Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

If you're having a "Netflix and chill" night, the last thing you want to worry about is finding something to watch—after all, you have better things planned for the night.

Downloading YouTube videos for offline use to watch later has always been a problematic endeavor. Dedicated third-party apps don't last long in the App Store, web-based converters aren't very functional on mobile, and rogue apps outside the App Store are tricky to sideload and open up the possibility of vulnerabilities. But that doesn't mean you still don't have a few good options.

If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing up for the new streaming service, let's take you through all the changes and features you should know about before doing so.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

With only a few days until Apple Watch preorders begin, and just a couple of weeks until its official release, the biggest question in Apple Land seems to be: "Are you going to get an Apple Watch?"

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

Are you someone who always struggles to wake up in the morning, no matter how much you've slept? For most, the thought of getting out of bed any earlier sounds horrific. Yet dragging yourself out of bed and towards the coffee maker a few hours earlier each day can have benefits you've never realized. Here are six reasons that make a compelling case for ending our bad habit of sleeping a little too long.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Coffee mugs: nothing proliferates more quickly in my kitchen cabinets. People are always handing them out as gifts or as swag, plus I always seem to find a vintage model or two at a garage sale that I'm compelled to buy. I used to do a yearly purge of my excess muggage, but it turns out it's a good idea to hold on to one or two extras.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Everything you thought you knew about cooking pasta is wrong. When I took cooking classes in Italy, they taught me to bring a large volume of salted water to a rolling boil, add a drop of olive oil so that the noodles wouldn't stick together, and wait several minutes until it was al dente (which literally means "to the tooth," i.e., firm and not mushy when bitten).

If you've ever searched for a new job online, chances are you've been completely overwhelmed by the process. Clicking through pages and pages of semi-relevant job postings, sending out hundreds of emailed résumés, and filling out applications is tiresome and dull.

Whether it's spotty data coverage, bad customer service, or a high monthly bill, at some point many of us consider changing carriers. The problem is, we often don't want or need to change our devices. Since it's now legal to unlock devices to bring to new carriers, getting devices switched over is doable, but it's pain going into carrier stores and dealing with their constant upselling.

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Attention all veterans and active-duty military personnel—this coming Tuesday, November 11th, is Veterans Day, that time of year where the whole country thanks us for our service. For the most part, a simple thanks will do, but some folks like to go above and beyond and give us veterans free or discounted meals and discounts on merchandise in stores.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Apple is notoriously cryptic when it comes to the reveals of its new products, and as usual, they've kept us guessing about the release of the iPhone 5 (or "New iPhone?"). It's expected to be officially revealed on September 12, and rumor has it that sales will begin on the 21st. Though the whole world seems to be anxiously awaiting the announcement, there has also been some controversy surrounding the iPhone 5's production. With the high number of suicides and poor working conditions at Foxc...

Tech tends to move forward without looking back, but that doesn't mean new is always better. One feature that dominated mobile phones in the late '90s had made a comeback thanks to Apple, and you can take advantage of it on your iPhone when making calls.

On your iCloud Mail account, you can easily use subaddressing to create hundreds of new iCloud email addresses to give to companies and other parties, all of which go straight to your primary iCloud email address's inbox. The problem with these types of alternative email addresses is that you can't ever respond to emails with the plus tag intact. But Apple has another alternative for you to start using.

When Steve Jobs introduced the first iPhone, he pointed out that the biggest problem with physical keyboards on mobile phones is that they're always there, whether you need them or not. Now, 17 years later, a new company is bringing us full circle, giving us the best of both worlds: a physical keyboard for iPhone that can disappear whenever you want.

There's more than one way to get free credits and discounts in the Google Play Store for apps, games, books, movies, in-app items, and other Play Store content. You may know a few of them — but some of these may surprise you.

There are a surprising number of hidden features in your iPhone's Phone app, from secret dialer codes that provide info or perform actions to special characters that dial extensions automatically. However, there's one little-known trick every iPhone owner should know when using the Phone app for calls — and it's the simplest and most useful of them all.

One of Android's headlining strengths has always been how it handles notifications, and things have only improved with each new update. More recently, Android has improved notification permissions, so you'll have a choice of whether to receive notifications as soon as you first open an app. It's easy to permit or deny these permissions, but it's just as easy to reverse your decision.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

The beginning of autumn has delivered a number of new augmented reality developments, and we're on top of it.

The legal battle between Epic Games and augmented reality startup Nreal isn't cooling off anytime soon.

Snapchat parent company Snap has opened up its war chest to acquire yet another company that will play a role in its augmented reality ecosystem.

Brands are increasingly adopting augmented reality to promote their products and services, and they have multiple paths for bringing AR experience to their audiences.

While Snap may eventually compete with Apple and Samsung in selling smartglasses to consumers, today it is helping them achieve their business objectives via augmented reality.

Not all Kickstarters are created equal. Some take forever to get their products to supporters, and when the product does arrive (usually much later than promised) it's often very rough around the edges.

Just when everything seemed settled over at Magic Leap, it turns out that the internal tumult is still in play.

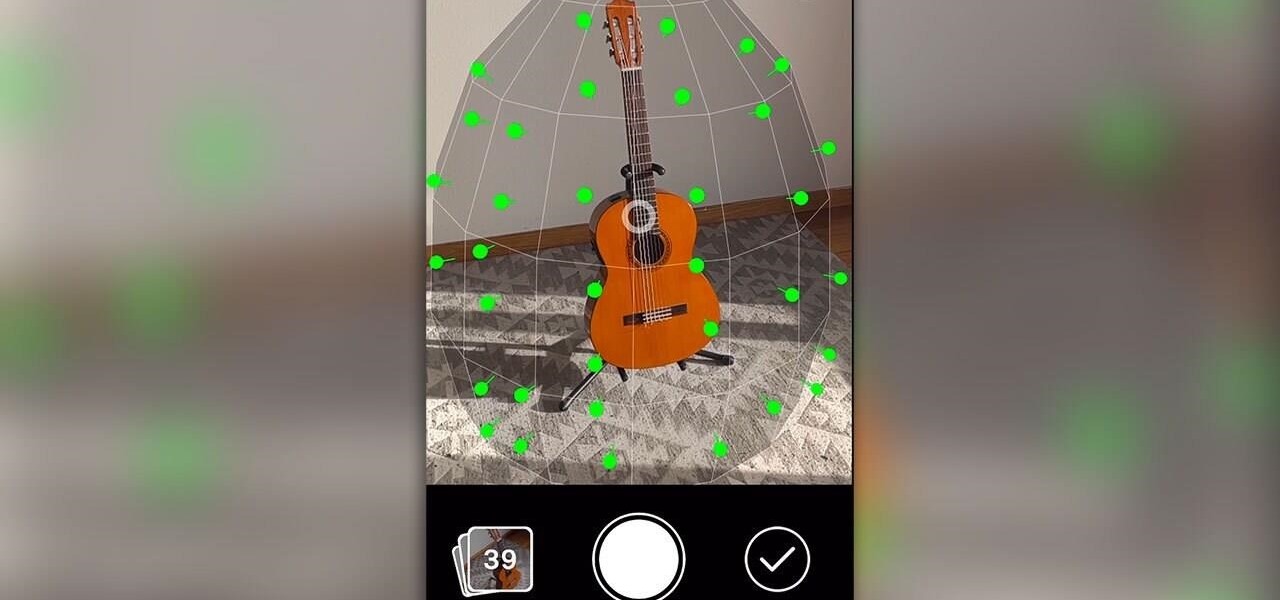
One of the more exciting augmented reality announcements Apple made during its WWDC keynote on Monday came in the form of Object Capture, a new 3D scanning feature coming to macOS Monterey.