Sure, you've probably seen a million YouTube videos that feature the impressive schemes of 2,000-sided modular origami balls that seem to defy gravity as well as patience. But sometimes the simplist origami craft is the most striking.

This video is about professional/business letter folding and mailing. Before starting this process your hands should be clean and dry so as not to ruin the look of the letter. To fold the letter correctly, you must take the bottom 1/3 of the letter and fold it upwards towards the letterhead - it should be folded about halfway to the top. Then crease the fold. Next you fold the top down and crease that fold also. To mail, you must place the lettehead, head down, face forward into the envelope....

When you start a blog of your own you will want to make sure you protect yourself. Even before your blog takes off you will want to research trademark law when you attempt to register for a domain name.

This is indeed a great instructional video on how to make a paper wind chime. The products you need to make paper wind chime are mixing grinder, scissors, paper, business card, pencils and a thread .First you draw a circle using the cup on a paper. Cut a few circles out of the paper. Draw x in the middle of all circles. Then make a hole in the middle of all circles. Now place the circle in side the grinder and let it rotate fast. now you can add colors as you like. Similarly you can make all ...
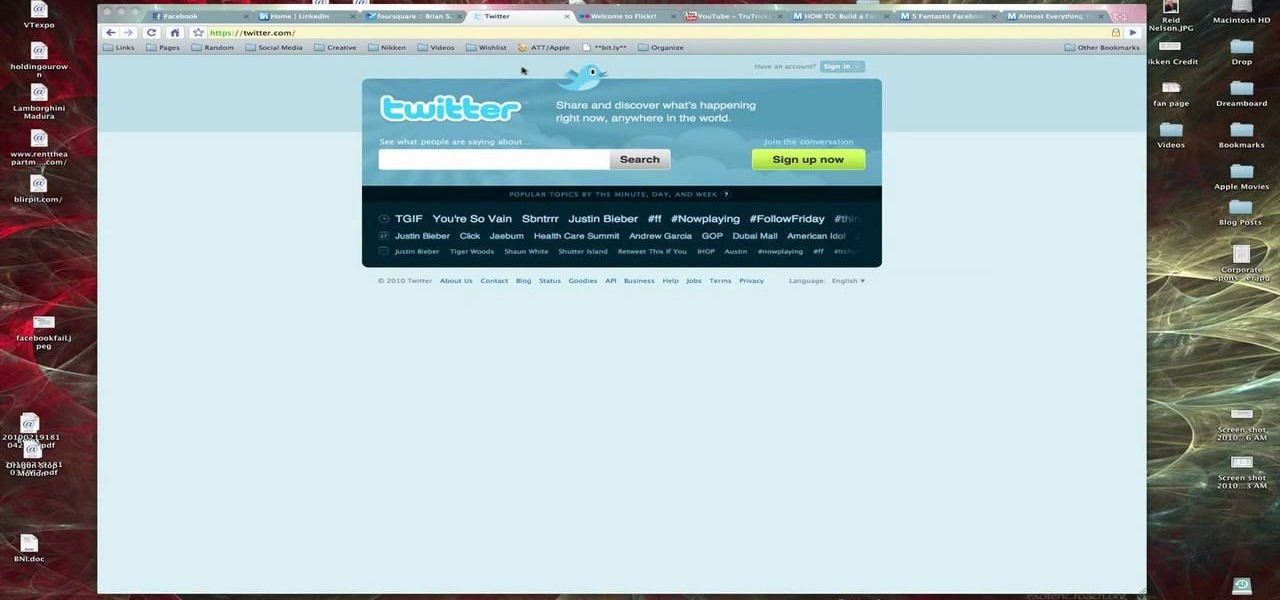
In this video, Brian from Trutricks shows us how to create a new Twitter account. First, go to Twitter and click on the "sign up now" button. You will now be brought to a new page where you can choose your user name and enter your email, password and full name into the information boxes. Once finished, click "create account". After this, you will be able to follow people you want as well as have other people follow you. Once you are ready to tweet you can type whatever is on your mind in 140 ...

Need to make an newsletter for your company or business? It's really not that hard to do, if you know a little bit about HTML coding. Ryan Quintal and the Email Dance House sits you down and shows you how easy it is to make a custom HTML email from design to Constant Contact.

When you need a website to showcase your product or service, it can be quite confusing. Follow these easy steps to gather everything you need to have a successful website. Start your search for a domain name in the domain name registrar. (Example: www.companyname.com) Rent space from a hosting company to hold the files for your website. Set up an email account for your company. Create the content for your website (example: products, prices, services, etc). Get internet security to protect sen...

Gigafide explains that with so many different social networking sites, it is hard to keep information up to date on all of them. He first introduces TweetDeck, an amazing desktop application that allows a user to update information for their Twitter, Facebook, MySpace, and LinkedIn accounts. If you don't want to go through the hassle of installing TweetDeck on your computer, there is HootSuite, a web application that allows you to do this and if you're interested in keeping track of much more...

This is one of the best hacks for Happy Island, so make sure to try it out before it's patched! With Cheat Engine, it's easy to do this coin and experience hack.

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show demonstrates how to make popular Japanese dishes.

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. This video demonstrates how to make Katsudon (Tonkatsu Deep Fried Pork and Egg Bowl).

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. This video demonstrates how to make kakiage soba (mixed tempura soba noodles).

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. Learn how to prepare Japanese Ichigo Daifuku, aka strawberry Daifuku. This is a Japanese dessert.

Arc welding is a type of welding that uses a power supply to create an electric arch between an electrode (electric conductor) and a base material to melt the metals at the welding point. While you can certainly purchase a welder for your car shop or jewelry making business, you can actually save some money in that department by making your own.

New to the pranking business? Well, this video tutorial ought to start you off good and proper. Here, you will learn how to perform the liquid pen prank. Maybe it's called something different, like water pen prank, but the point is to remove everything from the pen, then fill it with water and return the cap. Wait and watch as someone opens the pen lid to spill water all over their important document.

So you want to party with celebrities. Whatever you do, don’t cry. You won’t just look silly—you’ll look unstable. Follow these steps to get you one step closer to hanging with the stars.

Check out this instructional dance video that demonstrates how to dance the Cha-Cha with Jules Helm. The Cha-Cha (or Cha-Cha-Cha) is a dance from Cuba popular among ballroom dancers. Learn to dance the cha-cha, the moves and steps, in this ballroom dancing video.

Check out this instructional dance video to learn how to dance the mambo. The mambo is a popular dance of Cuban origin, a favorite in ballroom dancing competitions. Learn to dance the mambo, the moves and steps, in this ballroom dancing video lesson.

Pronunciation is key to learning any new language. Before diving into the vocabulary and basic phrases, a good approach is to listen and try and get your aural perception honed in. A new word or phrase, like "je m'appelle" in French, is awesome to learn, but it's important to learn it correctly: that starts and ends with pronunciation.

In a recent poll taken by an online recruiting company revealed that 37 percent of all hiring managers do not hire someone based just on the way they dress, more than half said they'd hold it against a candidate if they hadn't worn a jacket and seventy percent said that they wouldn't hire anyone wearing jeans, a leather jacket or a polo shirt to the interview. The rules for office dress code have changed, more and more companies offer their employees a business-casual dress code which makes i...

They say you have to be in the right place at the right time... how about an elevator? If you happen to run into your ideal employer or business partner, in an elevator – or anywhere else for that matter – you'll have about 30 seconds or less to wow them. Here's how to do it.

Proper phone etiquette is important for many businesses and career paths. Learn how to practice professional phone etiquette from a communications specialist in this free business video.

Learn how to say the names of the parts of the head in French

Learn how to say the names of the parts of a motorcycle in French

Learn how to say the names of the parts of the house in French

Every home is a little different, and for a smart home app to work, it has to be able to be customized to work with each person's unique setup. With the iPhone's Home app, everyone can set up a smart home just how they want, including the number and names of rooms, and where those rooms are in the house.

The newly enhanced focus from Magic Leap on enterprise, announced on Tuesday, also came with a few companies opting to weigh in with their experiences developing for the platform.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.

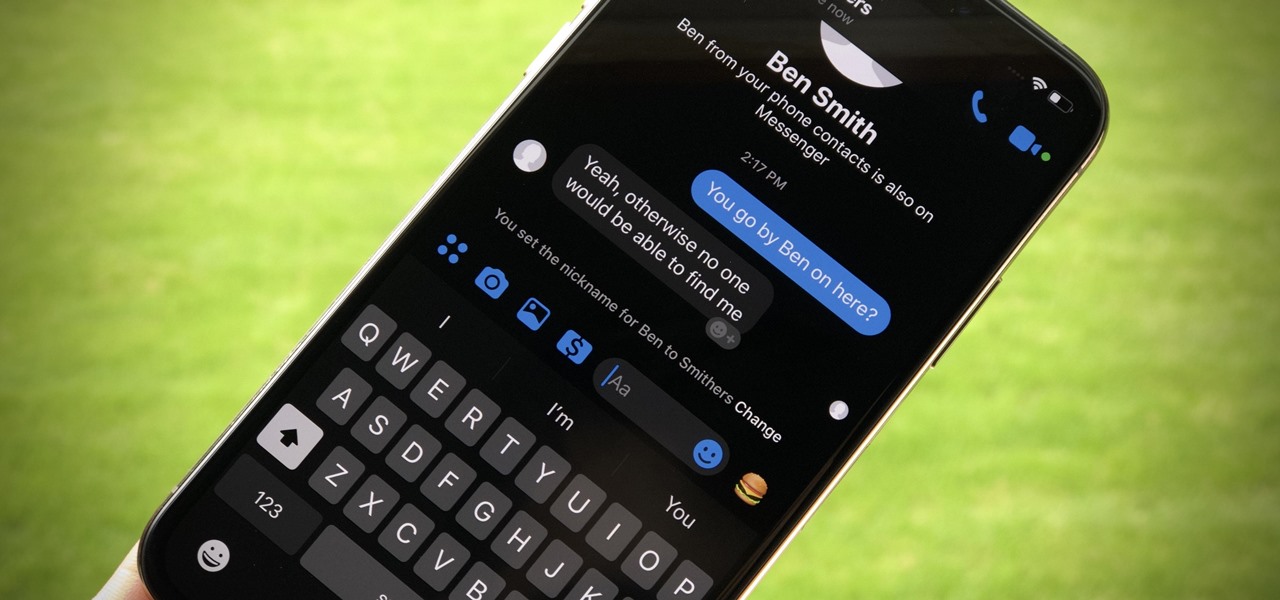
For the most part, people use real names on Facebook. That's all fine and well for keeping tabs on those you know, but it can make friendly Messenger chats feel oddly formal. Skirt around this stiffness by giving your friends nicknames in Messenger for Android and iOS, so your conversations reflect the way you and your friends communicate in real life.

The annual Augmented World Expo (AWE) typically packs the front page of Next Reality with new products and services from companies in the augmented reality industry.

The augmented reality industry has a bright future built on innovation and growth, but that doesn't mean we can't look back at the close of the year to see what the industry has accomplished from a business perspective.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Deep down inside, Android is really just a fork of Linux, the popular open source desktop OS. You can see traces of its roots everywhere, and this lineage still holds a certain appeal with many Android fans. If you're in that boat, you'll love the newest notes app we just found.

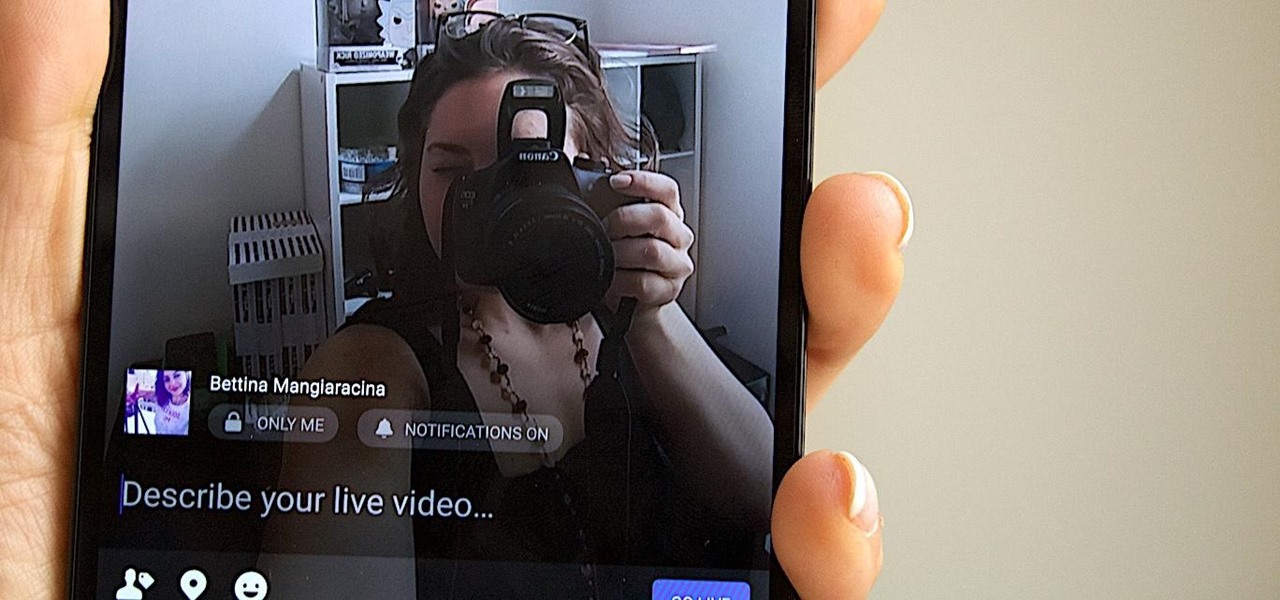
It looks like "going live" is another thing we all have to figure out how to do to remain relevant in this very Facebook-driven world. But why would you ever want to go live? That's really up to you.

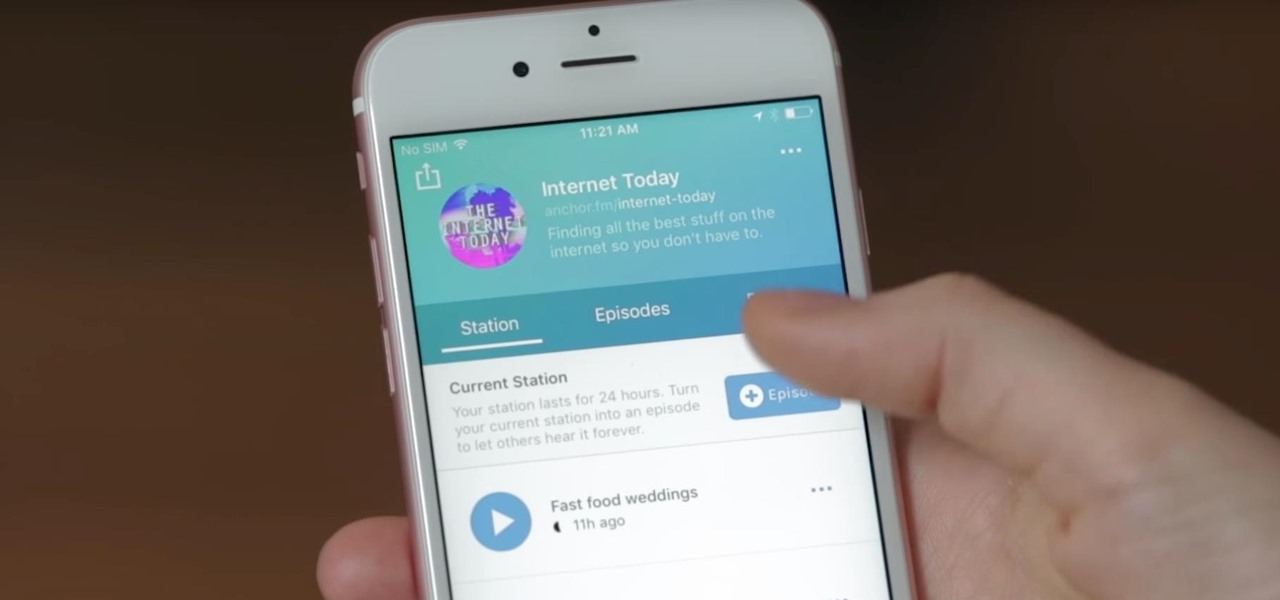
Anchor has been called the audio equivalent of Snapchat. The app lets you record audio and broadcast it to whomever you follow. If you haven't heard of the app, get familiar with it because it has announced an easy way for you to record and publish podcasts from your smartphone.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

It's about that time again. Spring weather is here, a new season of Game of Thrones is upon us, and we're getting ready for the next version of Android.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

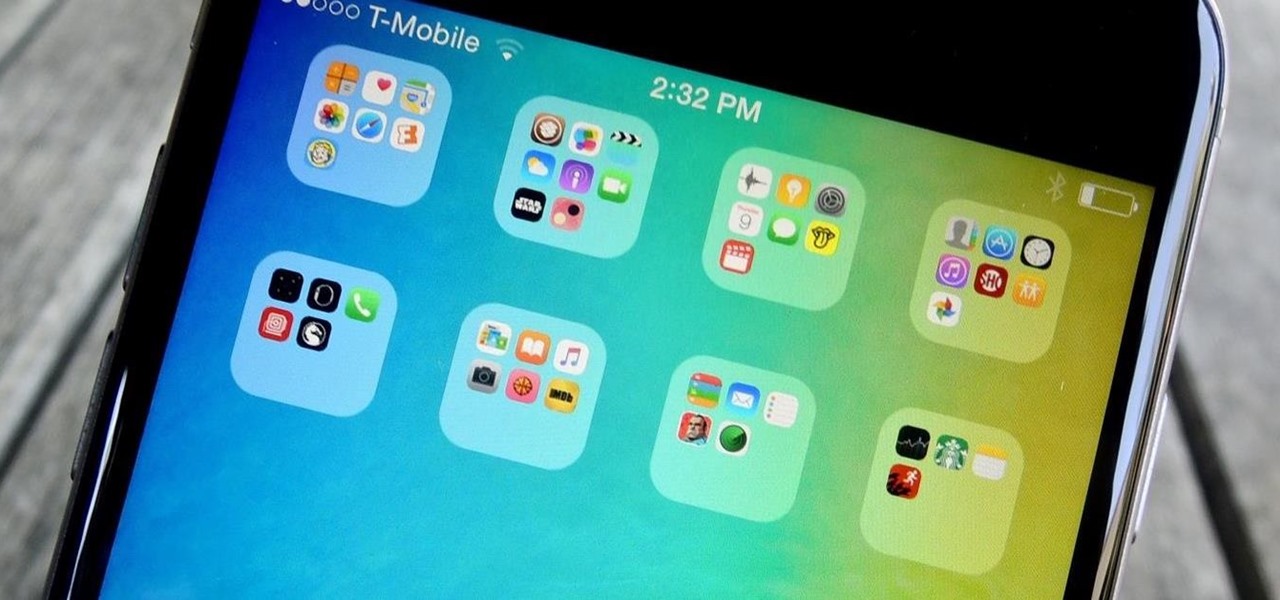
You know what's in your folders, so it's not always necessary to label them and ruin that clean look you're going for on your iPhone's home screen. I mean, how many folders am I going to have to title "Stuff" or "Junk"?