Magic Leap One owners with itchy trigger fingers may have their itch scratched next week, as Magic Leap has shared a brief teaser on Twitter for the long-awaited Dr. Grordbort's Invaders game from Weta Workshop.

Google's ARCore team is staying busy, as evidenced by yet another update of its augmented reality toolkit.

The HoloLens team is finally beginning to realize that to truly engage the mainstream, augmented reality needs to make its way out of the lab or factory floor and onto the streets.

Magic Leap loves to stoke mystery around its still unreleased product, the Magic Leap One: Creator Edition, and now we've found yet another piece of the puzzle in the form of an Easter egg on the company's website.
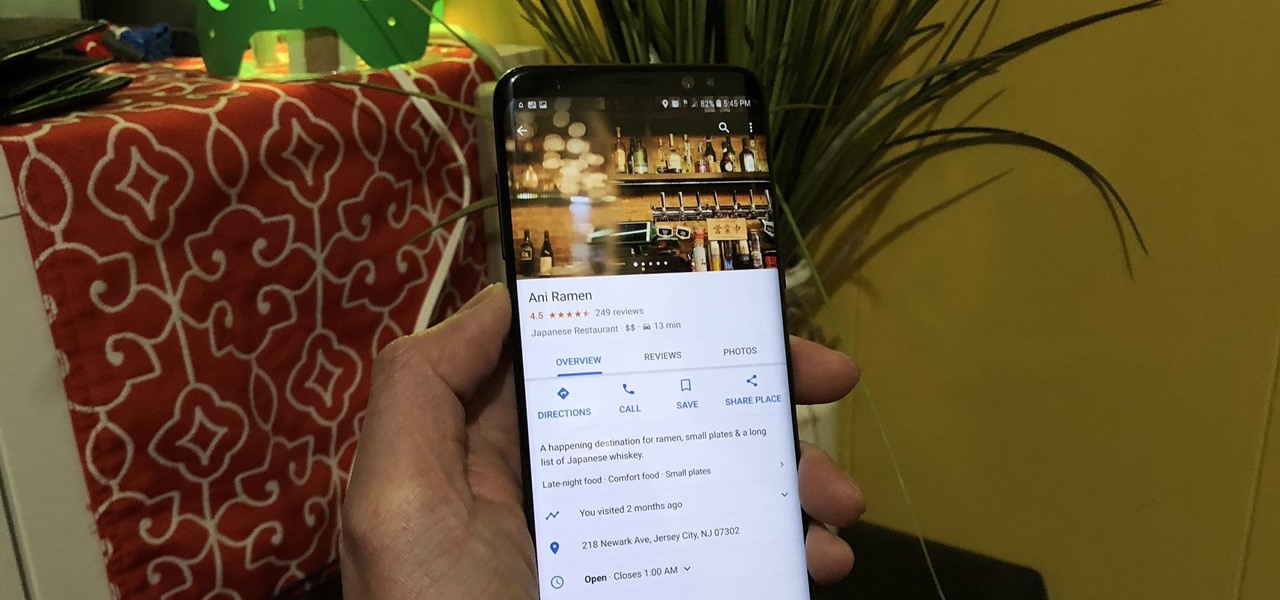
Going out to dinner on a Saturday night can be more trouble than it's worth when you find yourself waiting for hours on end just to be seated. Thankfully, Google Maps has some very useful data that can save you from a headache the next time you head out to your favorite restaurant.

Assassin's Creed Rebellion is a welcome addition to the popular gaming franchise, garnering great reviews so far. Unfortunately, the game has been stuck in soft-launch limbo for almost a year, with no firm release date in sight. With a little legwork, however, you can try the game out for yourself right now.

If you love to hear yourself talk, you can now enjoy seeing your words materialize in augmented reality with an ARKit-compatible iPhone or iPad.

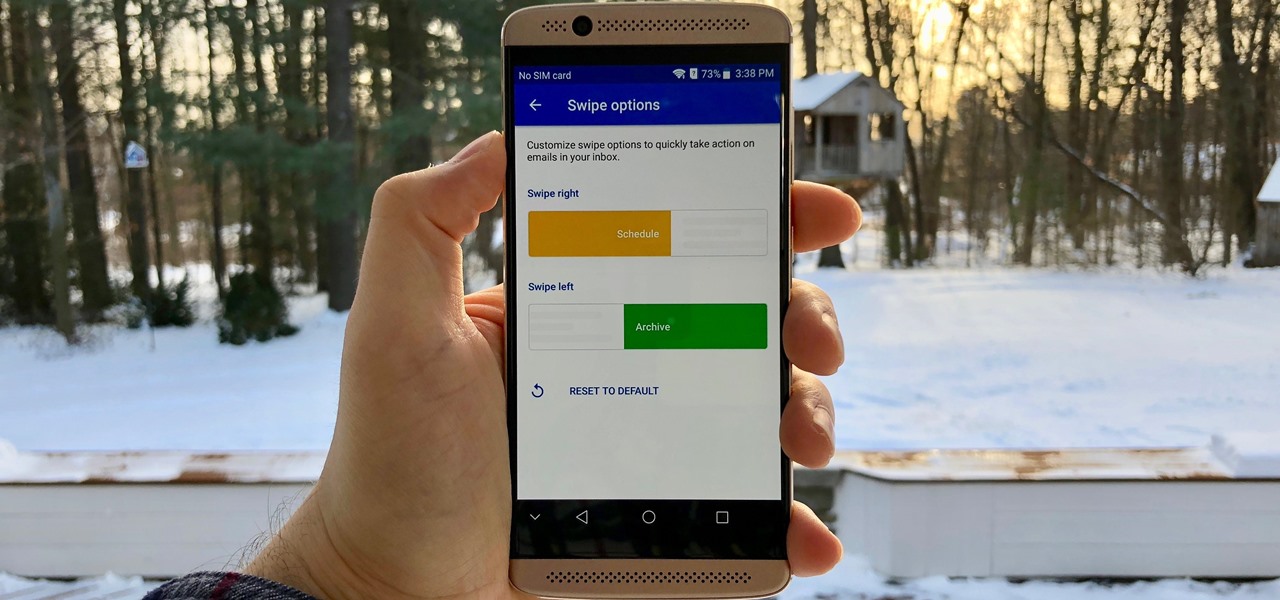
Swipe actions are an integral multitasking feature of any good email client, and Outlook is no exception. The application allows for two swipe actions at a time, but offers seven total options for those actions. We'll show you how to choose which actions go with which swipes to best tailor the app to your needs.

Many wonder how driverless cars will ever be able to navigate through any driving condition imaginable — but the point is self-taught machines, in theory, have the innate ability to adapt to chaotic and extreme driving conditions in ways far superior to what humans are capable of.

France's Groupe PSA (formerly known as PSA Peugeot Citroën) — one of the world's top-10 carmakers — aggressively seeks to take a lead in the rollout of the industry 's first driverless cars, as it becomes the first mainstream carmaker to announce it will launch a Level 3 self-drive vehicle launch by 2020.

The beauty gurus, gamers, and daily vloggers of the world are getting a great gift from YouTube very soon. No, it's not exclusive swag or diamond awards. Instead, it's an update to the YouTube mobile app that will support all video formats and let you send in-app messages.

Right off of the unveiling of the Moto Z2 Play, it looks like Lenovo is gearing up to announce the highly anticipated Moto Z2.

At the 2017 Augmented World Expo (AWE) in Santa Clara today, smartglasses maker Epson introduced two new augmented reality headsets from its Moverio line of products.

Remember back in 2011–2012 when "Little Talks" by Of Monsters and Men was the bumping new single being played everywhere? Well, thanks to this robot created from a LEGO Mindstorm EV3 kit, and an acoustic guitar, you get to get the iconic "hey!" stuck in your head for the rest of 2017. You're welcome.

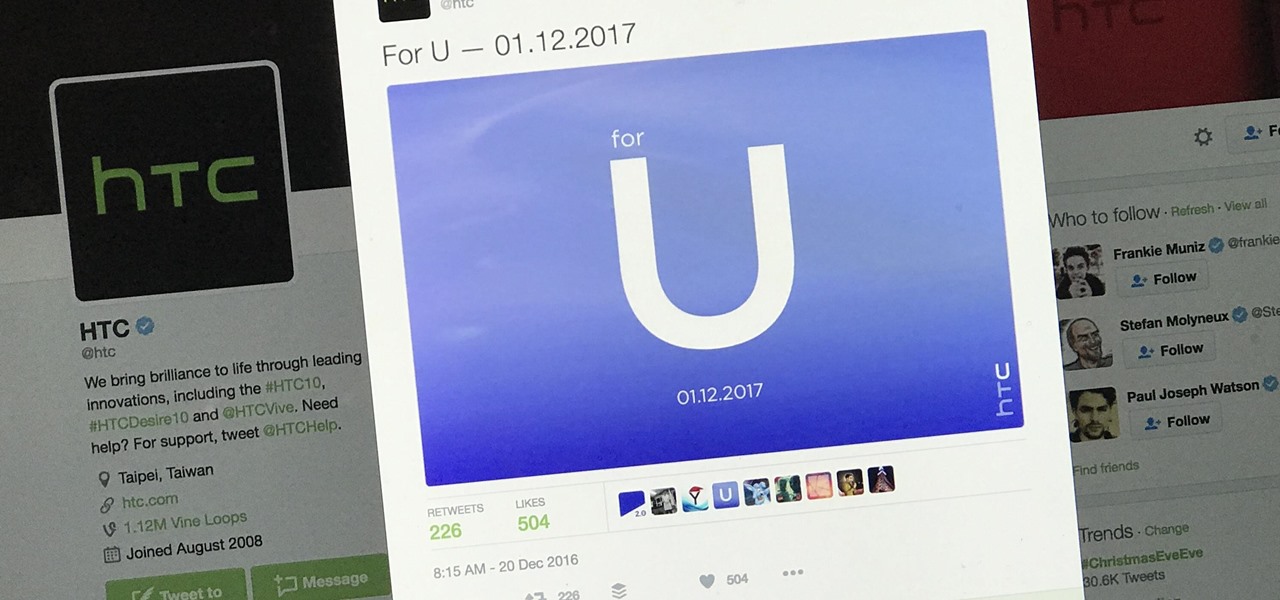
Earlier this week, a mysterious tweet appeared on the HTC Twitter account of a picture containing the letter "U" topped with a tiny "for" and the date "01.12.2017" at the bottom. It is a pretty solid teaser, but for a company that has had a solid year with their Vive virtual reality headset, and all of the other technological appendages they have, it seems a bit ominous for them.

A new contender has entered the mixed reality ring. San Fransisco-based Occipital has just released an "Explorer Edition" of Bridge—an iPhone-based mixed and virtual reality headset that uses their popular Structure Sensor. At a fraction of the cost of a HoloLens developers kit, this could be a place many curious people use to find their NextReality.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

We like our Egg McMuffins around here, albeit homemade with our preferred ingredients: whole wheat (or homemade sourdough) English muffins, a slice of thick Tillamook cheddar cheese, a meat, perhaps, like Canadian bacon, and finally—that perfectly-fried, perfectly-shaped egg.

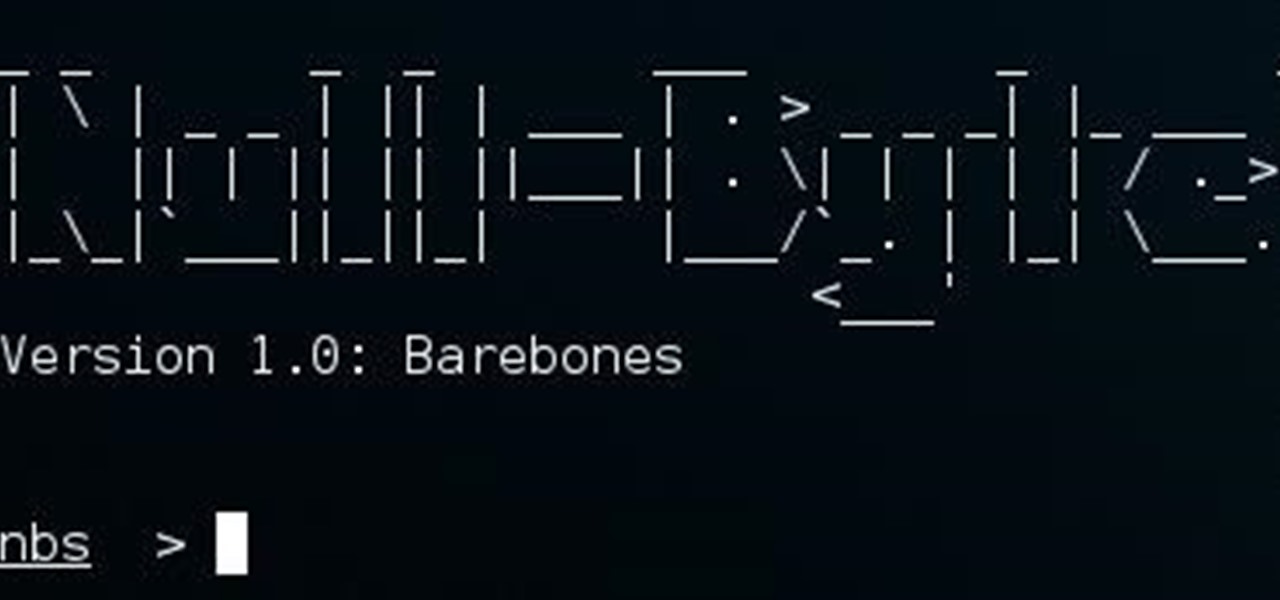
Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

From day to day, it can be difficult to remember everything that's required of you. I tend to forget exactly where it is I'm supposed to be during my busiest moments, and it's even easier to delete each day's events out of your brain when there's so much else that dominates your mind. Yet taking the time to remember exactly what it is that happens during each of our days can be a vital part of our memory—and with nothing more than 15 minutes, we can strengthen our brains and remember more tha...

As crazy as it sounds, there are times when bottles of wine go unfinished. I love a glass or three of vino, but am often guilty of not finishing the bottle. Sometimes I don't have the time to finish it, and other times I like it so much that I open bottle number two and can't finish that.

Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important).

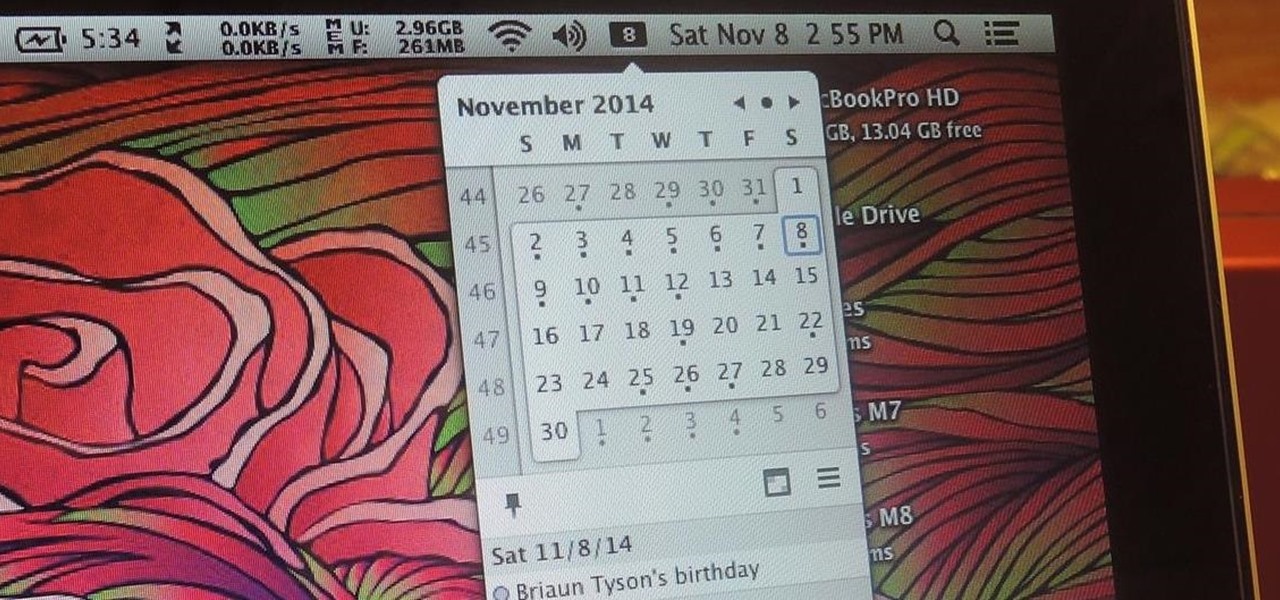
While it's much quicker in Yosemite, the Calendar app for Mac has never been as fast as I'd like. If my schedule is really full, it can sometimes hang when first opening the Calendar.

It's been a long time coming, but Google's Calendar app for Android has finally received a visual makeover. In the spirit of Android Lollipop, Google's new Material Design permeates throughout the update.

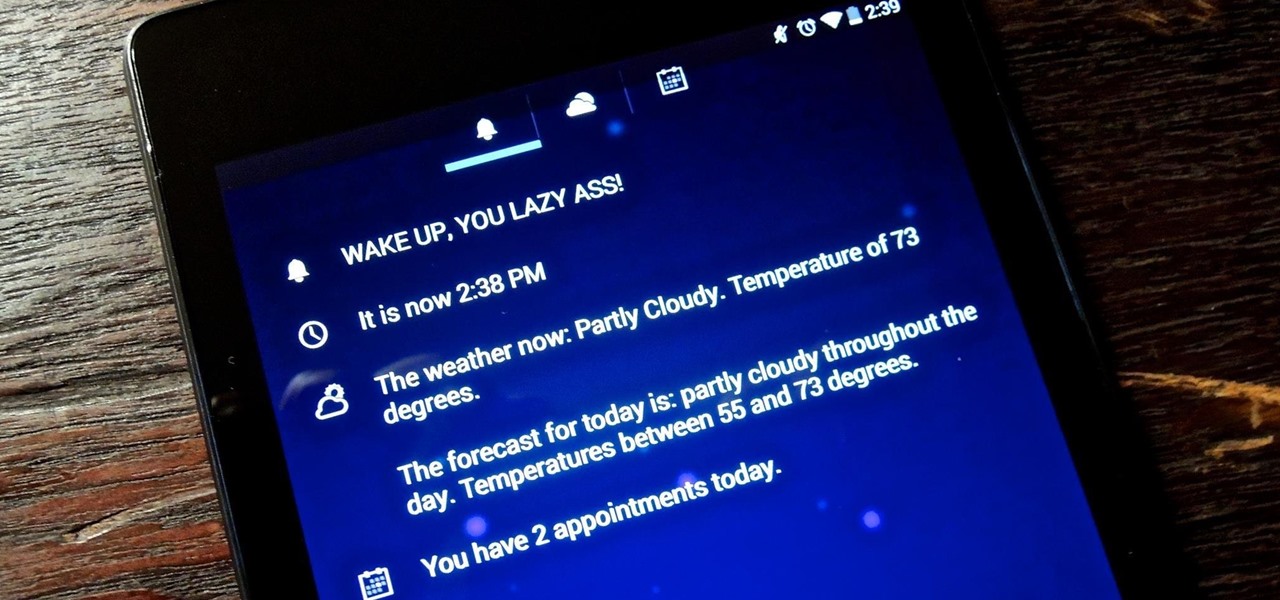
I regularly use my Nexus 7 to wake up in the mornings (well, sometimes afternoons), but it's pretty minimal in what it does. I shouldn't have to open multiple apps when I wake up to figure out my schedule for the day or what the weather is going to be like.

I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

Silence is golden, especially when you're sleeping and about to lock lips with Kate Upton in a dream (or Ryan Gosling, for all you ladies). The last thing you want is your tablet rudely interrupting your passionate kiss with blaring notifications. It's even worse in real-life when you're in an important meeting and you forgot to silence your Android up.

As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

I've never been much of a runner. I've tried running alone, with a partner, on busy sidewalks, and back country roads, but I just never got it. There are a few other forms of exercise I genuinely enjoy, but have yet to experience that "natural high" that avid runners are always talking about.
Project management covers a lot of processes needed for project completion. Among the many functions in managing projects, one of the most important is resource management. It is an aspect of project management which deals with various project management resources like human, materials, equipment and costs.

As a kid, there was nothing more fulfilling than sinking my teeth deep into the succulent flesh of an orange, savoring every drop of juice that wasn't busy sliding down your chin and onto your clothes. While my adulation for oranges never ceased as I grew older, the way I consumed the precious fruit did evolve with my maturity. Gone were the days of messy eating, and here I was now, peeling my oranges as a teenager, taking my precious time in separating each individual slice for a clean and t...

Ever drive a friend's car? Maybe a rental? Then you've probably found yourself in a very frustrating situation when you realize you need some gas. Heck, it probably even happens to you in your own car sometimes.

Advancements to Android's open source OS come in the form of ROMs and mods, available all over the web for anyone to find. Installing any of these modifications tends to wipe your phone clean, causing you to lose all of the precious data on your device.

For many busy people, time is of the essence, and for others, it's simply just being impatient. But no matter what your vice, having your computer start up as quickly as possible is usually a plus for anyone.

TIFF 2012 Wrap-Up - Pounds Personally Gained: 4.5

In this tutorial, we learn how to make a ribbon bow with the help of toothpicks. Start with a full twist on your ribbon, then place it behind the toothpick and hold it in place with another toothpick. Next, make another loop and then do a front loop with a half of a twist. Now, secure those in place with toothpicks and do three side loops with half twists. Secure them with toothpicks, then continue with larger loops made with half twists. When finished, hold the ribbon in the middle with your...

Need some cool sound effects for your next film? Kipkay's got an idea… the "Rumble Pipe". This noisemaking pipe creates a rumbling sound perfect for any drone SFX. Try it out. It's just a little sounds effects gizmo. Cheap and easy!