
What does it mean when a software company obsessively focused on innovating the way we use our mobile devices to see and communicate with the world adds virtual voice agents? Possibly e-commerce magic, with a powerful layer of augmented reality.

Apple does not provide a native way to lock apps on your iPhone behind Face ID, Touch ID, or your passcode. For a long time, we've wanted that option for improved privacy and security, but Apple does allow developers to use its authentication protocols. Apps like Messenger, Outlook, and WhatsApp give the option to lock them down, but for the apps that don't, you can force it with a little time and effort.

This week, developer Niantic began rolling out a new feature called AR Mapping to Pokémon GO that has bigger implications on the realism of augmented reality in mobile gaming and beyond.
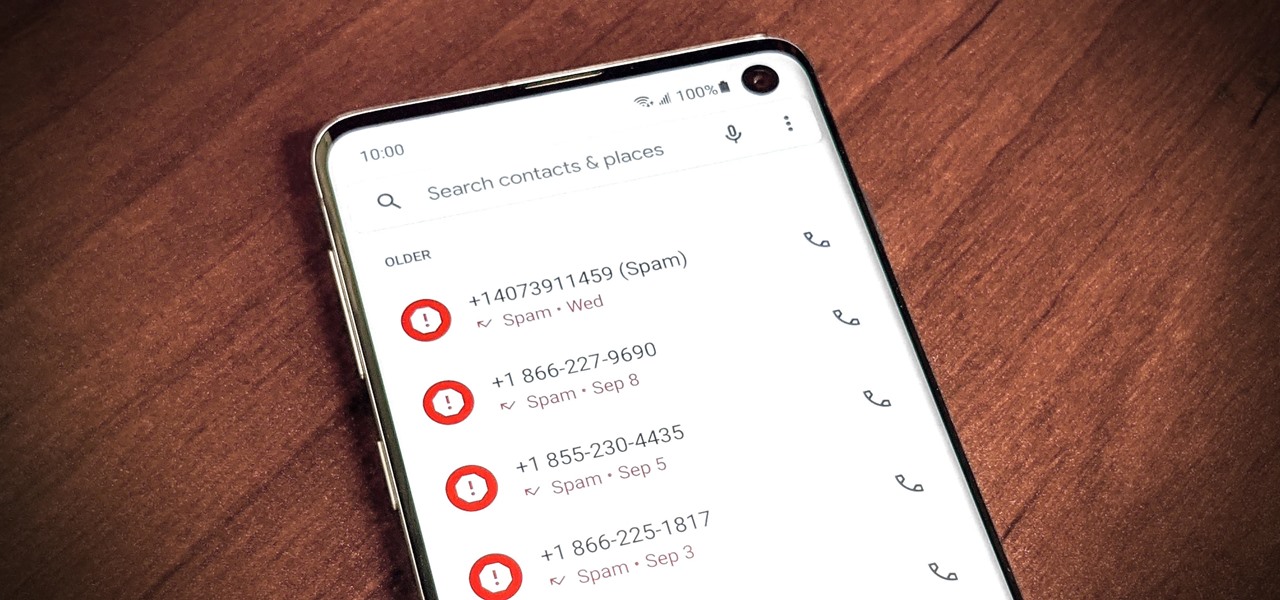
As if telemarketers weren't bad enough, now we have robocalls and spoofed numbers to deal with. Many of us get a least one spam call per day, if not much more than that. Google's Phone app has always been great at managing these calls, but it's been exclusive to their Pixel phones — until recently, that is.
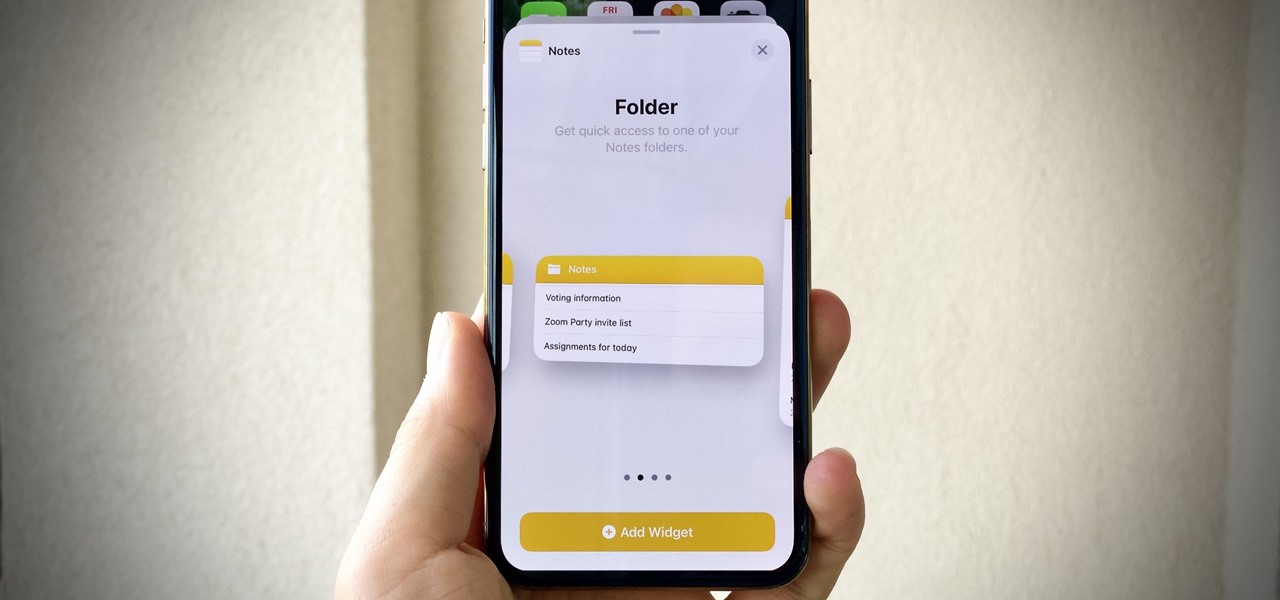
For a built-in app, Notes works pretty well and can stack up against some of the best third-party note-taking tools. Apple continues to update it with each iteration of iOS, adding new features and improving existing ones to make jotting down your daily thoughts a smooth and effective experience. With iOS 14, there are twelve such changes that we think you're going to want to know about.

"What's your Wi-Fi password?" That's usually the first thing guests ask for when you have them over. You tell them the network name, then try to explain your complicated hacker-resistant password, which becomes a whole ordeal. But there's a better way to do it, which doesn't rely on using the same mobile OS as your guests.

You may be wondering what exactly makes the Pixel 4a's camera so great. Compared to its predecessor, it has the same Sony IMX363 sensor and no additional hardware. Well, beyond stellar image processing, it also has several great new features that Google has added since they released the Pixel 3a last year.

Many apps on your iPhone want to use your location, most of which are for valid reasons. But some apps can function perfectly fine without location permissions, while others have no business even requesting it. If you want to be more selective about which apps and services you give away your coordinates to, the best thing you could do is start from scratch.

Instagram makes it easy to view a public account without that person or business knowing unless, you know, your finger accidentally slips and hits the like button on a post. Aside from that, if you're careful, you can browse anonymously through an account without anyone noticing — only you can't do that with Instagram Stories.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

If you've jumped on board HBO Max to watch more than just HBO's content, such as DC films, Looney Tunes, Turner Classic Movies, Cartoon Network, and movies from Warner Bros., there is a downside to HBO's improved service. Namely, you cannot use it on all of your devices yet. The most notable omission is Roku players and TVs. But there are workarounds you can use until an official app comes out.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a participating website or put yourself out there and sell the iPhone on your own. It's all about what's best for you.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

On April 26, 2019, Sinemia posted a note on its website stating it has ceased all operations in the United States. It's not known if it continues to work in other countries or if US users will be getting any refunds, particularly, for annual subscribers.

MoviePass was once the best subscription service on the market for getting cheap movie tickets. For the price and the number of films you could see and save money on, it was unbeatable, but recent changes to the service have made it less enticing. While it still works well for some users, others may have to rely on other options. Personally, I'm leaning toward the latter.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.







































