While putting content and information online gets easier every day, it seems like getting it back is only getting harder. In a lot of cases (we're looking at you, Facebook), once you upload something, it's forever in the hands of someone else. That's where The Data Liberation Front comes in. Believe it or not, The Data Liberation Front is a team of Google engineers who work to make it easier for users to take their stuff back whenever they feel like it.
As if iOS 6 wasn't under enough scrutiny, a new issue has surfaced regarding the App Store for iOS 6 on the iPhone and iPad. According to users, the application store is very sluggish and doesn't load properly. Below is a video of just how slow the application store is.

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

How would you like to be able to watch all of the movies and television shows available on the Netflix watch instantly service on your HD2 Android phone? Check out this video to learn how to download the Netflix app.

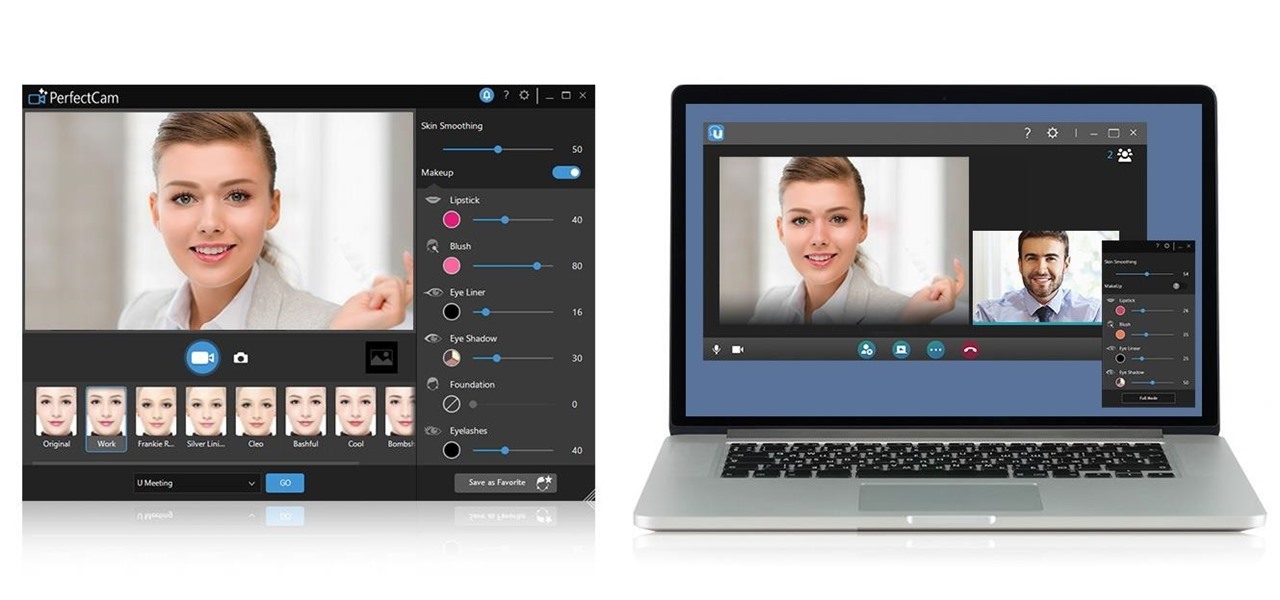
Check out this basic back-to-school look that's also great for daily work and church services. It's a neutral makeup look with very little shimmer. It only takes about 5 minutes to create these beautiful eyes! Watch and learn how to apply these eyeshadows and cosmetics.
Want to receive daily, weekly or monthly updates on a subject of your choice? With Google Alerts, it's easy! So easy, in fact, that this home computing how-to from the folks at Easily can present a complete (and somewhat talky) overview of the process in just under five minutes' time. For the specifics, and to get started setting up and using Google Alerts yourself, just watch this handy how-to.

This tutorial will show you a super simple way to get free ringtones for your iPhone. This method will let you bypass iTunes's expensive ringtone service and create your own - anytime, from any song and for free!

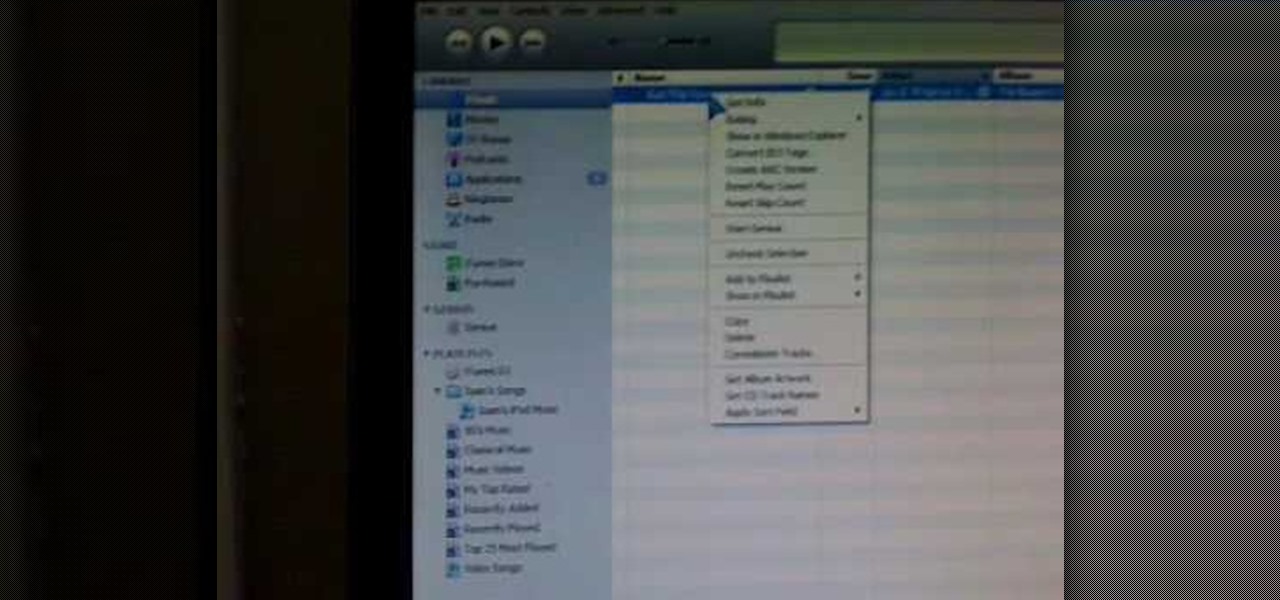
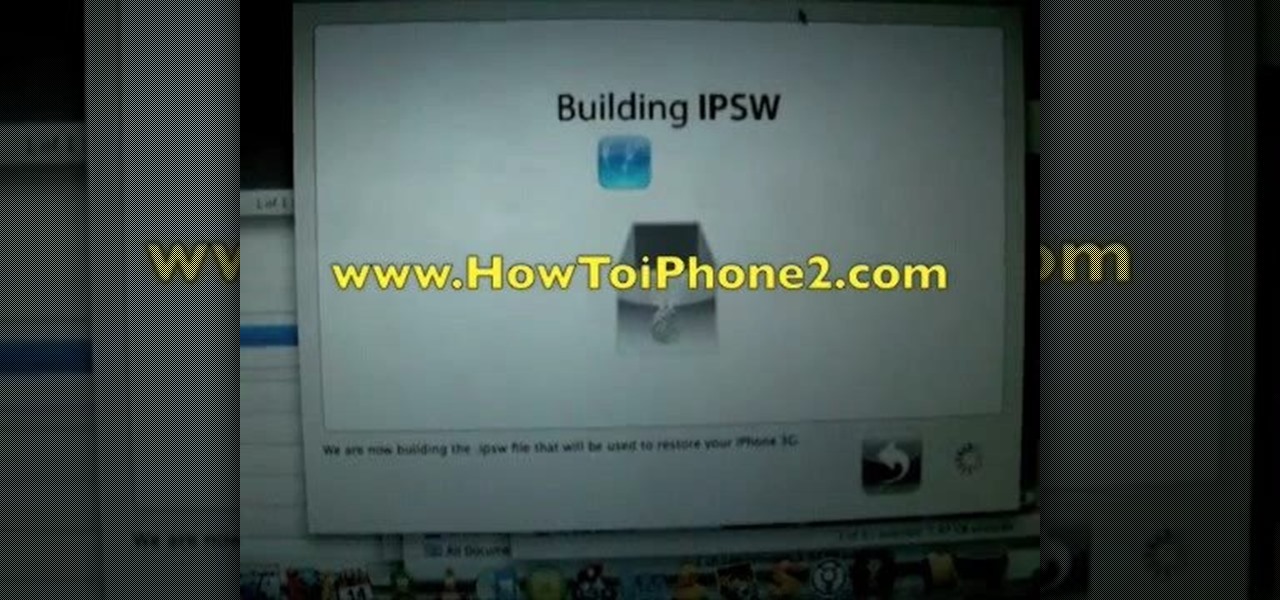
This is an Apple iPhone video tutorial that will show you how to unlock an Apple iPhone 2G or 3G for use with another mobile phone service provider other that AT&T. If you are using a Macintosh computer, you can unlock both the 2G and the 3G phones. If you're using a PC, then you can only unlock the 3G iPhone.

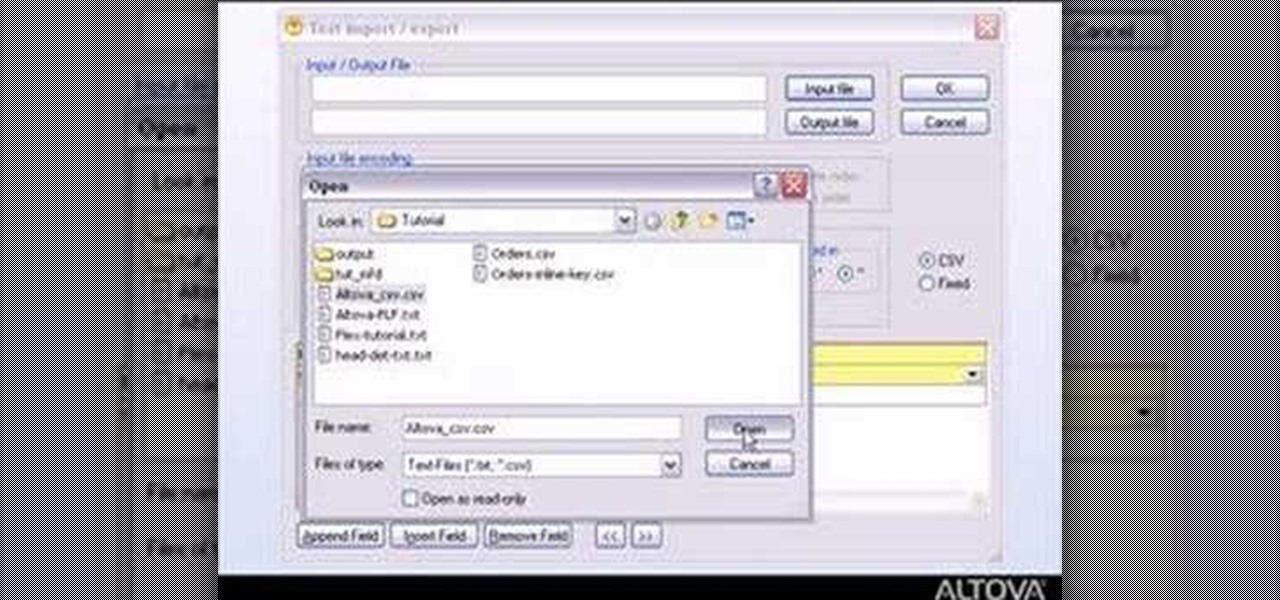
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

The Prada cell phone (the LG KE850) is a unique, sophisticated and elegant mobile phone with the first complete advanced touch interface.

Watch this how-to video to learn how to get 30 days of Xbox Live Gold for free just by pretending you don't want it. Xbox Live Gold is normally a subscription service, but you can get 30 days of it for free by following the tips in this how-to video.

In this how to video you can learn to create a punk, goth, emo red Avril Lavigne inspired eyeshadow look. This makeup tutorial uses the following products:

An installer shows some tips to help remove your trialer hub so it can be serviced and then reinstall it so your wheel can be remounted.

Just some suggestions and roughly the way I handle calls. There is more than one way to do this and every call is different. Enjoy!

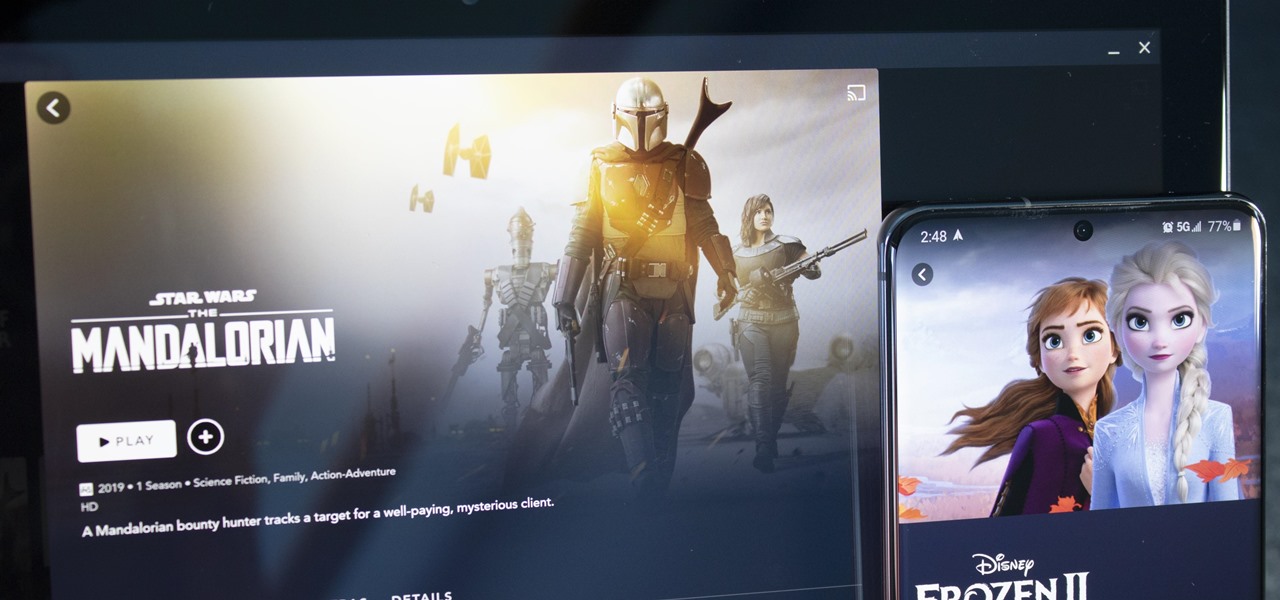
With shows like "The Mandalorian" and movies like "Frozen 2," Disney+ has quickly become a must-have streaming service. However, with Netflix, Amazon Prime Video, and Hulu, adding another subscription-based service can become expensive — but there are ways to trim down the cost.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

While Magic Leap turned heads at the Game Developers Conference with AR experiences at the Unity and Unreal Engine booths, news broke that the company was the winning bidder for ODG's patents.

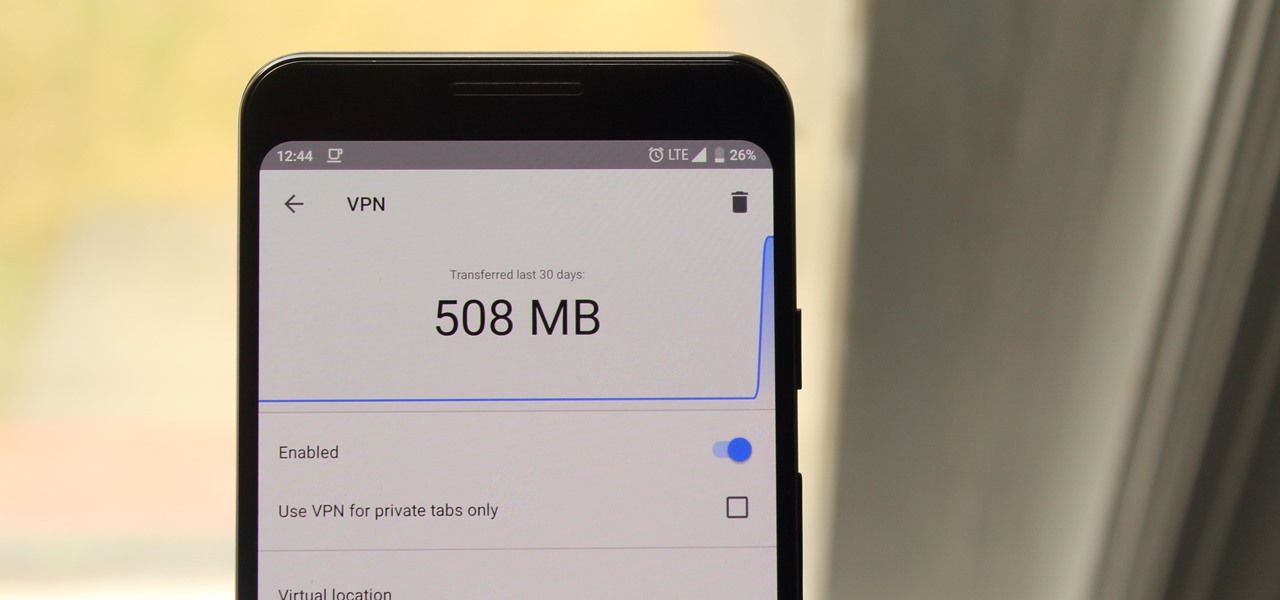
There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

There are more than a few subscription-based movie streaming apps available for Android and iPhone, each with different benefits and varying pricing plans. Needless to say, it can get expensive fast if you sign up for multiple services because you can't decide on what's best. Hopefully, we can help you out with choosing the right video-on-demand app to spend your hard-earned dollars on.

If you use Apple's email services and the "From:" field in your iPhone's Mail app is cluttered with @Mac.com, @Me.com, and @iCloud.com variations of the same address — along with third-party accounts — there's an easy way to declutter things and hide the addresses you don't use anymore.

A new augmented reality cloud platform from German startup Visualix is working to give enterprises the capability to scan their own warehouses, factories, and stores and create maps for augmented reality navigation.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

In this series, we are going to get you to the edge of building your own cloud-based, cross-platform augmented reality app for iPhone, Android, HoloLens, and Meta 2, among other devices. Once we get the necessary software installed, we will walk through the process of setting up an Azure account and creating blob storage.

The cosmetics industry faced a rude awakening on Friday as beauty behemoth L'Oréal gobbled up ModiFace, one of the leading providers of augmented reality technology to the cosmetics industry (price details for the acquisition were not disclosed).

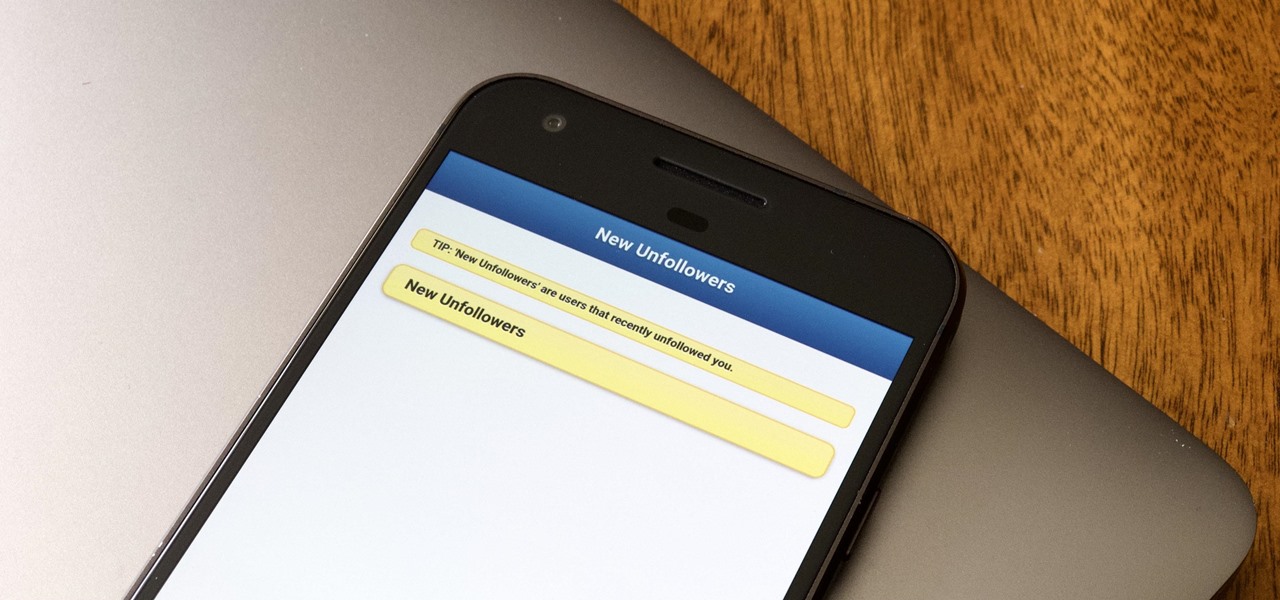
Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

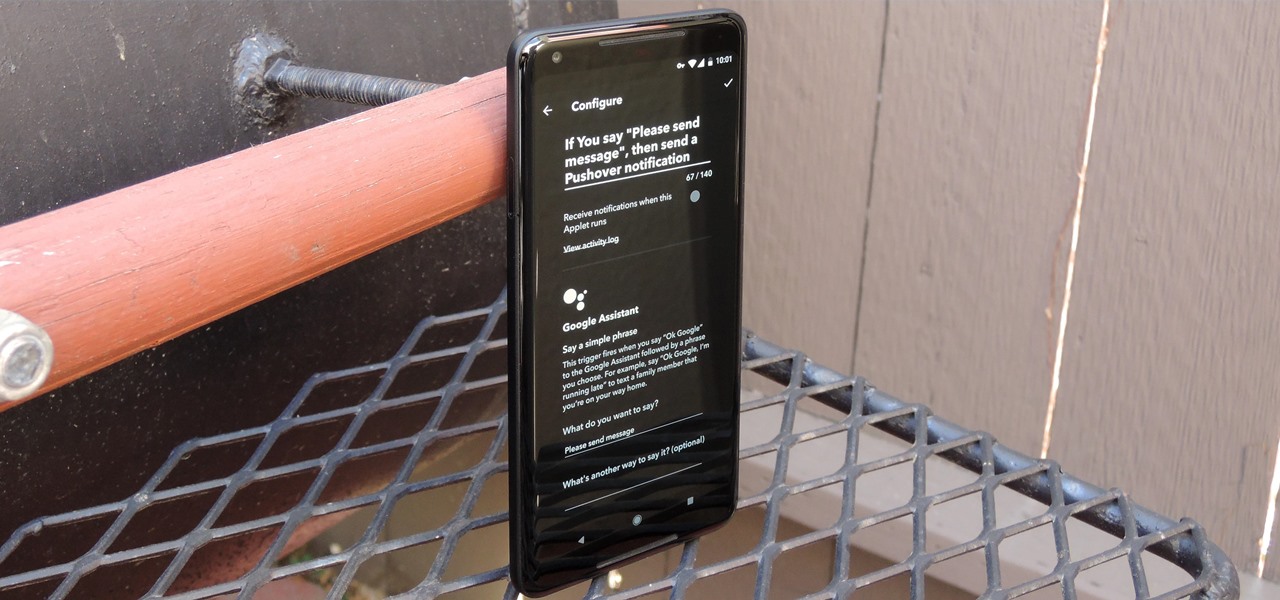
IFTTT is a fantastic tool that lets you trigger actions on your smartphone that normally require more advanced hacking. With the help of its friendly user interface, turning your phone into a more personal device has never been easier. However, the app has some more intricate options under the surface, making advanced implementations of applets difficult for beginners.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

A survey by ABI Research revealed that only 25 percent of businesses have implemented augmented reality technology in some form or fashion.

Paying for street parking in New York City just got so much easier. Instead of searching for loose change or hoping you didn't forget your wallet, you can use a device you always have with you: your phone.

Wegmans recently partnered with Instacart, an online grocery-delivery app, to bring your groceries right to you. The collaboration will begin in the suburbs around Washington, DC, and Wegmans plans to expand to other areas later on.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Nokia, the Finnish telecommunications company, is about to shake things up a bit after its networks sales in the final quarter of last year declined 14% compared to sales in 2015.

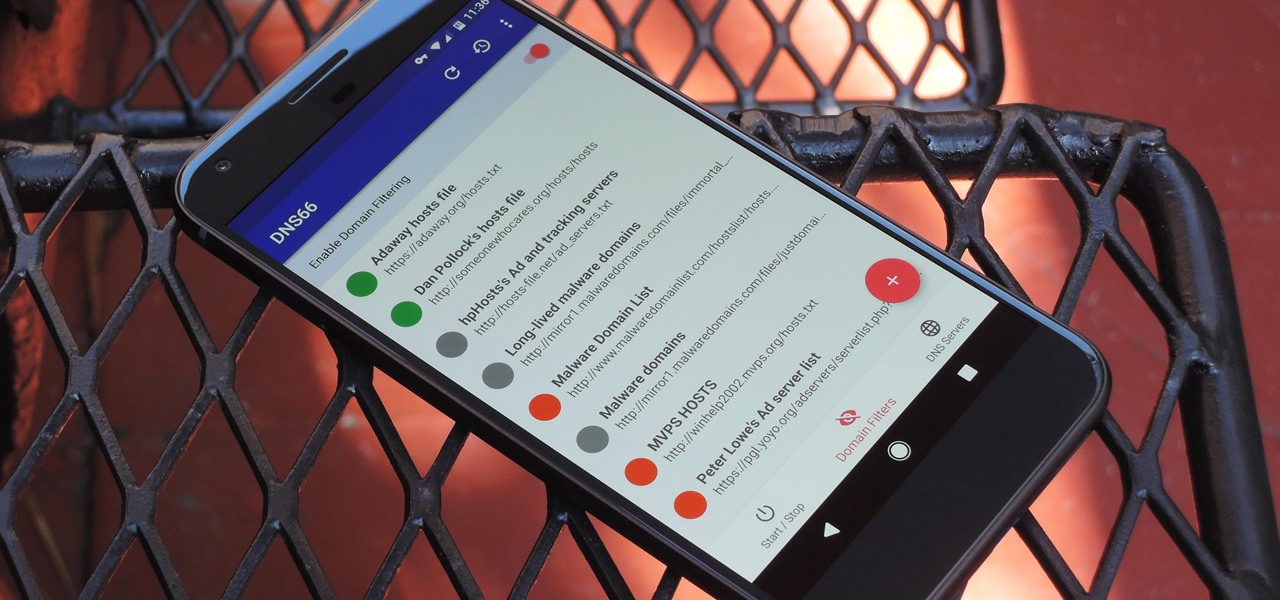
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?