Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.
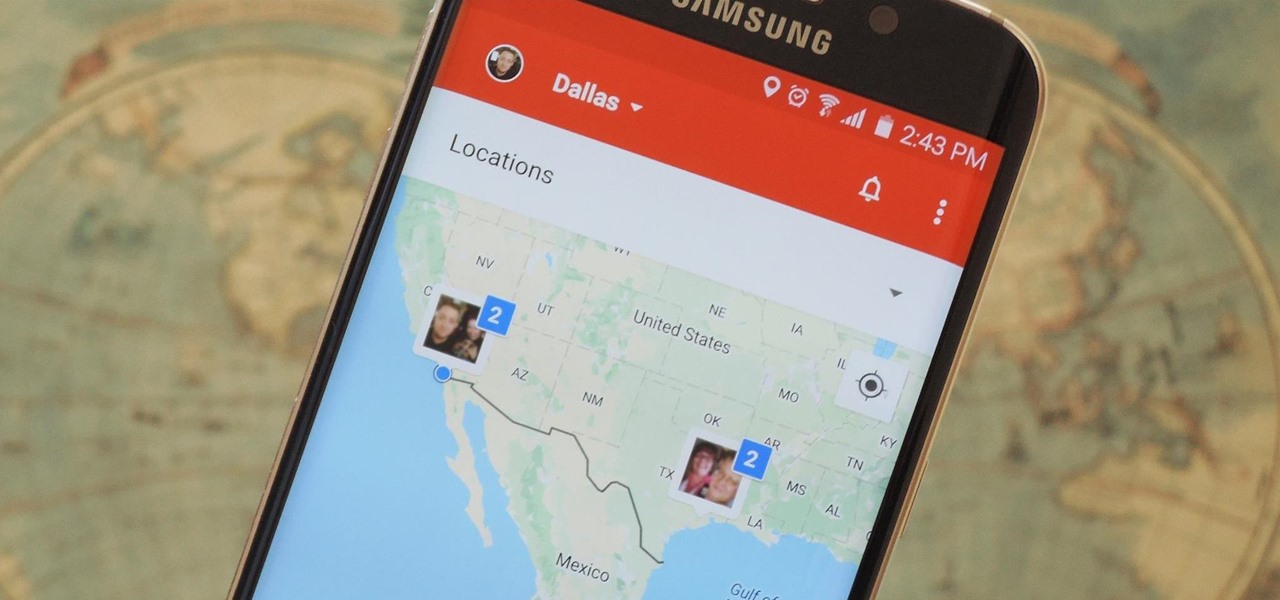
Instead of wasting time asking where your friends and family are at a given moment, then having them waste time by describing their location, there are several Android apps you can use that will automate this whole process. To top it off, it doesn't have to be about invading privacy or spying on someone, since most of these apps are offer two-way location sharing, or at least let you share locations only when you feel comfortable with it.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

At last, what you all finally waited for! Hi! Fire Crackers,

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

It didn't take long at all for developer Chainfire to sort out a root method for the new Android 5.0 Lollipop. After handling a few issues with changes to the SELinux kernel module, Chainfire pushed out an update to his popular SuperSU root app.

If you've ever noticed that the stock launcher on an Android device seems to just feel faster than any third-party home screen replacement app, this is not a placebo effect. Most manufacturers, Samsung included, force their stock launchers to reside permanently in your phone's memory, thus reducing the risk of redraws.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

Getting a new phone is exciting, but having access to its exclusive apps ahead of its release is what we're all about here on Gadget Hacks.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

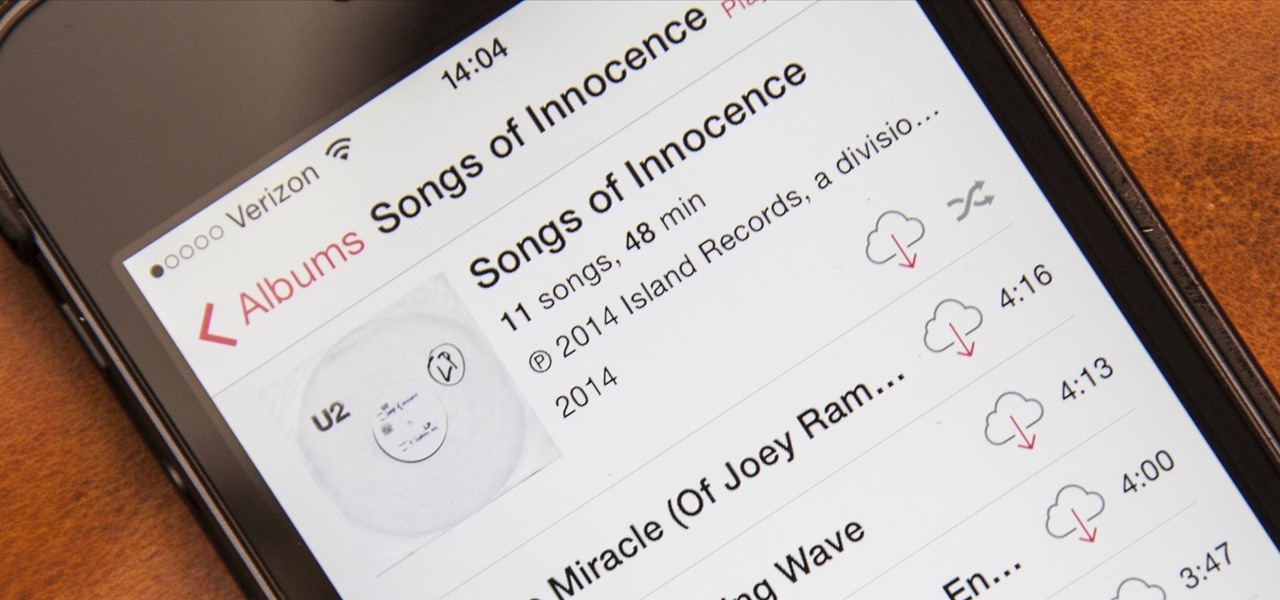
From my experiences, there are only two types of U2 people: those that love them and those that hate them. I'm the latter, so it's pretty damn annoying that Apple just added U2's new album, "Songs of Innocence," to my iCloud. If you find it creepy that U2 is appearing on your iPhone or in iTunes, don't worry—I've found a few ways to deal with it. UPDATE: How to Delete U2 Forever & Ever

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Sony has been hard at work refining its Xperia line of flagship phones. With a 6-month release cycle, they've managed to slim bezels, increase viewing angles, and boost processing power in the 1.5-year span between the original Xperia Z and the Z2.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

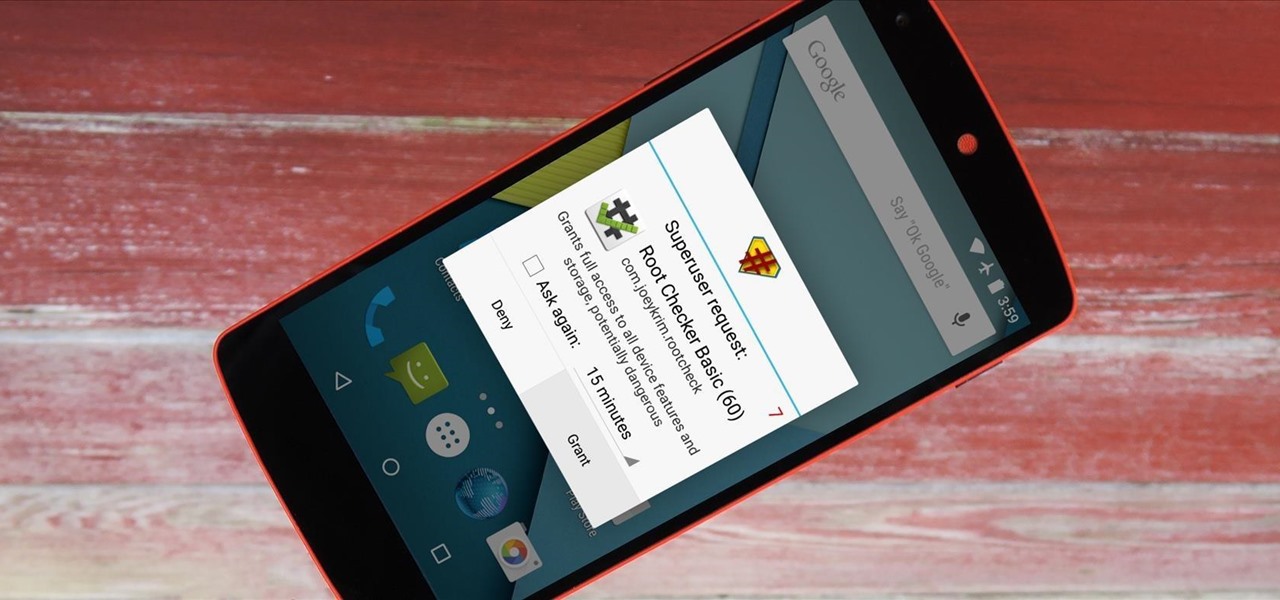
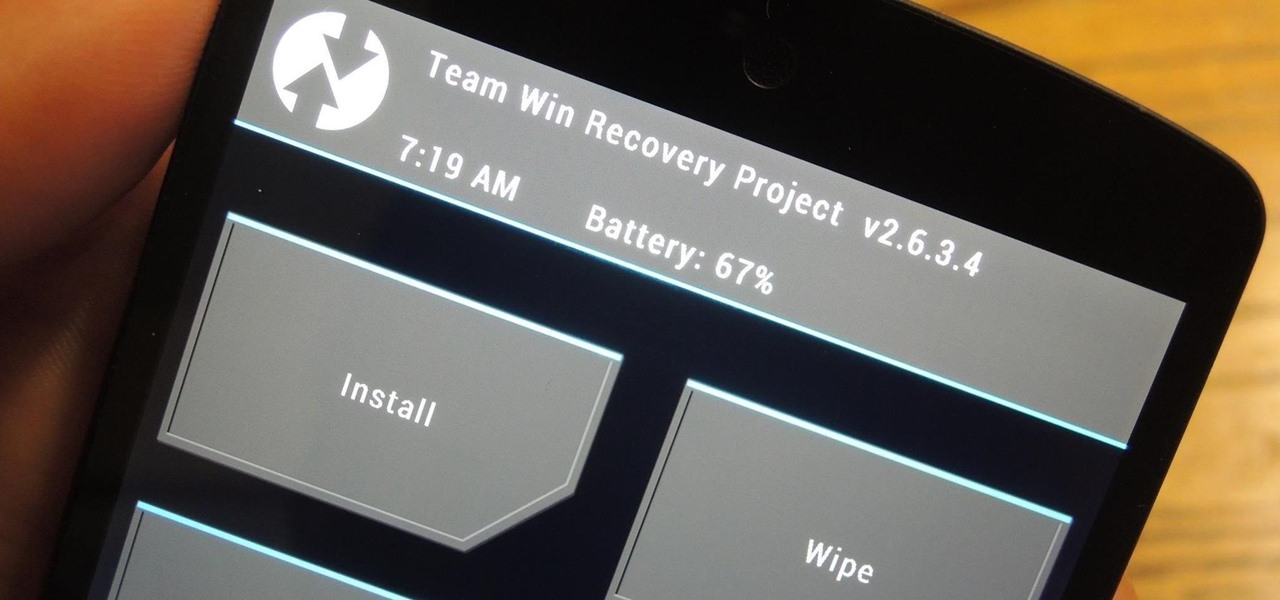
A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

For my money, one of the greatest improvements brought about from the smartphone revolution is the advent of visual voicemail. No longer do we have to slog through dial menus or trudge through every single message to get to the next. We can just look at our messages, right there on our screens, organized neatly like emails or text messages.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enlighten you on a subject you may not have even thought of yourself.

After a two-month delay, Apple has finally released iTunes 11, which was initially slated to be released alongside iOS 6.

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on configuring and connecting to your 2Wire Gateway via DSL wireless Internet instead of through an Ethernet cable. make sure to follow this whole process to get your High-Speed Internet up and running on your computer.

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing DSL 2Wire Gateway filters on home phones. Make sure to repeat the install process for the Gateway filters for each telephone in your house that uses the same phone number as your High-Speed Internet.

Get a new perspective on computing with an HP Tablet PC. HP's Tablet PCs are well-equipped personal notebooks, with a significant twist. The display turns around one hundred and eighty degrees, transforming your notebook into a flat tablet touchscreen PC.

Learning the blues isn't an easy task, but this video helps make it a little easier. The song you'll be learning is "Coffee Blues" by Mississippi John Hurt. It's in the key of A and is a typical blues progression, in an alternating bass. It's the chords A, D, and E. If you're yearning to learn the delta blues, this is a great first step.

This video will go over how to insert a check box in Microsoft Word for printing or for electronic distribution. With just a few clicks you can get a check box. You can even add different symbols or styles for your check box.

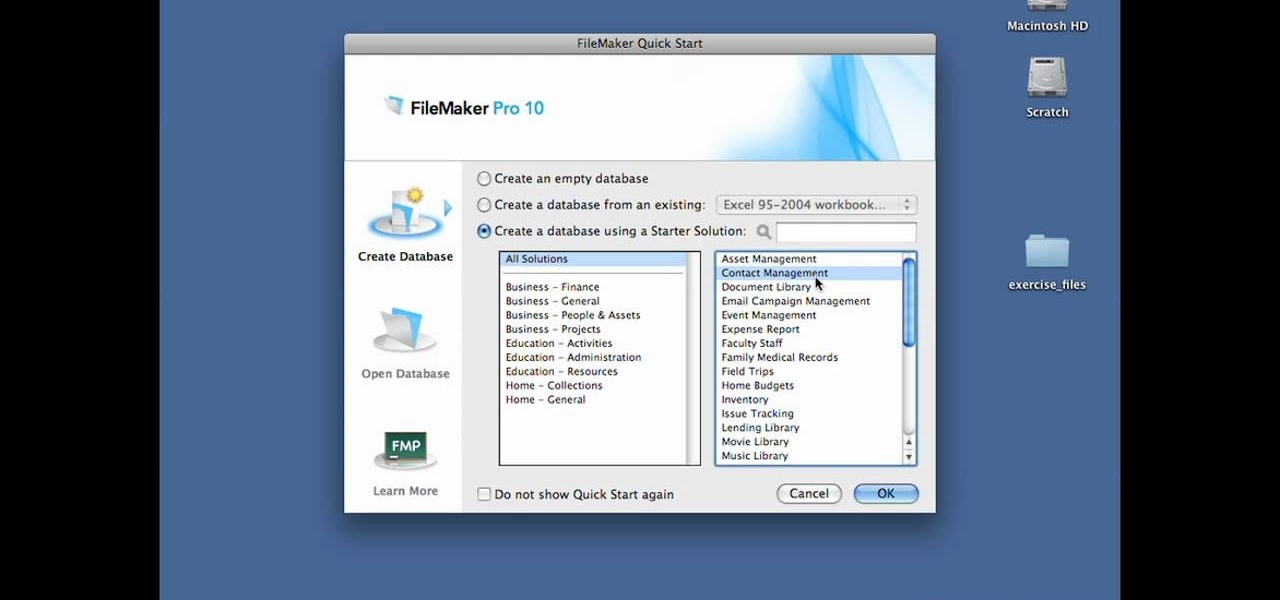
In this Lynda video tutorial, learn how to use FileMaker Pro 10 software to create databases with pre-made templates. FileMaker offers these templates in a package called Starter Solutions. To access these options, click open FileMaker. Then, go to New Database under the File menu. Click the option "Create a database using a Starter Solution." The templates are grouped according to the nature of their use. Some are for the home, while some are for business. All you do is open the template you...

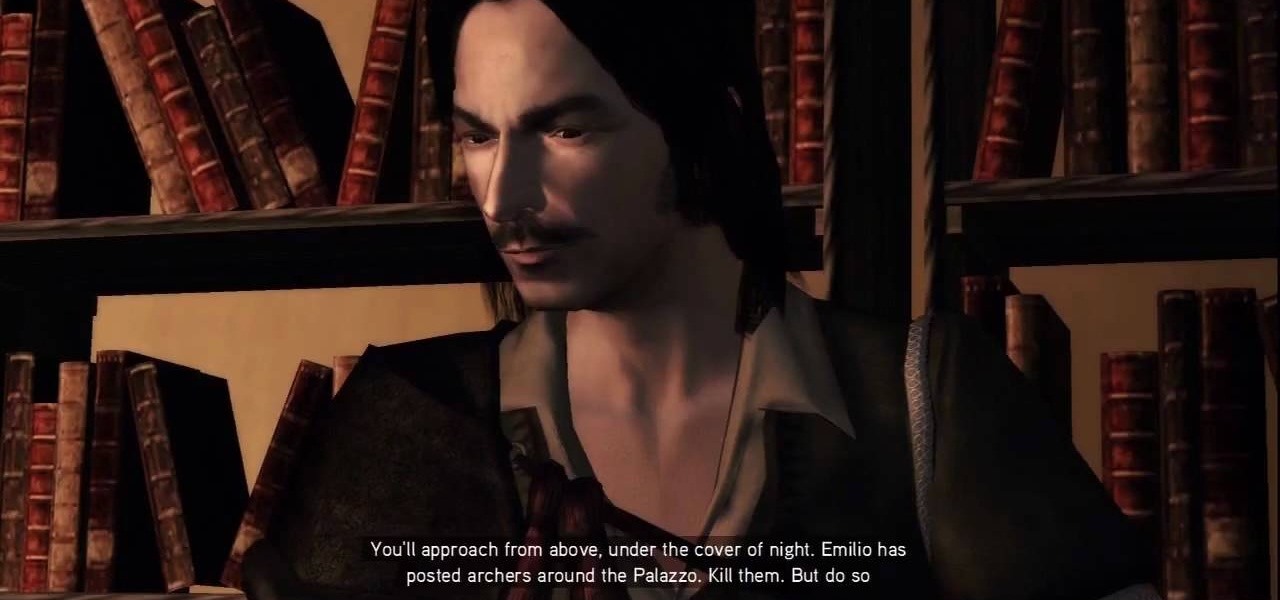
Everything Must Go: It's the truth. It's time to say goodbye to everything. See Antonio again and be ready for a quick time event during the cut scene after you accept the mission. The first order of business is to kill five archers surrounding the building in which Emilio is camping. Take to the rooftops and locate the guards. Once you've gotten near them, you can't let them get too far away from you. Kill all of 'em, being as stealthy or as brazen as you like. Personally, we like brazen.

Learn how to remove ink stains from fabric. Getting ink out of fabric is a tricky business, often best handled by a dry cleaner. If you want to try it yourself, though, here's what to do.