
How To: Make homemade bratwurst
BBQTalk.ca shows you how easy it is to make homemade bratwurst sausage. You will need to have a meat grinder for this.


BBQTalk.ca shows you how easy it is to make homemade bratwurst sausage. You will need to have a meat grinder for this.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

Beware: After a new caucus — the Congressional Caucus on Virtual, Augmented, and Mixed Reality Technologies for the 115th Congress — formed in the US House of Representatives, the government has decided to go after all mixed reality head-mounted displays. The HoloLens, Magic Leap — nothing is safe anymore.

The fun of gambling can come at a hefty price. Problem gambling affects 331, 000 individuals and can quickly destroy families and lives. Know the risks. The Responsible Gambling Council offers a free Cost2Play Calculator app and safe gambling tips atwww.noregrets.ca


One of the most basic things you should know in French is a nice greeting. Saying "hello" to someone in French is easy, and is comprised of either "bonjour" or "salut". To say "hello" or "hi" to a friend who is either your age or younger, you say, "salut". To ask "how are you" to someone older than you, you say "bonjour, allez-vous bien" or "bonjour, comment allez-vous?" To a friend, you ask, "Salut, Ca va bin?"

Learn how to care for your pet with help from VetVid. See how to diagnose and treat atopy in dogs with this video tutorial.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

People take their Black Friday shopping seriously. Some of them are even willing to fight over it. Every year the stories get crazier and crazier, and someone always gets hurt (or even killed).

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

I was mesmerized by the decoration in Rosalind’s. It has pictures of the Ethiopian people from tribes, the walls are painted bright yellow and covered with black nyala’s an endanger species found in Ethiopia, amazing hut roofs on top of the tables, Hi-Definition television playing a basketball game and neon lights that attracts the eyes. I felt like I was in a different country.

The smell of hot curry pouring from room is inevitable. The mixture of spices filled up my nostril as I sat. The lighting of the room might not be pleasant but it is the way in which the restaurant owner set up his restaurant to stop excessive lighting, which is done with a huge decorative curtain. My attention was set on the glamorous uplifting Indian pop music, playing from the large high-definition televisions.
If you upgrade to an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, you can take advantage of super-fast 5G speeds, but which 5G network are you actually getting and is it better than the others? Depending on your carrier, you may see 5G, 5G+, 5G UW, or 5G E in the status bar next to the signal strength, and there's a pretty big difference between them.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Historically, Apple loves to drop hints about its major upcoming events through clues included on its invitations. Those invites usually require a good bit of deciphering to connect the dots, but in the case of Apple's upcoming Worldwide Developers Conference (WWDC) 2018 invite, the topic is immediately obvious: it's augmented reality.

Google has begun the testing phase for its new Hands Free app that lets you pay at participating locations without having to even take your phone out of your pocket.
Recently, Mike over on Samsung Galaxy S4 softModder showed how to scroll from the bottom to the top of a page with a single tap, a feature that Apple is well known for, and something I missed very much on my Galaxy Note 3. However, there's always room for improvement.

The possibility of the Sriracha factory in Irwindale, CA being shut down was one of the biggest food stories of 2013. Huy Fong Foods was almost forced to close the plant due to complaints about the factory's smell, but luckily the brand emerged triumphant.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

There are only three more episodes of Game of Thrones left before the saga is over, but Magic Leap is capitalizing on the series' popularity while it still can.

The Game of Thrones premiere is fast approaching, and along with it, Magic Leap has begun to unveil some of the fan-centric swag associated with its immersive experience based on the hit TV series.

Six Flags is teaming up with Samsung to make riding a roller coaster a little more thrilling, and quite possibly a little more nauseating as well.
Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

A couple weeks ago, GM's Cruise Automation released a remarkable self-driving video from the streets of San Fransisco that Driverless analyzed in detail. And now they've just released a new one giving more insight into their growing mastery of the complex roads in San Francisco, specifically, the Potrero Hill and Mission Dolores neighborhoods.

Students from Carnegie Mellon University's Entertainment Technology Center have been working on an augmented reality system to help teach music in a project called Music Everywhere.

There may be no other crustacean with as many names as the crawfish: crayfish, crawdad, crawdaddy, mudbug, Florida lobster, spiny lobster, rock lobster, and freshwater lobster (to name a few). But no matter what you call it, there's no denying that it's a popular delicacy in the South and beyond.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Star Trek Communicator badges rule. If you're a Trekkie, you know they are iconic to the TV series. The Next Generation, Voyager, and Deep Space Nine all had these awesome communicator badges.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

With a 5-inch screen, it's possible that the Samsung Galaxy S4 can be a bit large for our hands. While my grubby hands let me navigate the phone pretty easily, the same can't be said for everyone. A lot of us use two hands to type on the phone, play games, and perform tap or swipe gestures.

Apple announced support for mobile driver's licenses and state identification cards in Apple Wallet back in 2021, and Arizona was the first state to jump on board in 2022. Fast forward to now, and only seven states let you add a driver's license or state ID to Apple Wallet on your iPhone and Apple Watch. It has been a slow rollout, but more states are coming or are at least showing interest.

Hey, you, still stuck at home? Cheer up, today is the first day of spring. Yes, really. And since you're probably locked in on TV, we're guessing you need a break from some of the less than sunshiney news reports rolling in. Well, no worries, because there's actually some good news to report.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.
At an event in Mountain View, CA, and watched by fans via live stream on YouTube, Google announced a slew of new products today. Over the last few weeks, there was no shortage of rumors and leaks about what might be unveiled, but now the secrets are out.

If you could save the world by eating a burger, would you? Two companies, Beyond Meat and Impossible Foods, are on a mission to redefine veggie burgers and eliminate all of the downsides of animal farming on our planet. With over five years of research and product testing, they've finally figured out how to make a plant-based burger look, feel, and taste just like real meat.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.
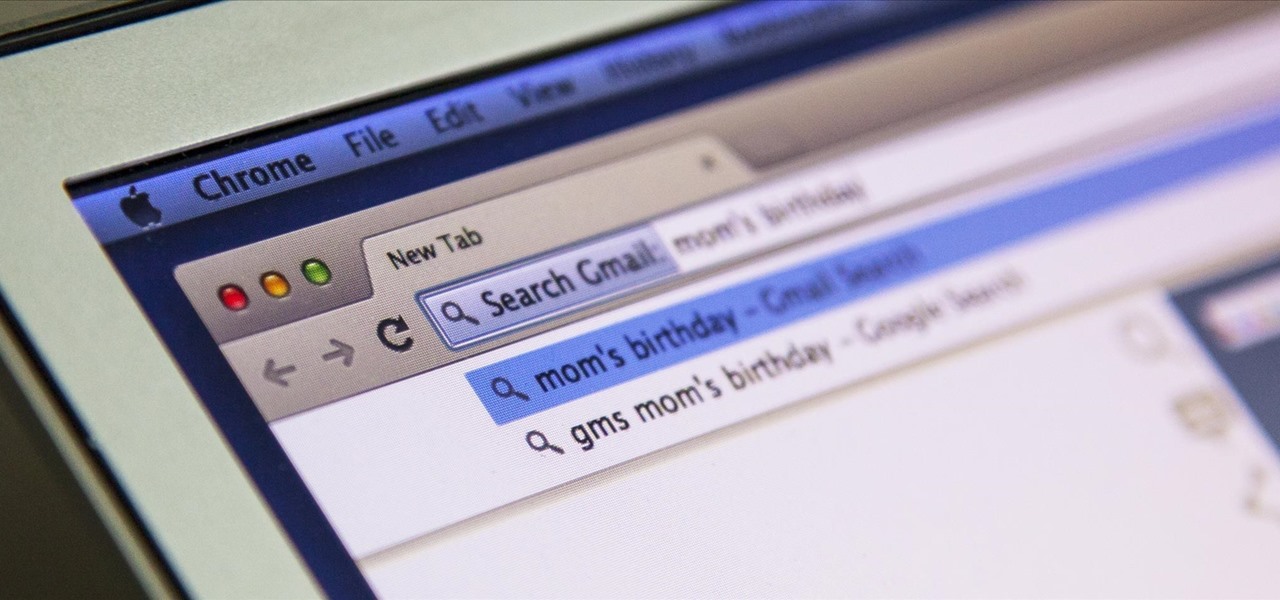
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."