it can also cause instability across the system and can dissuade you from getting future updates from Apple that have important features, bug fixes, and security enhancements.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Wonder Woman has always been a Halloween and cosplay staple. It's a costume that's both dependable and stylish — just like the Amazon who wears it. This year's reprise with Gal Gadot offers a fresh take on the old standby, with more muted colors, a tougher demeanor, and a decided lack of stars or stripes. Tahnee Harrison from CineFix's DIY Costume Squad has come up with a compromise between the old and new costumes. It's got the cut, styling, and details of Gal Gadot's 2017 costume, but the b...

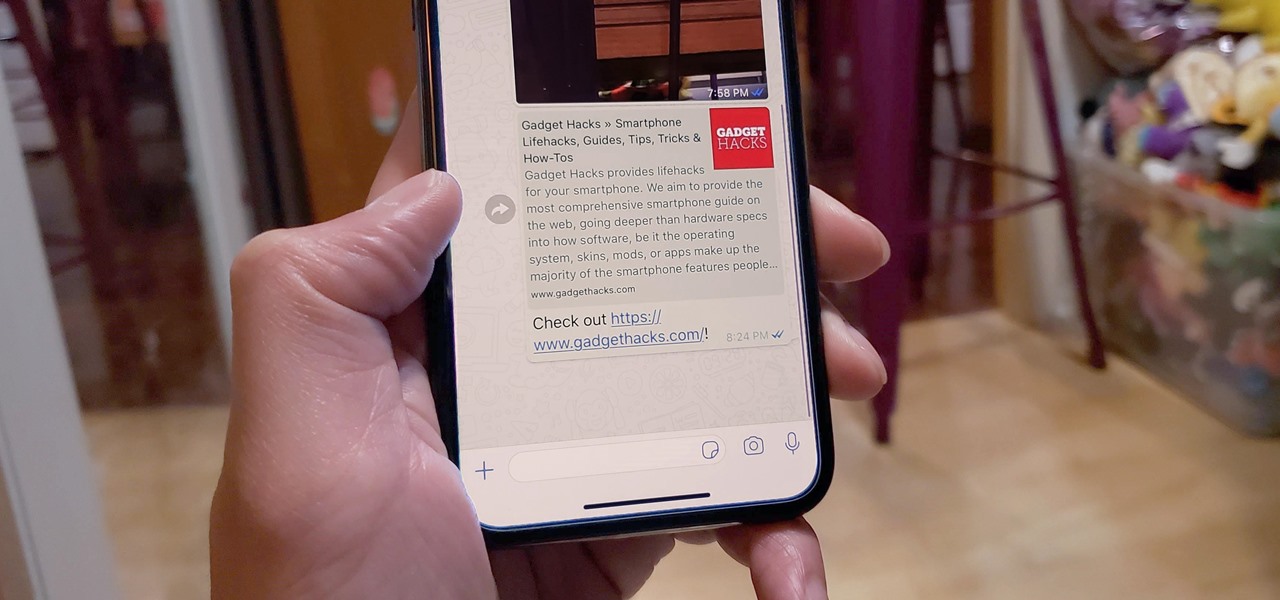
When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists.

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

This holiday season, give yourself a gift that will keep on giving: a new web development skill. Whether it's to secure lucrative freelance work in the new year, bolster your résumé, or have fun with some frankly outrageous discounts on online course bundles right now (up to 99% off), there's nothing better you can do with your free time. Your future (pro coder) self will thank you.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Your smartphone stays with you everywhere you go, so it's only a matter of time before you spill coffee all over it or drop it on the ground. For some of you, it has already happened, perhaps even multiple times. That's why we thought it was important to find out which flagship phones are the most life-proof.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

Learn how to create your own Valentine's Day card with Bruce Blitz. All you'll need is a paper, pencil, marker, colored chalk or pencils, and an eraser. Using your pencil, draw 2 circles, one with curved guidelines to have the face turned to the left, and one with straight guidelines to have the face looking straight ahead. You want to be able to draw curved guidelines when it’s time to create your Shy Guy, because he will be looking down. Starting with a fresh sheet of paper, draw another ci...

Keep on cartooning with host Bruce Blitz as he shows you how to draw a proud girl with pigtails. All you need is a pad of paper, pencil, marker, colored chalks or colored pencils and eraser. Using a pencil, draw a bean shape for her head. Use your marker to draw an upside down U, down low on the face, for her nose. Draw 2 upside-down U’s for eyes, eyebrows going up and a large, proud smile. Draw a big ear on her right side, and go over the pencil lines around her face. Starting at the center ...

The Australian government has a dysfunctional history with video games. Any regular Yahtzee Croshaw follower can attest to that. The Parliament has established a series of unfortuante regulations that make games both highly taxed and overregulated in price. Bringing any goods all the way to an island in the bottom of the world is expensive to begin with, and new games in Australia can tip the scales at $80 or more.