
How To: Make business calls in Chinese
Benny from askbenny.cn teaches you some Mandarin Chinese words and phrases for use when making a formal business call.


Benny from askbenny.cn teaches you some Mandarin Chinese words and phrases for use when making a formal business call.

Benny teaches you some Mandarin Chinese words and phrases for use during a business meeting.

Benny teaches you some Mandarin Chinese phrases to convey business etiquette.

In this episode of Gopher Haul you'll learn you can use an autodialer to market your business. This is a device that makes outgoing calls from a computer while you are out working. Then when you get back you can listen to the messages of people who want an estimate.
Open After Effects. Create a new composition by selecting "Composition" and "New" from main menu. Use default NTSC DV preset. Keep 30-sec default duration unless you need more time for the video scene to edit. Import several video clips by selecting "File," then "Import" from menu. Navigate to video files you want. Import at least 3 different video files using Import File dialog box. Double click on 1st video file you want to add to your timeline. The file will now open in a video monitor win...

Step 1 Launch the Adobe Flash program and select “Flash File (Actionscript 3.0)” under the “Create New” menu. Change the workspace layout to “Essentials” by clicking on the drop-down menu in the upper left of the top menu bar.

Say goodbye to heavy backpacks and overcrowded bookshelves. You can fit a whole library – up to 350 ebooks! – in a device that's smaller and lighter than the average paperback. Here's how to make it work for you. Use the Reader Digital Book by Sony PRS-700.

There's no better time to reset, improve yourself, and develop new skills than at the start of a brand new year, where you're stuck at home with nothing better to do. Thankfully, this amazing deal on The 2021 Career & Self Development Master Class has come at a perfect time. Right now, it's on sale for just $39.99 — that's a whopping 98% off the regular price of $2,000.

Since Motorola engineer Bill Smith invented Six Sigma in 1986, corporations around the world have employed it to eliminate costs and process cycle time while increasing profits and customer satisfaction. These techniques and tools for process improvement were invaluable to famed CEO Jack Welch, who used them to redefine General Electric's business strategy in 1995.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

For a decade, Microsoft Azure has been transforming businesses across the globe. The cloud-computing service is leading the way in software as a service (SaaS), platform as a service (Paas), and infrastructure as a service (IaaS) protocols.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.
The Pixel 4 is one of the most talked-about phones of 2019, so you know there will be lots of third-party developer support. Mods are already popping up, so you'll want to get Magisk installed as soon as possible to get root access. The current method used to gain root is the quickest way yet, thanks to the recent TWRP custom recovery support for the Pixel 4.

Now that Microsoft has squarely focused on the enterprise market with the HoloLens 2, it appears Lenovo is content to play follow-the-leader with its new augmented reality headset.

Anyone who has been within a block of any wireless brick and mortar store or tech conference in the last couple of years has no doubt seen banners, posters, and videos promoting 5G high-speed wireless services on the way.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.
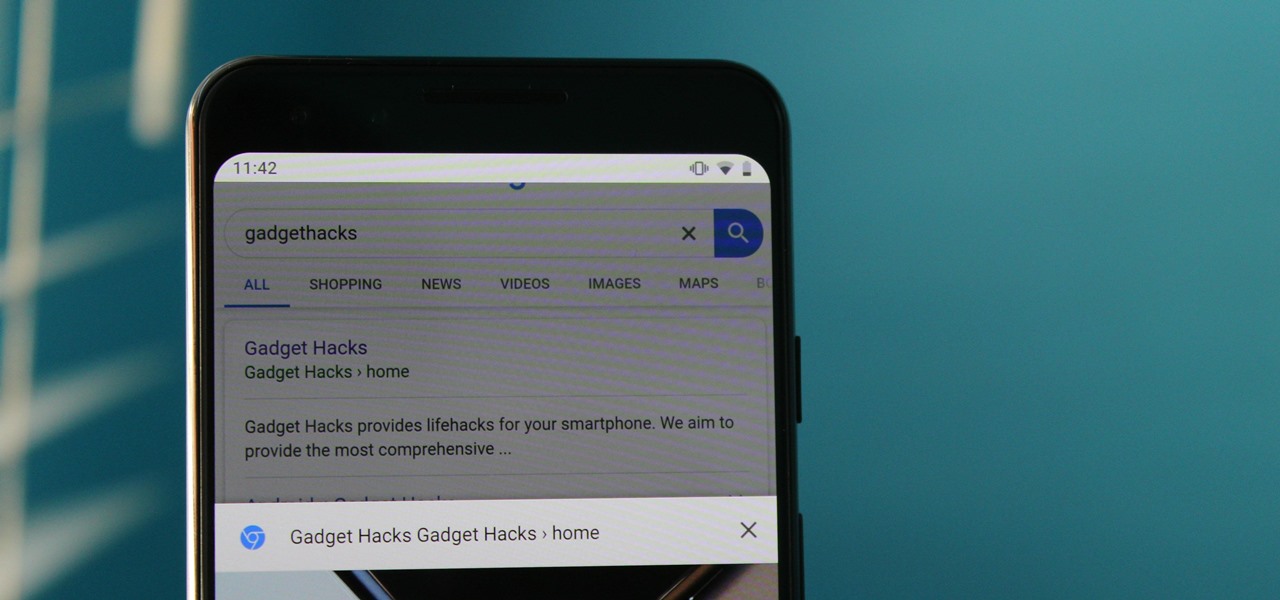
If you ever looked at Apple's Peek and Pop feature on Safari and said "I want that," Google has kinda-sorta delivered. A new hidden Chrome feature brings similar functionality to Android despite the lack of 3D Touch, and while it's a bit redundant and nowhere near as polished, it does make navigating the web easier.

With would-be unicorns Magic Leap and Niantic among its investments, Google is an active investor in augmented reality technology. This week, the search giant experienced both ends of the investment cycle, with an exit via Lyft's acquisition of Blue Vision Labs, and a funding round for Resolution Games.

For the augmented reality hardware industry to progress towards the consumer segment, display technology needs to get better. Investors recognize that, and they are showing AR display makers the money.

Apparently, it's Google Week for the augmented reality business. Now that ARCore has a firm foothold in the app ecosystem, Google is making a case with educators and marketers that the apps should have a place in schools and campaigns, and the company is also encouraging developers to learn how to build apps using ARCore.
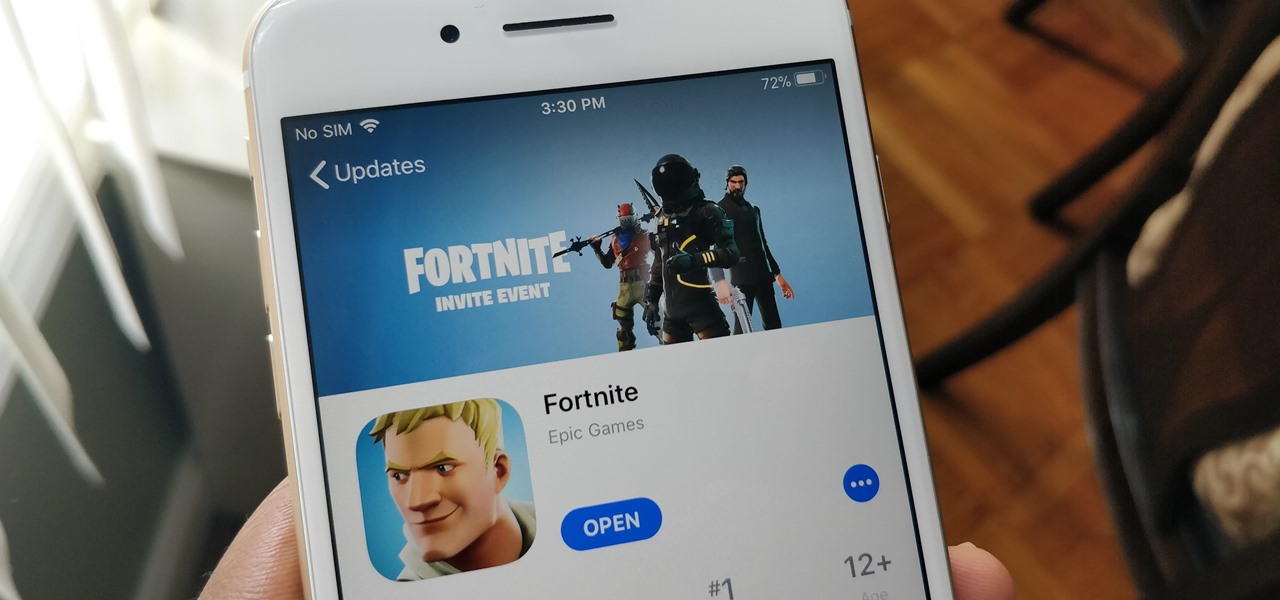
If you're a console or PC gamer, you may be quick to ignore the mobile version of Fortnite Battle Royale. The lower graphics and the switch to touchscreen controls may be enough reason to dismiss this version of the game. But don't be so quick to judge — there are actually some clear advantages to playing on mobile.

Coming into this year's Consumer Electronics Show (CES), the common sentiment among observers was that this was expected to be the big year for augmented reality.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.
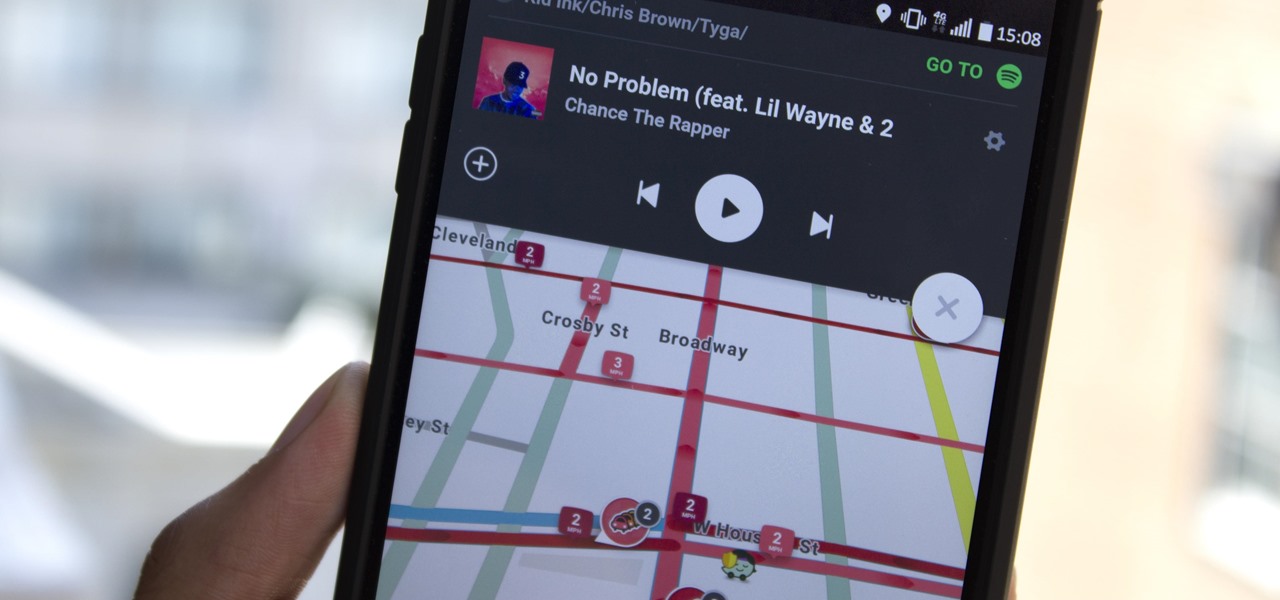
Who doesn't love listening to music or playlists when driving? The open road and an awesome playlist make for a perfect pairing, but it can become quite the challenge if you're trying to navigate at the same time. That's why Waze's built-in audio controls for compatible apps like Spotify and Pandora are so useful, so you can always keep your eyes on the map and road ahead of you.

Brace yourselves, because Siri has a trick up its sleeve that iPhone users have wanted for some time. Yep, that's right, I'm talking about the ability to use Siri without having to talk out loud for the whole world to hear. It's great for privacy, Siri-ing on the down-low when you're not supposed to, or ... you know ... if you have a speech disorder.
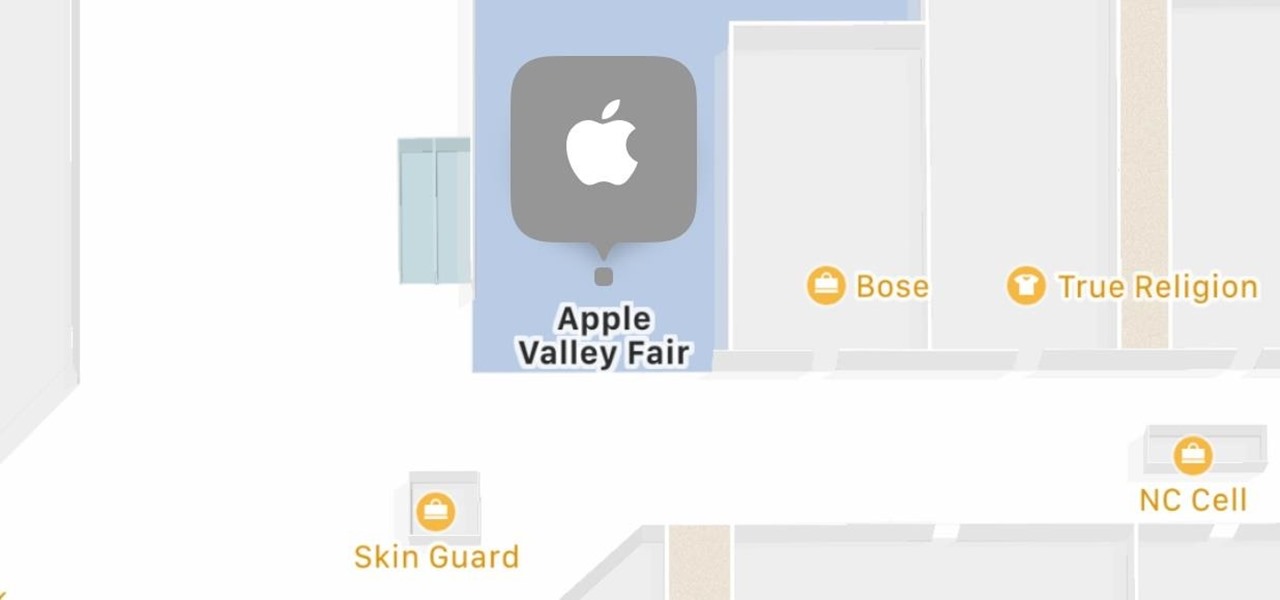
Apple has some great features aimed at making the lives of globetrotters and mall aficionados significantly easier, such as having detailed floor plans for airports and shopping centers in its native Maps app. With this feature available in Apple Maps, you no longer need to rely on publicly posted maps and directions that are often hard to understand.
This week's Market Reality covers a variety of business news from acquisitions and partnerships to competitive and technology assessments to quarterly financial results.

At the moment, it would be safe to say that demand for devices running Tango, Google's augmented reality smartphone platform, is relatively low among consumers. Kaon Interactive, a B2B software company who has built more than 5,000 interactive applications for use at trade shows, remote sales demonstrations, and other customer engagements, is betting that there is a market for the devices in sales and marketing.

The technology driving the automated vehicle revolution relies on the car's ability to see and understand the world around it.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

If you have a mobility impairment that affects your hands, arms, or manual dexterity, a smartphone's touch-based interface can almost be a barrier between you and the mobile internet. Eye-tracking software requires too much computing power for today's smartphones to handle, so it might seem as though there's no good way to interact with an Android device.

LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader is absolutely pointless, as having it locked will not hinder normal device usage, which is kinda true.

Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official debut already, you might not get that "Update available" notification for another few weeks.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

This is the second installment of the short series on how to remove user passwords in Windows. Once again this has only been tested on Windows 7. If I can find some time between two jobs and school I'll test all the ways on Windows 10 and Windows 8/8.1.

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules: