Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

When it's all said and done, it doesn't really matter who did it first — the more important question is who did it best. Still, it's nice to know who's really responsible for groundbreaking innovations in the smartphone space.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.

UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Below, we've saved the early rumored information on the Axon 9 for posterity.

Waze is the go-to navigation app for millions of drivers, and it's easy to see why. Benefits such crowd-sourced traffic data, police trap locations, and road work avoidance are just the tip of the iceberg. It can almost be overwhelming, but with these simple tips, you'll master Waze and start navigating like an expert in no time.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.

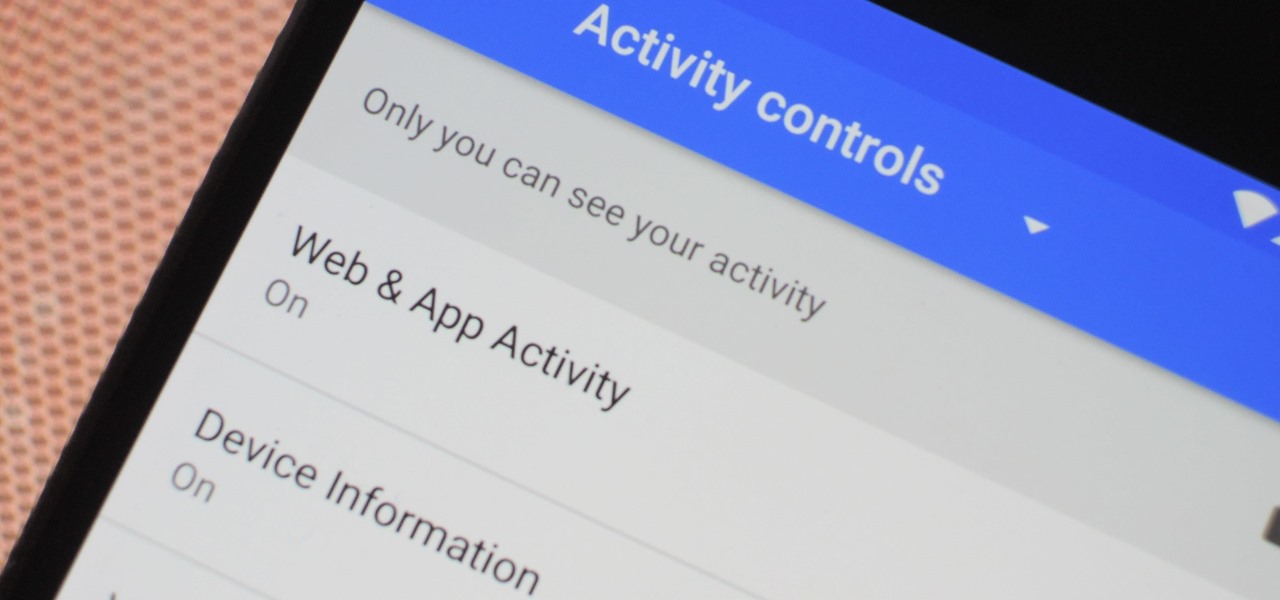
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.

While it is easy to create and maintain your compost pile, you can enjoy it more knowing a few basic tips.

In the tech world, when you're a small startup going up against the Goliaths and their massive marketing budgets, you're forced to find and produce something almost magical to help your product stand apart from the rest. And that's exactly what Occipital Inc. has done with their Bridge headset.

When it comes to global warming, most of us think of carbon dioxide emissions. While carbon dioxide is the most important greenhouse gas, carbon dioxide emissions have stayed constant for the last three years. On the other hand, methane, the second most important gas, has been steadily rising since 2007.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

One of the big hurdles when equipping vehicles with sensors for autonomous driving is the cost. For example, the Light Detection and Ranging (LiDAR) sensors that power many versions of self-driving car technology are pricey, currently ranging from around several thousand dollars up to $85,000 per sensor—and vehicles often need multiple sensors to see enough of what is going on around them to drive safely.

And so it begins... CES 2017 is upon us! This is a very exciting time for those who are looking out for the newest innovations and releases from the world of technology. I said this was going to be a fun week, and here we start it with a bang from smartglasses developer Osterhout Design Group (ODG).

The coming year promises to be a good one for those of us watching the augmented and mixed reality world. And the Consumer Electronics Show (CES), starting Jan. 5 in Las Vegas, Nevada, for its 50th year, is bringing 2017 in with a bang—we're expecting a ton of great announcements on the horizon.

If you've been following NextReality, you've surely seen me around, or at least have seen my articles. My name is Jason Odom, aka Subere23, and it's about time for a formal introduction.

When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...

The big night is less than a week away, so how do you not have a costume yet?! In my world, Halloween is the night of all nights. It's the only day of the year when it's socially acceptable to dress and walk around like an insane person, eat too much sugar, and scare the hell out of total strangers. What's not to love?

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

Virtual reality holds the promise of electronically visiting distant places we'd otherwise struggle to reach, but that teleportation-esque ability isn't possible without the right content. YouVisit created a platform that makes it easy for almost anyone to create immersive 360-degree experiences so we can map our lives and see the world through the eyes of our fellow humans.

When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.

Several technologies seek to change the way we perceive our reality, whether that involves entering a virtual world, augmenting an existing one in a realistic and interactive way, or somewhere in-between.

The spice selection at Trader Joe's is both inexpensive and truly top-notch. According to their site, they deal with some of the highest-quality spice manufacturers in the world and, in working with them directly, they eliminate hidden costs spent on promotions, brand-building, and advertising. This allows the customer to experiment with new flavors and build up their spice rack—without the usual limiting factor of high cost. If you don't have access to a Trader's in your culinary neck of the...

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

Coverage for the 88th Academy Awards, aka the Oscars, will air live this Sunday, February 28th at 4 p.m. PT (7 p.m. ET). The ceremony itself, hosted by Chris Rock, is set to begin at 5:30 p.m. PT (8:30 p.m. ET).

Up until the last 15 years or so, watching the commercials during the Super Bowl was arguably more exciting than the game itself. Super Bowl XXIV featured the San Francisco 49ers blowing out the Broncos, 55-10, in the worst Super Bowl beatdown of all time. The game might not have been that exciting, but the commercials sure were.

The Microsoft Surface has been the go-to device for many professional artists since its initial release back in 2012. Since then, the Surface line has continued to offer customers a portable, high-powered machine that's a near perfect value for both casual and professional artists. And the Surface Book is its best model yet—a full laptop convertible with a detachable screen and a dedicated GPU.

Sooner or later, you're going to come across a person at work that you don't like—or someone that doesn't like you. This can result in uncomfortable tension, insulting gossip, and a disrespectful attitude, to name just a few of the negatives. But it doesn't have to be that way. The next time you're having a workplace conflict with a particularly challenging coworker, the best thing you can do is keep your mouth shut, and here's how to do it.

Lemons, limes, and even oranges compliment a wide variety of both food and drink: gin and tonic, poached salmon, shrimp cocktails, fajitas, and so on. And you can easily step up your hosting game by making citrus garnishes: a presentation that is both elegant and interesting.